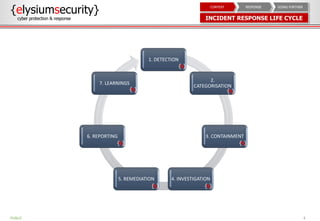
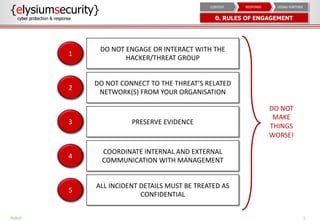
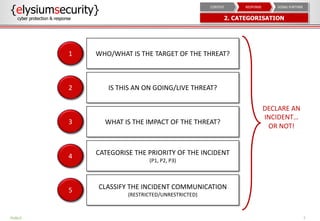
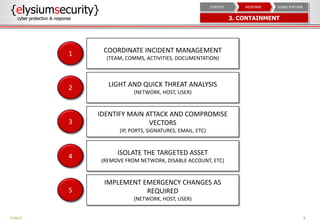
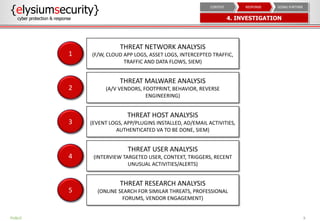
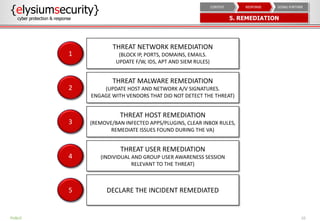
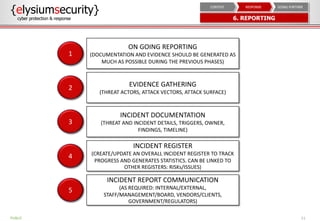
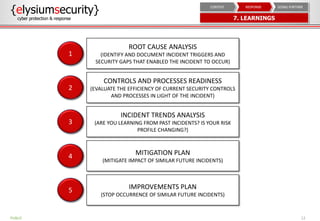
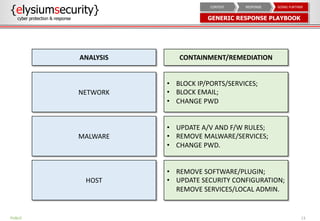
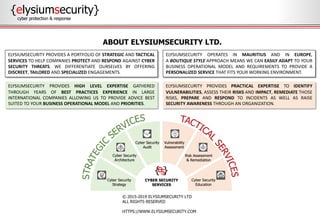
This document provides an overview of incident response procedures, including the incident response life cycle of detection, categorization, containment, investigation, remediation, reporting, and learnings. It outlines roles and responsibilities, communication processes, and generic response playbooks. Resources for incident response frameworks and standards are also referenced.