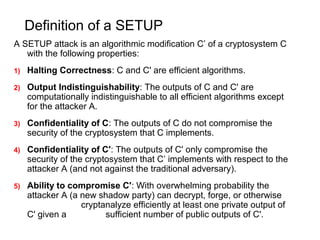
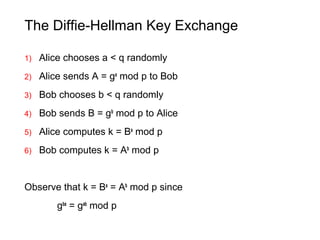
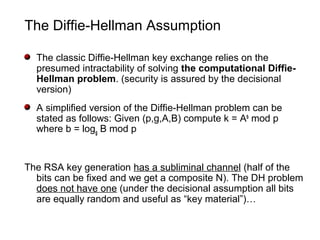
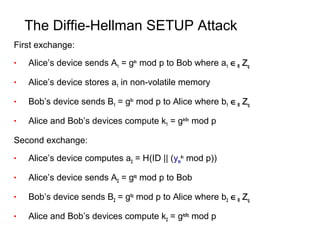
The document discusses kleptography, which is the study of secretly stealing cryptographic information in a way that cannot be detected. It proposes a technique called a Secretly Embedded Trapdoor with Universal Protection (SETUP) that allows an attacker to steal private keys or other secret information from cryptosystems in a way that is undetectable, even if the cryptosystem is reverse engineered. Specifically, it describes how a SETUP could be used to steal private RSA keys during key generation or compromise the Diffie-Hellman key exchange. The goal of kleptography and a SETUP is to allow an attacker to obtain secret information like private keys in a way that cannot be detected by users, reverse engineers, or other attackers



![Kleptographic Theft of RSA Private Key
Problem: To devise a backdoor (i.e., a way to covertly obtain the RSA
private keys of users) that can be deployed in an RSA [RSA78] key
generation program such that:
— The backdoor can only be utilized by the attacker, even
if the code is obtained and scrutinized (confidentiality).
— The resulting RSA key pair must “look like” a normal
RSA key pair (indistinguishability).
— The same copy of the key generation program is obtained
by everyone (it may be code signed for instance).
Observation: Note that a pseudorandom bit generator that uses a fixed
secret seed does not accomplish this. The seed or seeds will be revealed to
the reverse-engineer and the resulting pseudorandom bit sequences will be
revealed (also: statistical test will reveal this attack).
This provides that attacker with an exclusive advantage that is
maintained even after reverse-engineering.](https://image.slidesharecdn.com/yung-150830052721-lva1-app6892/85/Kleptography-6-320.jpg)
![Algorithms that can be attacked
By compromising RSA key generation using a SETUP, we can
compromise:
— RSA [RSA78]
— Rabin [Ra79]
— Properly padded RSA: RSA-Optimal Asymmetric Encryption
Padding (OAEP) [BR95,FIPS01,Sh01].
— And others…
Certification/ Validation: Simple Zero-Knowledge protocols will
not:
— reveal that a SETUP attack has taken place
— inhibit the operation of the SETUP attack in any way.](https://image.slidesharecdn.com/yung-150830052721-lva1-app6892/85/Kleptography-7-320.jpg)

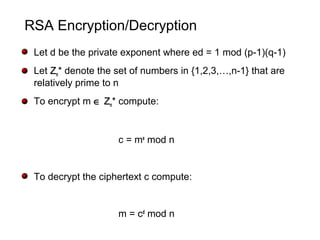
![Kleptographic RSA Key Generation
The key generation algorithm is modified to contain a cryptotrojan. The
cryptotrojan contains the attacker’s public key Y. This is an earlier version of
the attack [YY96,YY97], more mature versions exist [YY04,YY05].
1) choose a large value s randomly (e.g., 512-bits)
2) compute p = H(s) where H is a cryptographic one-way function
3) if p is composite or p-1 not relatively prime to e then goto step 1
4) choose a large value RND randomly
5) compute c to be the asymmetric encryption of s under Y (the attacker’s p.k.)
6) solve for (q,r) in (c || RND) = pq + r
7) if q is composite or q-1 not ….. then goto step 1
8) output the public key (n=pq,e) and the private key p
Note that n is about 1024 bits in length](https://image.slidesharecdn.com/yung-150830052721-lva1-app6892/85/Kleptography-10-320.jpg)


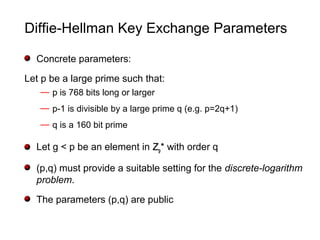








![Parameters for the DSA
- The primes p and q are as before (but q much smaller 160
bits).
- g is the same as before (gq
= 1 mod p).
- The DSA signing private key is x where x is chosen randomly
modulo q.
- The DSA signature verification public key is y where:
y = gx
mod p
- SHA1 denotes the “somewhat-secure hash algorithm”
[NIST180]
SHA1: {0,1}* {0,1}160](https://image.slidesharecdn.com/yung-150830052721-lva1-app6892/85/Kleptography-27-320.jpg)
![DSA Signing Algorithm
Algorithm [NIST186] to sign m given (m,x,g,p,q):
• Choose k < q randomly
• Compute r = (gk
mod p) mod q
• Compute s = k-1
(SHA1(m) + xr) mod q
• Output (r,s) as the digital signature on m.
• The DSA sends only 320 bits per signature,
can they be exploited fast?](https://image.slidesharecdn.com/yung-150830052721-lva1-app6892/85/Kleptography-28-320.jpg)
![DSA Signature Verification Algorithm
Algorithm to verify the signature (r,s) given (m,r,s,y,g,p,q):
1) Make sure all values are contained in the correct sets
2) Compute t = s-1
mod q
3) Signature is valid if and only if:
r = ((gt
)SHA1(m)
ytr
mod p) mod q
Note that:
r = (gk
mod p) mod q and k = s-1
SHA1(m) + xs-1
r mod q
Also,
(gt
)SHA1(m)
ytr
mod p = gk
mod p [Very Important!]](https://image.slidesharecdn.com/yung-150830052721-lva1-app6892/85/Kleptography-29-320.jpg)






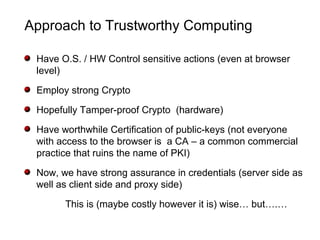
![Conclusions
In all these schemes: we have proof of security of the system
(against all but the attacker) and a second security
(exclusivity) proof for the attacker [Two systems in one!] and
proofs are according to modern standards….
Cryptography is about security (we know..), it is about
solving seemingly paradoxical schemes (we know….), and is
also about looking for things that no one will ever look at (thus
it is also about non-trivial scrutiny, namely: hacking with a
purpose)….](https://image.slidesharecdn.com/yung-150830052721-lva1-app6892/85/Kleptography-36-320.jpg)
![Conclusions
Trust relationships: manufacturer has to be trusted and
implementations scrutinized as much as possible.
Some black box tests will not work (under cryptographic
assumptions)
Trust within and about cryptographic system is “tricky” (also
true in dealing with other systems, but not everyone thinks
about it seriously! So cryptographers ought to look at these
other things…)
Since cryptographic thinking is important in analyzing security
issues cryptographic training is important! [to catch a thief
you have to think like one]](https://image.slidesharecdn.com/yung-150830052721-lva1-app6892/85/Kleptography-37-320.jpg)