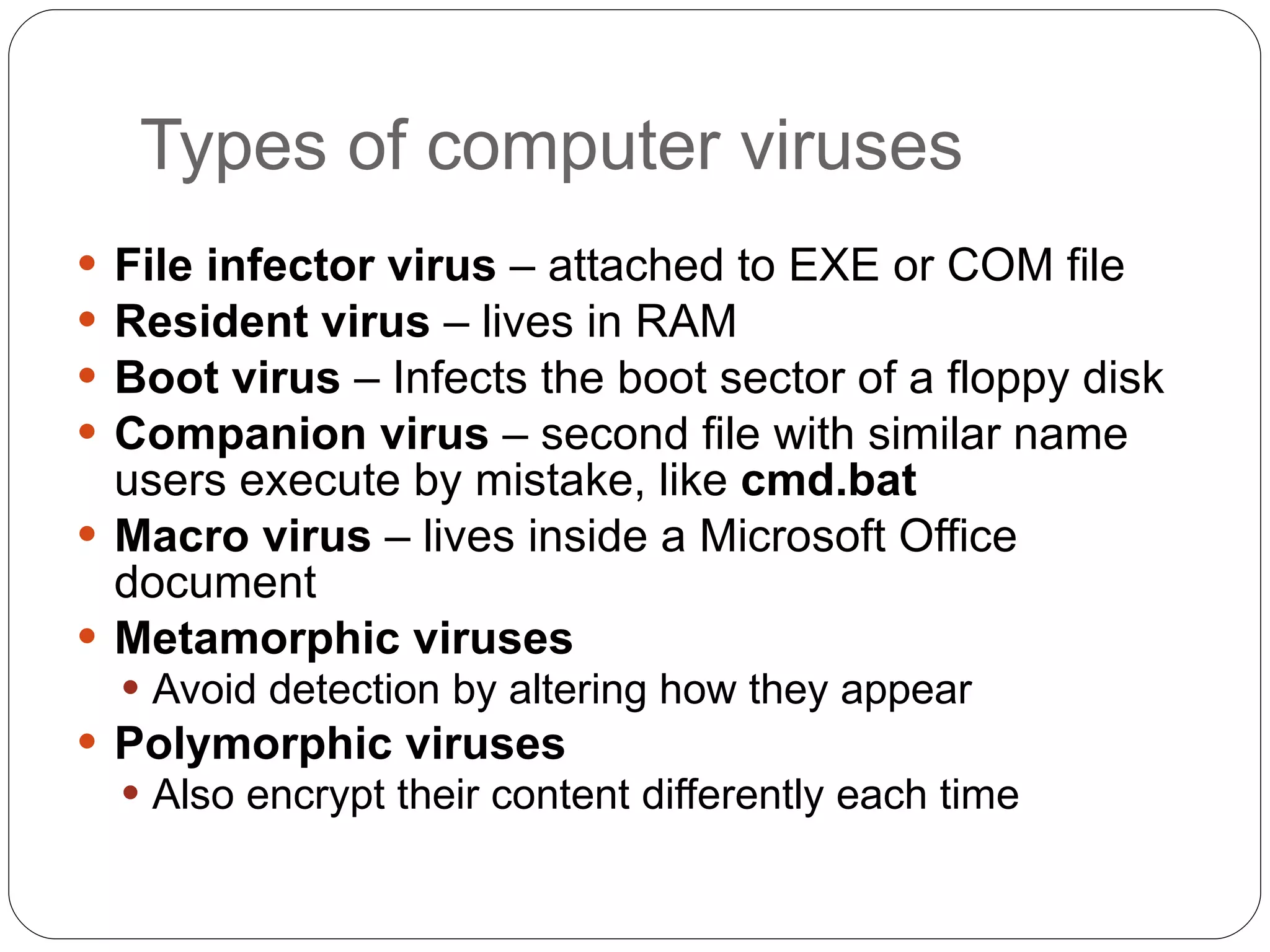
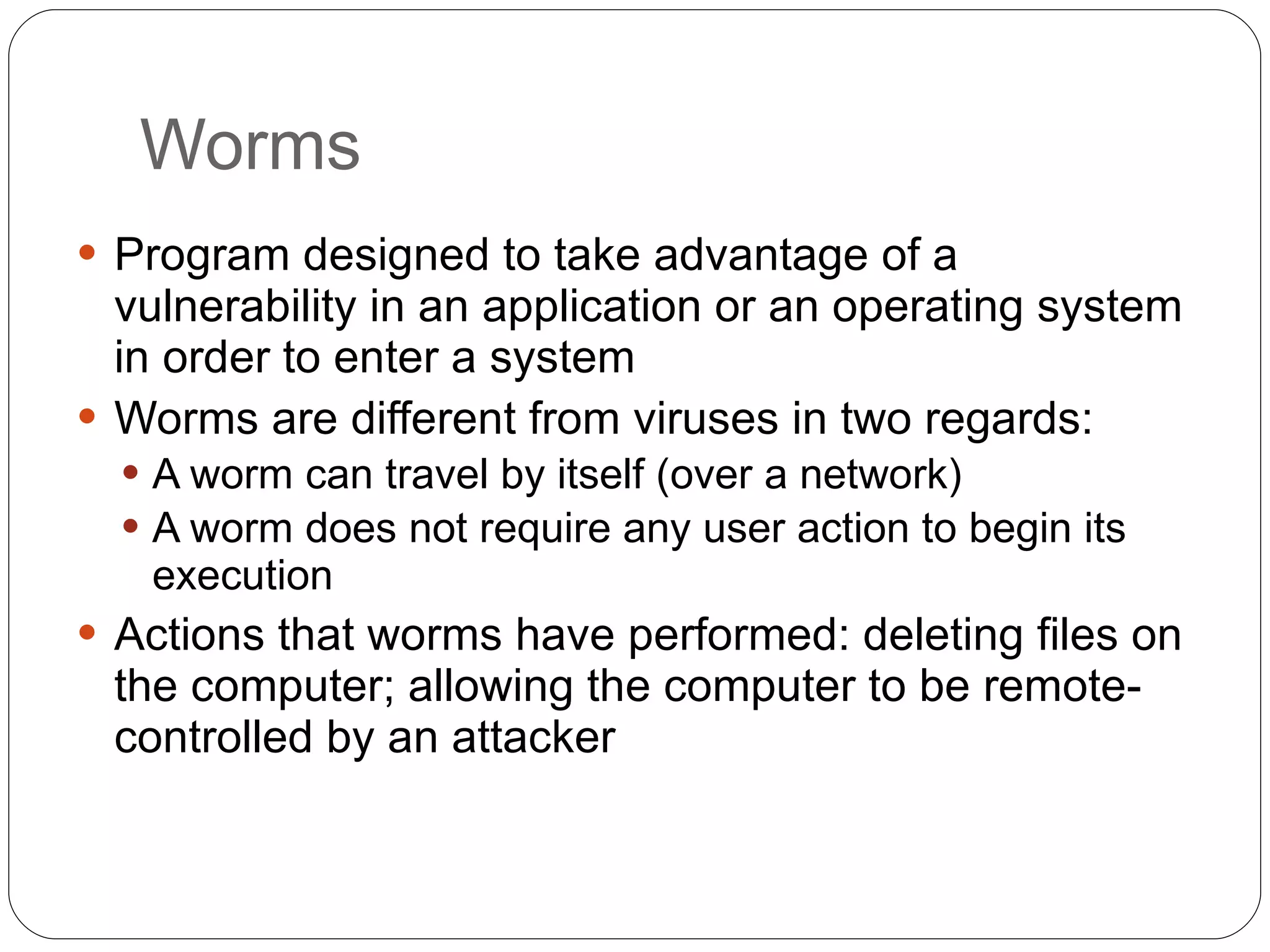
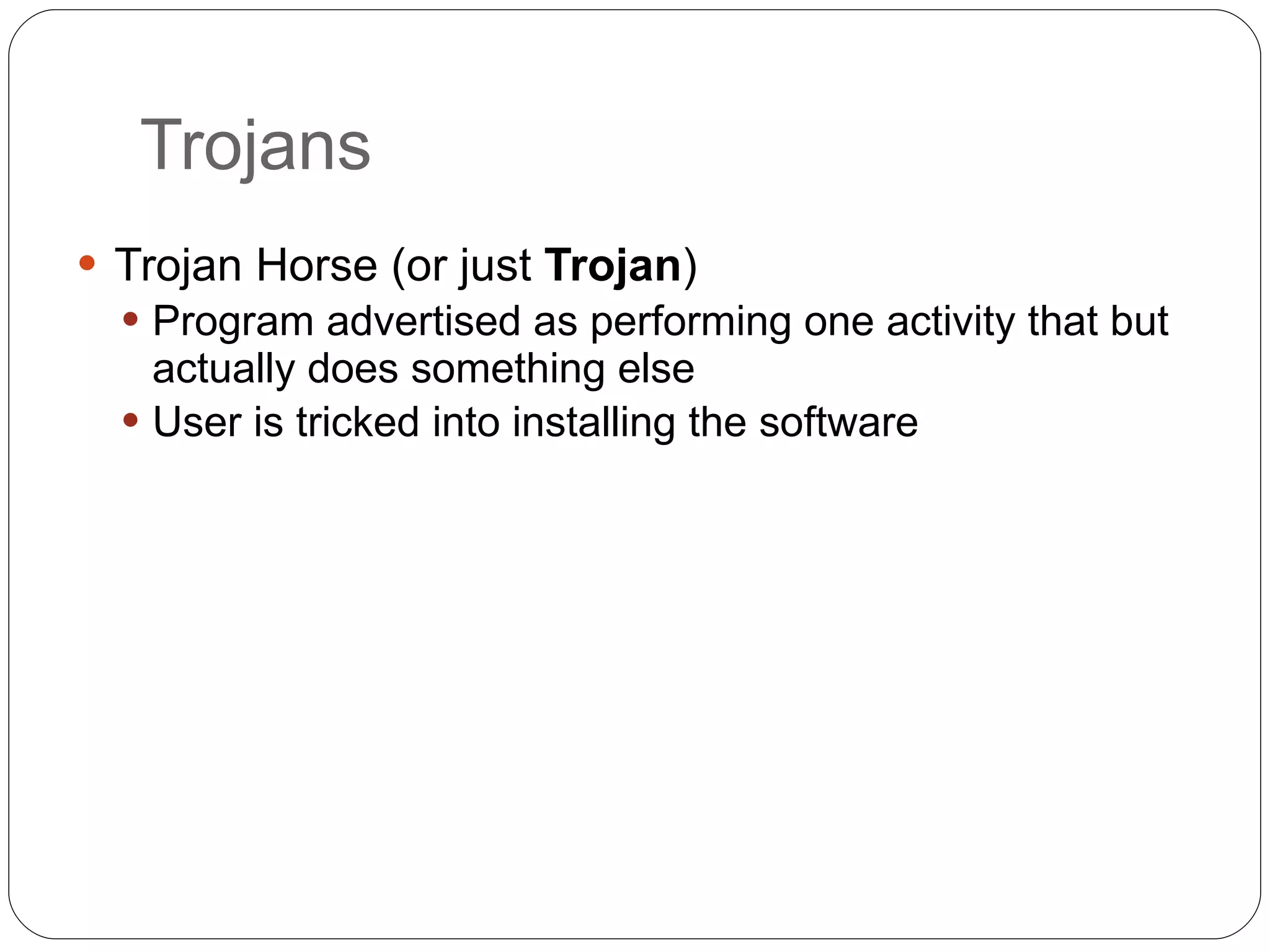
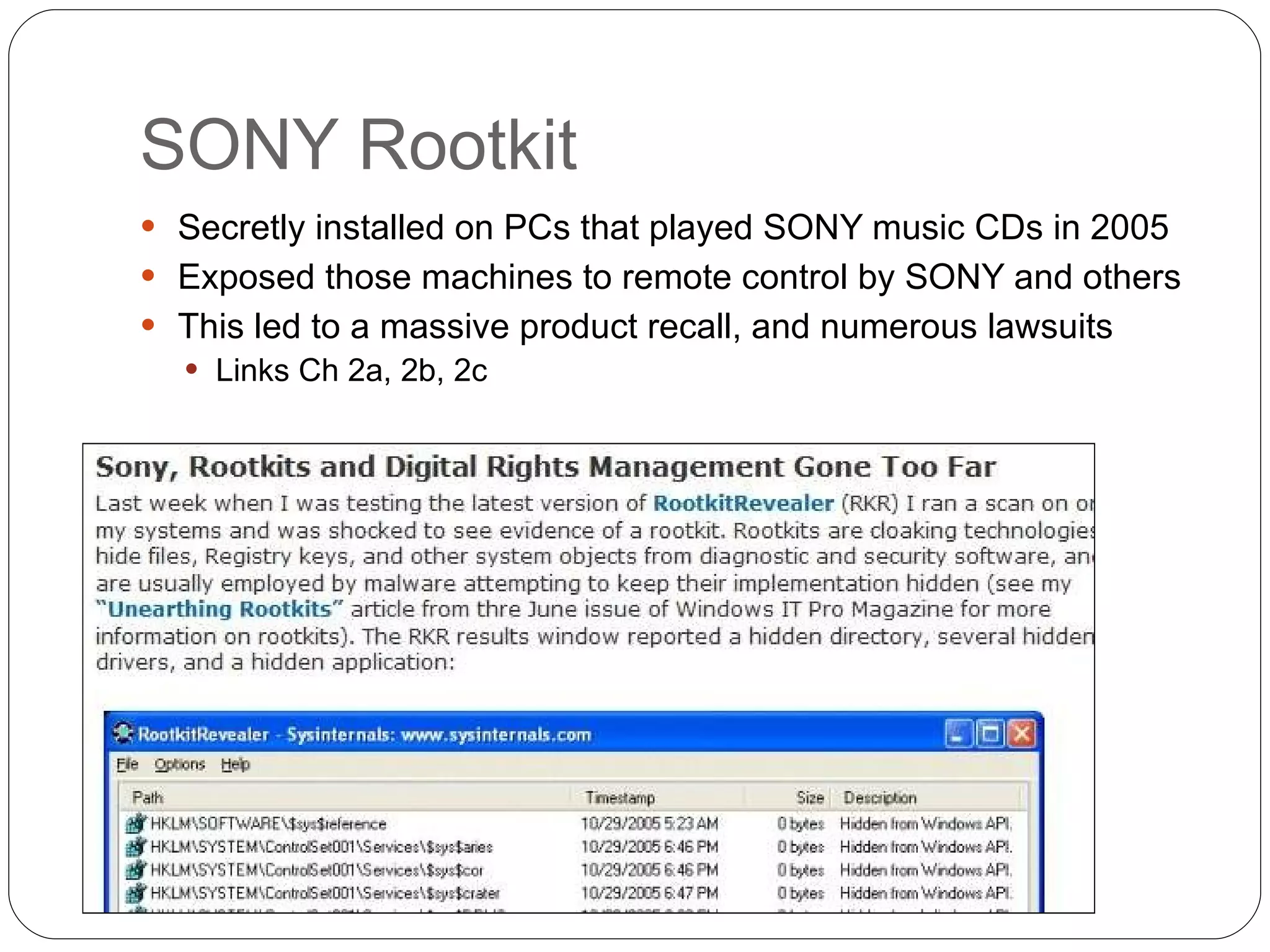
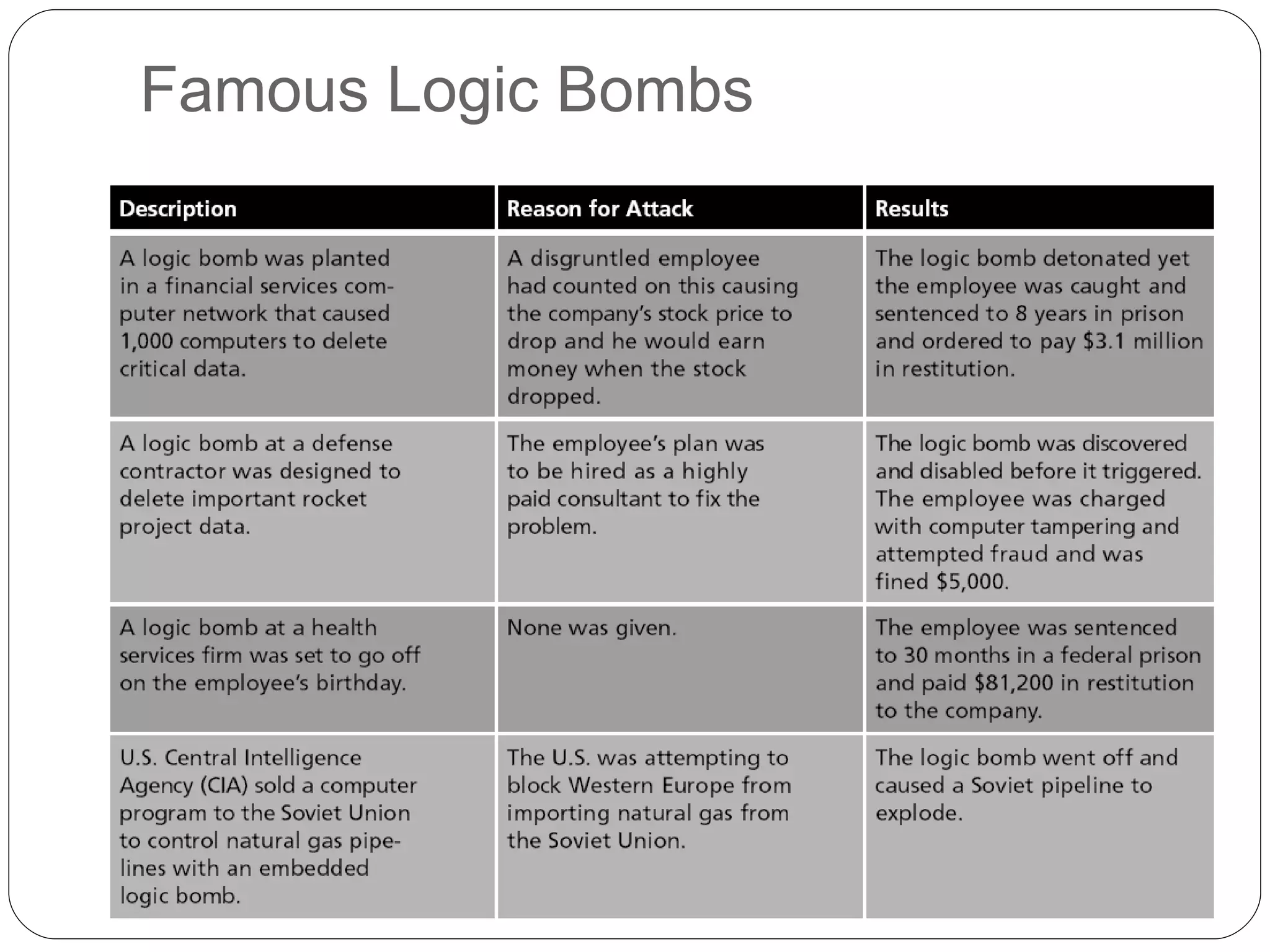
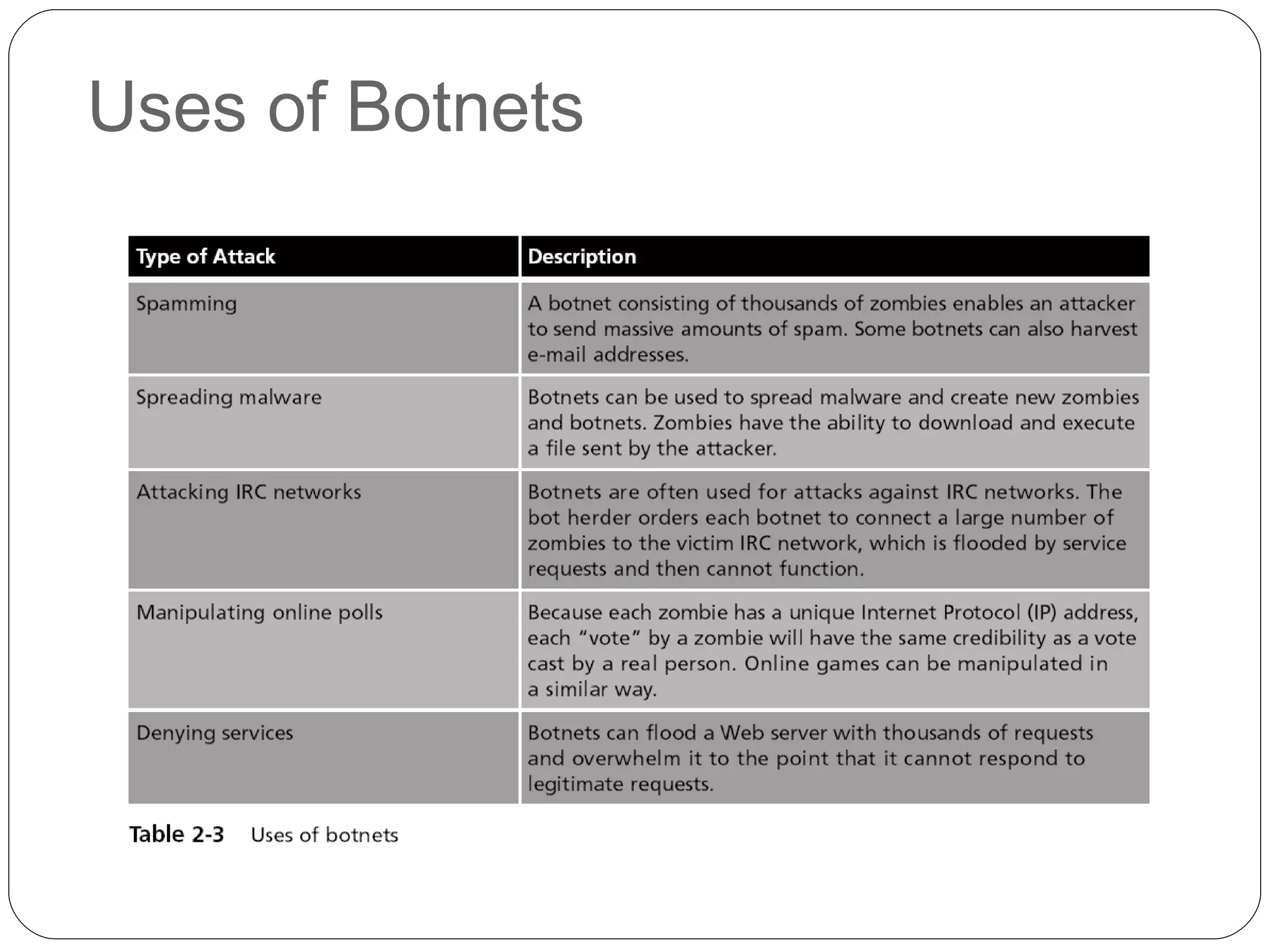
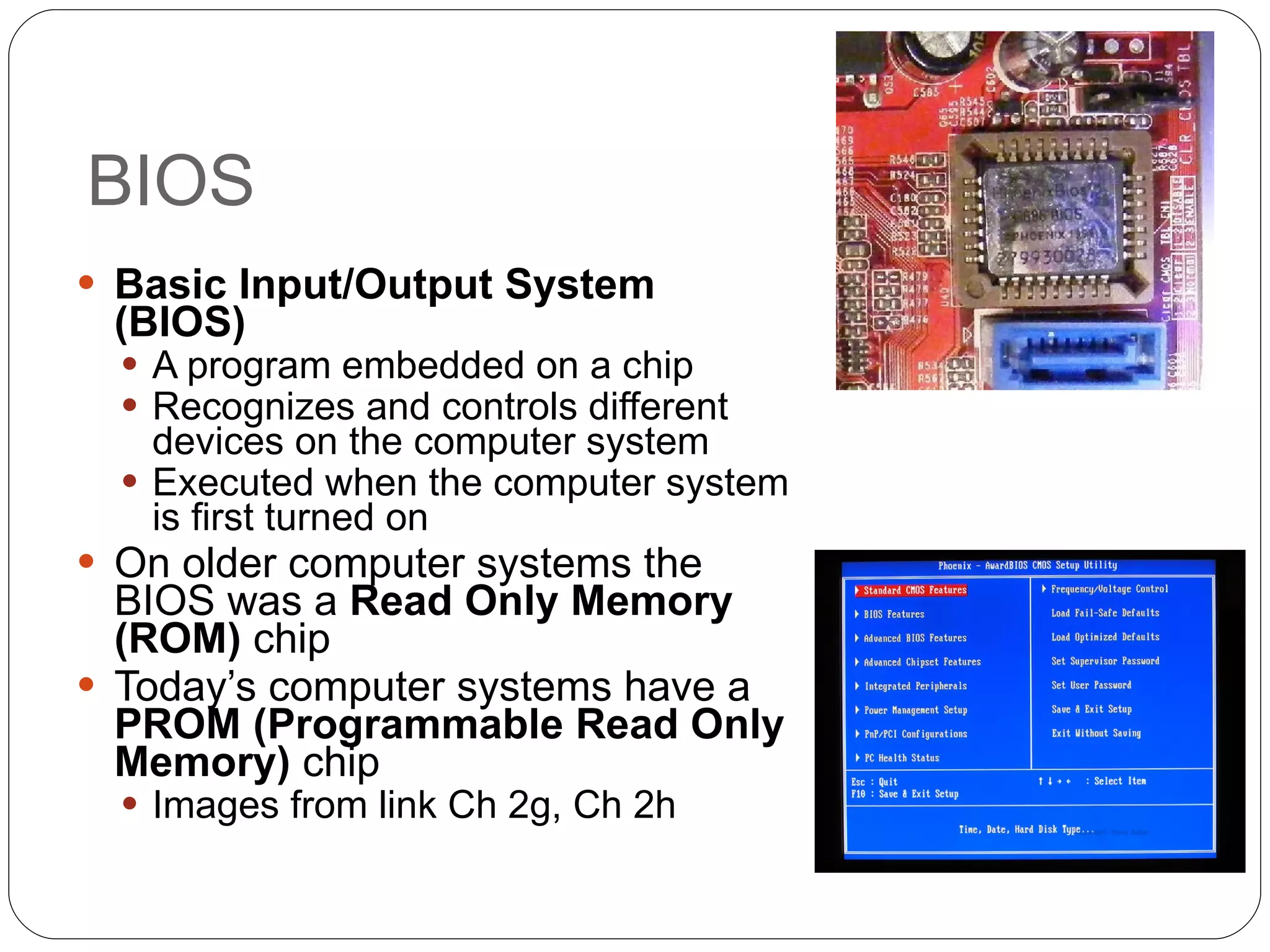
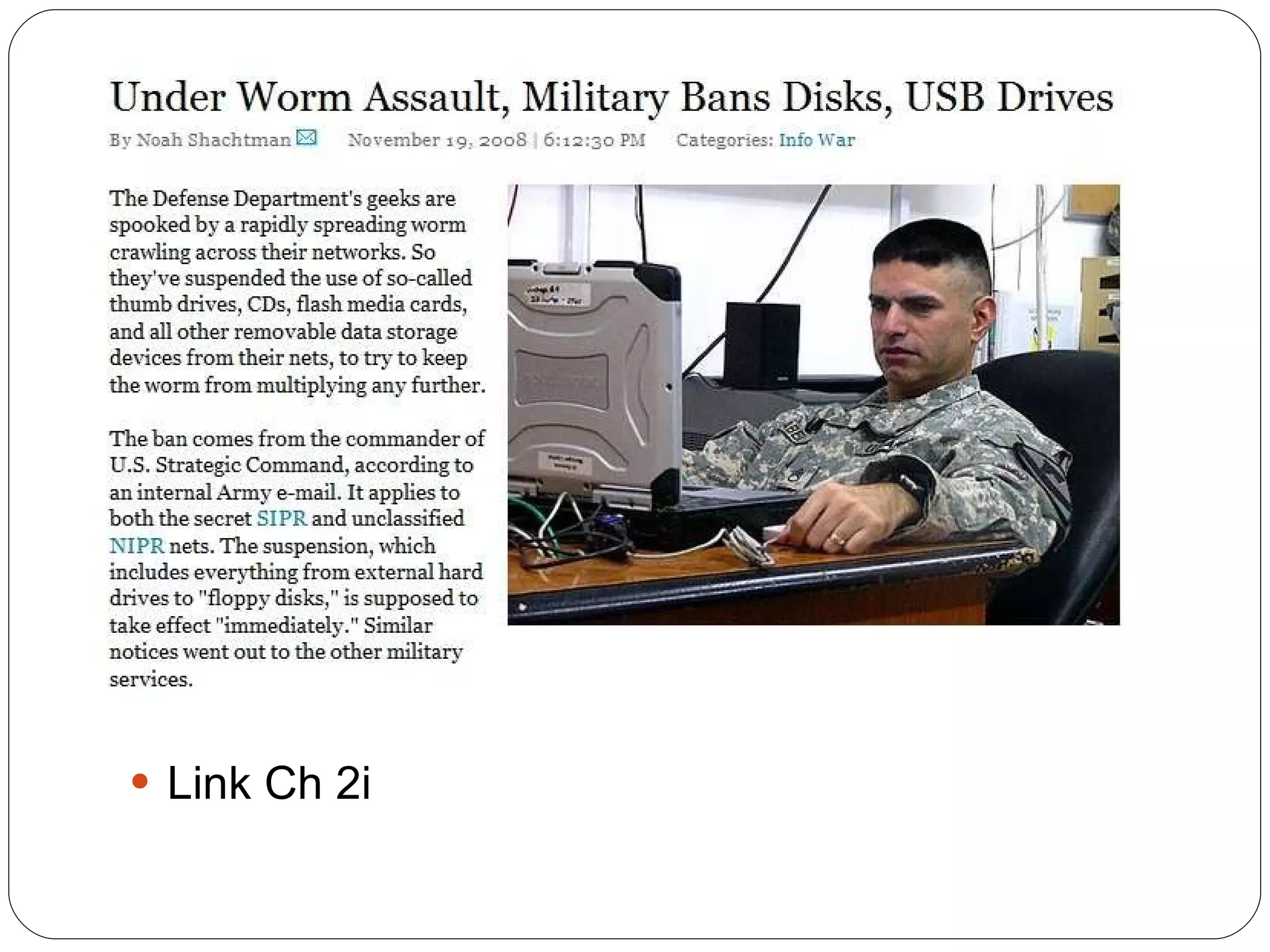
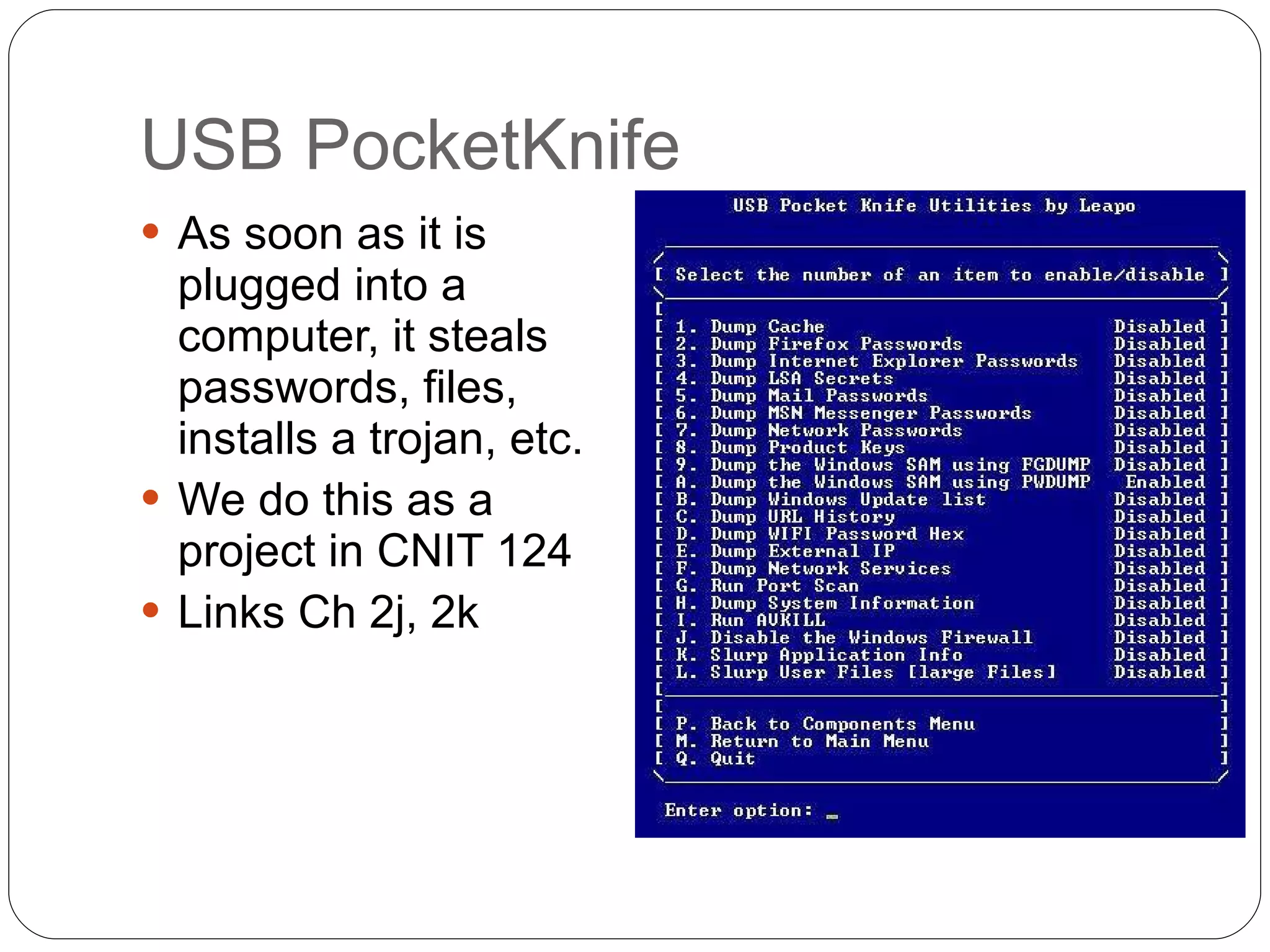
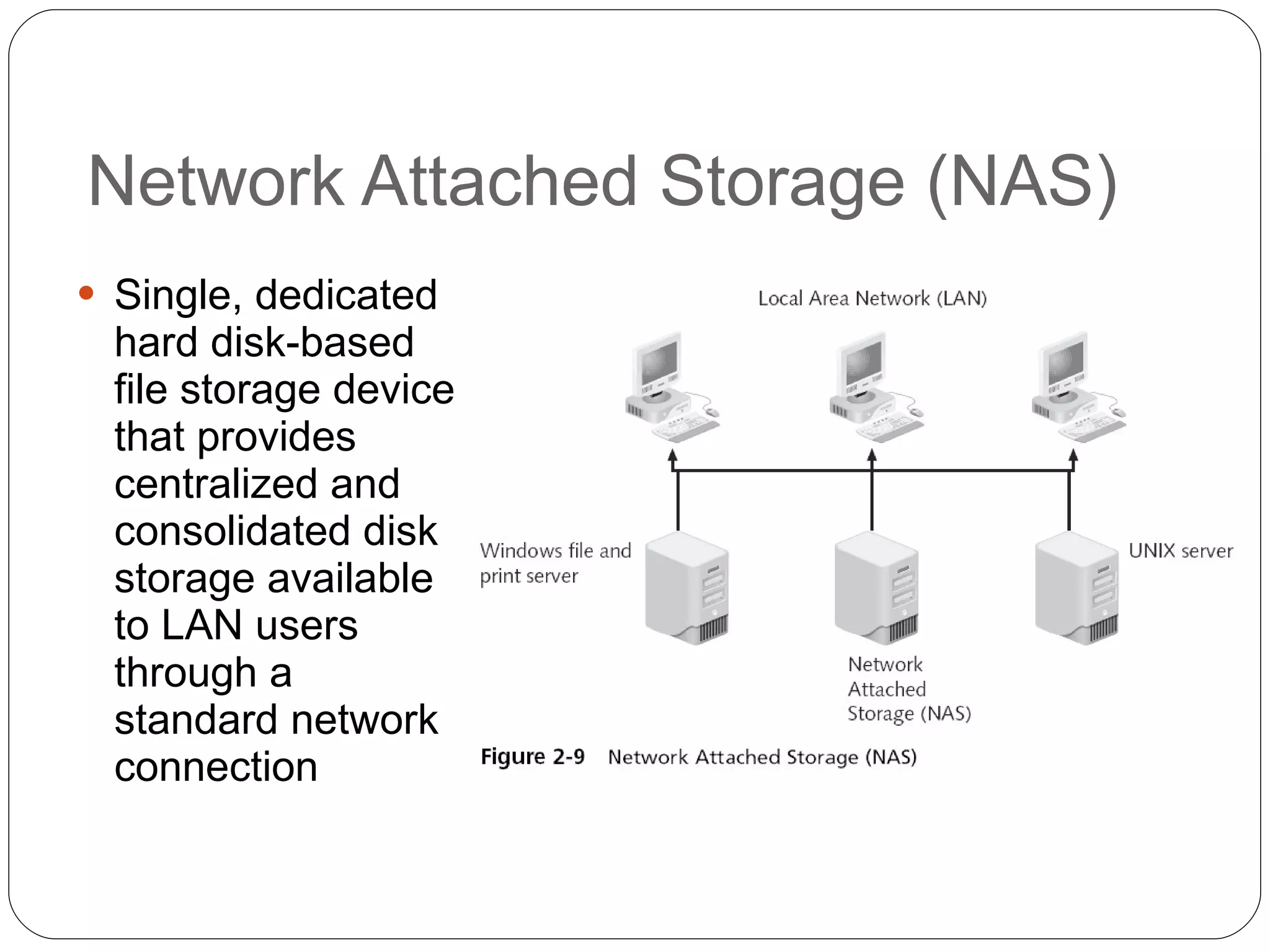
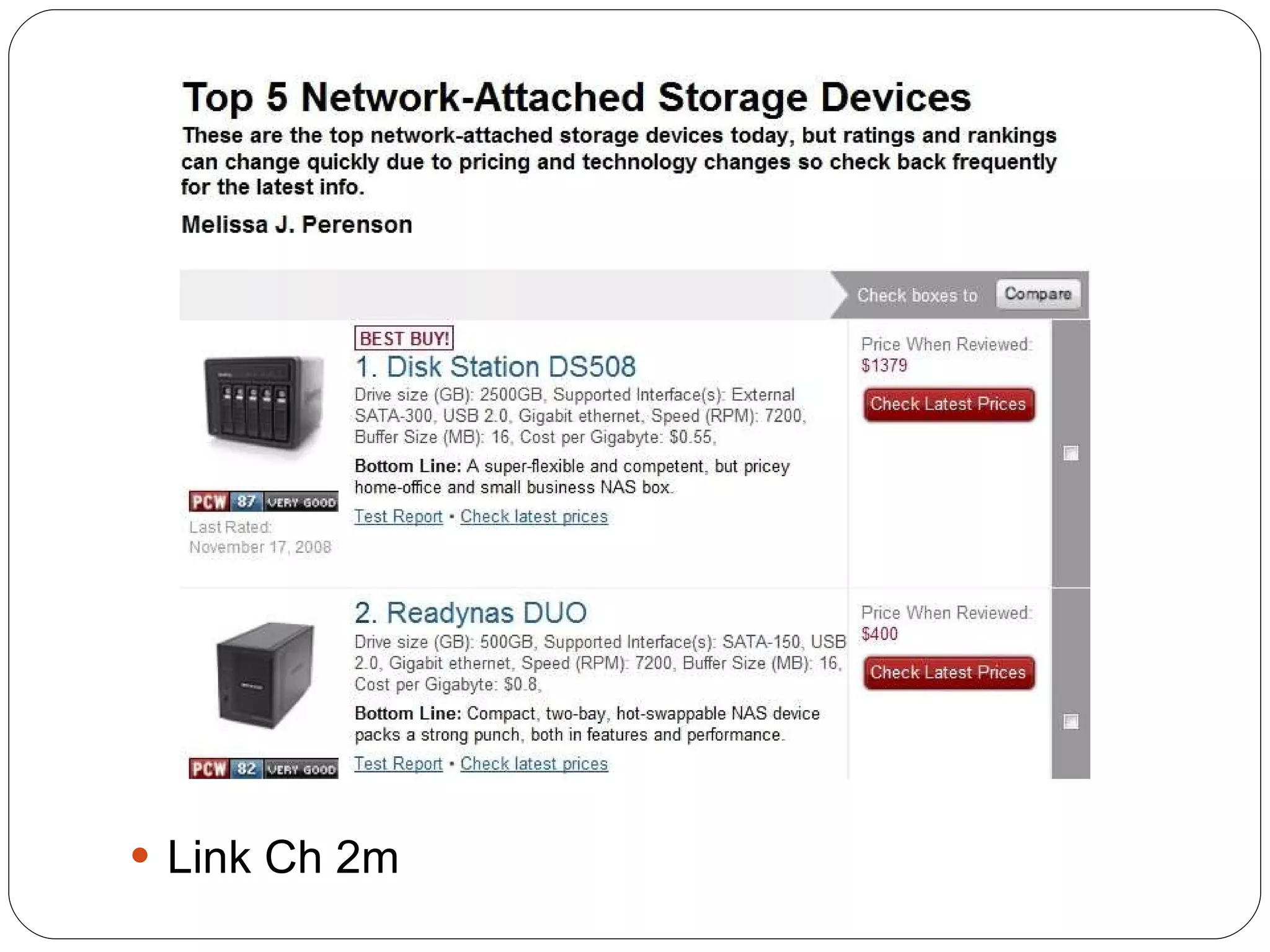
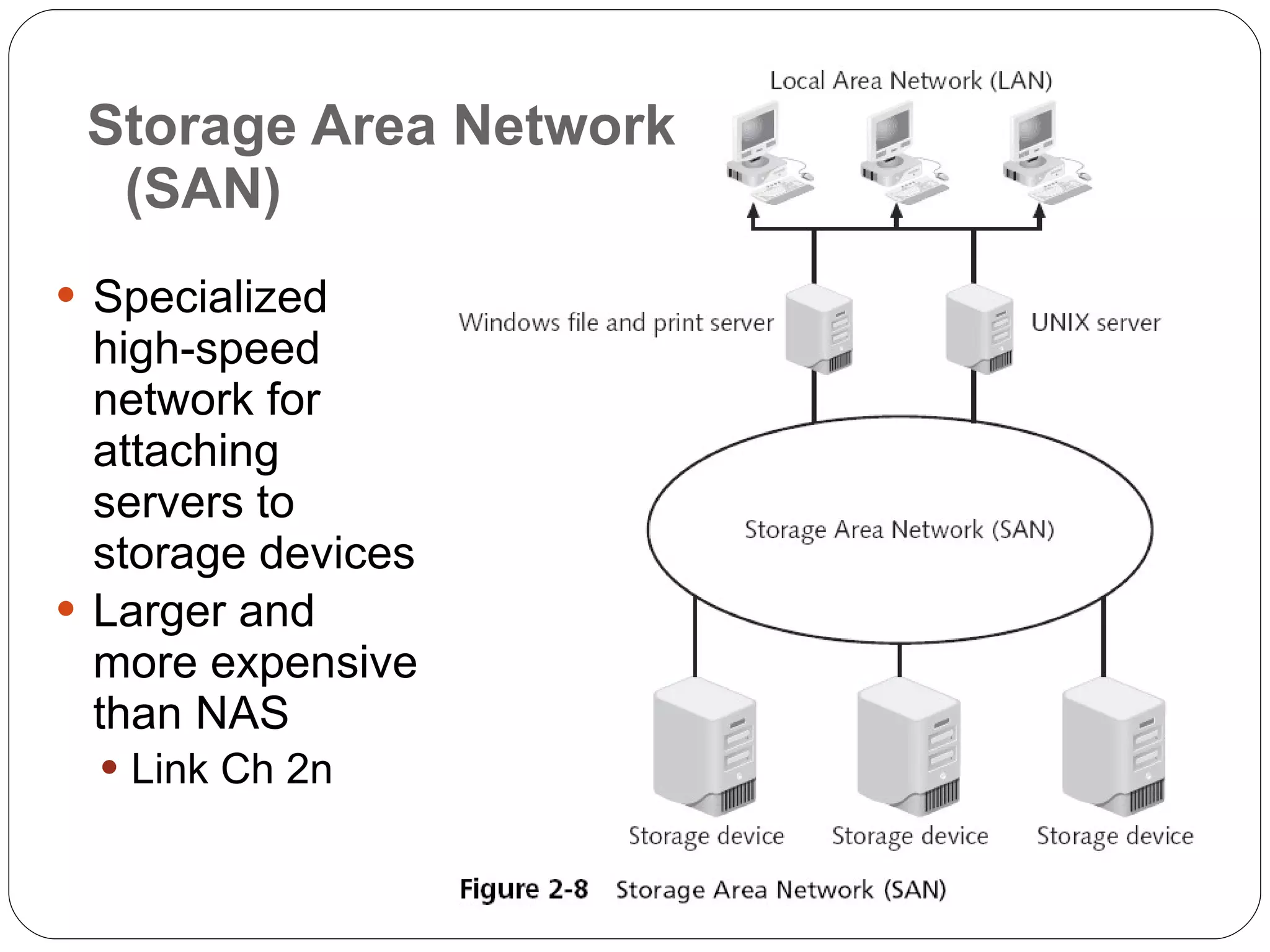
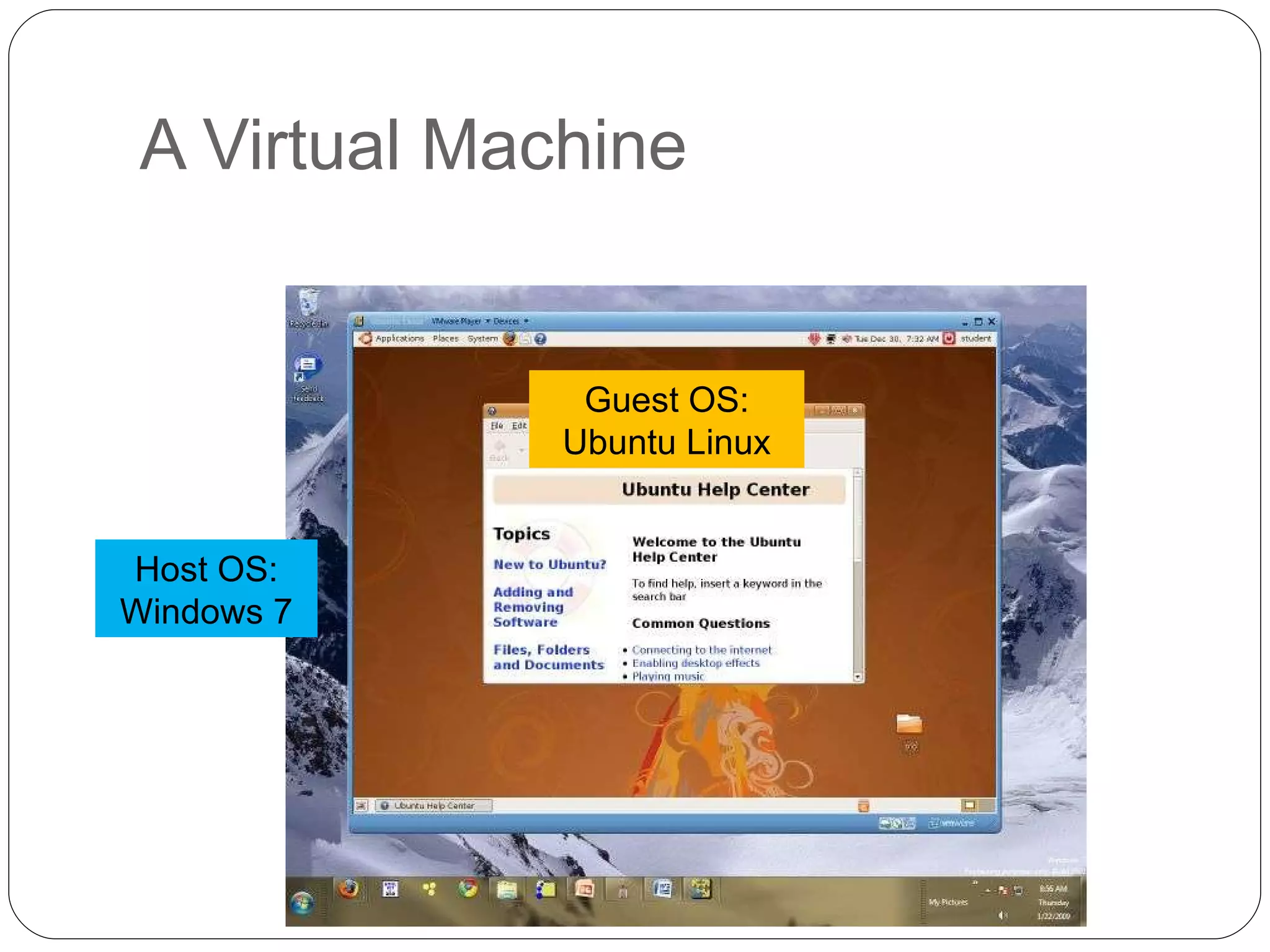
Chapter 2 of the 'Security+ Guide to Network Security Fundamentals' discusses various types of software and hardware-based attacks, including malware, Trojan horses, and spyware, detailing their functions and impact. It explains the significance of viruses, worms, and logic bombs, as well as the vulnerabilities introduced by USB devices and how to mitigate risks associated with them. Additionally, the chapter addresses the security concerns related to virtualization and how existing security measures may not effectively protect virtual environments.