Embed presentation
Download as PDF, PPTX




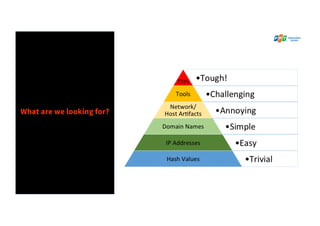
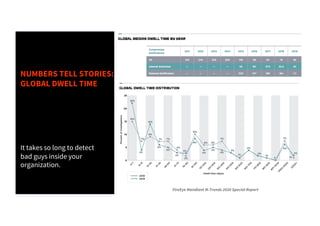
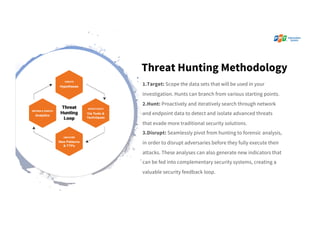



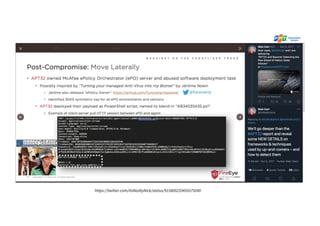










The document discusses the enhancement of threat hunting programs using the MITRE ATT&CK framework, emphasizing the differences between threat hunting and detection methods. It highlights a case study on combating APT32, detailing the methodologies and findings related to advanced threats in a large enterprise context. Key takeaways include the importance of assuming a breach mindset, training for threat hunting skills, and developing a strategic roadmap for implementation.



















