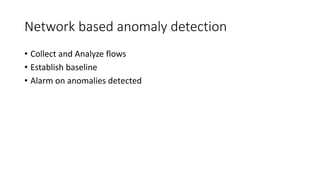
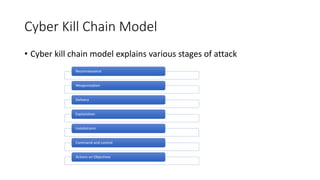
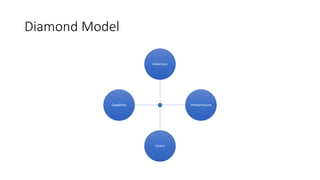
The document discusses the security challenges in device-to-device (D2D) communications, highlighting vulnerabilities such as eavesdropping and the need for enhanced safety alongside the fast communication provided by technologies like Bluetooth and Wi-Fi. It presents a network-based anomaly detection approach and defines various outcomes of security controls, while introducing two models: the Cyber Kill Chain and the Diamond Model for analyzing attacks. The Cyber Kill Chain outlines stages of an attack, emphasizing that attackers may not follow a strict sequence.