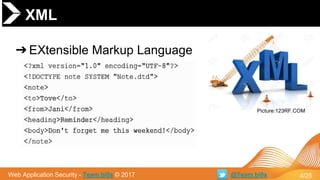
This document discusses XML External Entity (XXE) attacks. It begins with an introduction to XML and DTDs. It then explains how XML entities work and how parsers handle XML. The document outlines several attack vectors for XXE, including local file inclusion, internal port scanning, denial of service, and in rare cases, remote code execution. It provides examples of XXE in different contexts like Microsoft Office documents and JSON payloads. Finally, it recommends solutions like disabling external DTD fetching and entity parsing to prevent XXE vulnerabilities.










![OFFICE OPEN XML
Web Application Security - Team bi0s © 2017 @Team bi0s
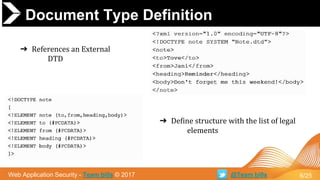
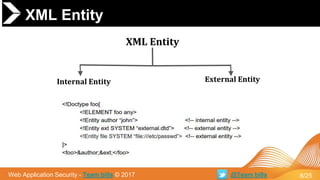
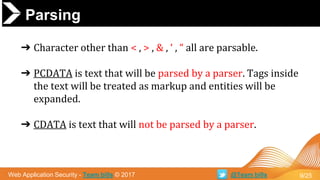
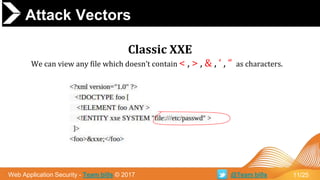
➔ General Parsing XML
◆ /_rels/.rels
◆ [Content_Types].xml
◆ Default Main Document
● /word/document.xml
● /ppt/presentation.xml
● /xl/workbook.xml
22/25](https://image.slidesharecdn.com/xxe-xmlexternalentity-170227101211/85/XXE-XML-External-Entity-Attack-22-320.jpg)