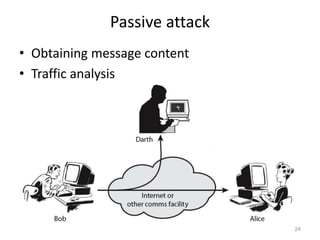
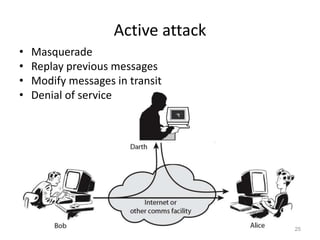
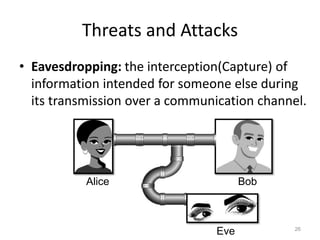
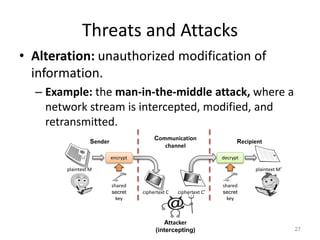
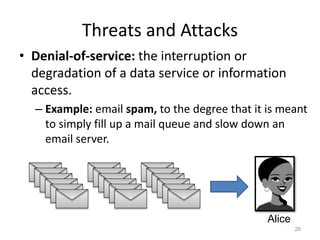
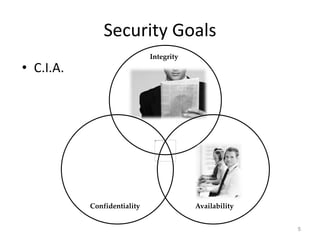
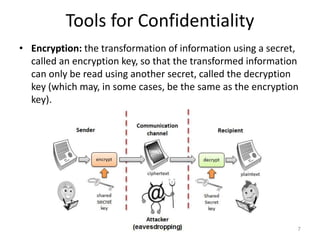
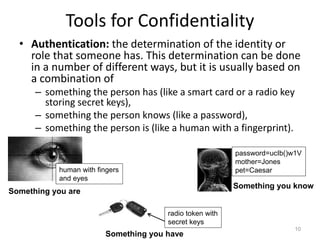
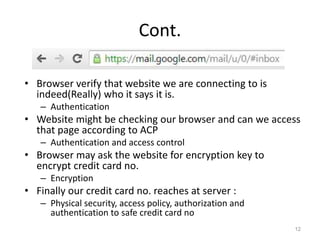
The document provides a comprehensive overview of information security, outlining key concepts such as the CIA triad (confidentiality, integrity, availability) and the principles of access control. It discusses the importance of security models, tools for ensuring confidentiality, and different types of security attacks and mechanisms. Additionally, it highlights various techniques for maintaining authenticity and anonymity within security frameworks.







![[Physical security]
• One can determine the letters by
– Listening to the recording of key stokes
• Possible to reconstruct the image of computer
screen
– By monitoring its electromagnetic radiations
– From video of blank wall the screen was shining
on
• Physical security is IS concept and should not
be taken for granted
13](https://image.slidesharecdn.com/ch01-introduction-240420115930-76020c34/85/informations_security_presentations-pptx-13-320.jpg)