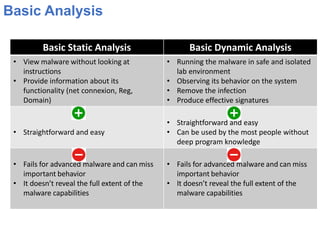
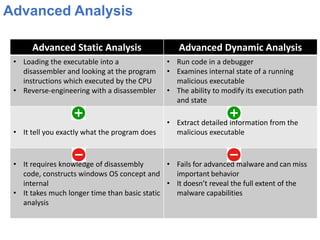
This document outlines a course on advanced malware reverse engineering. It begins with an introduction to malware types like viruses, worms, trojans, and ransomware. It then covers basic analysis techniques like viewing malware behavior and signatures. More advanced topics include static analysis using disassembly and dynamic analysis using debuggers. The goals of analysis are understanding malware functionality and enabling incident response. Analysis requires both static and dynamic methods to fully comprehend advanced threats.