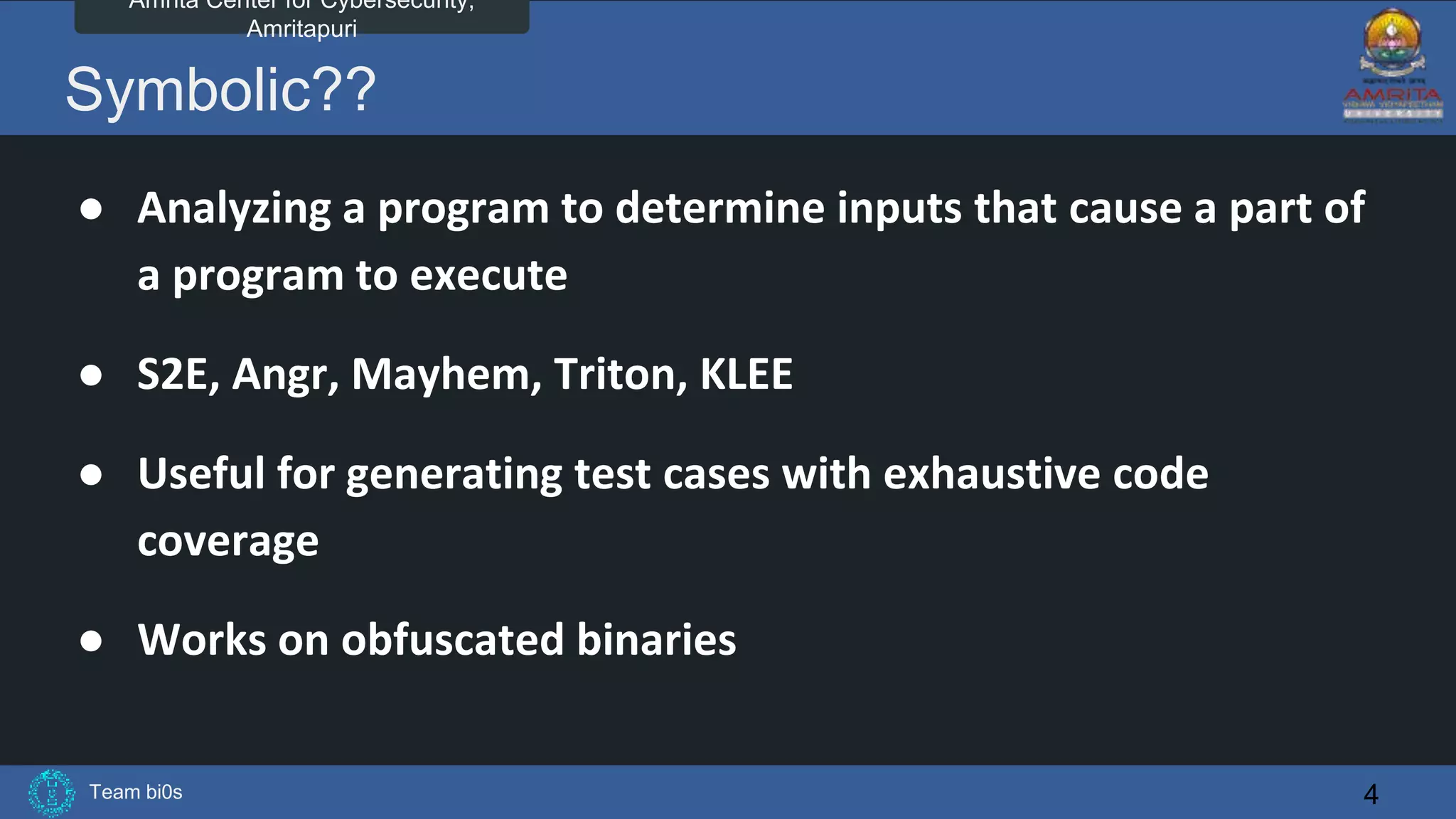
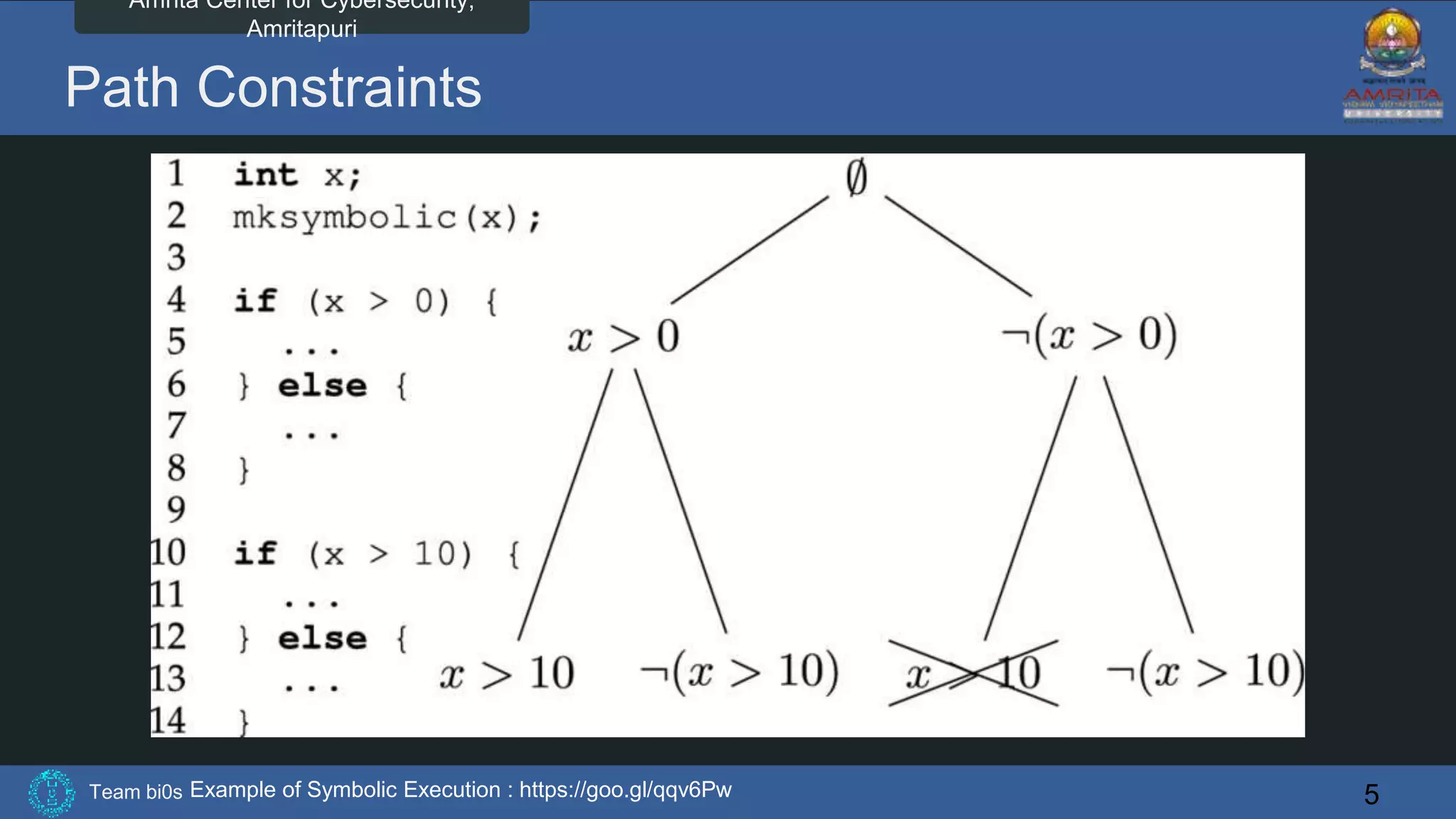
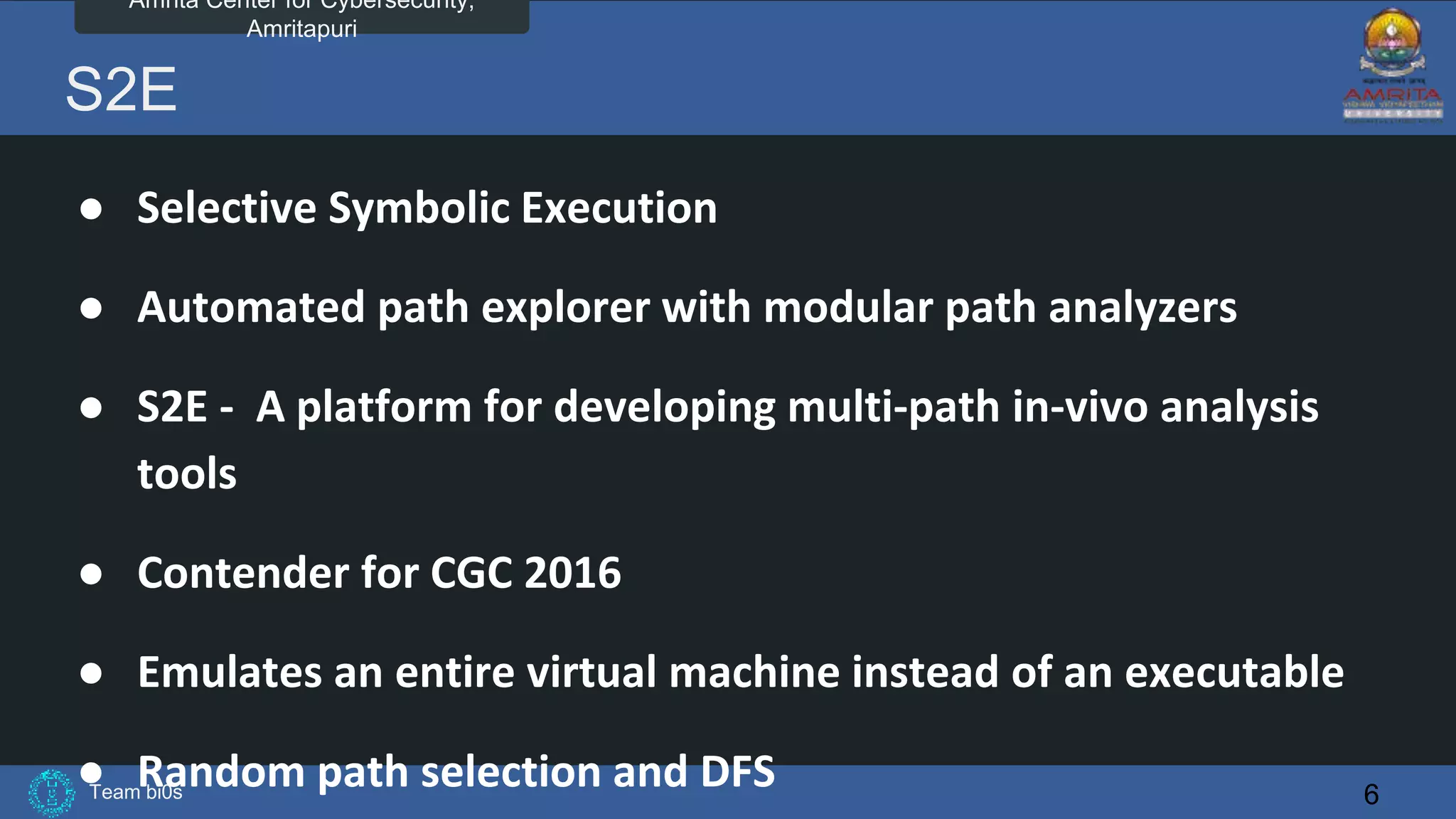
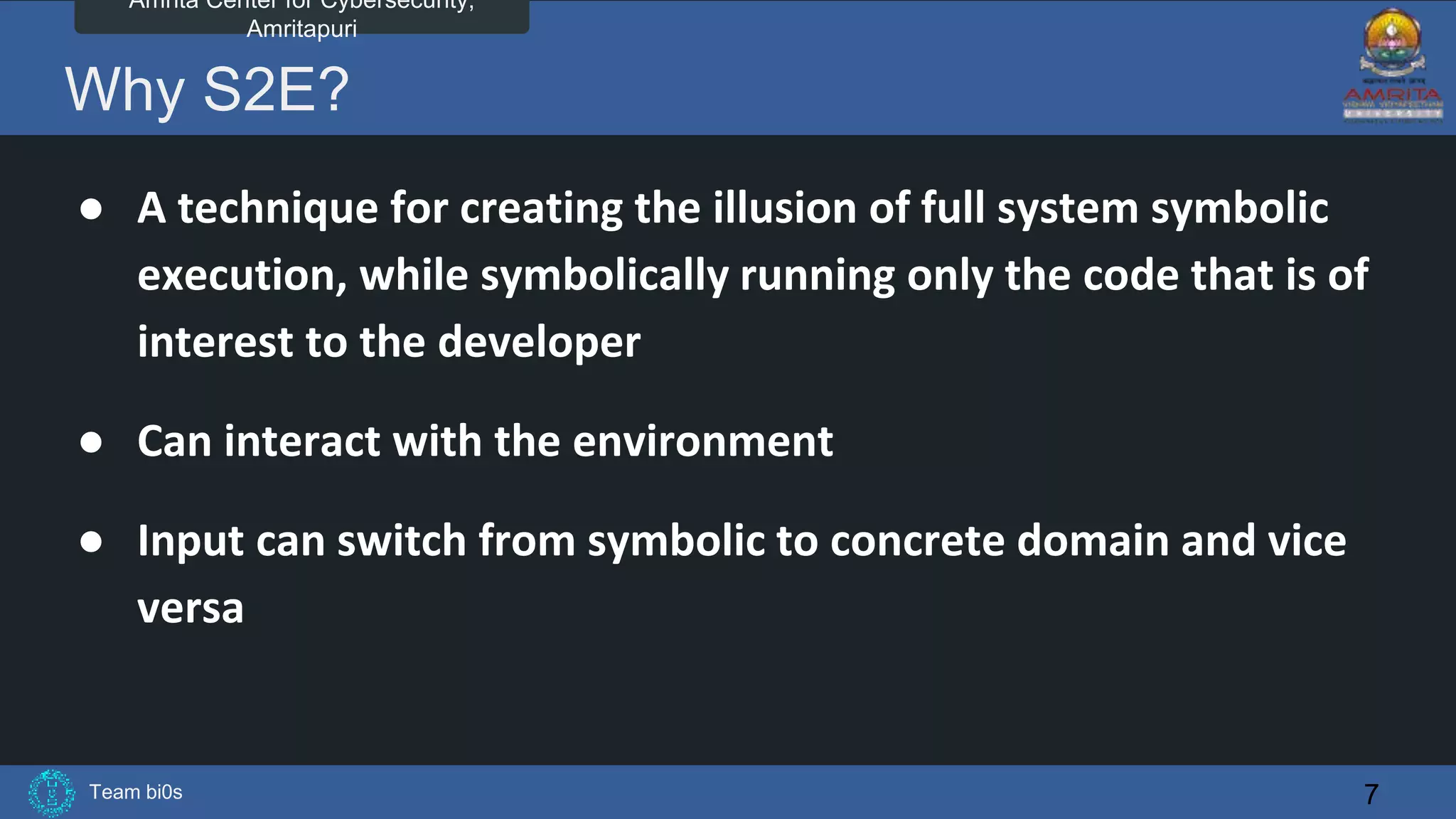
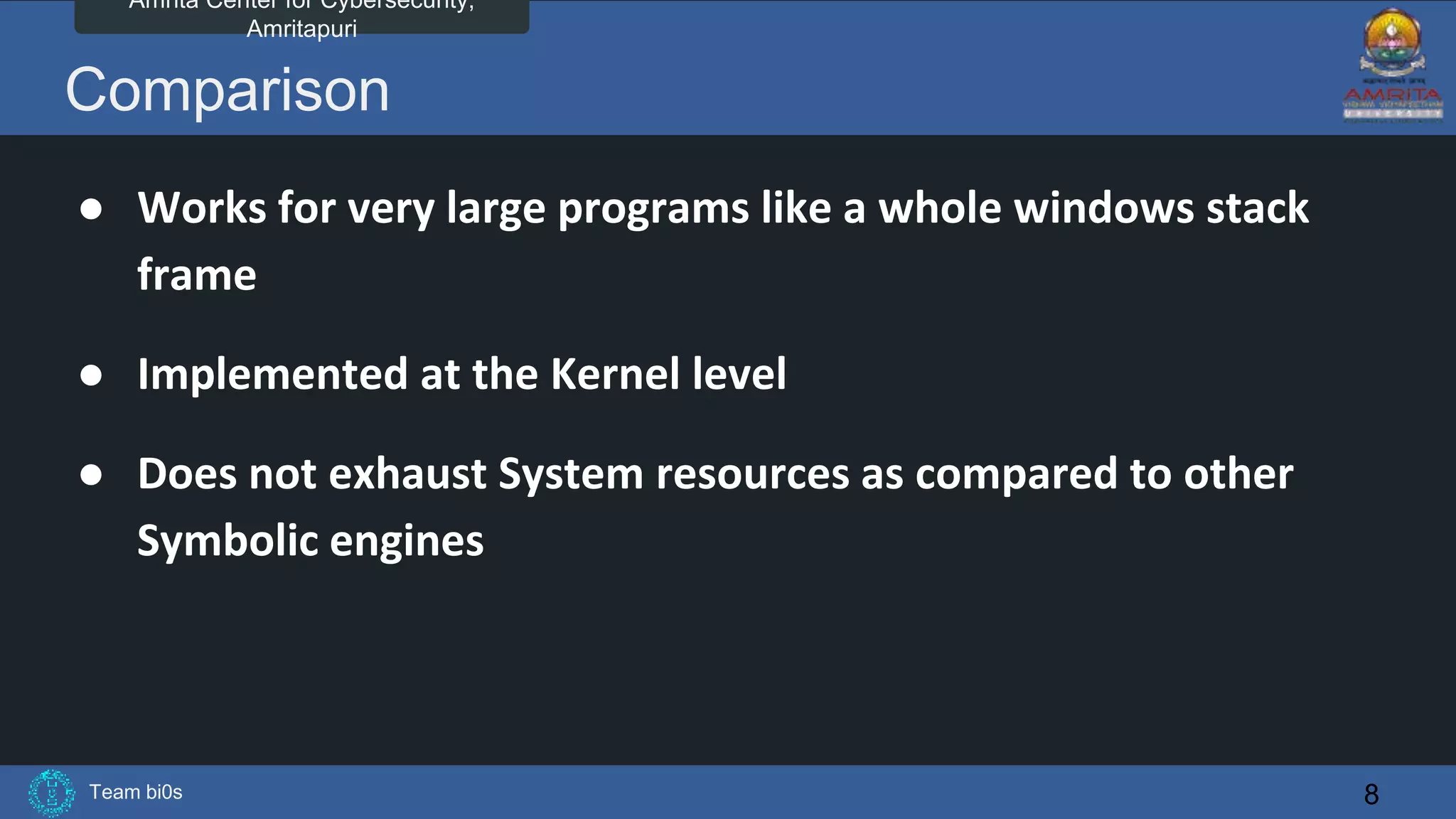
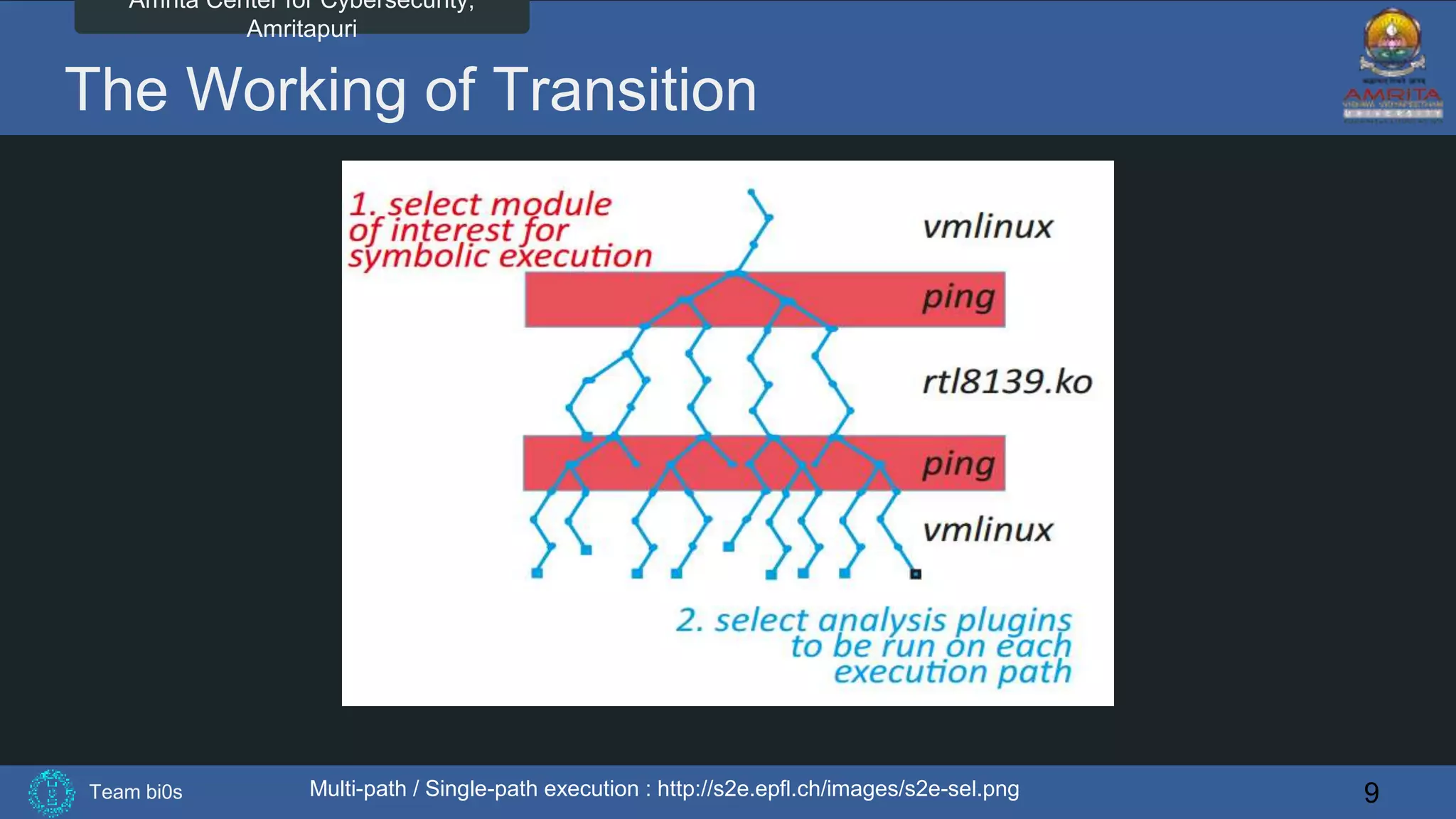
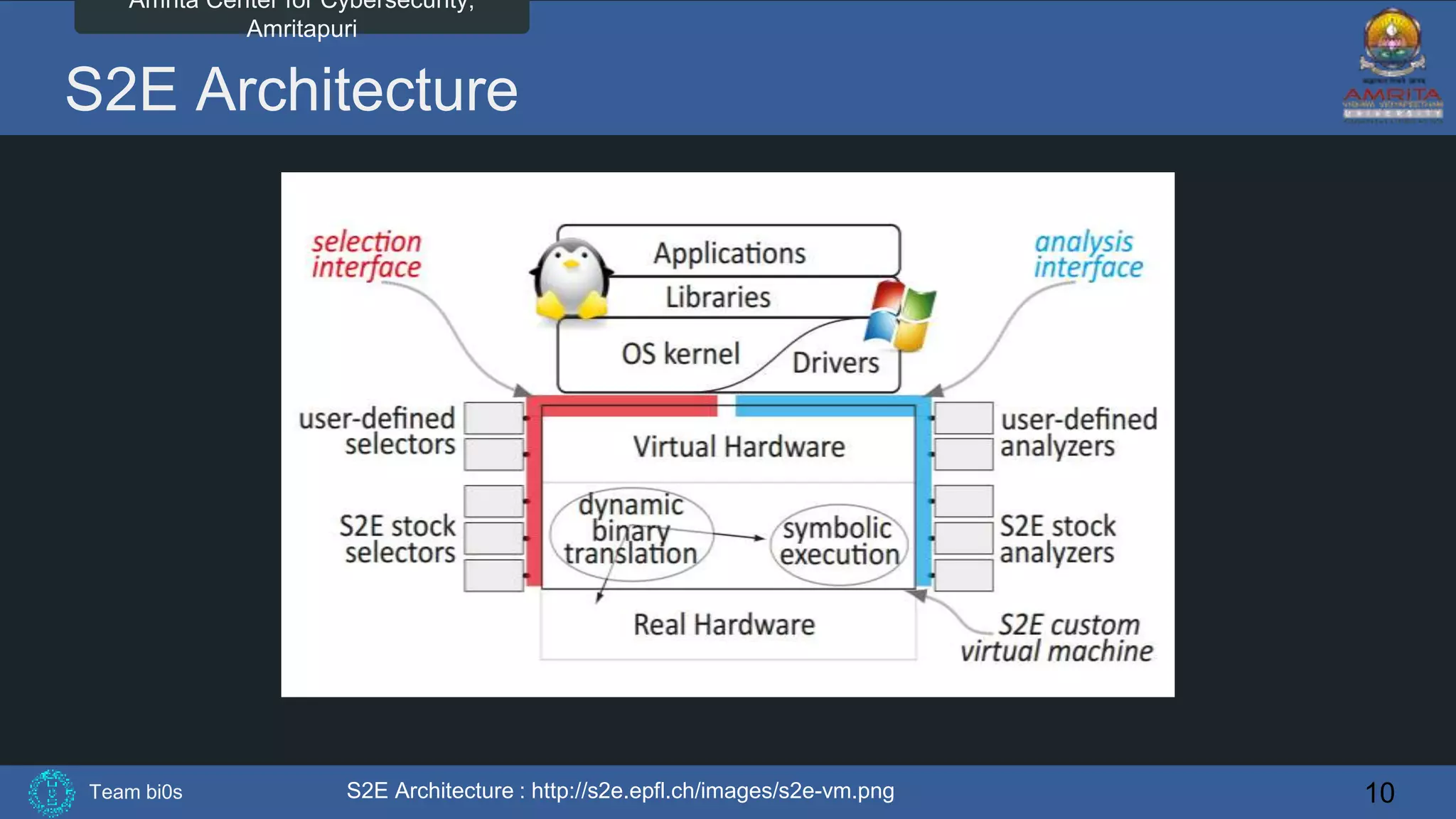
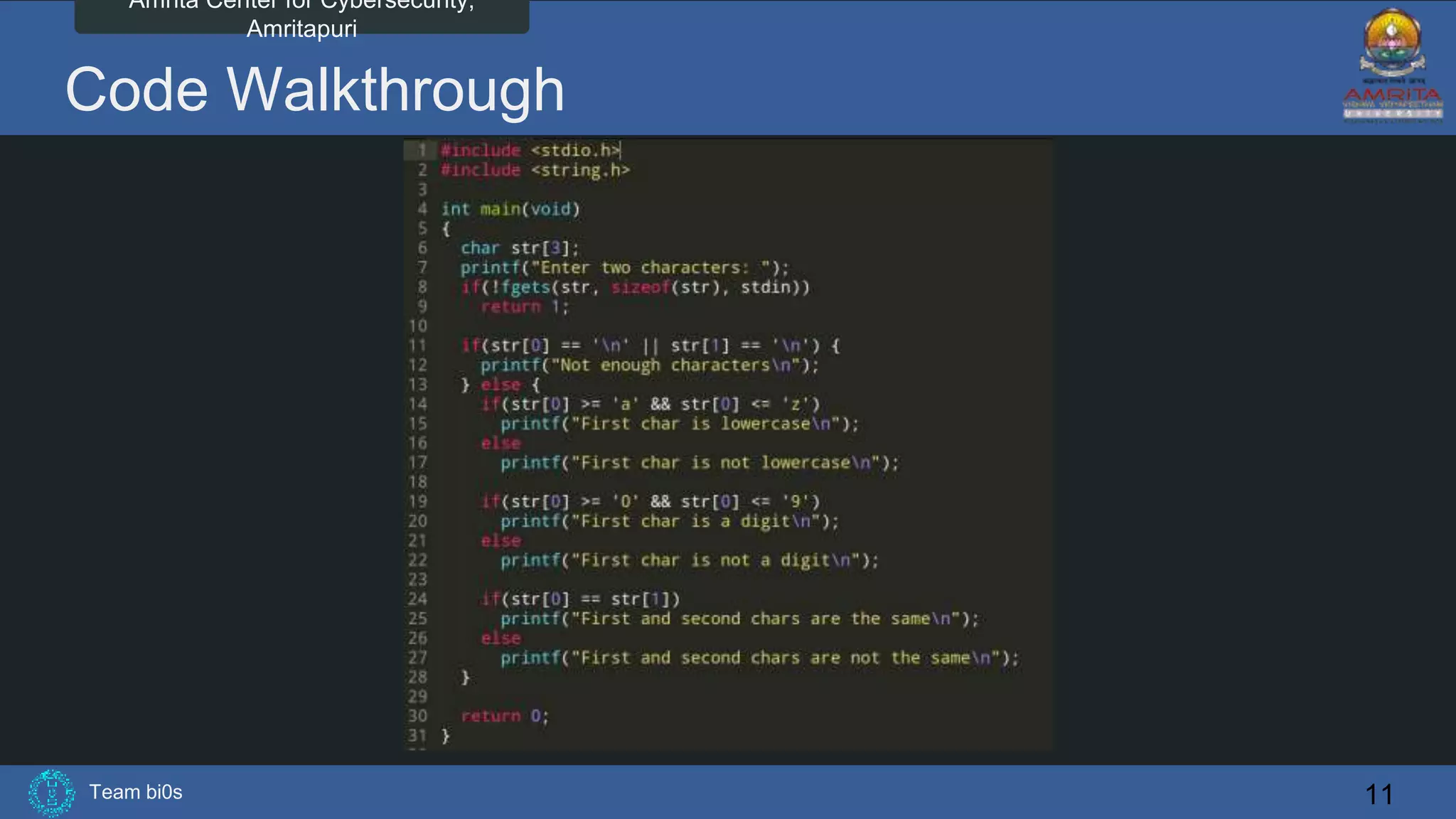
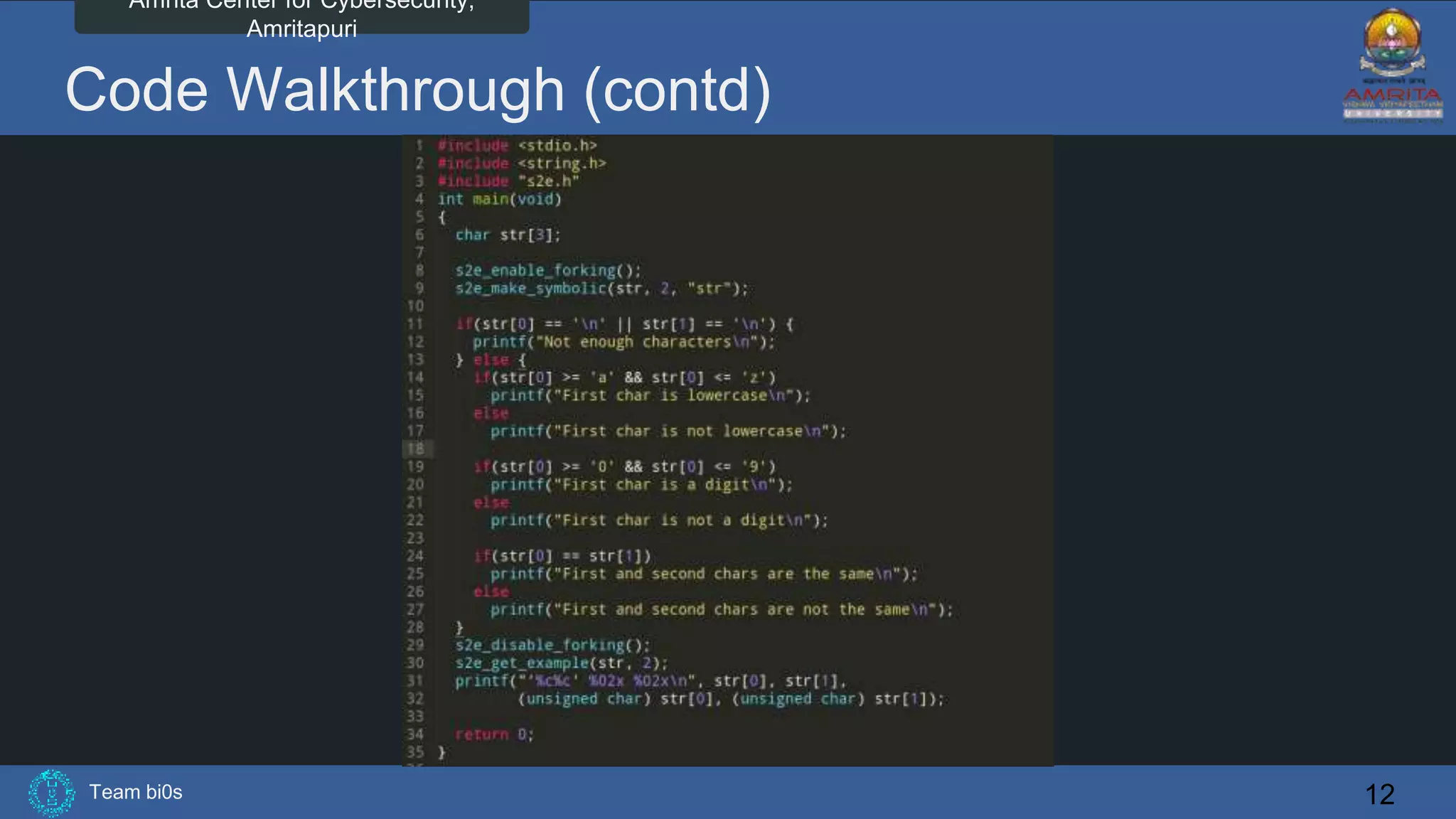
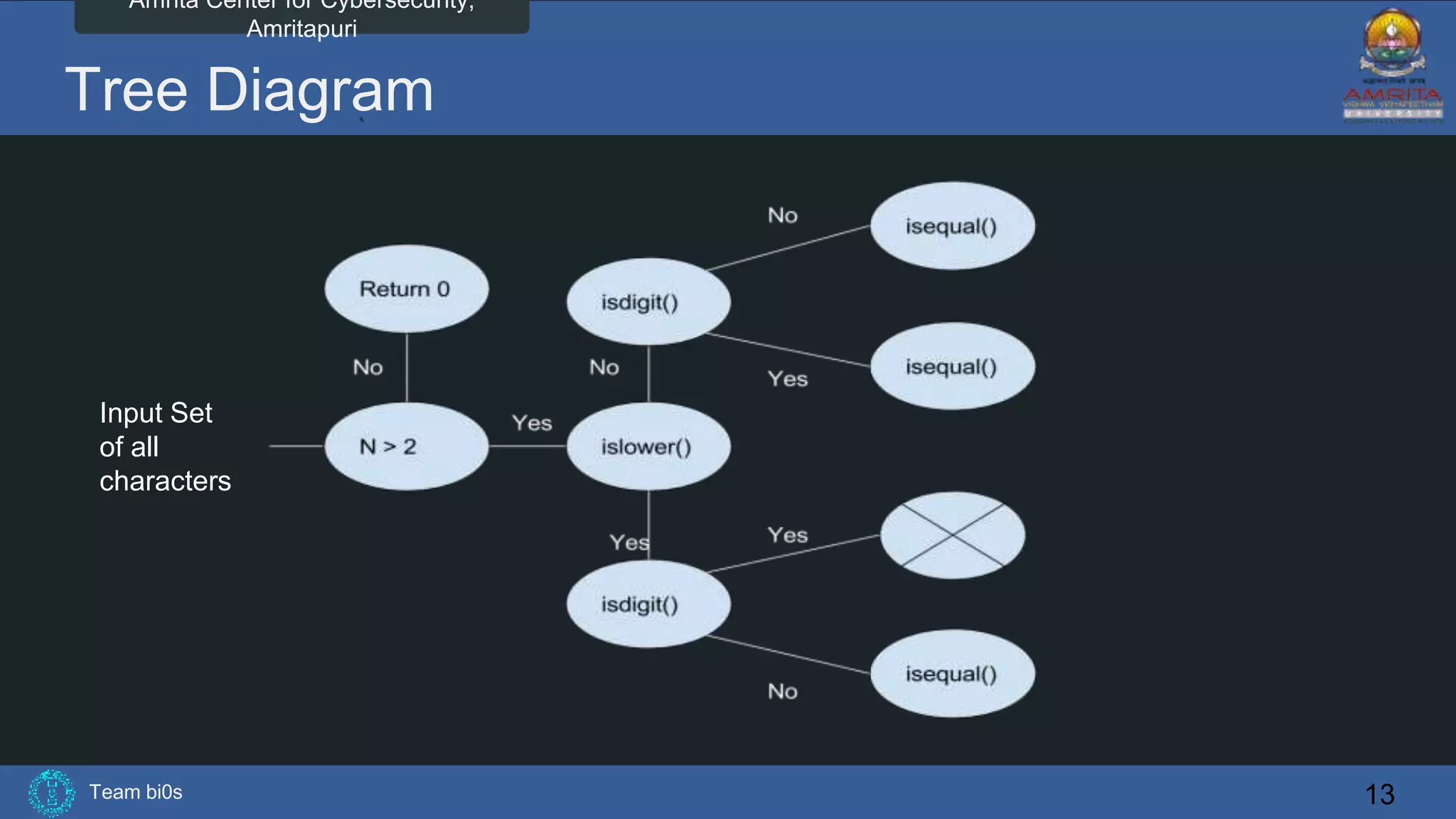
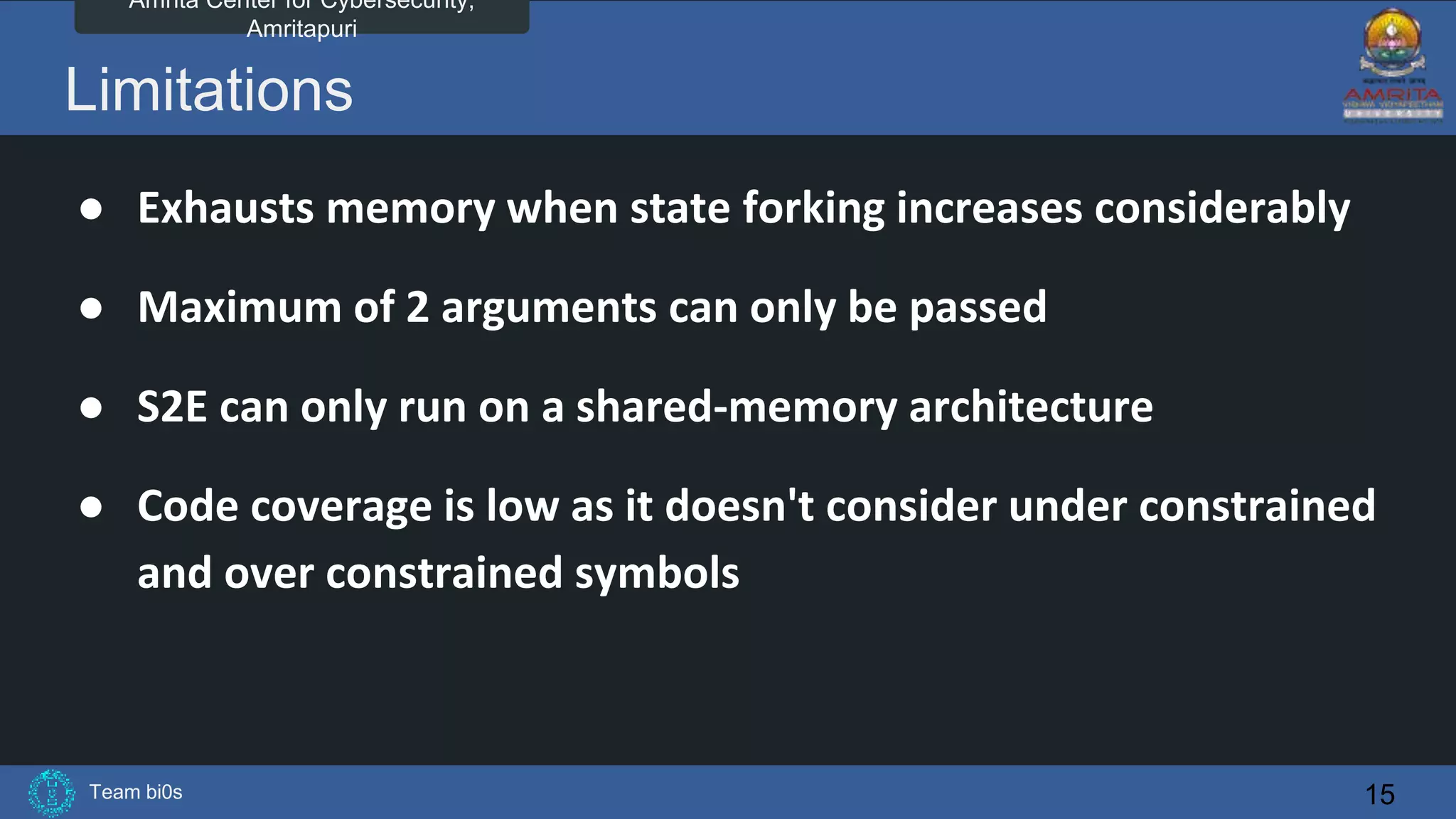
The document discusses Team bi0s from the Amrita Center for Cybersecurity, focusing on selective symbolic execution and their work with the S2E platform. It highlights the benefits of S2E for analyzing large programs, its architecture, and the differences between symbolic and concrete execution. Limitations of the approach, such as memory exhaustion and code coverage issues, are also mentioned.