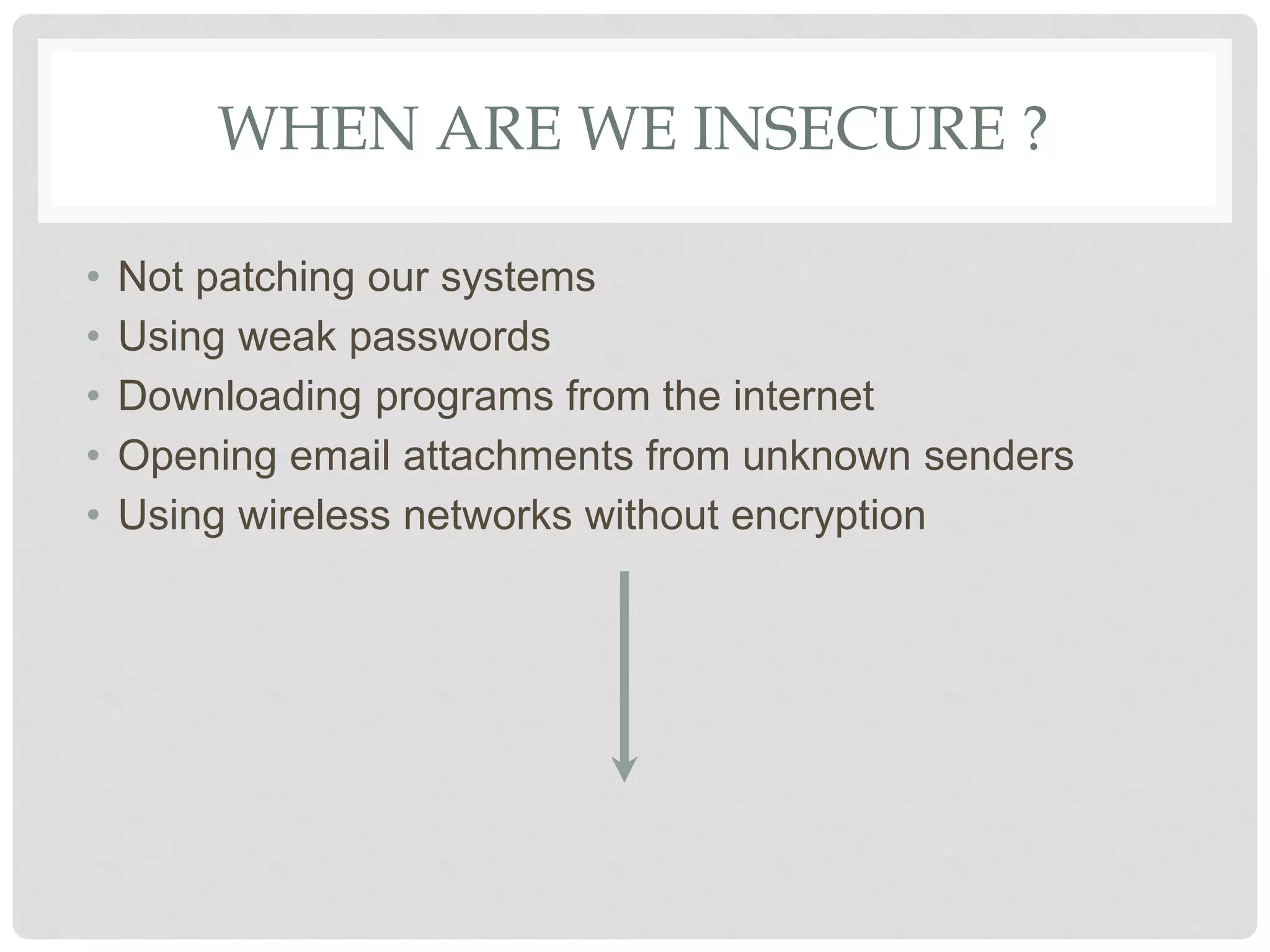
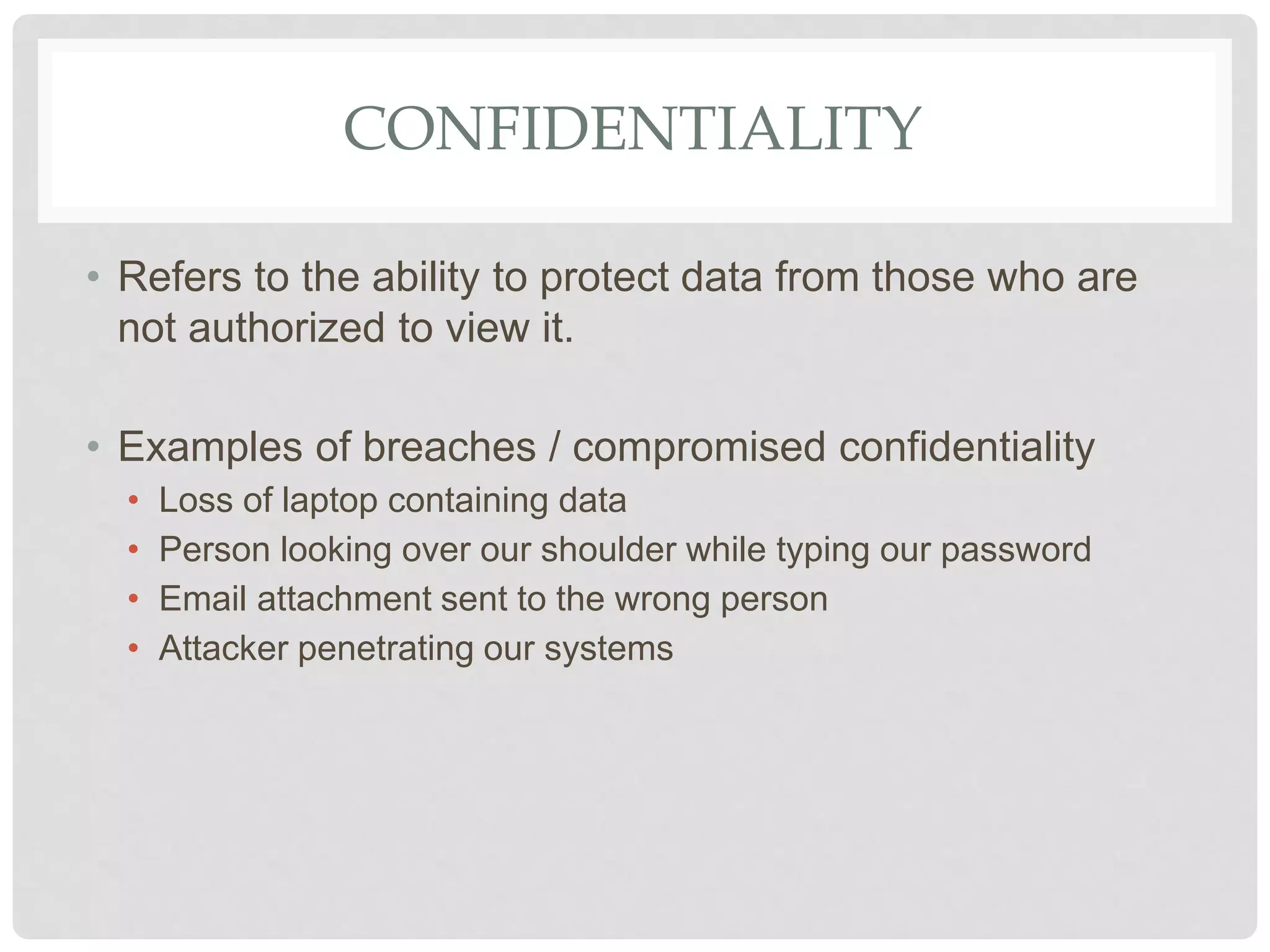
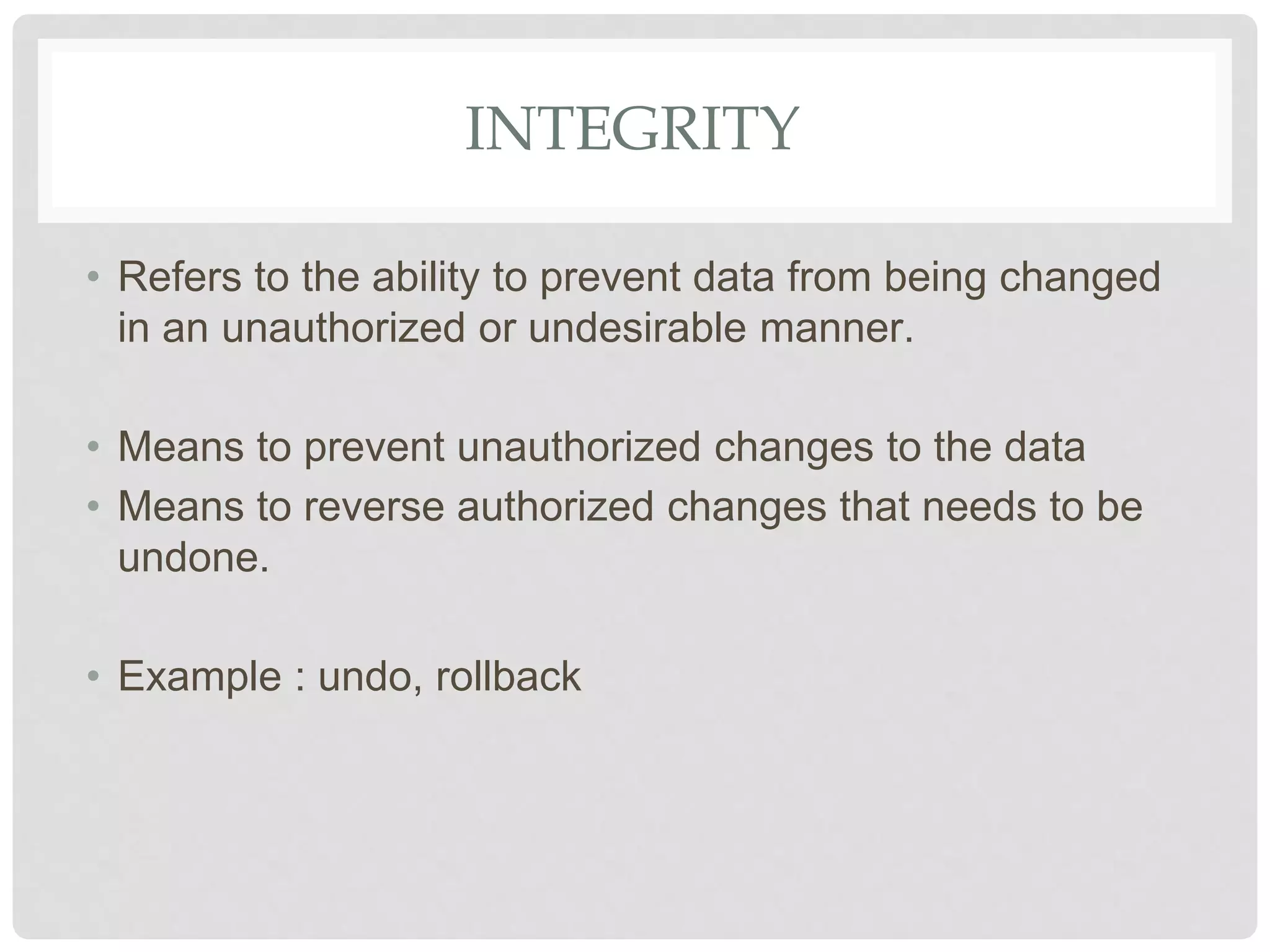
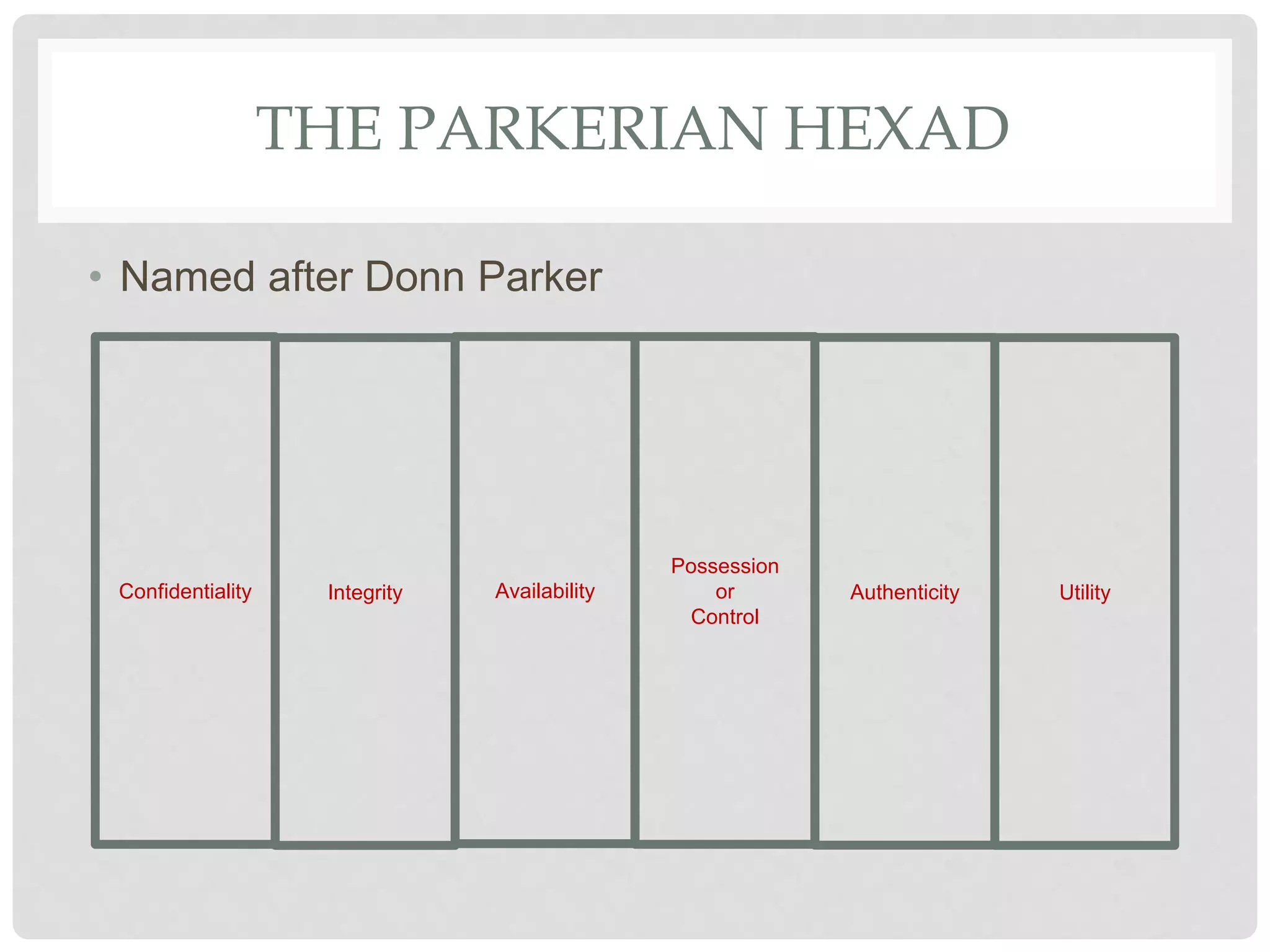
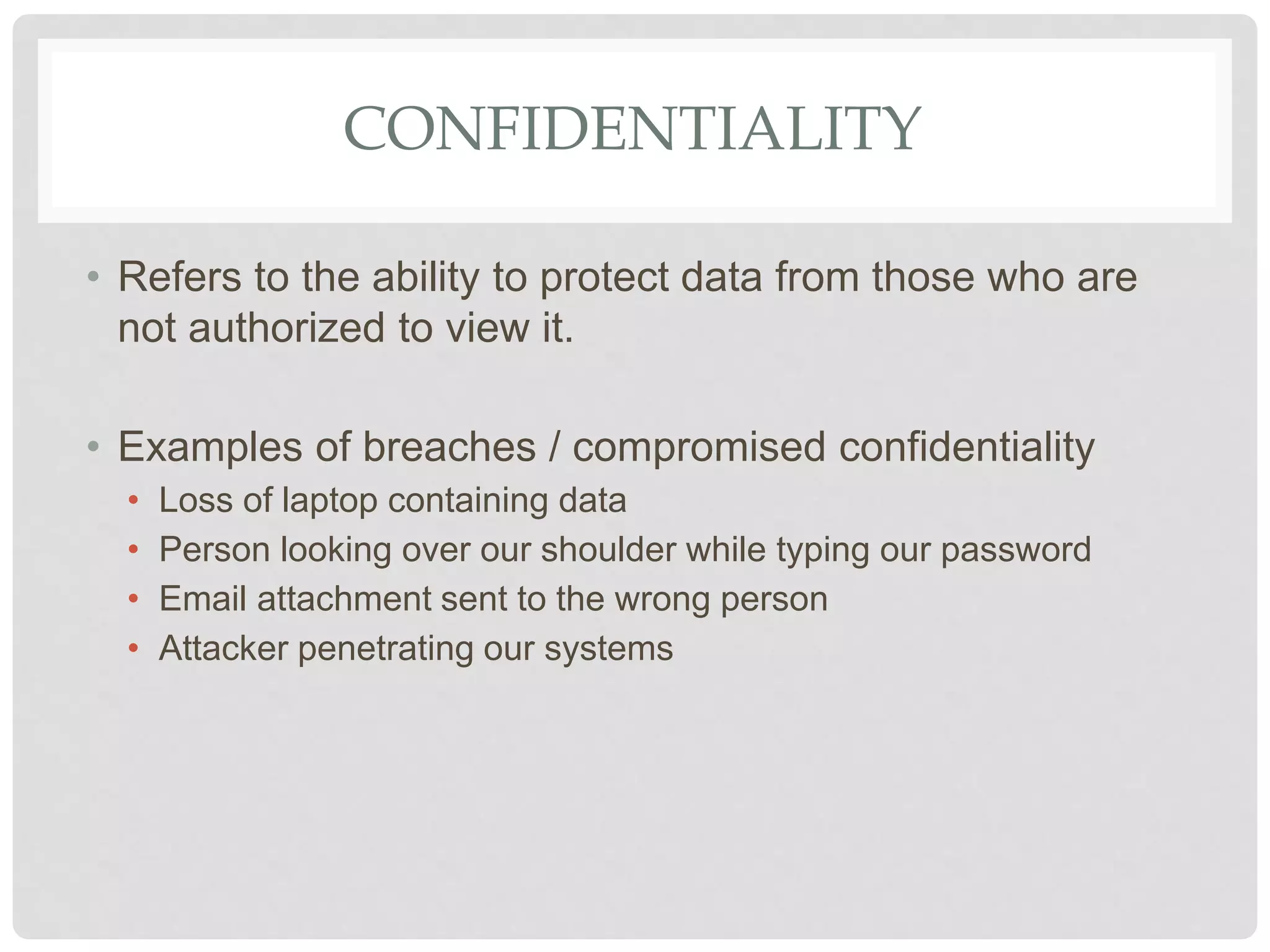
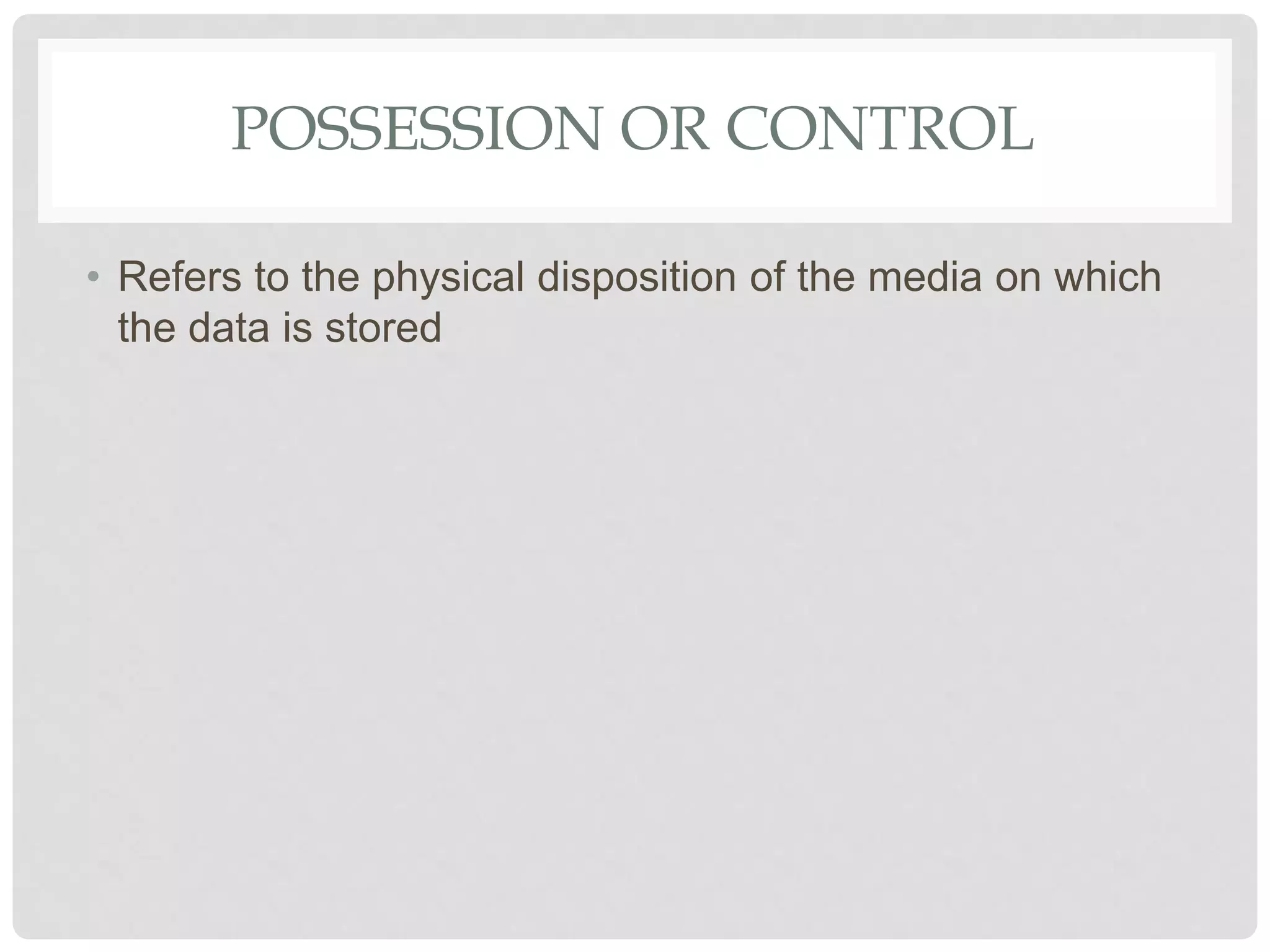
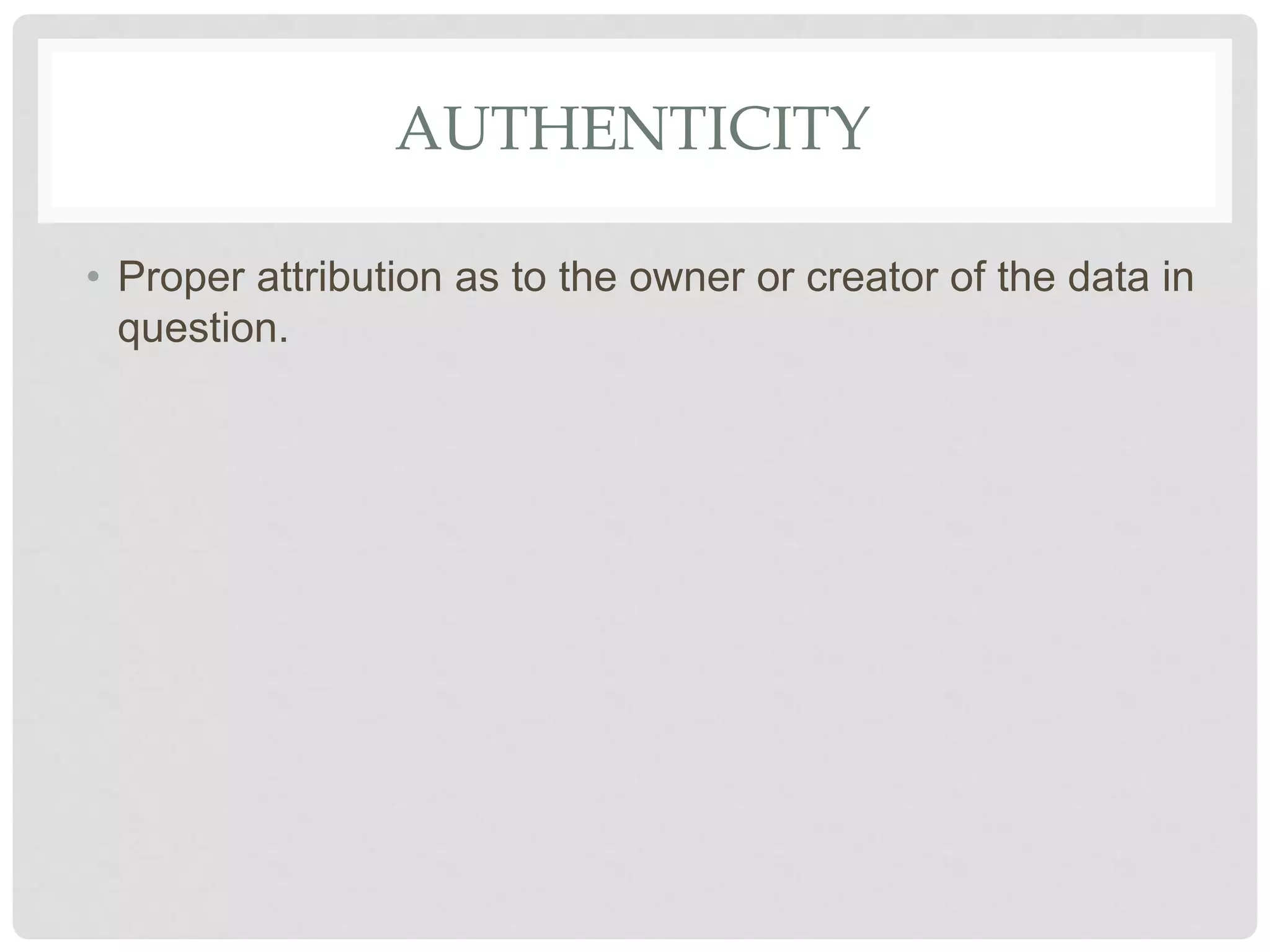
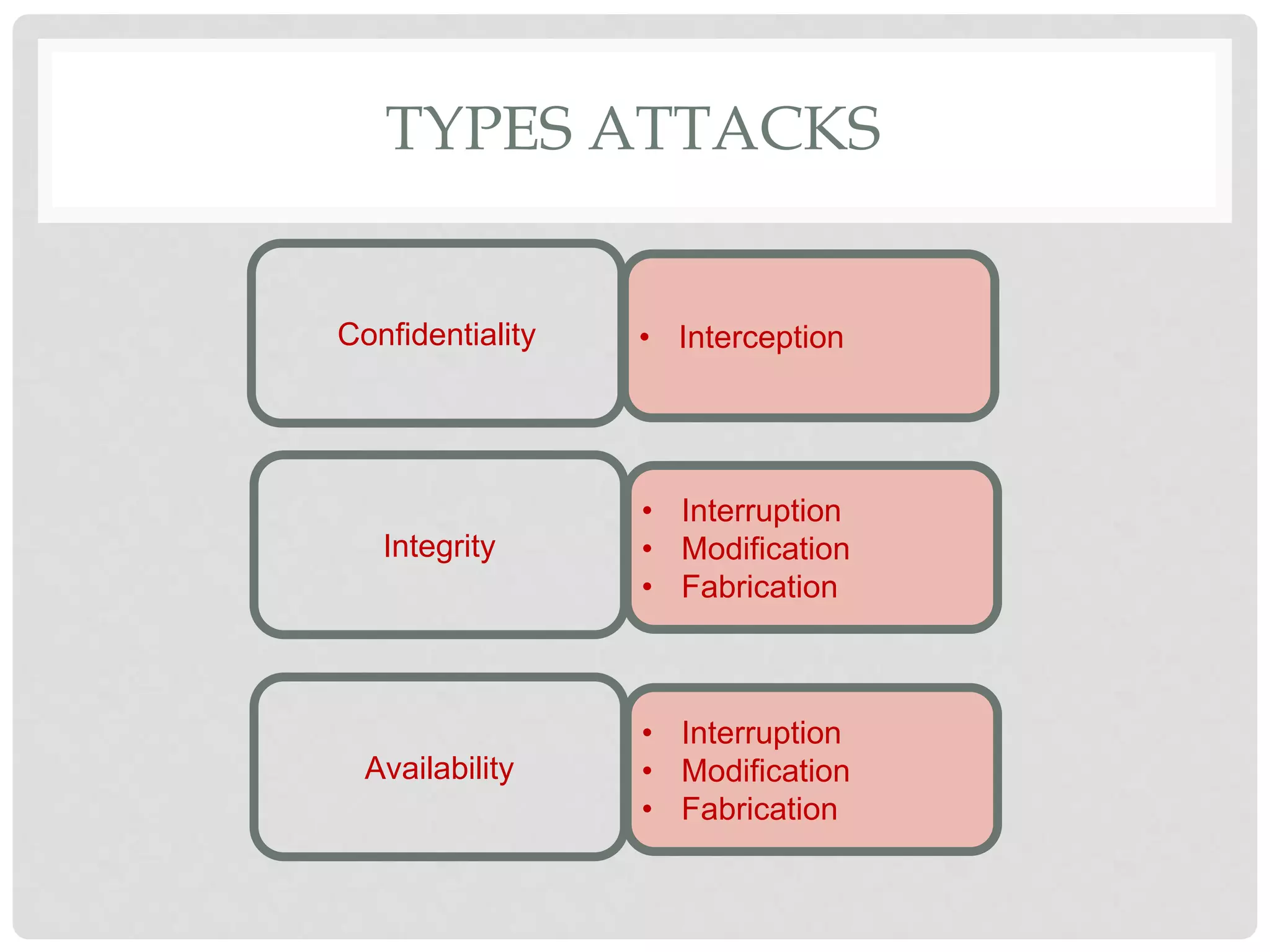
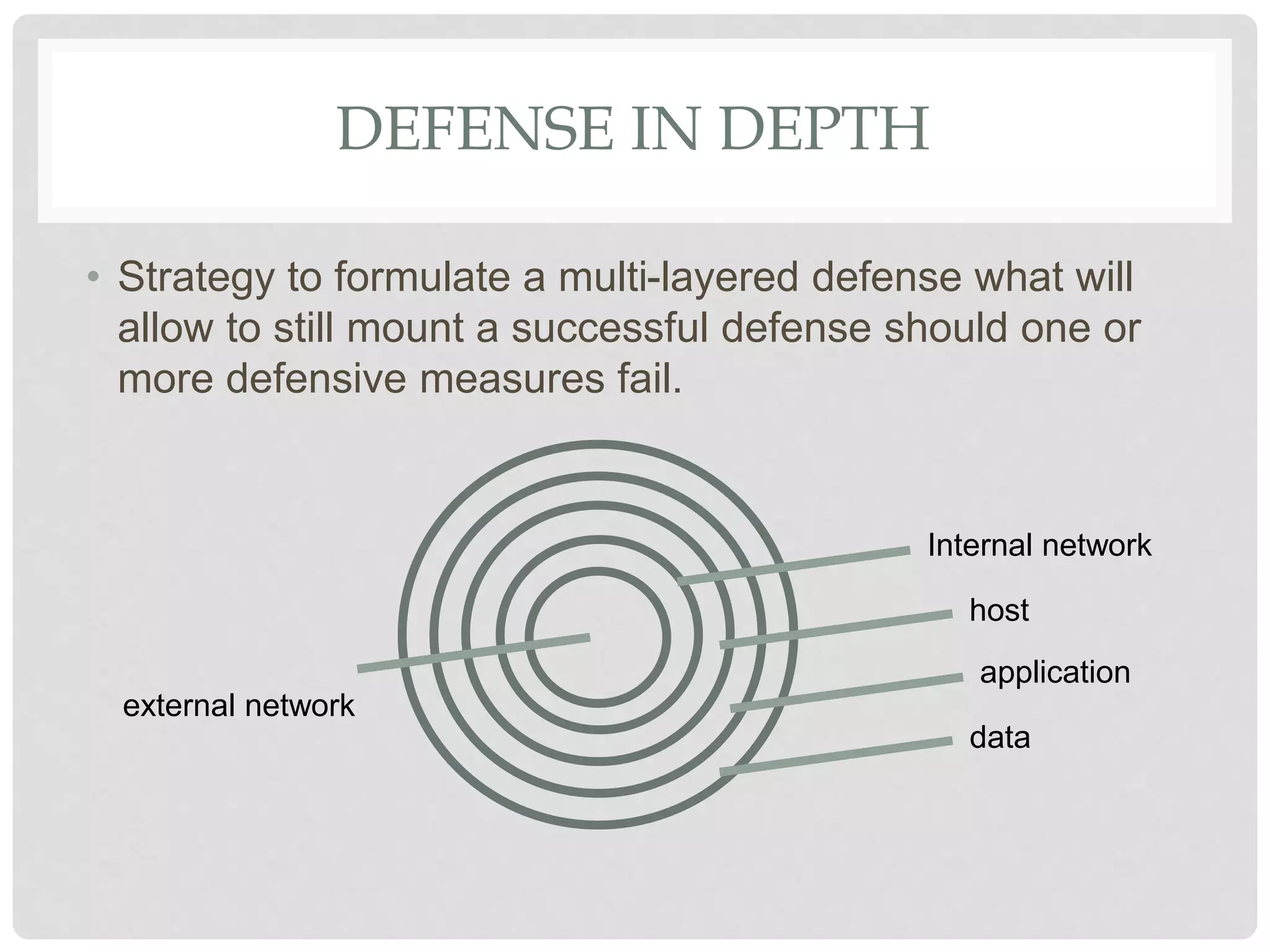
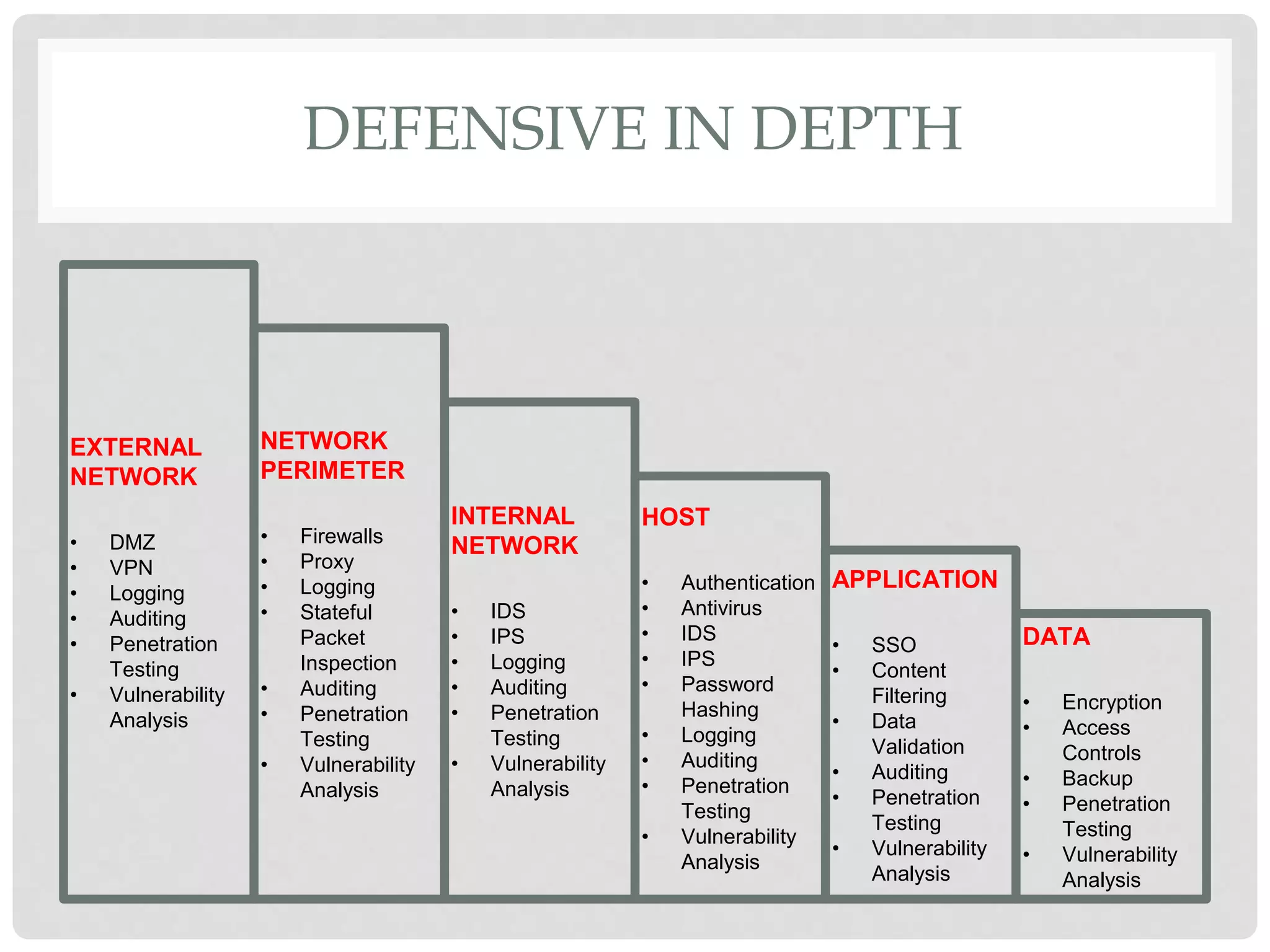
The document discusses various aspects of information security including protecting data from unauthorized access, natural disasters, and other threats. It defines key concepts like confidentiality, integrity, and availability and explains vulnerabilities like failing to patch systems, using weak passwords, and opening unknown email attachments. The document advocates adopting a defense in depth approach with multiple layers of security controls at different levels to still provide protection even if one control fails.