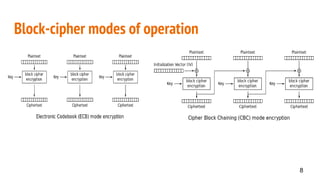
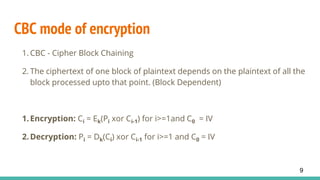
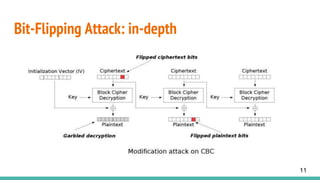
This document discusses CBC (Cipher Block Chaining) mode of encryption, explaining its vulnerabilities and the specifics of a bit-flipping attack. The bit-flipping attack is demonstrated with an example that circumvents HTTP session tokens, allowing unauthorized access. Preventive measures against such attacks include verifying that a random string prepended during encryption remains consistent after decryption.








![The XORing
A = P xor BlockCipherDecryption(B)
A[n] = P[n] xor BlockCipherDecryption(B)[n]
BlockCipherDecryption(B[n]) = A[n] xor P[n] ----> Fixed
A[n] = PD xor (A[n] xor PA) (Plaintext value
desired - PD)
or A[n] = A[n] xor (PD xor PA) (Actual plaintext value -
PA)
14](https://image.slidesharecdn.com/bitflippingattackonaes-cbc-ashutoshahelleya-170803060236/85/Bit-flipping-attack-on-aes-cbc-ashutosh-ahelleya-14-320.jpg)


