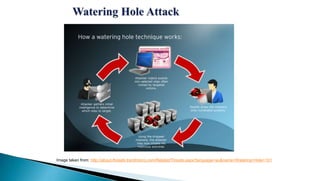
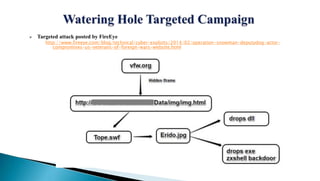
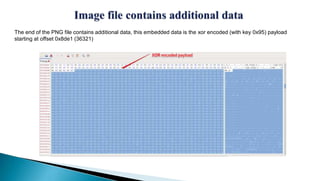
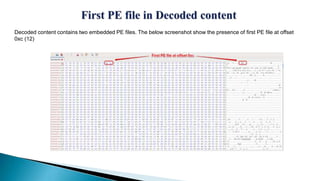
The document describes a watering hole attack campaign that targeted military websites. It used a zero-day exploit in Internet Explorer 10 along with a malicious Flash file to download an image file containing hidden payload data. This payload contained two malware files - a DLL and a ZxShell backdoor executable. The backdoor made DNS queries to malicious domains and attempted to connect on port 443. The content is provided without warranty and solely represents the author's views.