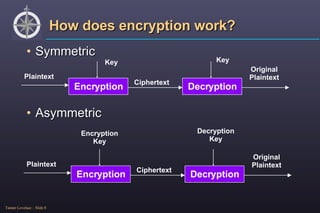
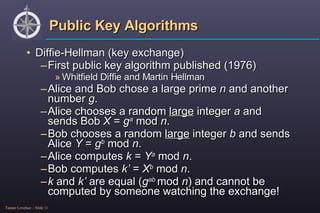
The document provides an overview of cryptography, detailing its purpose, types (symmetric and asymmetric), and basic functioning. It explains various public key algorithms, particularly focusing on OpenPGP/GnuPG for secure communication, including encryption, decryption, and key management. Additionally, it discusses the importance of trust in cryptographic keys and the creation of a web of trust among users.









![Public Key Algorithms RSA (Rivest, Shamir, and Adleman) [1977] Choose two random large prime numbers p and q . Compute n = pq . Choose a number e such that e is between 1 and pq and e is relatively prime to ( p – 1)( q – 1). Compute d from e ( d = e -1 mod (( p -1)( q -1))) Multiplicative inverse To encrypt, calculate c = m e mod n . To decrypt, calculate m = c d mod n .](https://image.slidesharecdn.com/openpgpgnupg-encryption-1206500672890206-5/85/OpenPGP-GnuPG-Encryption-12-320.jpg)


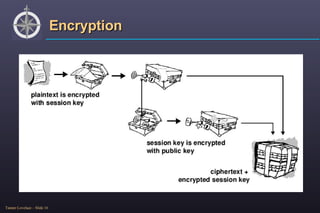
![Encryption To encrypt a file, you need to specify options Recepient (can be yourself) Binary or ascii mode Output filename Input filename % gpg -r [UID]-a –o [outname] –e [file] Will also work with streams.](https://image.slidesharecdn.com/openpgpgnupg-encryption-1206500672890206-5/85/OpenPGP-GnuPG-Encryption-17-320.jpg)
![Decryption Only need to specify the decrypt option % gpg -d [file] Will prompt for pass phrase](https://image.slidesharecdn.com/openpgpgnupg-encryption-1206500672890206-5/85/OpenPGP-GnuPG-Encryption-18-320.jpg)
![Signature Can be combined with encryption Can be integrated or detached % gpg –a --sign[file] % gpg –a --detach-sign[file] Detached signatures are useful for signing binary packages. Used with rpm (--addsign and –resign options)](https://image.slidesharecdn.com/openpgpgnupg-encryption-1206500672890206-5/85/OpenPGP-GnuPG-Encryption-20-320.jpg)


![Key revocation Always generate a revocation certificate after creating a key! If you lose your pass phrase, will allow you to cancel your key. % gpg --gen-revoke [UID] Need the pass phrase (to get to the secret key)](https://image.slidesharecdn.com/openpgpgnupg-encryption-1206500672890206-5/85/OpenPGP-GnuPG-Encryption-25-320.jpg)
![Key functions List keys and signatures % gpg --list-keys % gpg --list-sigs % gpg --fingerprint Import % gpg --import [filename] Export % gpg --export [UID] By default export is binary. Use “-a” to do ascii-armor.](https://image.slidesharecdn.com/openpgpgnupg-encryption-1206500672890206-5/85/OpenPGP-GnuPG-Encryption-26-320.jpg)
![Key servers You could exchange keys by e-mail or web page, but there is a better way. PGP and GnuPG support a remote key server Send % gpg --keyserver [ks] --send-key [UID] Receive % gpg --keyserver [ks] --recv-key [UID] Default key server can be put in options file. If default server set, gpg will automatically look there for new keys.](https://image.slidesharecdn.com/openpgpgnupg-encryption-1206500672890206-5/85/OpenPGP-GnuPG-Encryption-27-320.jpg)
![Key signing ONLY SIGN A KEY WHEN YOU ARE ABSOLUTELY SURE IT IS AUTHENTIC!!! Use the edit key function % gpg --edit-key [UID] Will bring up a command prompt Can sign, revoke, change trust, delete, etc… >sign Make sure you send the newly signed key to a key server.](https://image.slidesharecdn.com/openpgpgnupg-encryption-1206500672890206-5/85/OpenPGP-GnuPG-Encryption-28-320.jpg)

