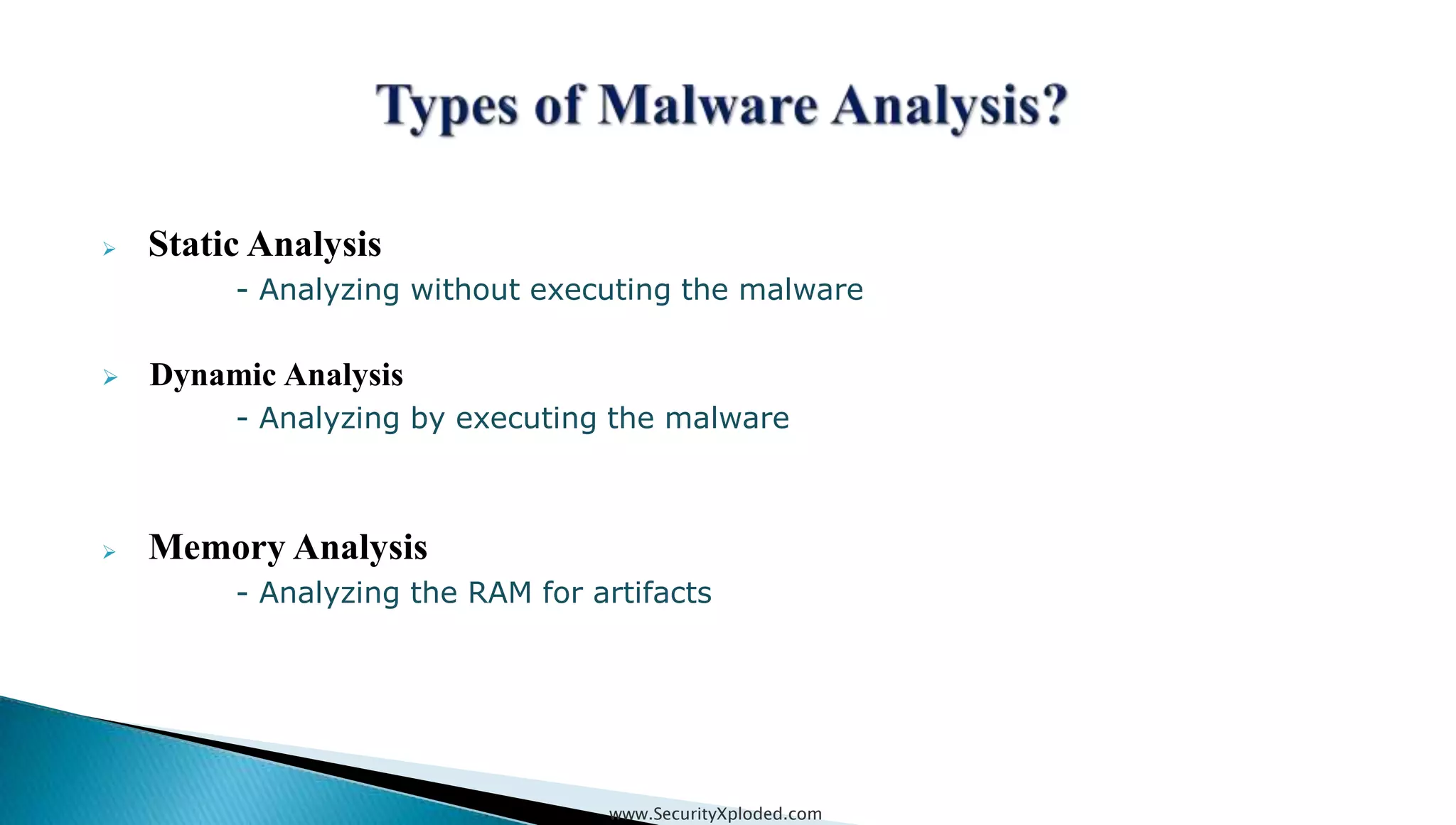
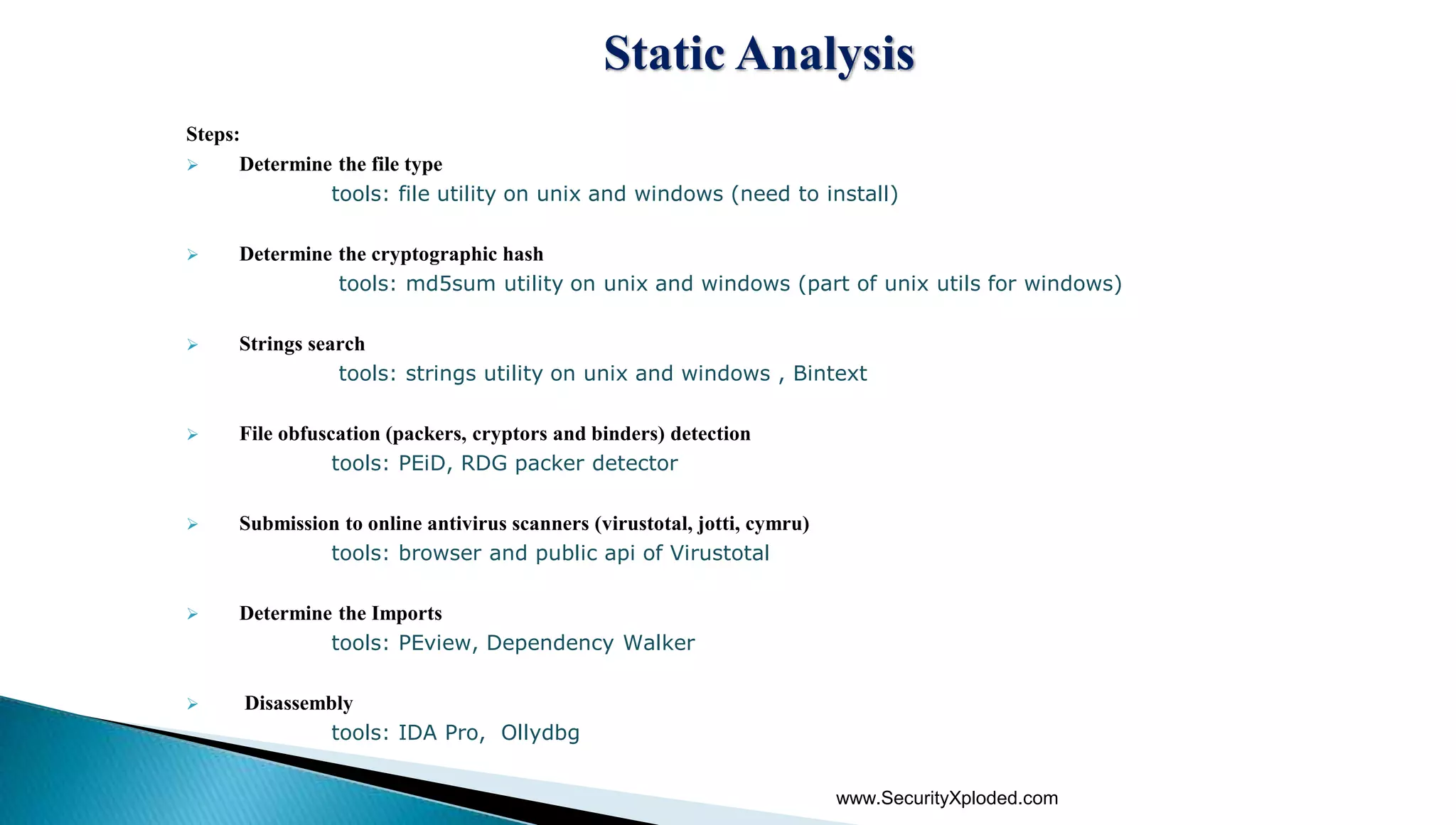
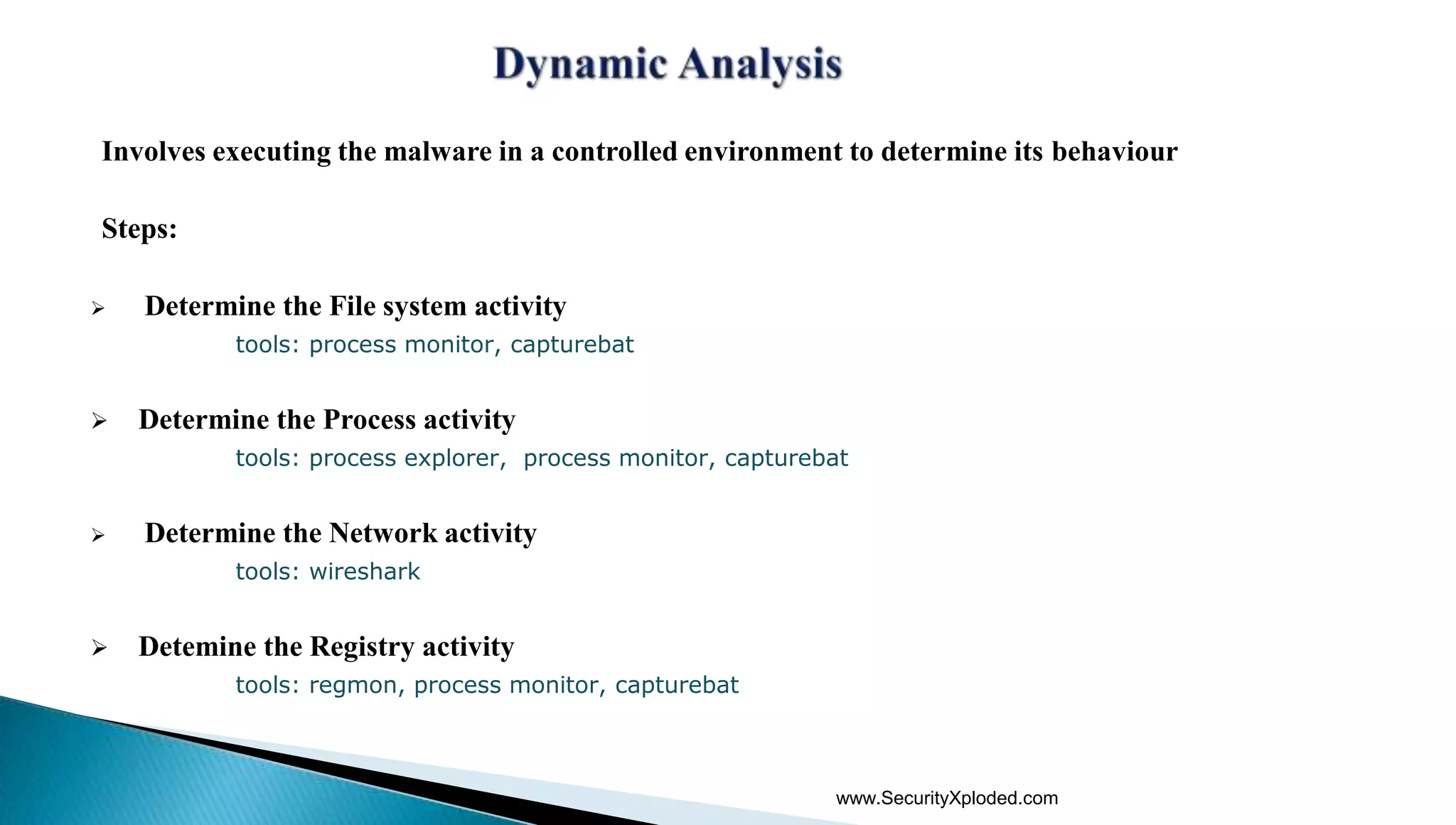
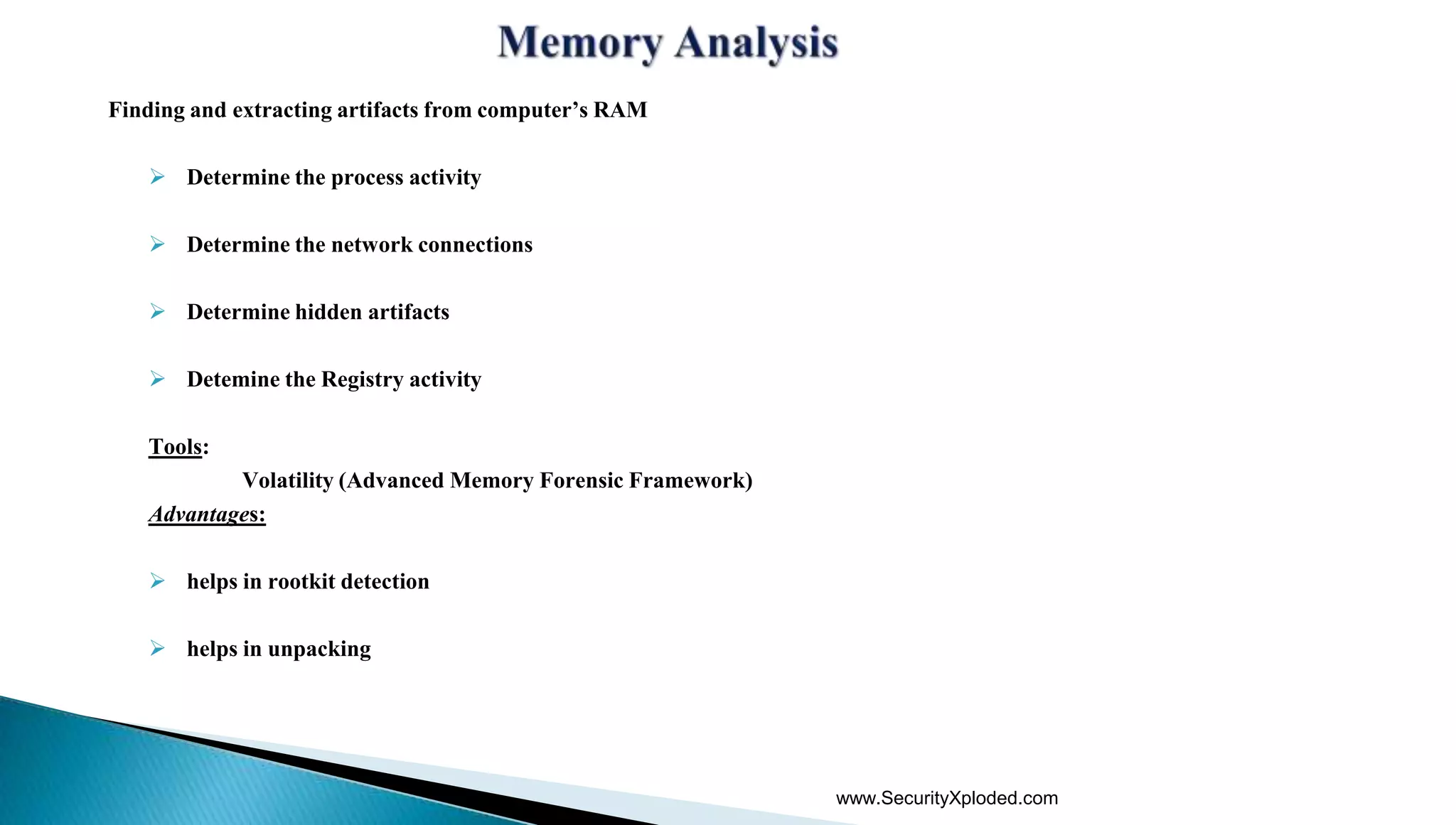
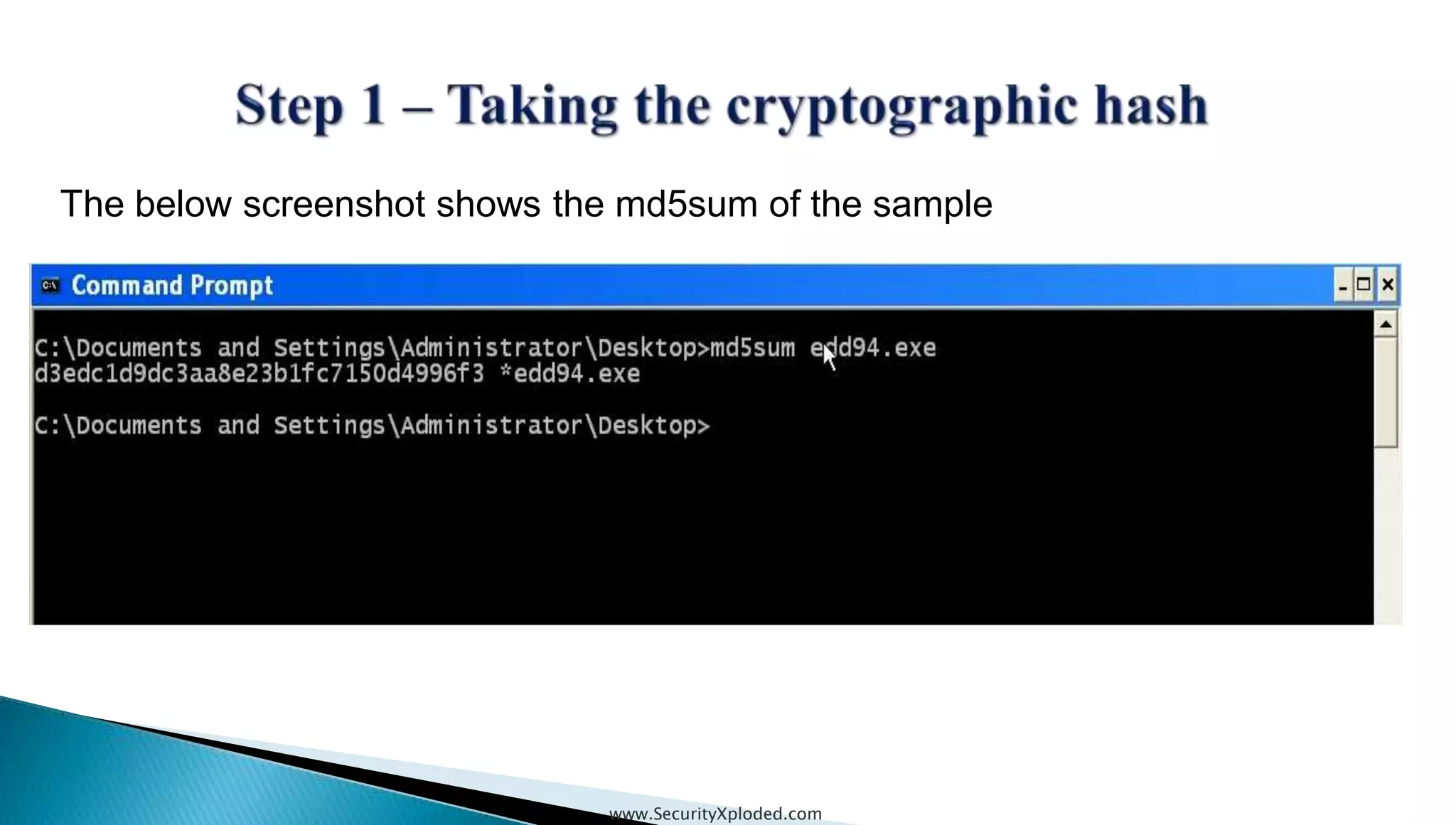
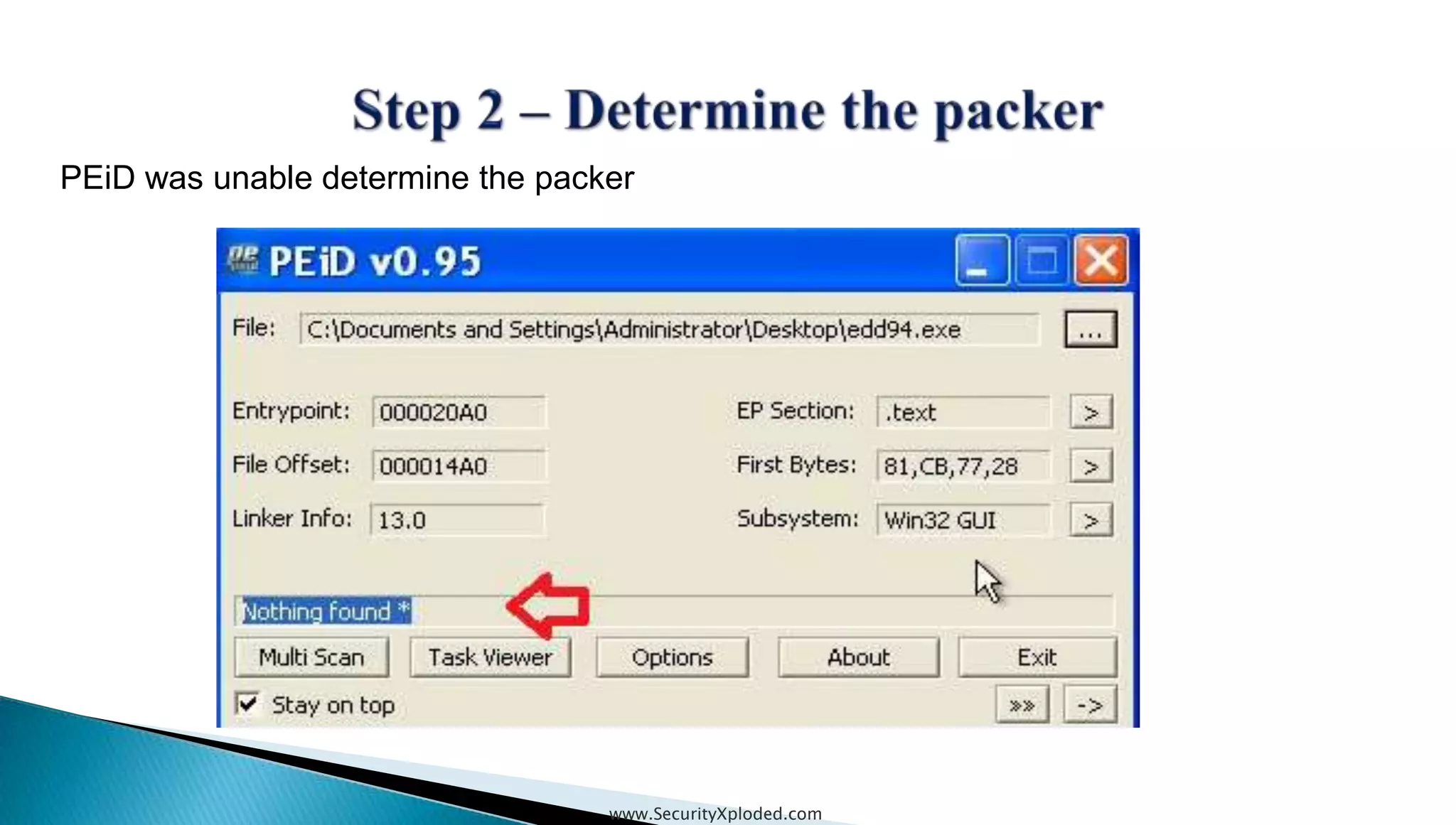
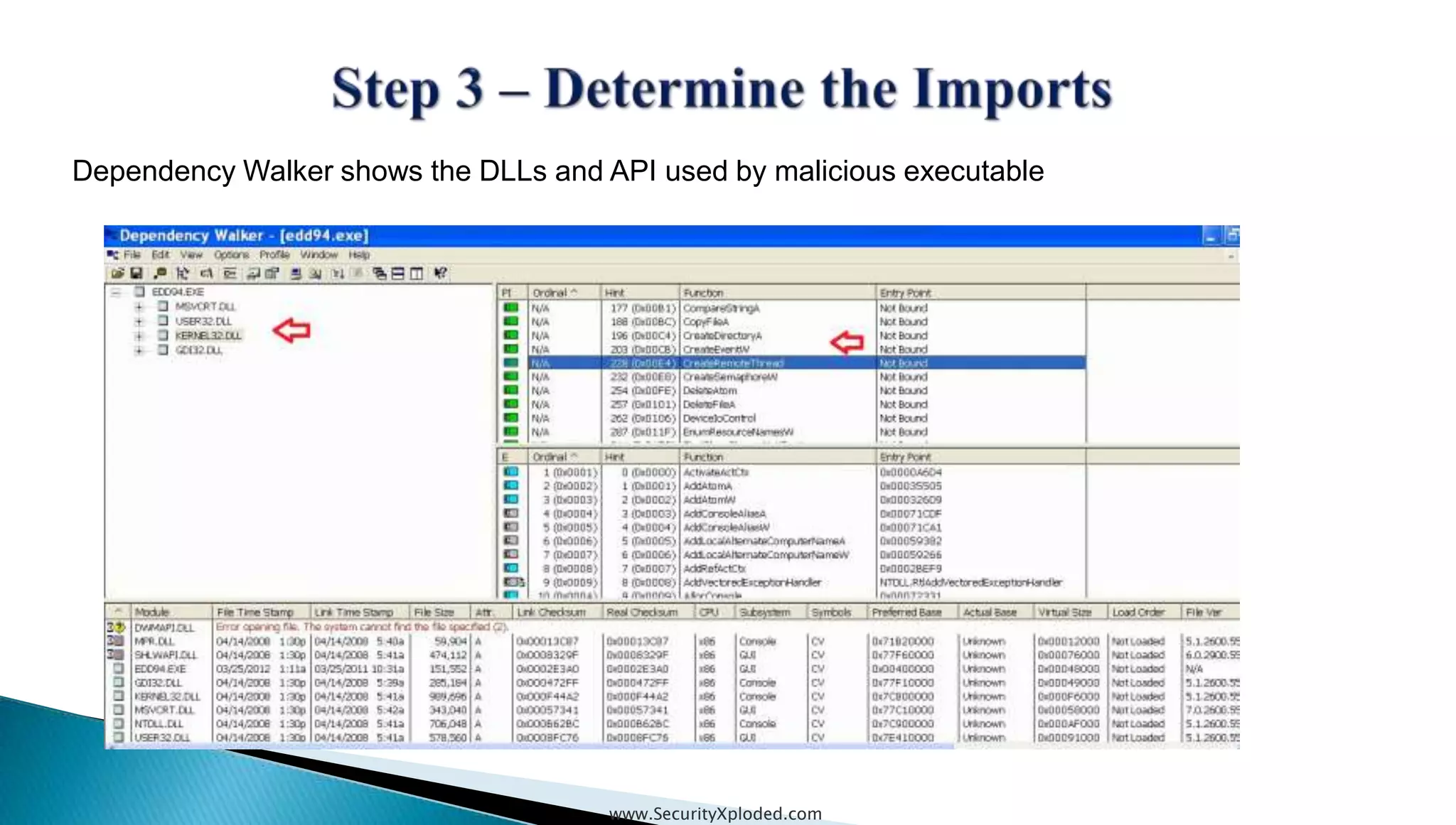
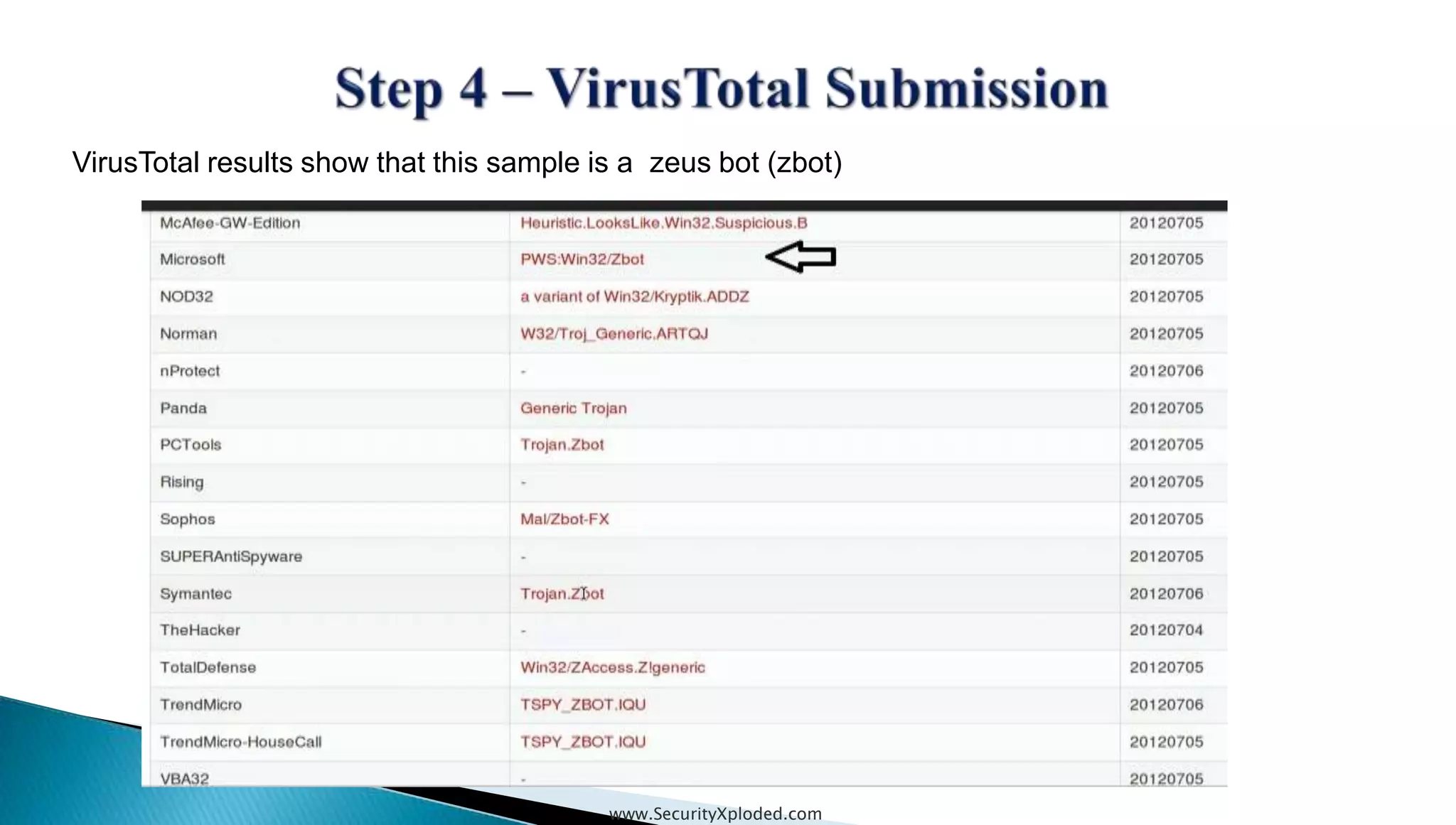
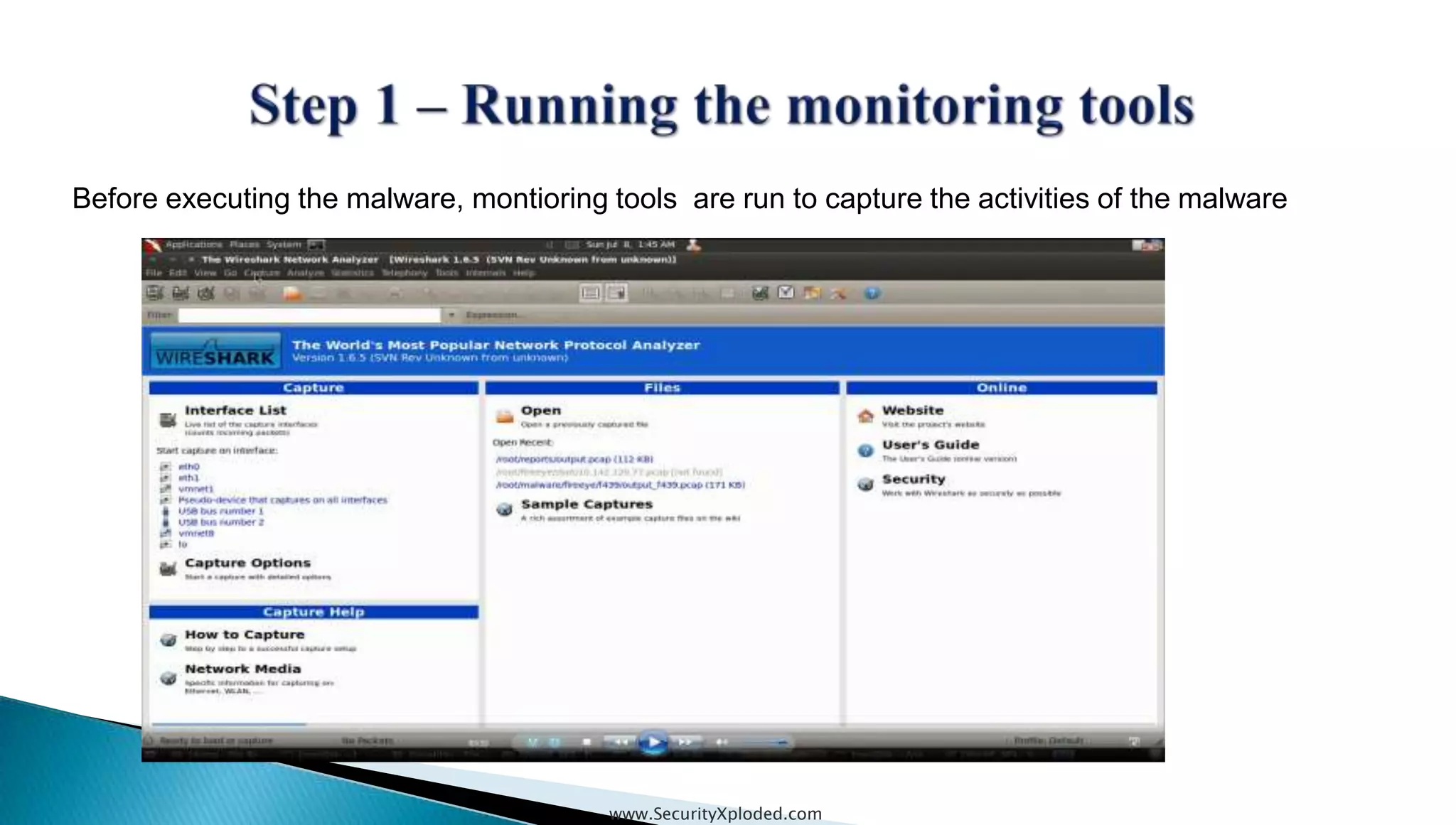
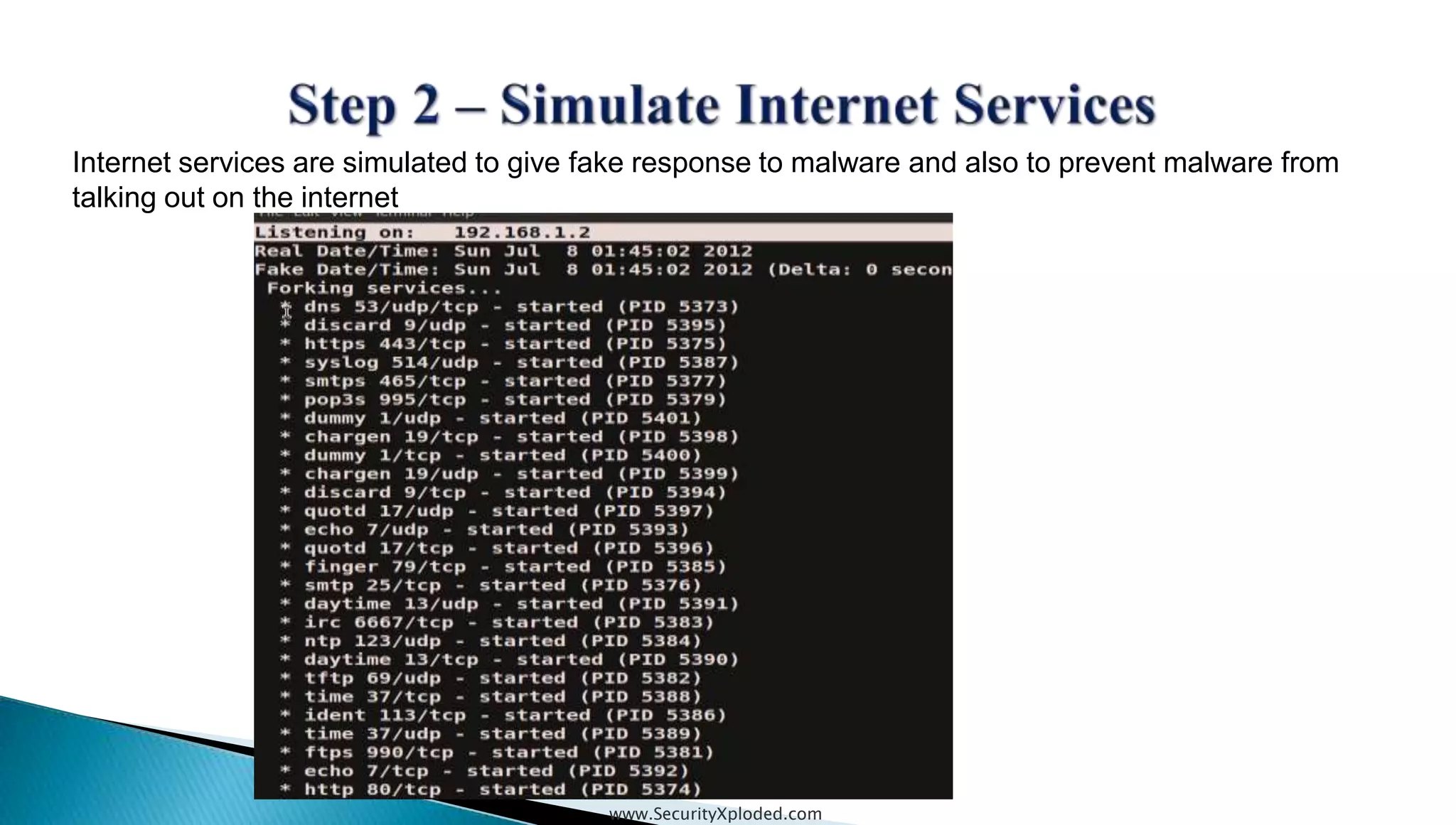
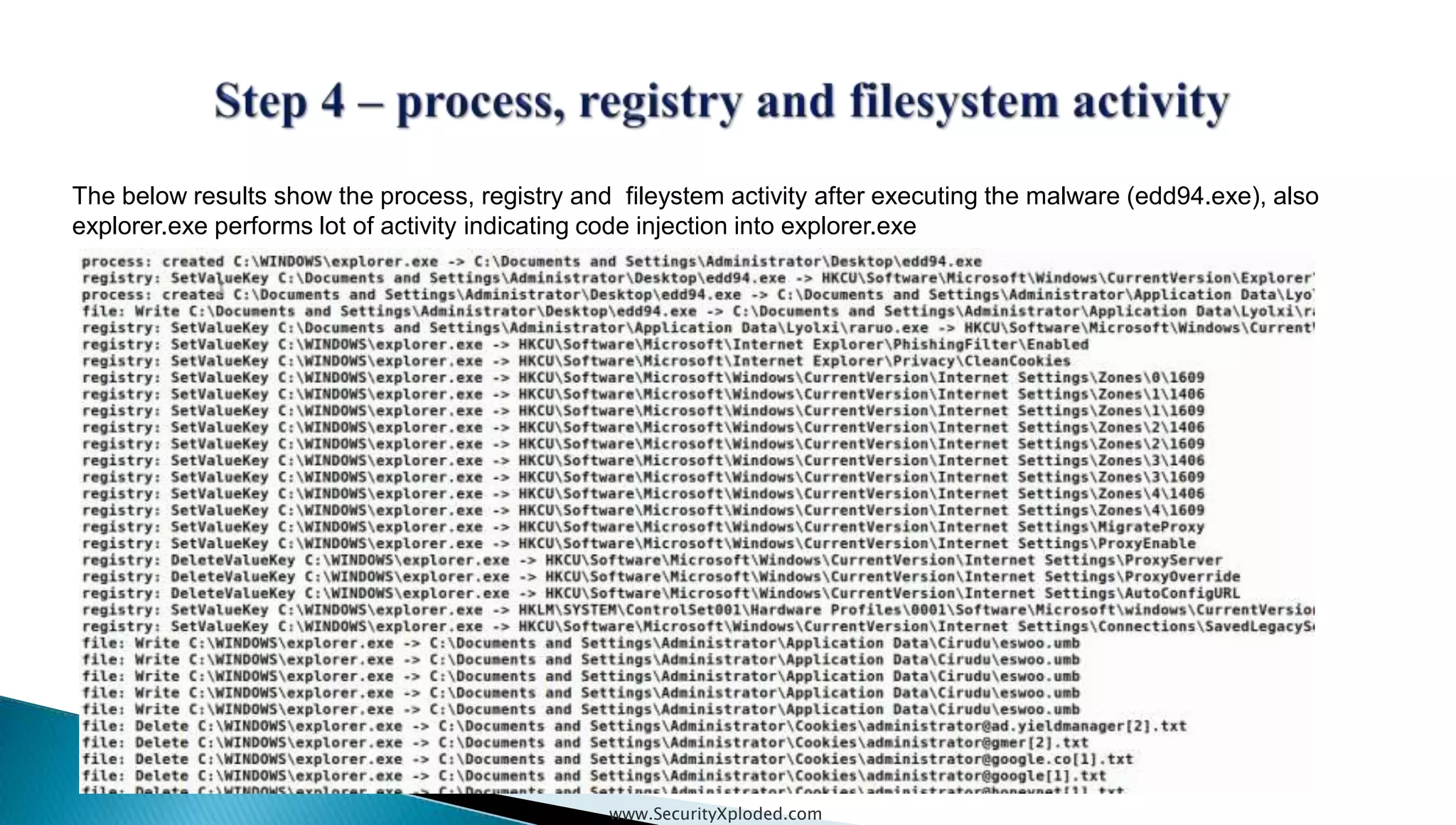
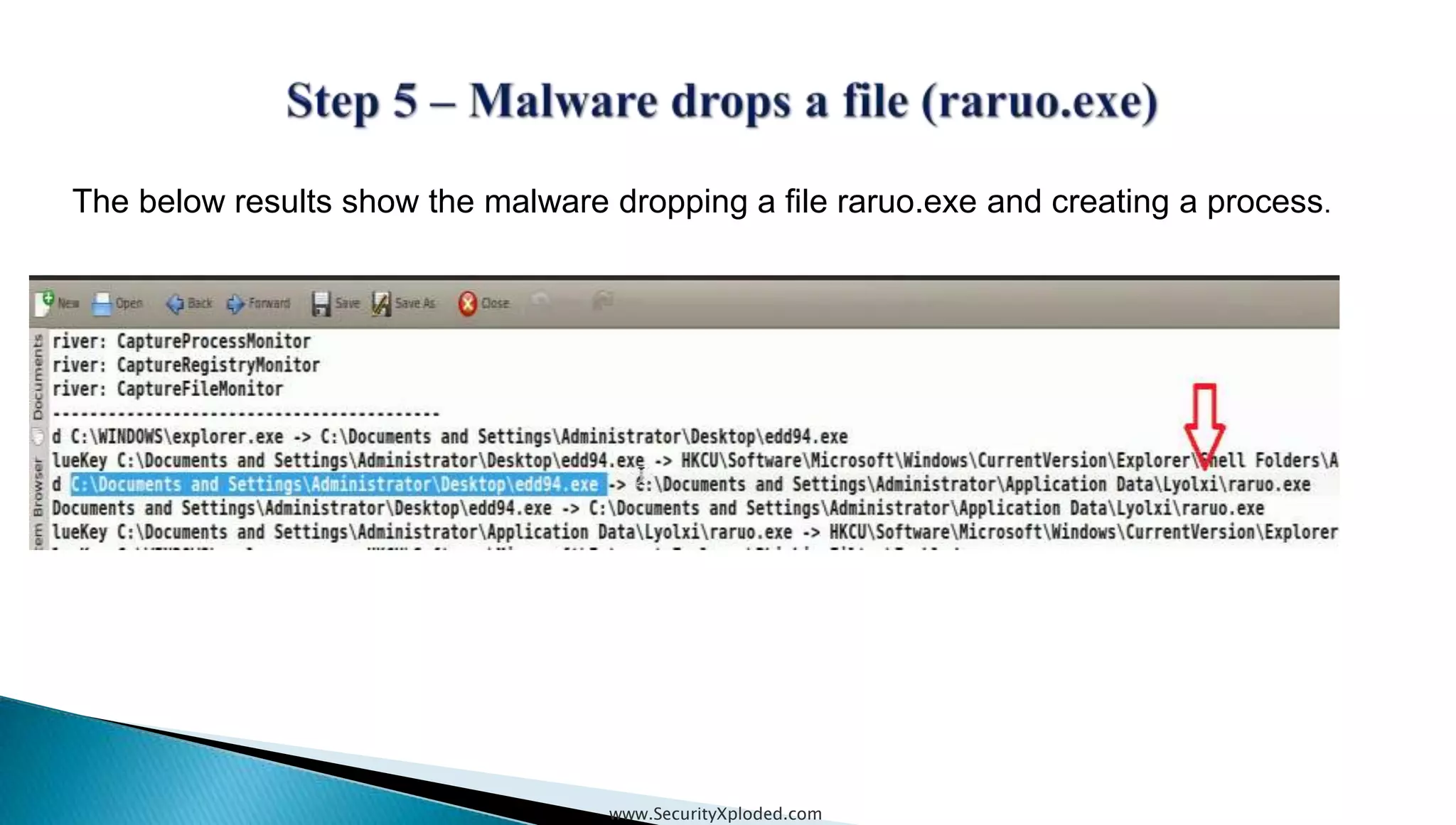
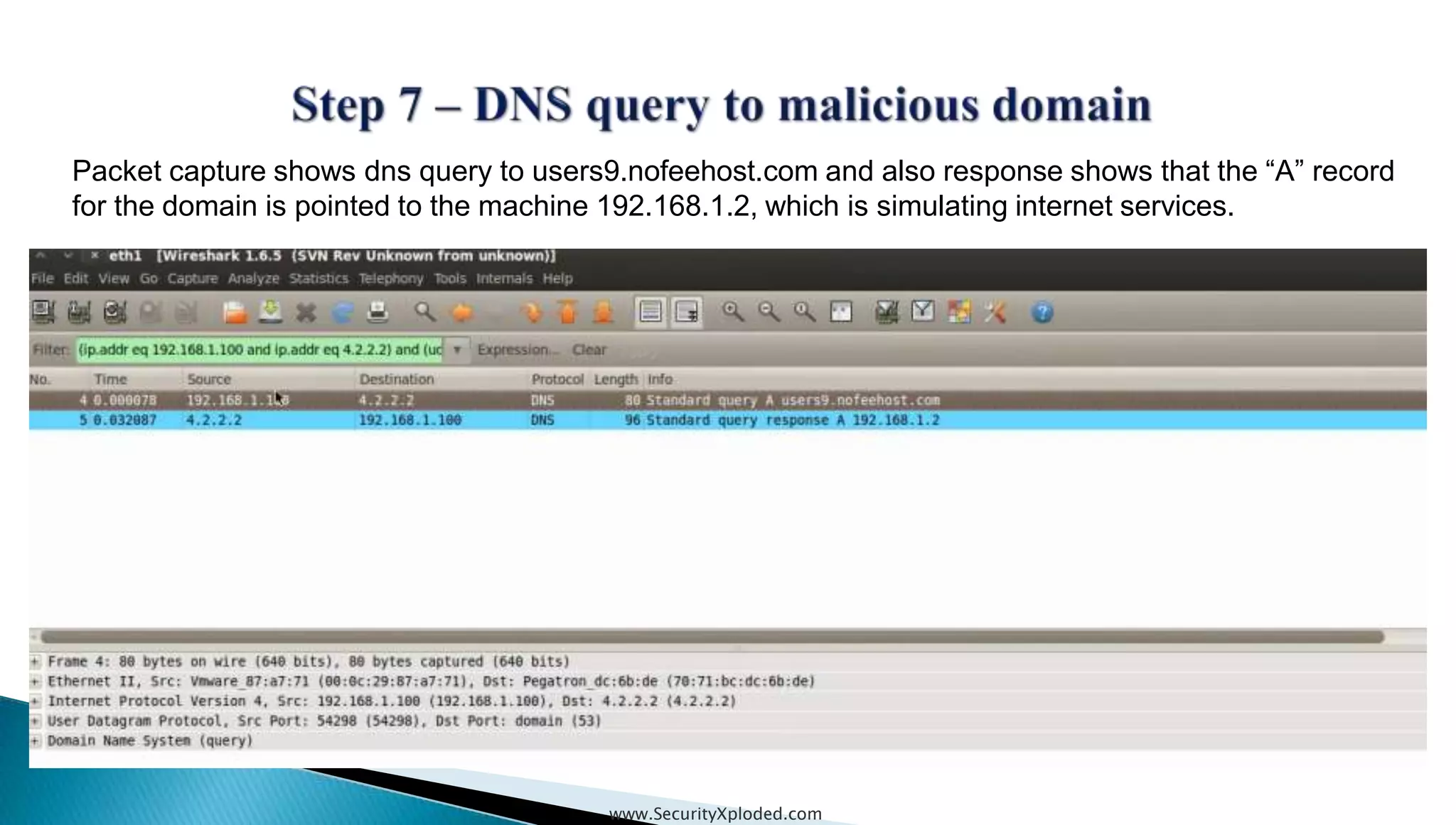
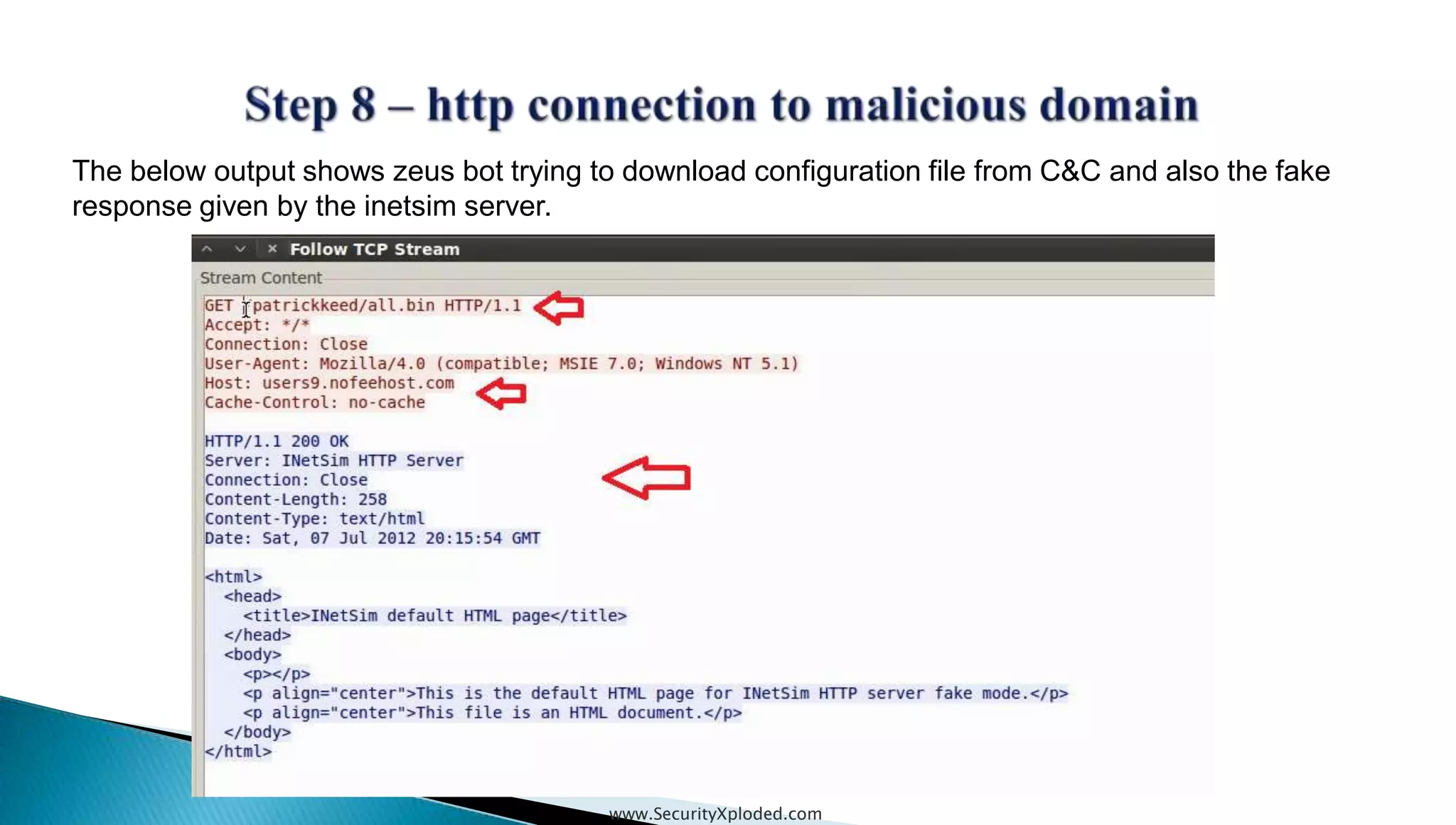
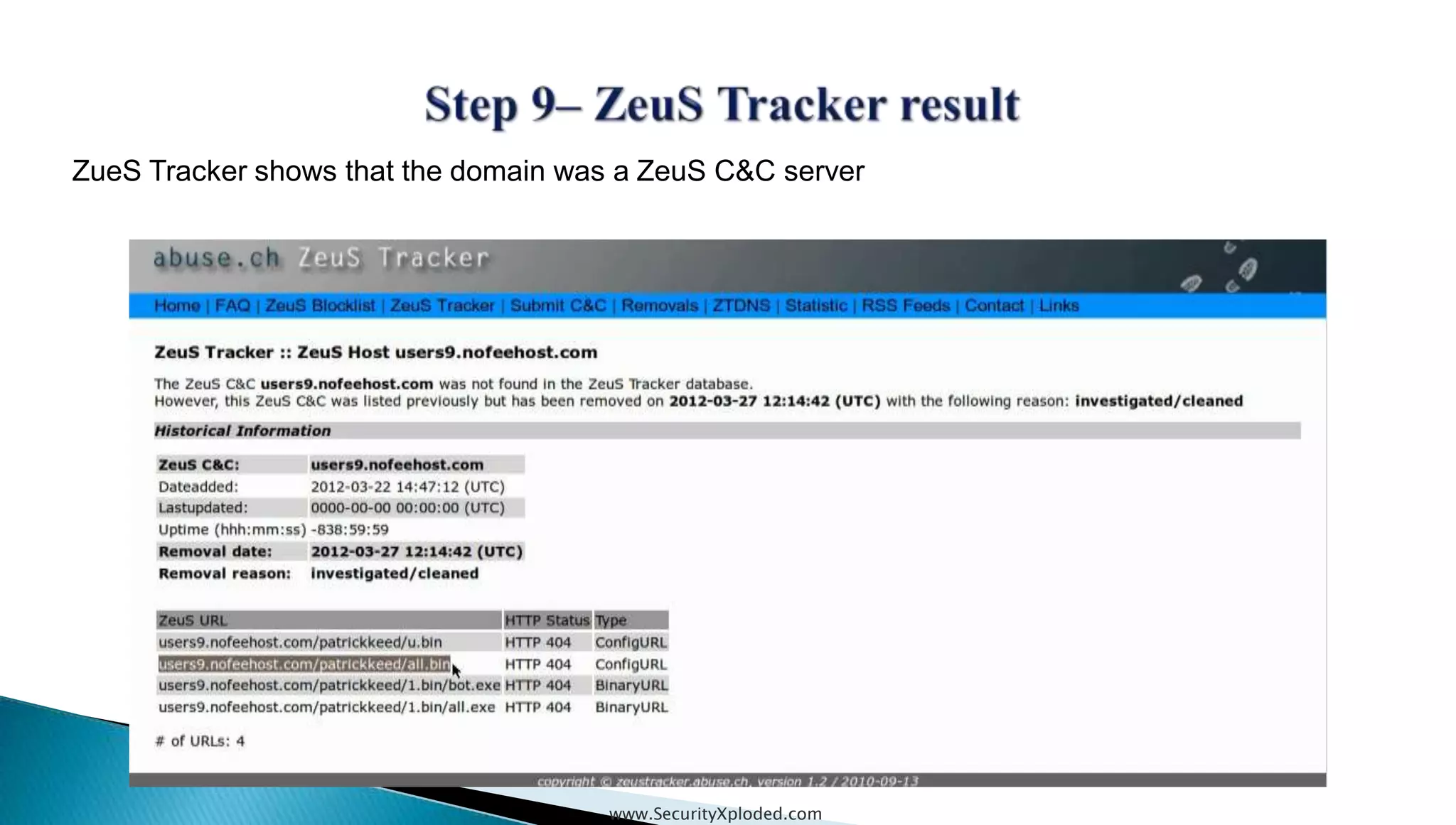
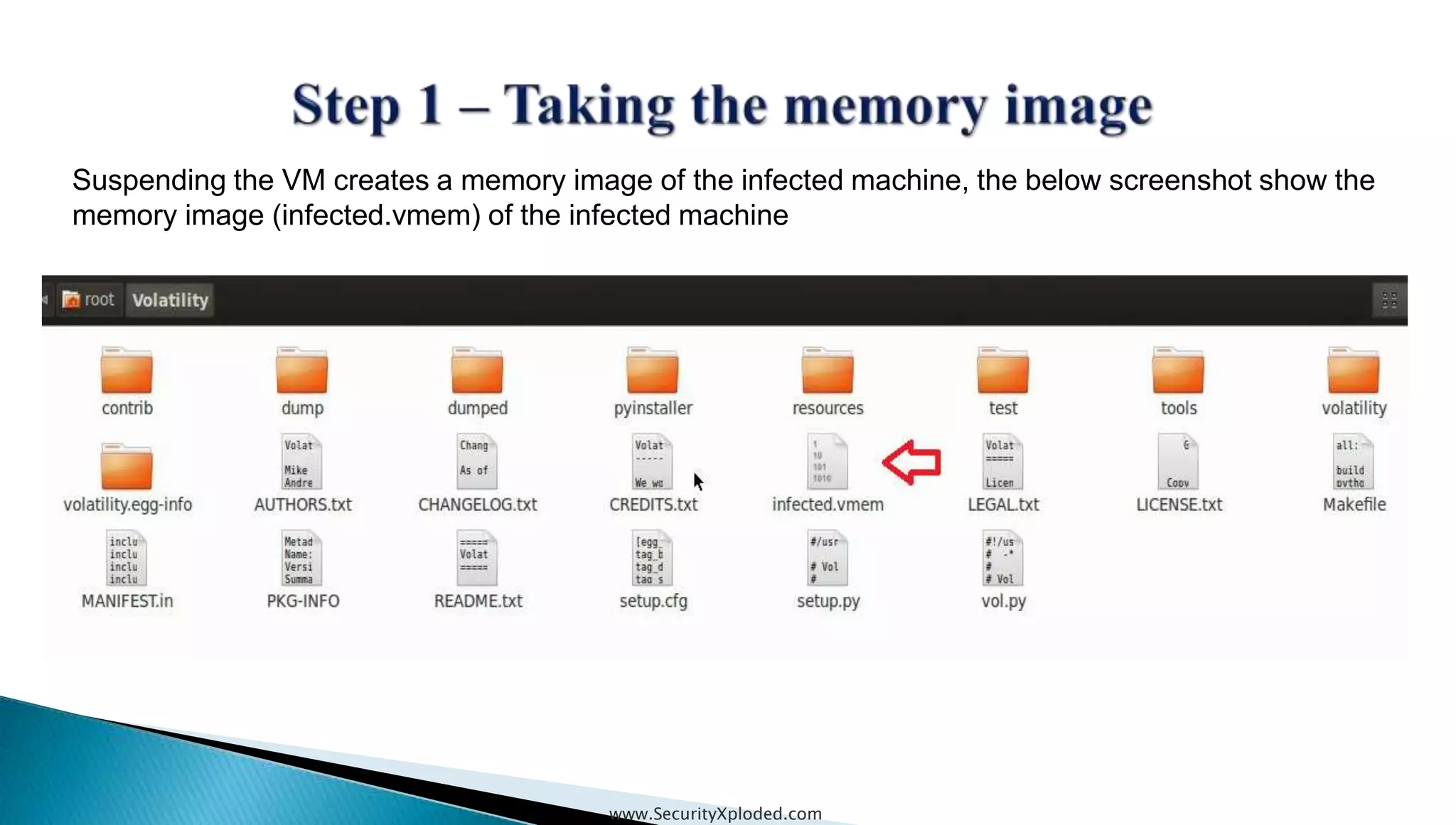
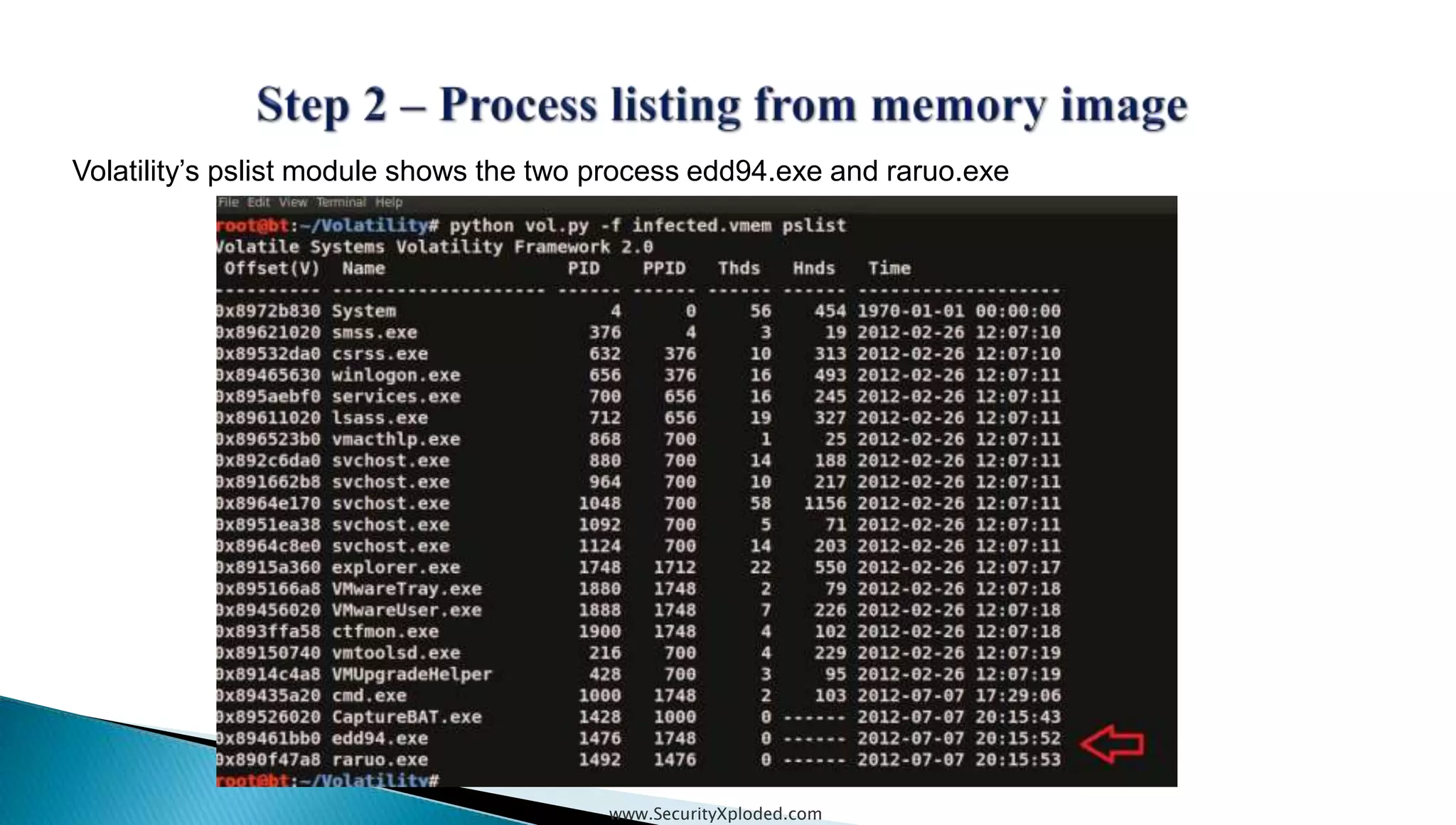
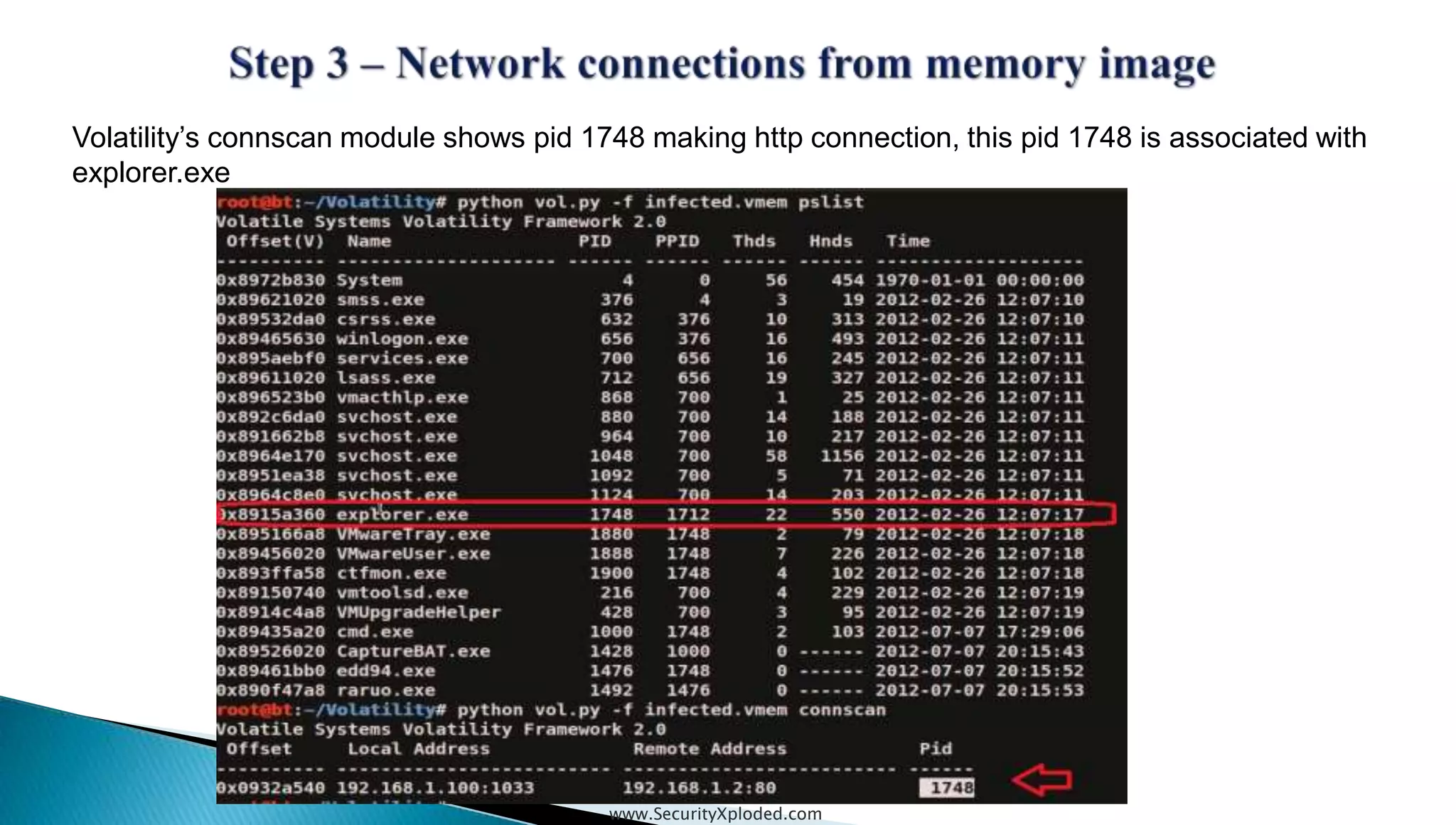
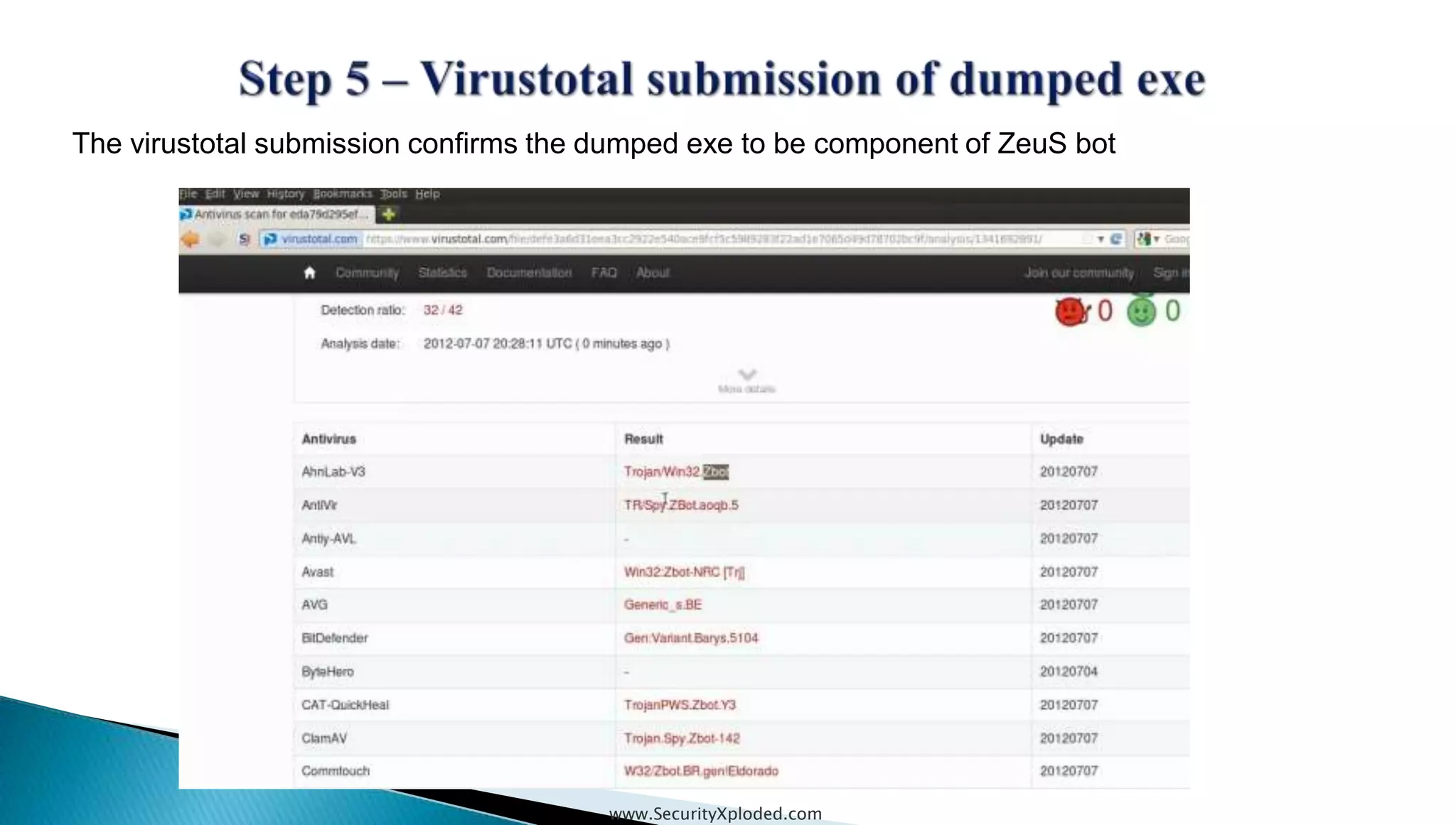
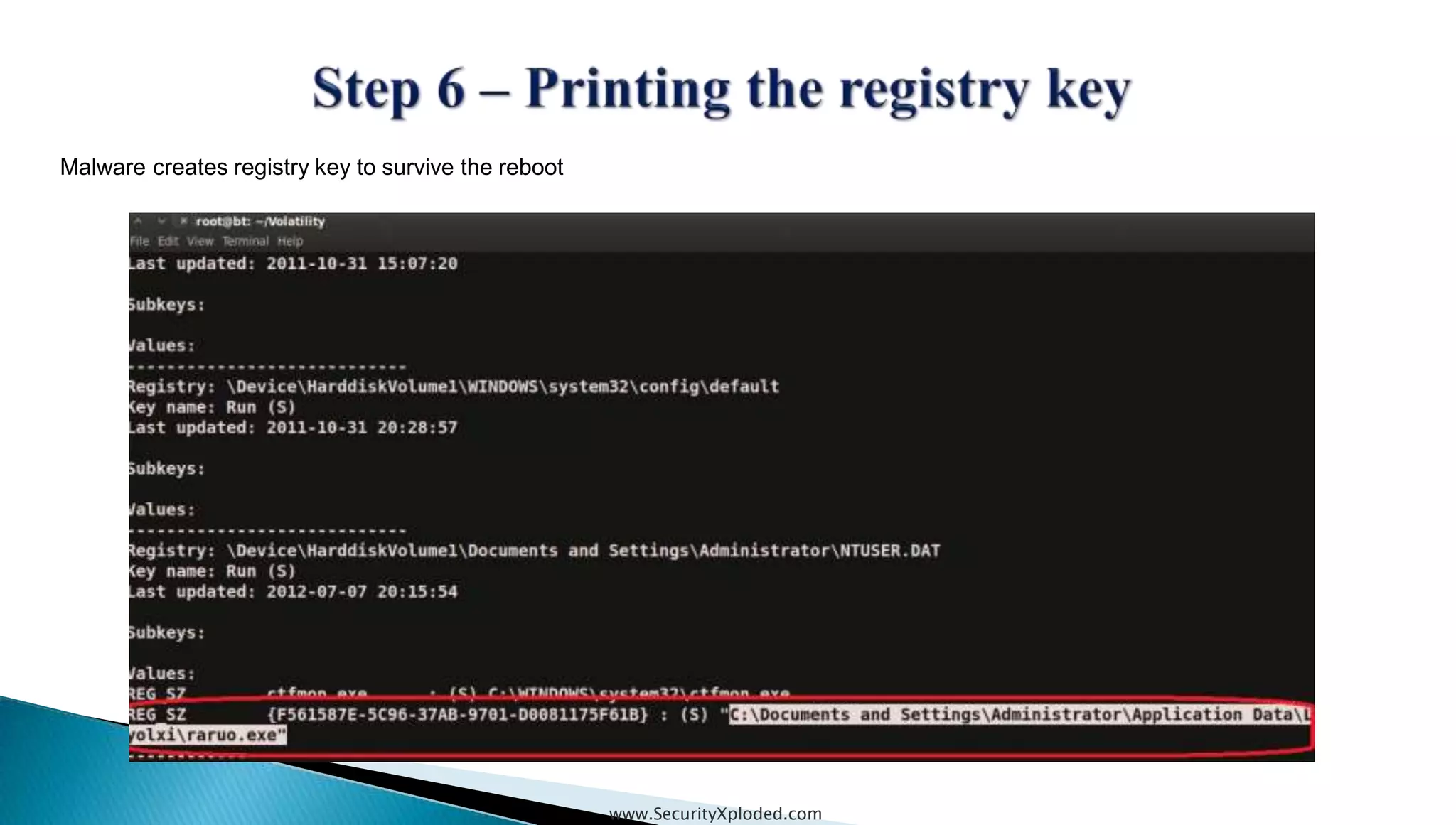
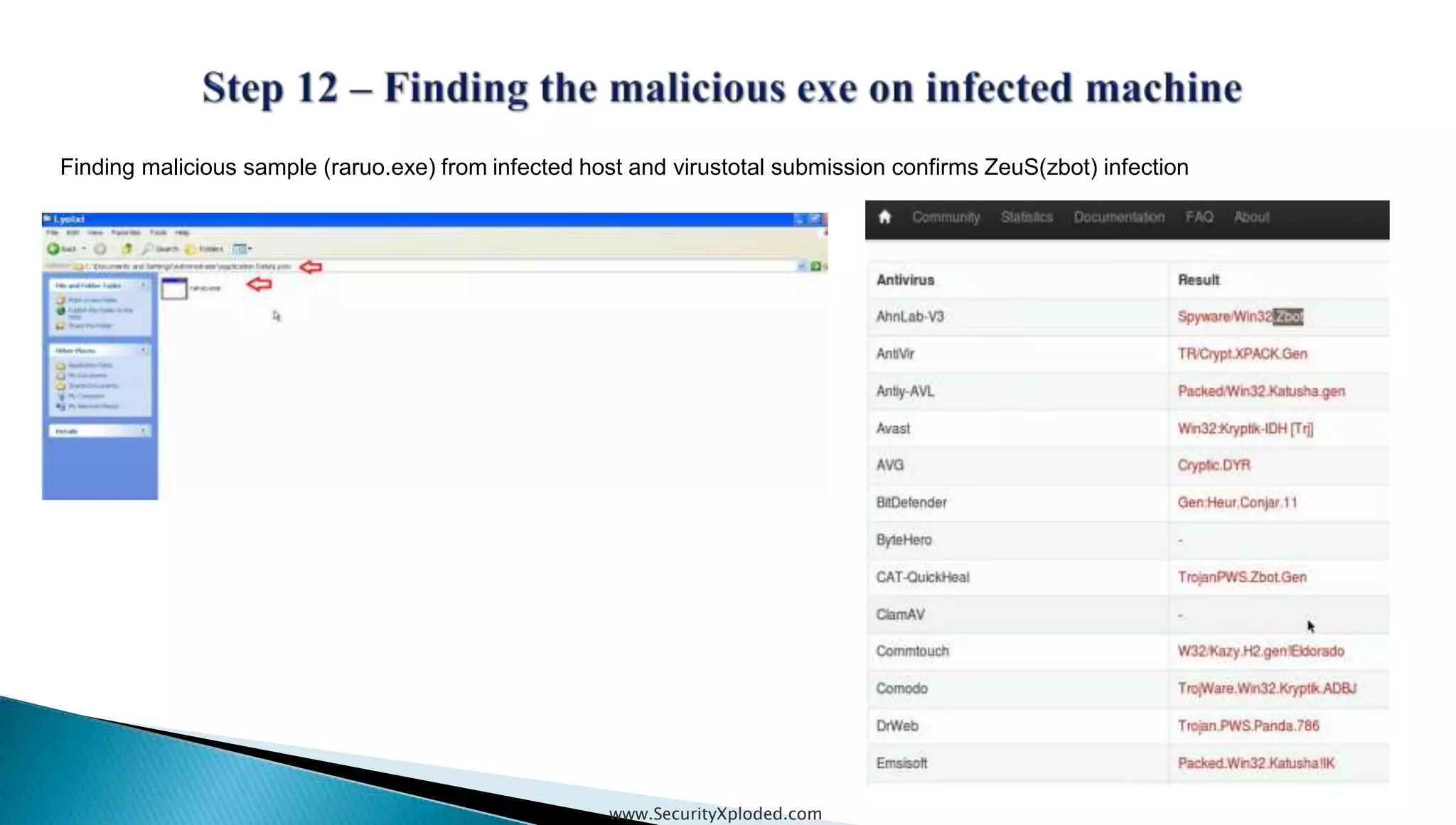
The document discusses malware analysis techniques including static analysis, dynamic analysis, and memory analysis. Static analysis involves examining a file without executing it to determine things like file type and cryptographic hash. Dynamic analysis involves executing malware in a controlled environment to observe its behavior, such as file system, process, registry, and network activity. Memory analysis examines a computer's RAM to find artifacts and reveal hidden processes, network connections, and registry modifications. The document provides examples of analyzing a Zeus bot sample using these techniques.