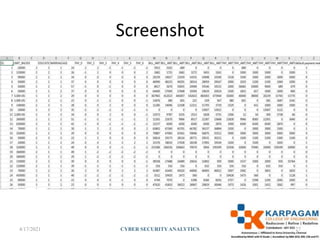
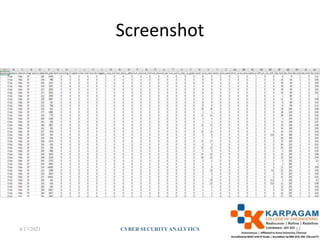
The document discusses cyber security analytics and its importance. It covers topics like cyber threats such as ransomware, malware, social engineering and phishing. It also discusses applications of data analytics in cyber security problems like SMS spam detection, credit card fraud detection, and intrusion detection. For each problem, it describes collecting and preprocessing relevant data and then applying machine learning algorithms like logistic regression, Bayesian classification to build models.