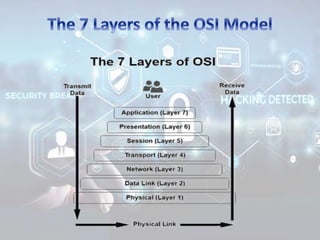
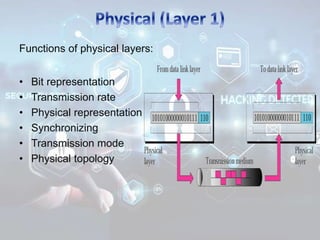
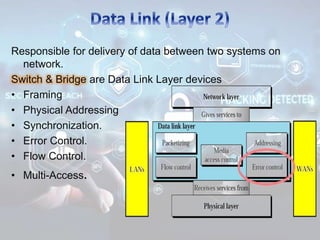
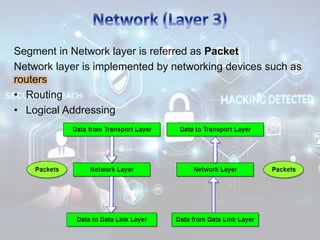
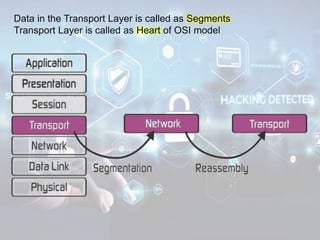
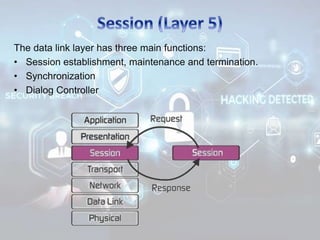
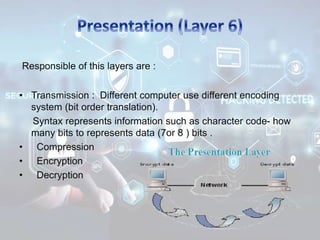
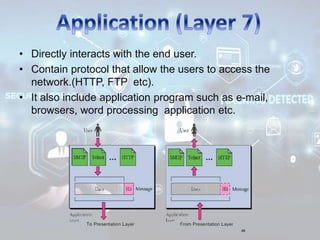
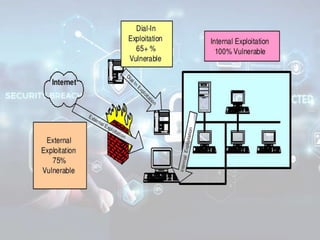
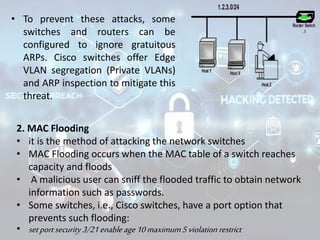
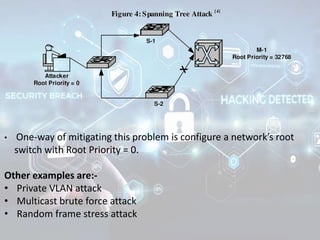
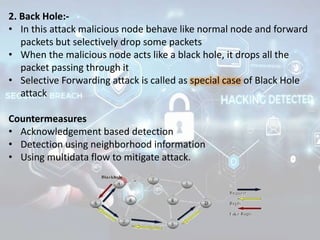
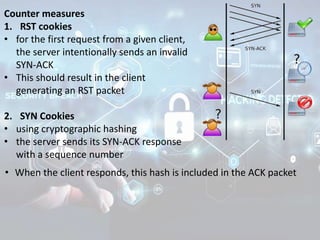
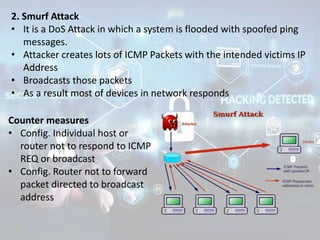
The document summarizes the seven layers of the OSI model and security threats that can occur at each layer. It describes the functions of each layer and common attacks such as IP spoofing at the network layer, ARP spoofing at the data link layer, and viruses/worms at the application layer. The document provides examples of security measures that can be implemented to mitigate threats at different OSI layers.