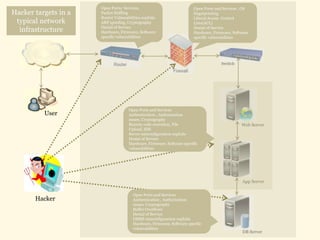
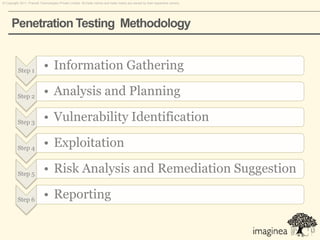
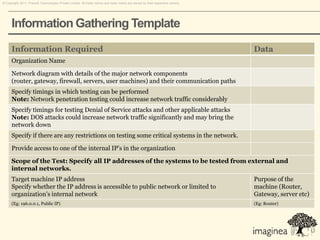
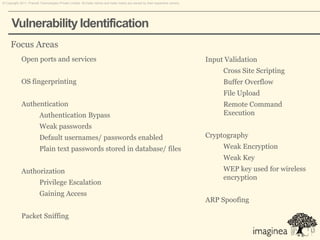
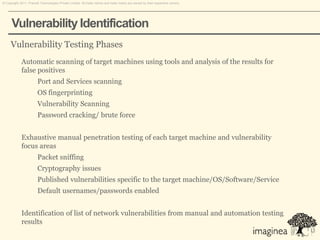
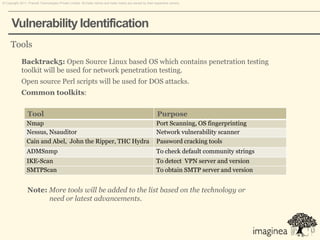
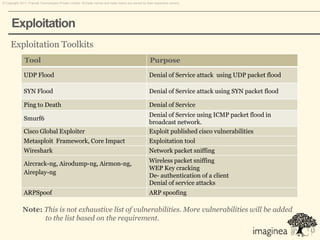
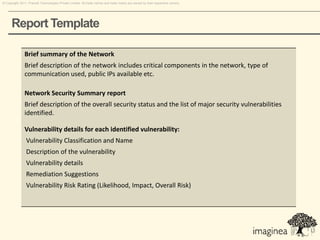
This document discusses network penetration testing conducted by Information Security Group. Network penetration testing uncovers network weaknesses before malicious hackers can exploit them. It involves testing a network from both external and internal perspectives to identify vulnerabilities. The methodology involves information gathering, analysis and planning, vulnerability identification, exploitation, risk analysis and remediation suggestions, and reporting. Specific vulnerabilities examined include open ports and services, packet sniffing, denial of service attacks, authentication issues, and more.