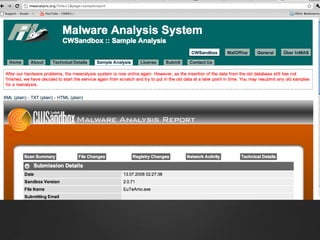
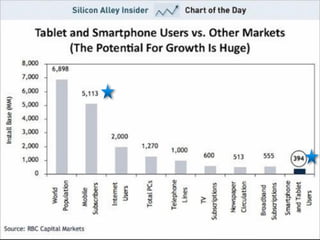
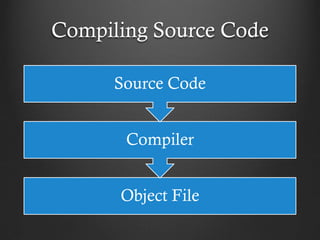
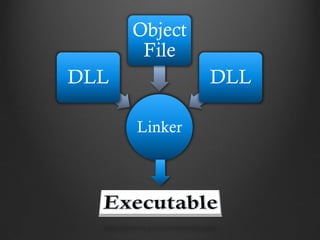
This document provides an introduction to malware analysis through a presentation. It discusses key concepts like Zeus malware, behavioral analysis through tools like NetworkMiner and Wireshark, reverse engineering malware using tools like OllyDbg, and submitting samples to VirusTotal for analysis. The presentation emphasizes setting up an analysis workstation, analyzing malware behavior on networks and systems, reverse engineering code to understand malware functionality, and using virtual environments and tools safely to explore malware without risking real systems. It provides examples of real malware like Zeus to illustrate analysis concepts and techniques.














































































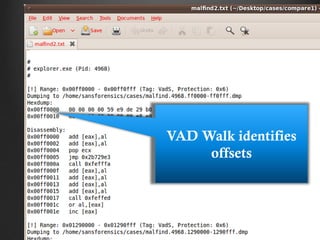
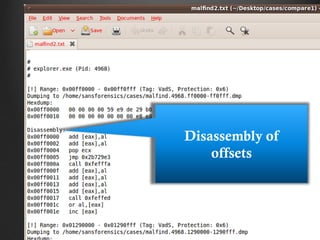












![Example Assembly
MOV AX, 47104
MOV DS, AX
MOV [3998], 36
INT 32
Each line is one CPU-level instruction](https://image.slidesharecdn.com/intro2malwareanalysisshort-130103001504-phpapp01/85/Intro2-malwareanalysisshort-124-320.jpg)
![Example Assembly
MOV AX, 47104
MOV DS, AX
MOV [3998], 36
INT 32
Tells the computer to copy the
number 47104 into the location AX](https://image.slidesharecdn.com/intro2malwareanalysisshort-130103001504-phpapp01/85/Intro2-malwareanalysisshort-125-320.jpg)