Embed presentation
Downloaded 12 times

![Malware use of DNS
rndruppbakyokv[.]com
1.2.3.4
Command and
Control
Infrastructure
Communication
Chanel with C&C
is established.
Compromised device
receives updates,
instructions, targets.
DNS Server
DNS Server
End point device](https://image.slidesharecdn.com/zpeaubwosesofcv1xmlf-signature-fa17ef08645a3cce9ed98bc960f7e89b419197b8ab9318d2a54057ce7f634710-poli-160709185307/75/Malicious-Client-Detection-using-Machine-learning-3-2048.jpg)
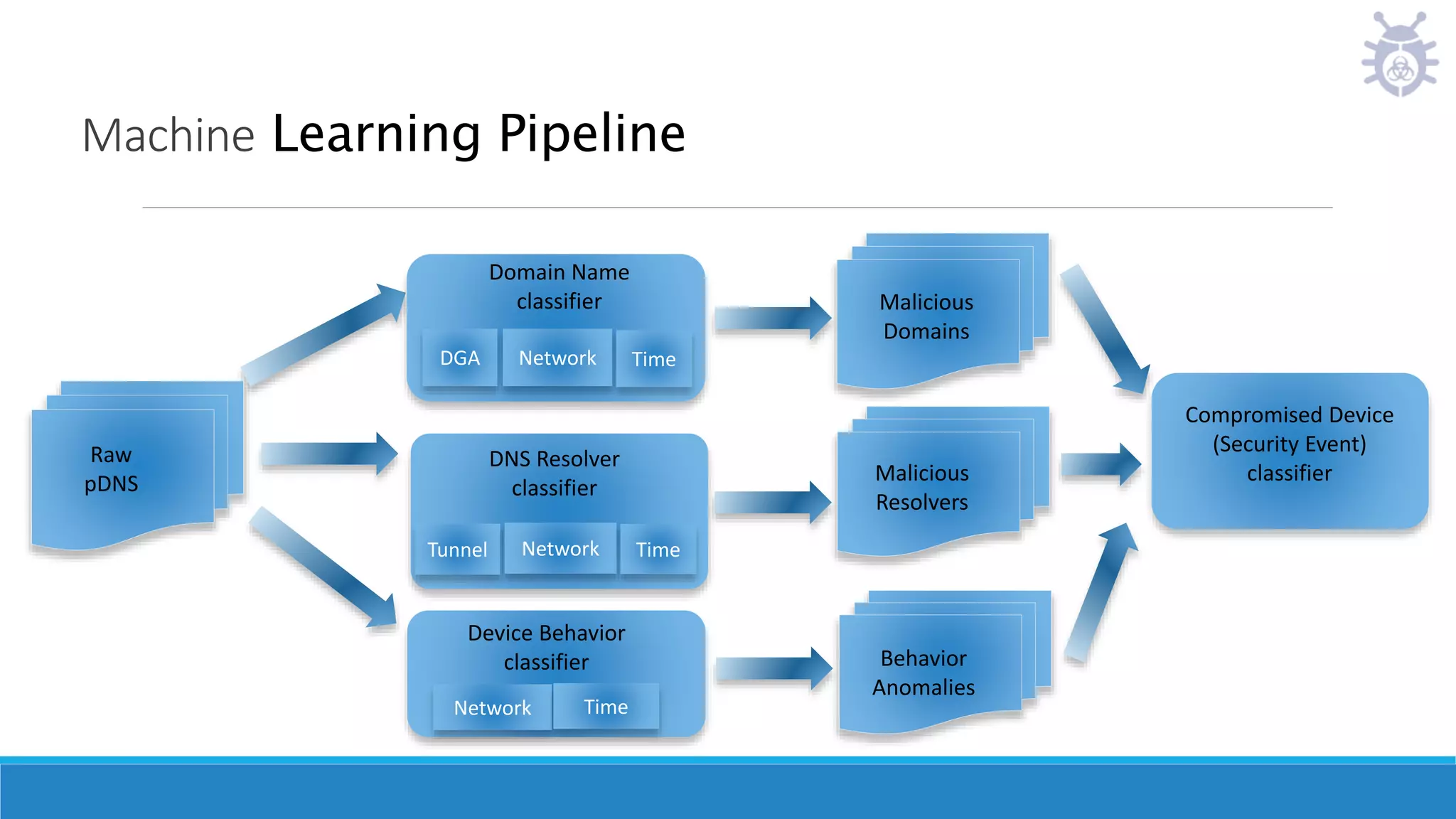
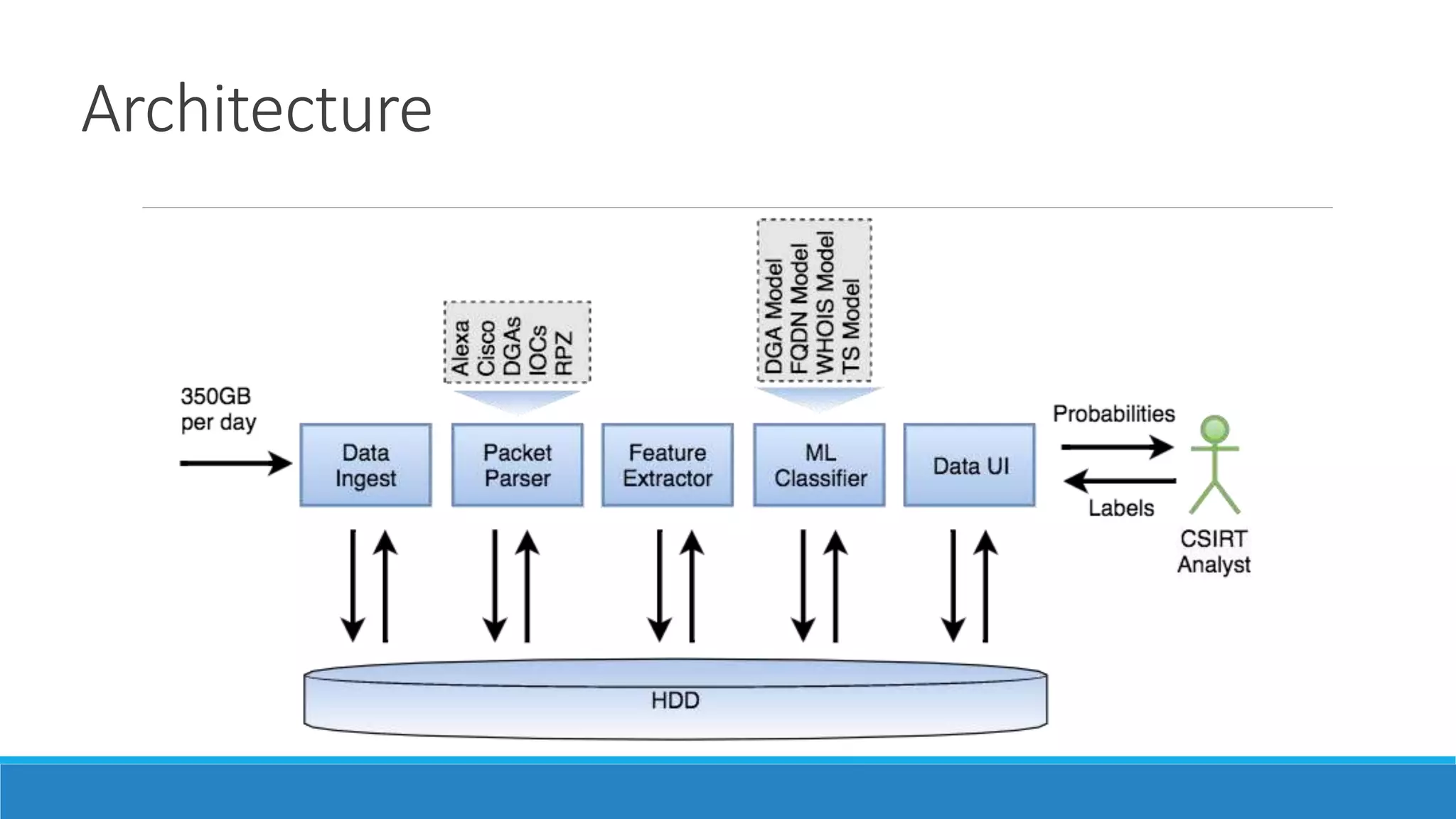
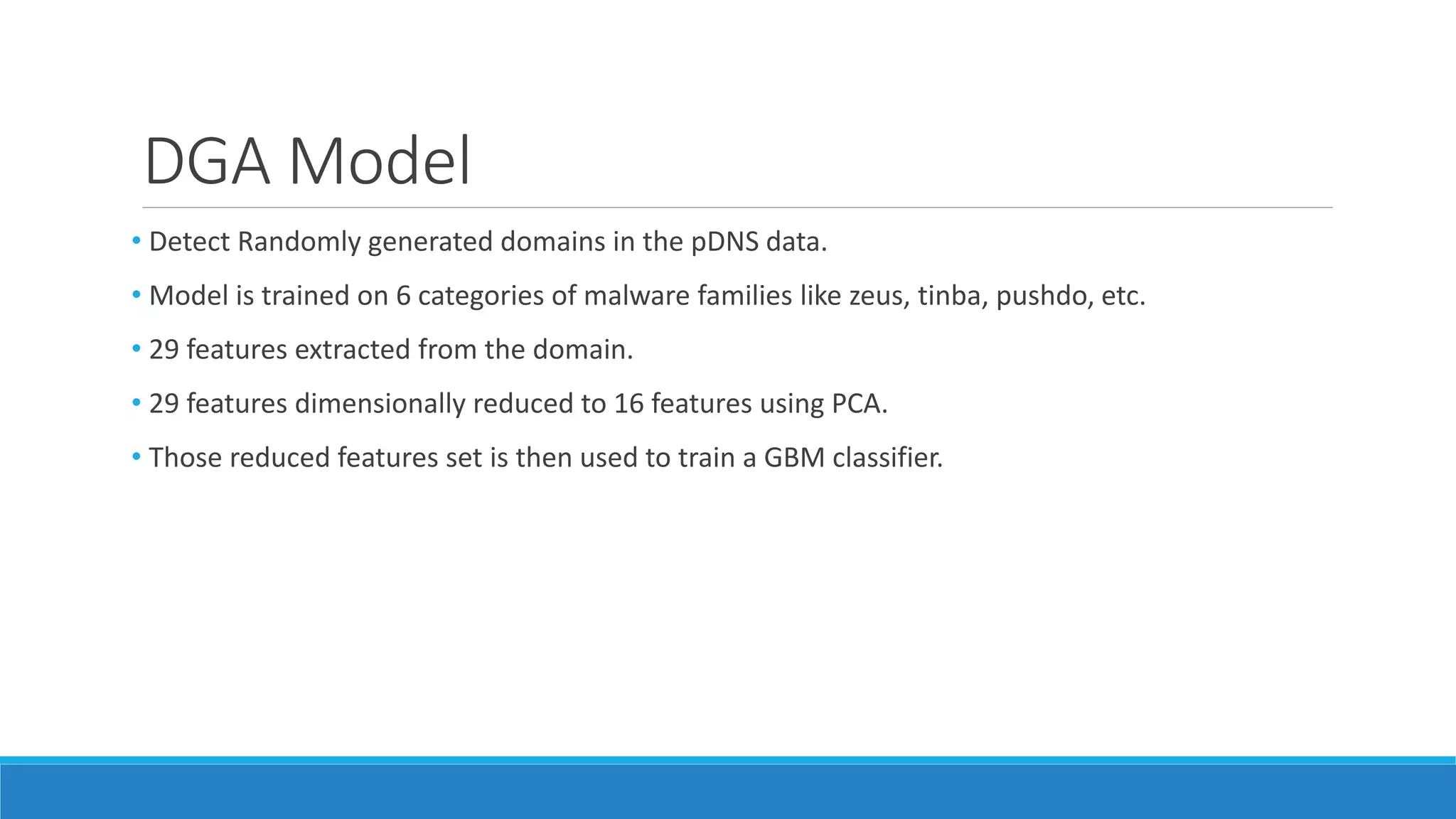
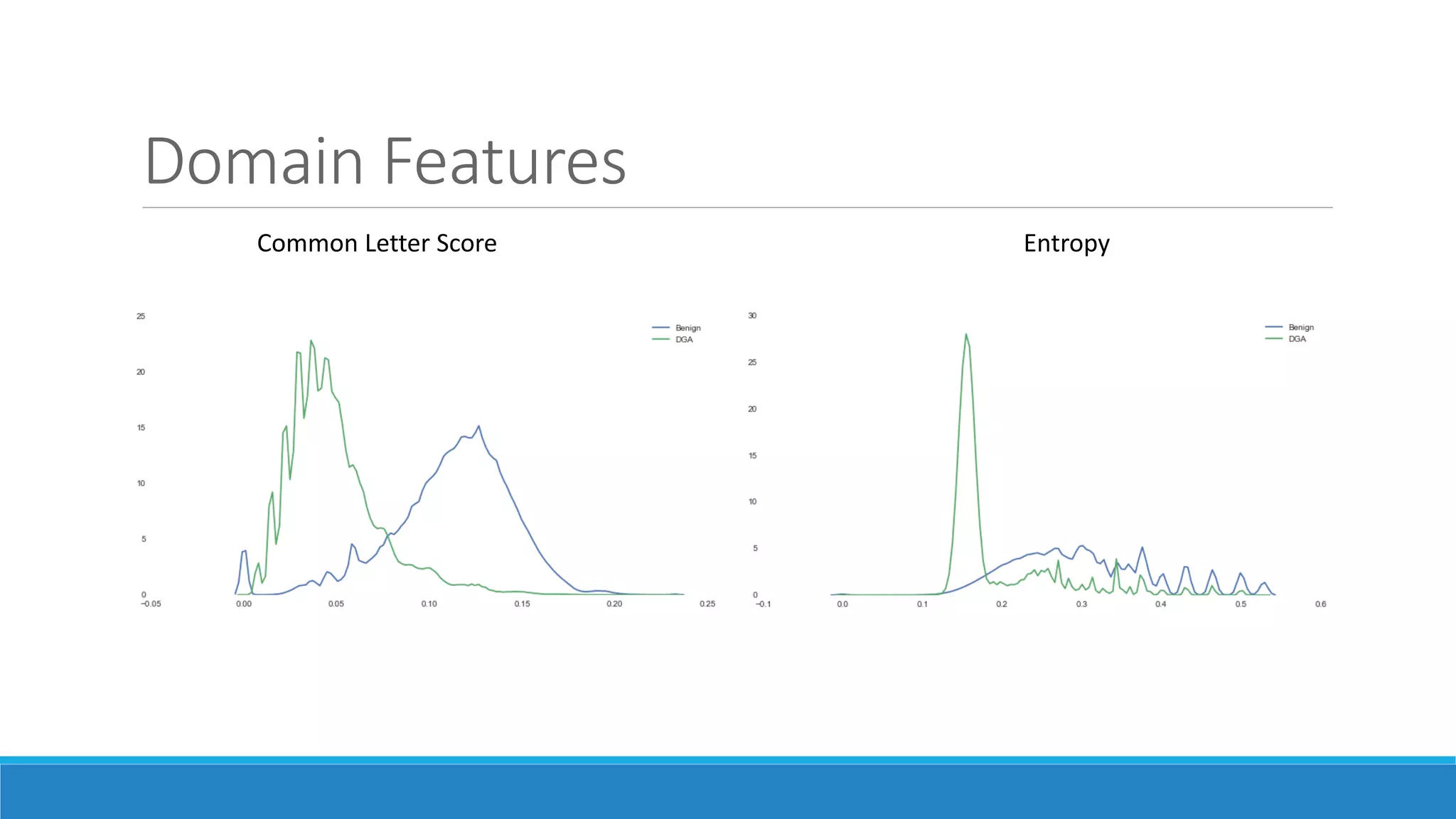
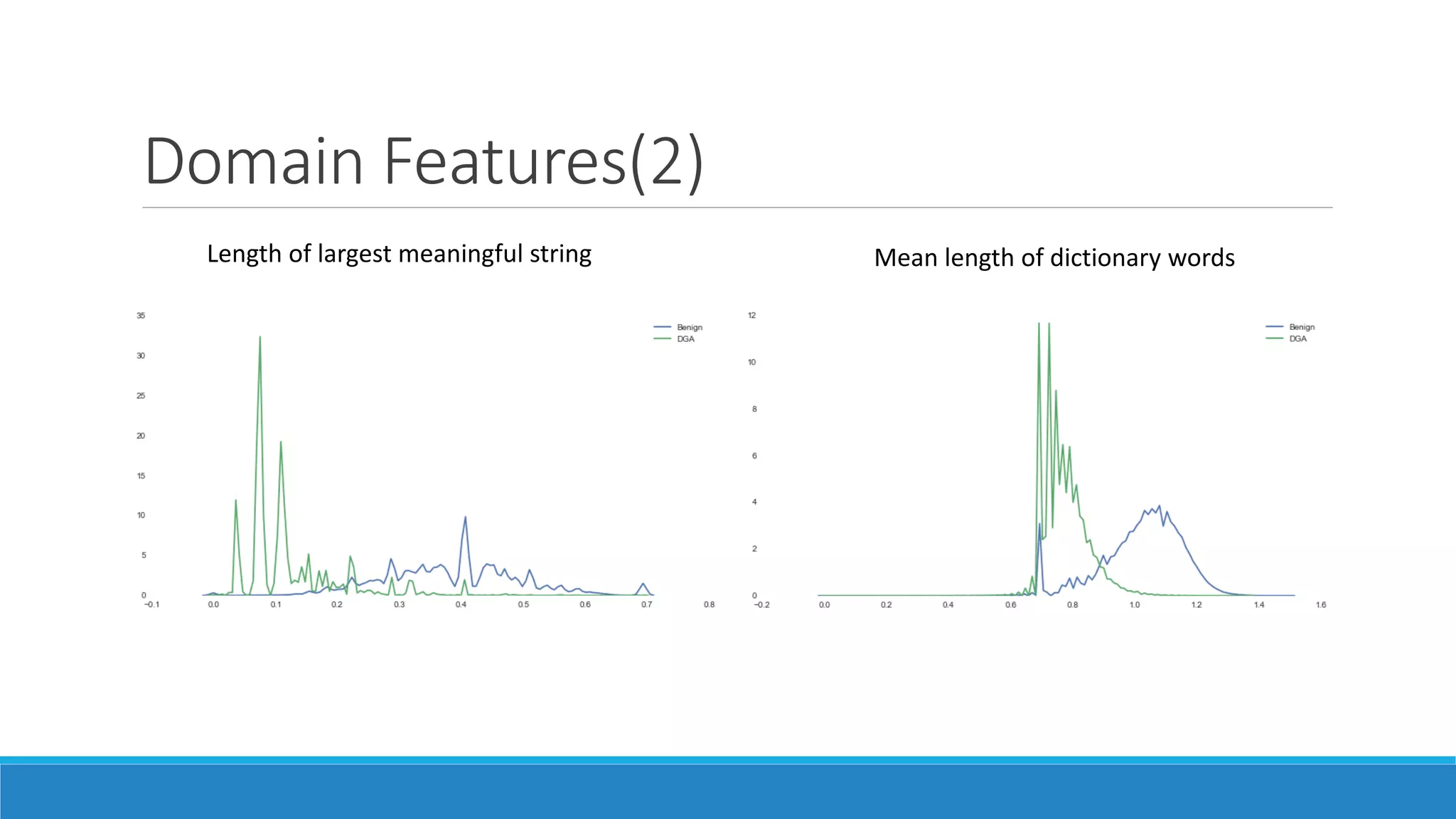
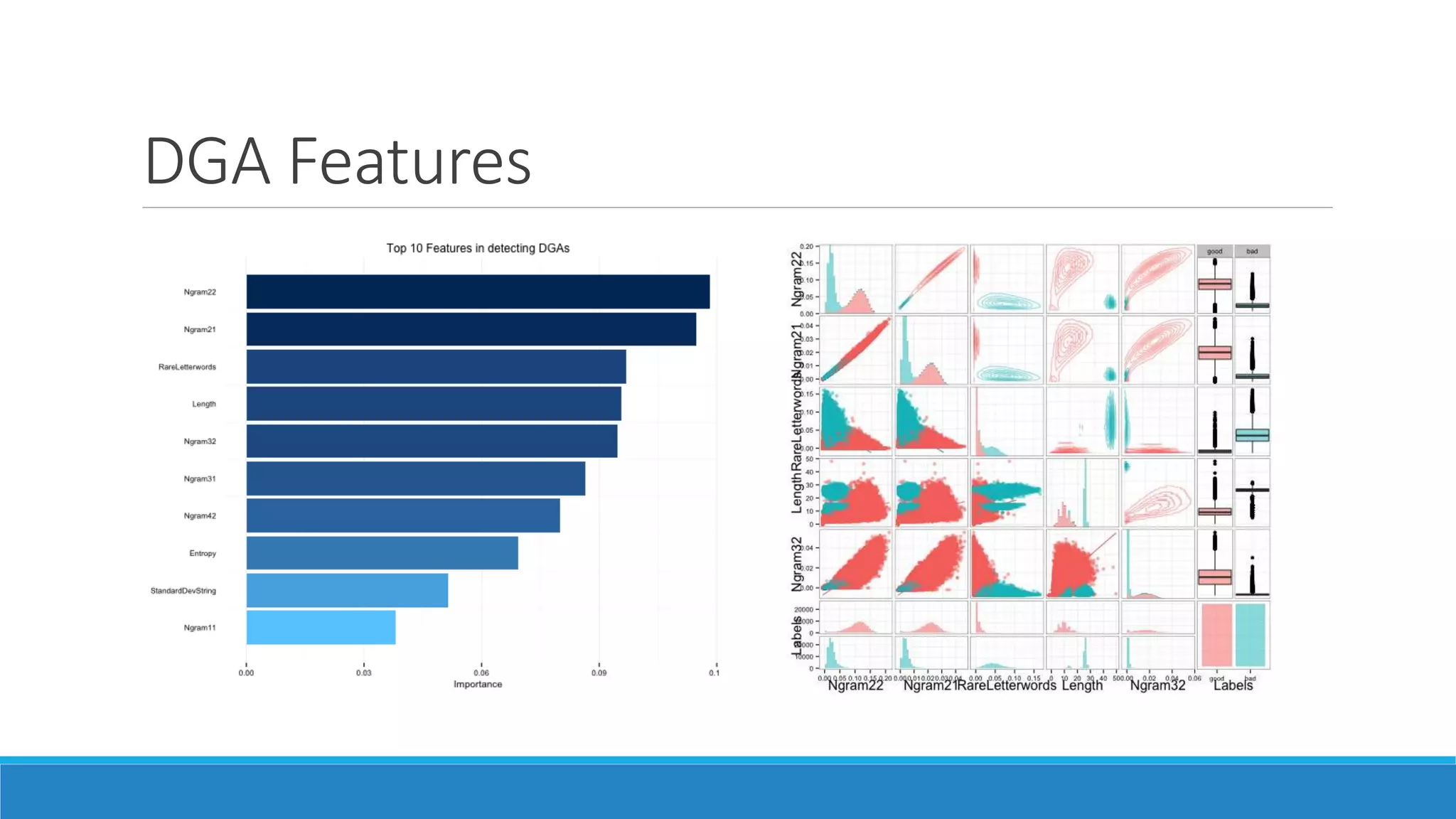
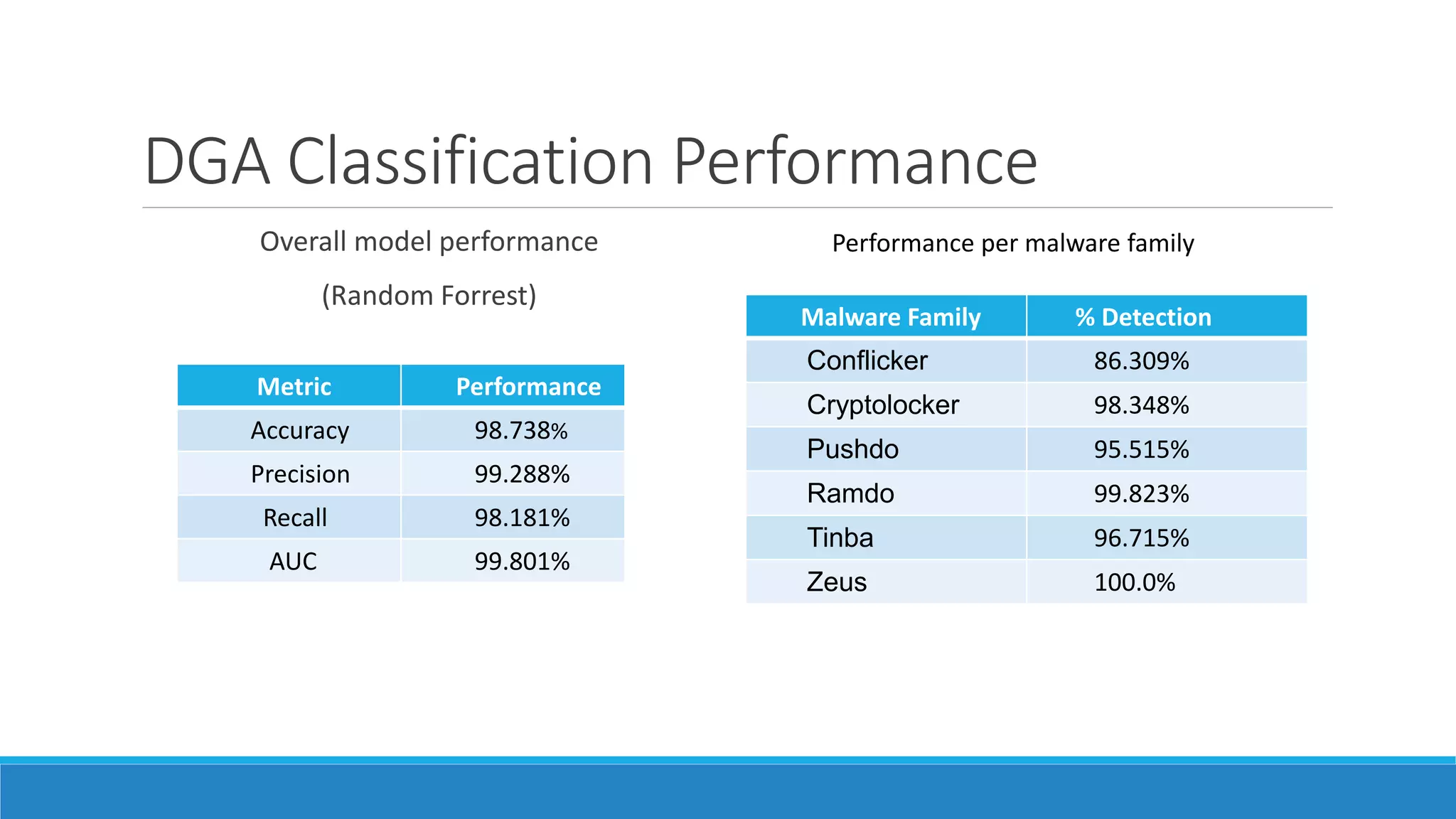
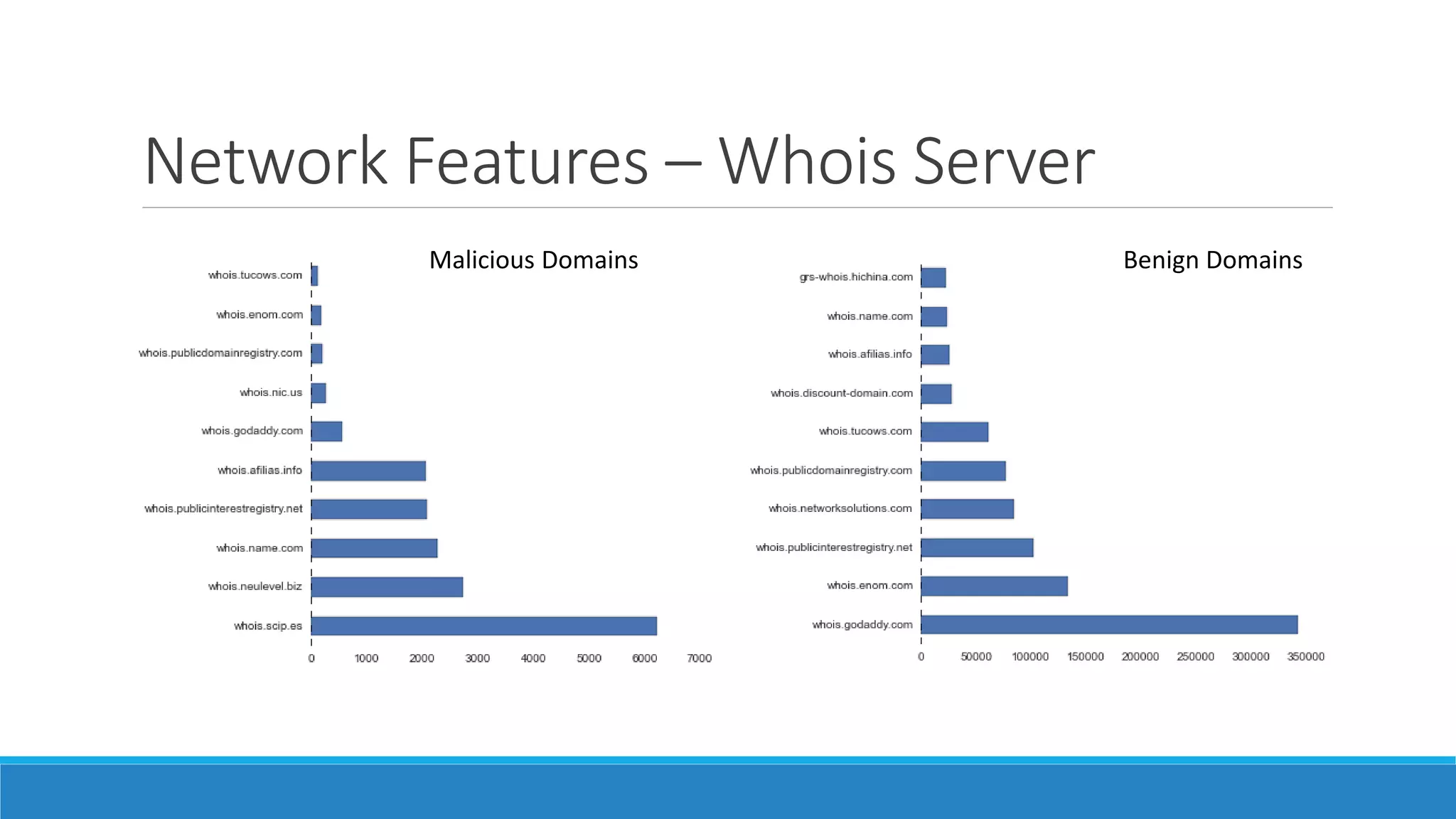
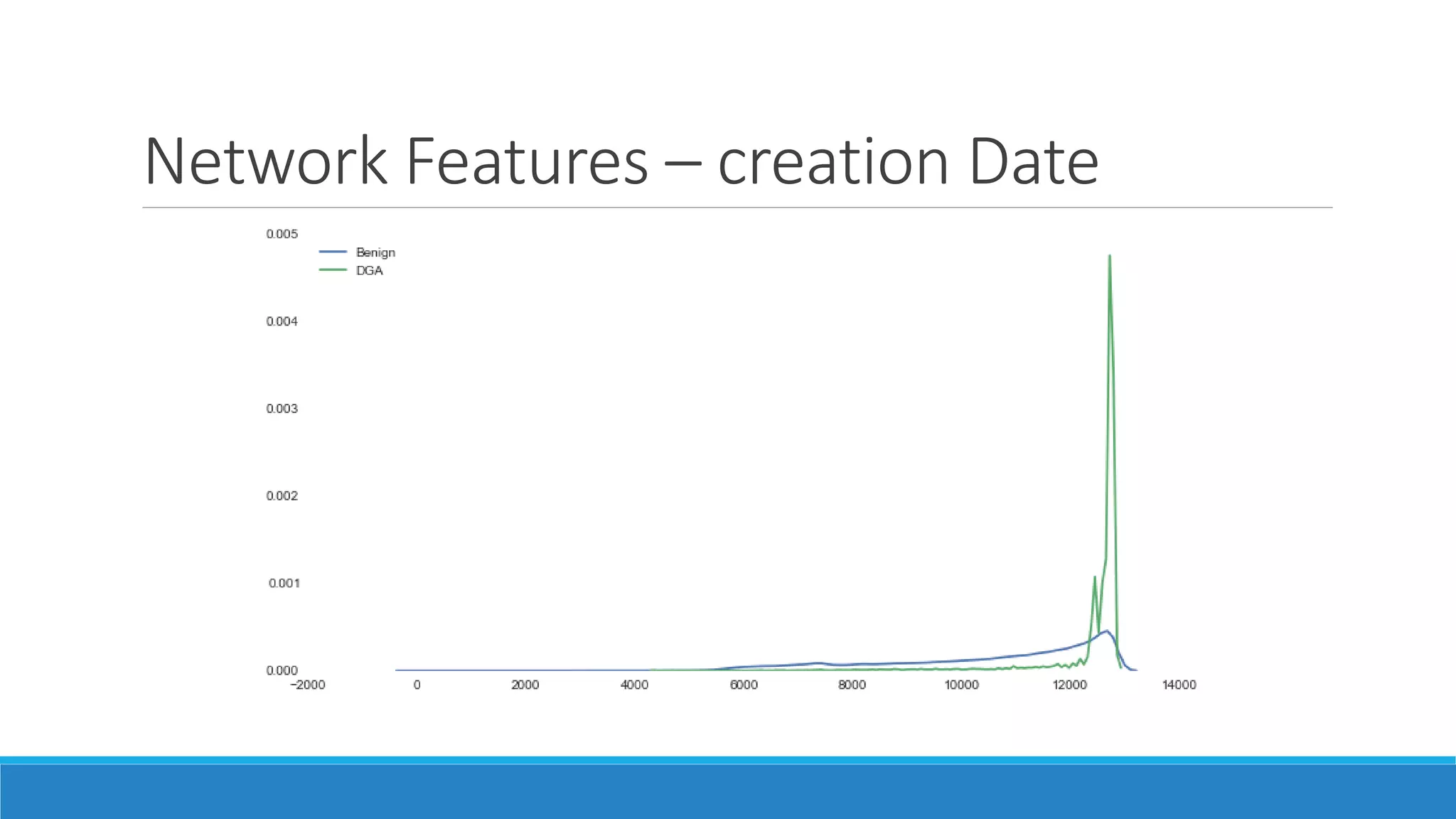
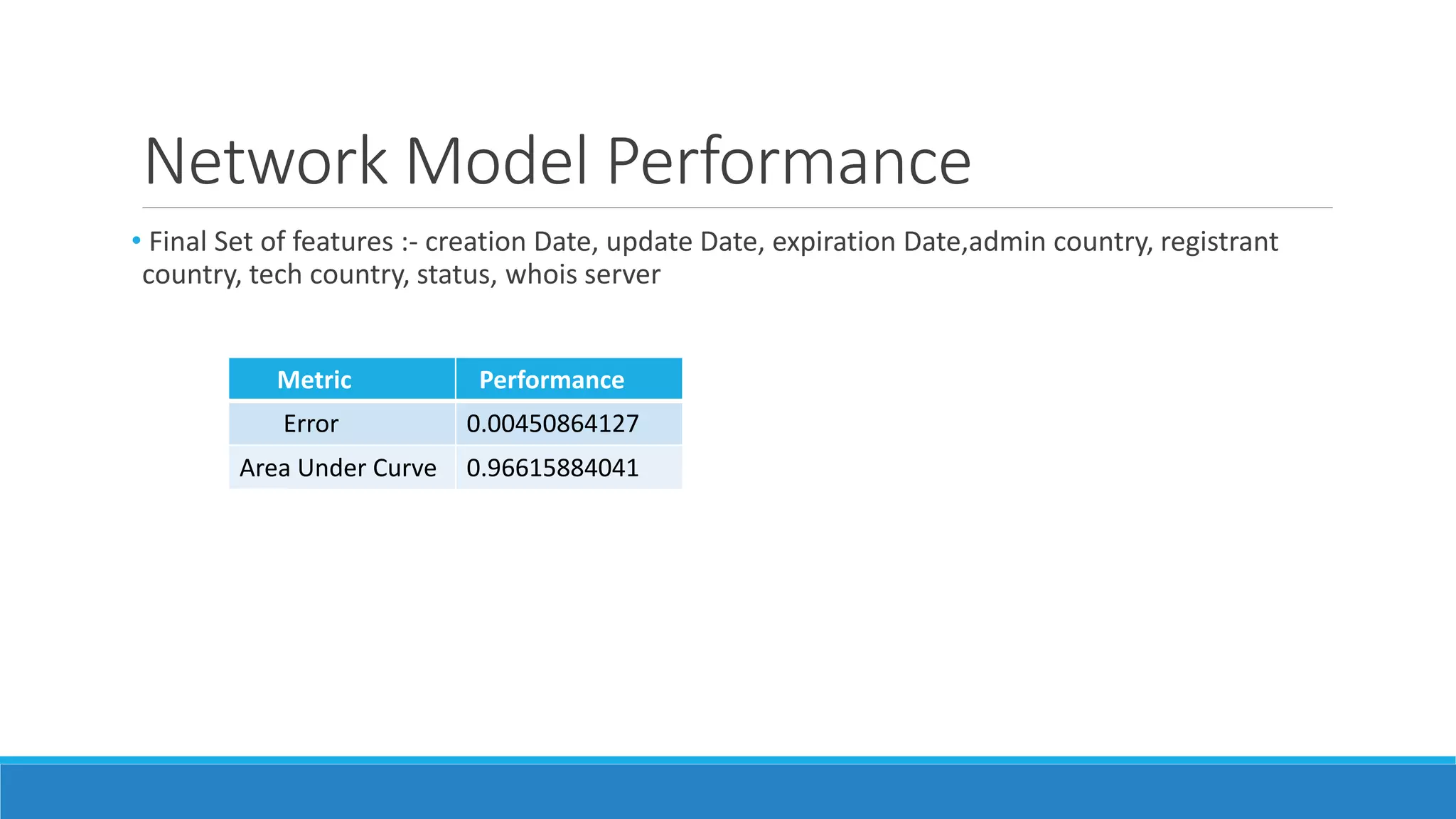
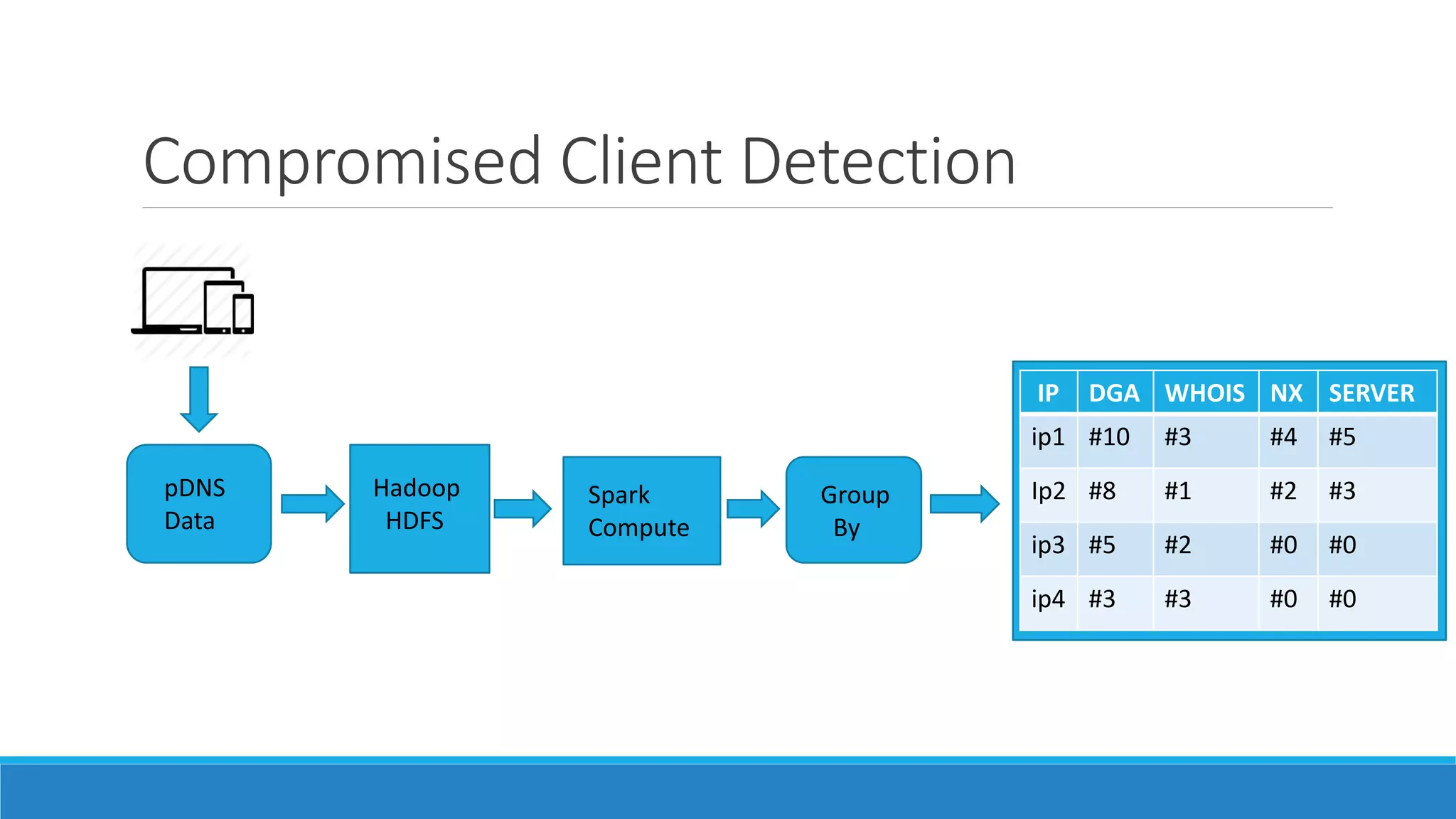
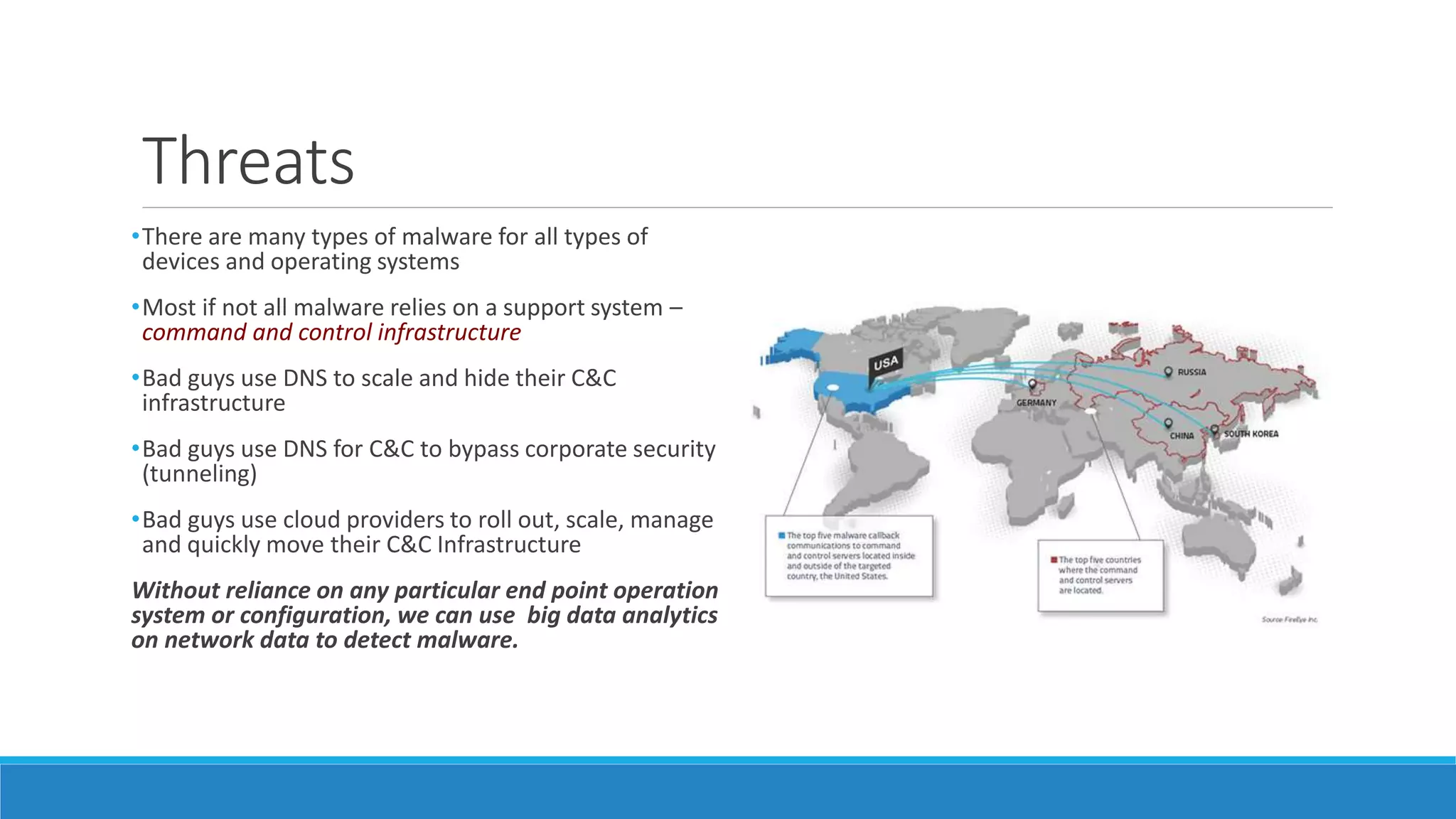
This document discusses using machine learning to detect malicious clients. It covers how malware relies on command and control infrastructure and DNS to operate and evade detection. It then presents an architecture that uses big data analytics on network data like DNS queries and WHOIS records to detect malware without relying on endpoint information. Models are developed to detect randomly generated domains, malicious DNS resolvers, and anomalous device behavior. These models analyze features of domains, DNS queries and WHOIS records. The document shows the models achieve high accuracy, precision, recall and AUC in detecting different malware families.


![Malware use of DNS
rndruppbakyokv[.]com
1.2.3.4
Command and
Control
Infrastructure
Communication
Chanel with C&C
is established.
Compromised device
receives updates,
instructions, targets.
DNS Server
DNS Server
End point device](https://image.slidesharecdn.com/zpeaubwosesofcv1xmlf-signature-fa17ef08645a3cce9ed98bc960f7e89b419197b8ab9318d2a54057ce7f634710-poli-160709185307/75/Malicious-Client-Detection-using-Machine-learning-3-2048.jpg)












