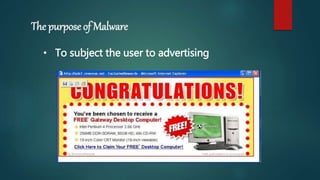
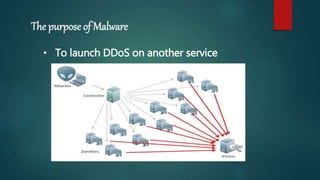
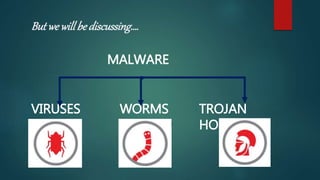
Malware refers to malicious software like viruses, worms, and trojans. Viruses propagate by infecting other programs and spread when an infected program is run. Worms propagate without human interaction by exploiting vulnerabilities. Trojans appear desirable but are malicious, and must be run by the user. Malware spreads through websites, email attachments, links, and removable media. Anti-malware software uses signatures and behavior analysis to detect and remove malware through scanning, detection, and removal.