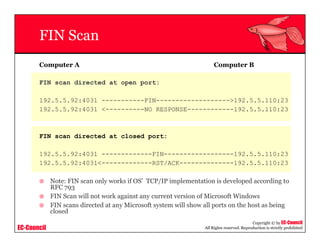
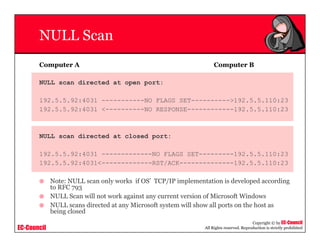
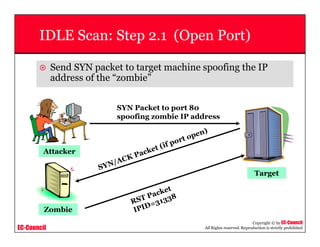
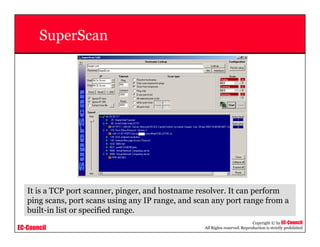
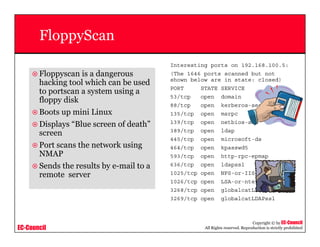
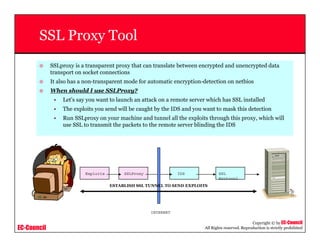
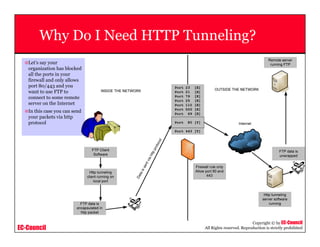
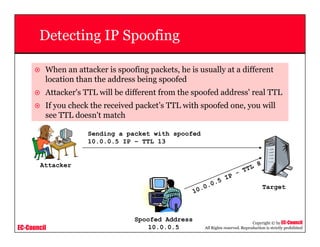
This document provides an overview of scanning techniques used in ethical hacking. It defines scanning as gathering information about IP addresses, operating systems, services, and architectures of target systems. The document outlines common scanning types like port scanning, network scanning, and vulnerability scanning. It also describes popular scanning tools like Nmap and Hping2, and scanning methods like ping sweeps, SYN stealth scans, and Xmas scans. The goal of scanning is to detect live systems, open ports, operating systems, and services to inform later stages of hacking like banner grabbing, vulnerability assessment, and network mapping.