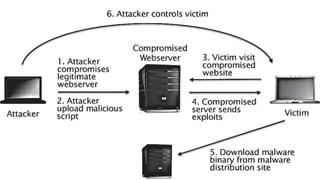
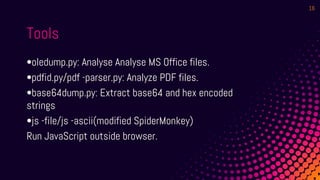
This document discusses techniques for analyzing obfuscated malicious web scripts. It begins by noting some limitations and objectives of the analysis. It then covers common obfuscation techniques used such as minification, visual noise, character encoding, and multiple layers of obfuscation. Methods for deobfuscation without wasting time are presented, such as using beautification tools and writing custom scripts. Specific tools are also highlighted that can aid in deobfuscation, like Didier Stevens tools and JavaScript analysis tools. Lastly, it discusses prevention best practices like keeping systems updated and avoiding unknown links/emails.