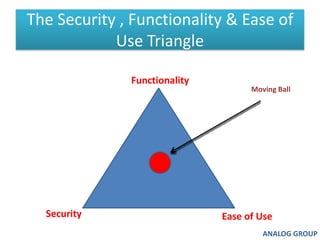
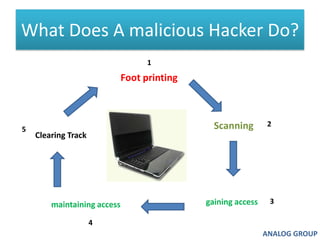
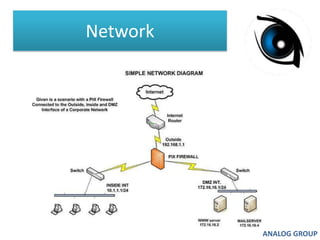
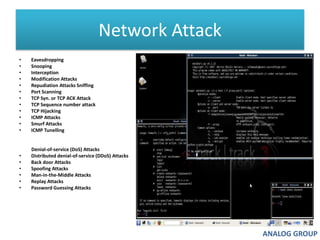
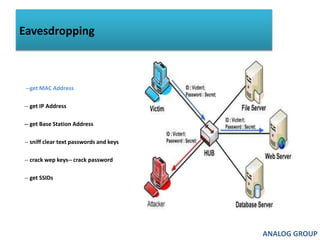
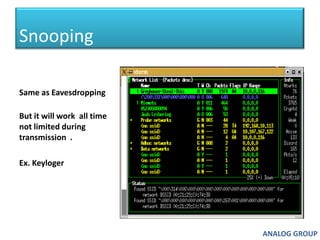
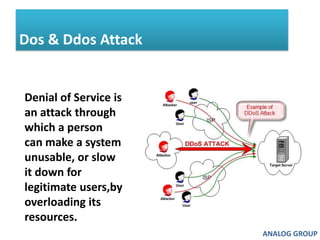
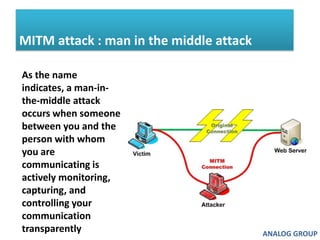
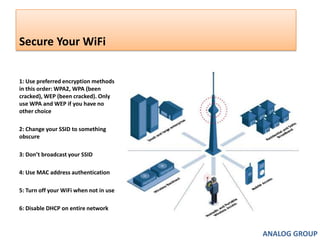
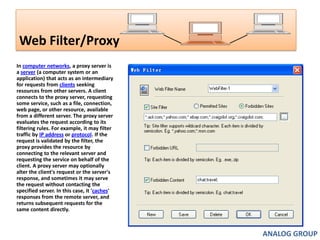
The document discusses cyber security and network attacks. It defines key concepts in cyber security like confidentiality, integrity, authenticity and availability. It then discusses different types of network attacks like eavesdropping, spoofing, man-in-the-middle attacks, and denial of service attacks. It also provides ways to protect against these attacks, such as installing firewalls, securing wireless networks, using antivirus software, and establishing a national cyber security policy.