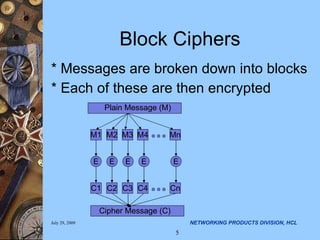
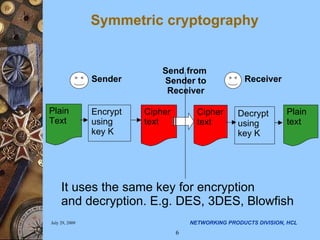
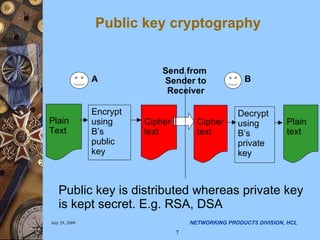
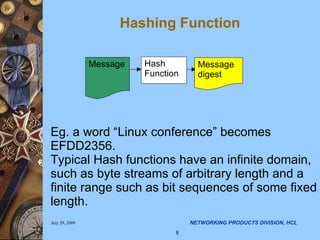
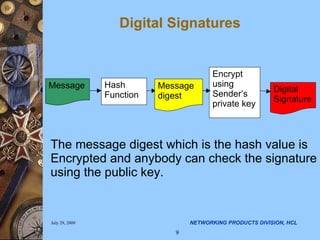
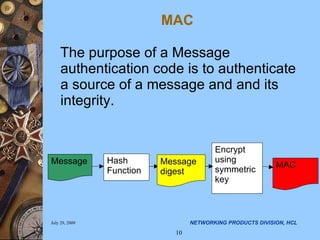
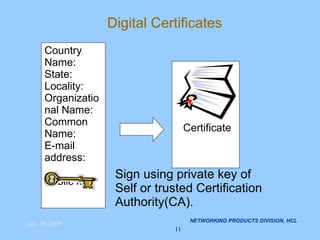
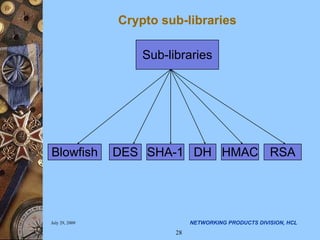
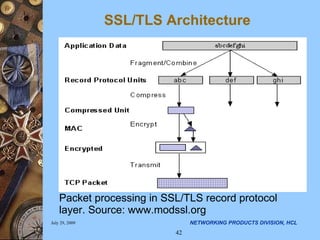
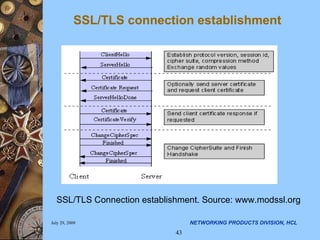
The document discusses applying security algorithms using the OpenSSL crypto library. It provides an overview of common security algorithms like hash functions, authentication codes, symmetric and public key cryptography. It then describes how OpenSSL implements these algorithms via sub-libraries and provides command line tools to generate keys, encrypt/decrypt data, and sign/verify signatures. The last section discusses programming with the crypto library, showing examples of generating keys, encrypting/decrypting data with Blowfish, and establishing SSL/TLS connections.
























![Programming using Crypto library – Blowfish – Create a key Step 2: Initialize key Read 16 bytes from /dev/random That gives 128-bit random symmetric key. Read 8 bytes to populate initialization vector. int bf_key[16]; int bf_vector[8]; if ((read (fd, bf_key, 16)) == -1) perror (“Could not read the key"); if ((read (fd, init_vector, 8)) == -1) perror ("read iv error");](https://image.slidesharecdn.com/applying-security-algorithms-using-openssl-crypto-library-4634/85/Applying-Security-Algorithms-Using-openSSL-crypto-library-38-320.jpg)





![Questions B.C. Sekar HCL Technologies Limited, 49-50, Nelson Manikkam Road, Chennai - 600026. Phone - +91-44-23750171 [email_address] http://www.hcltech.com](https://image.slidesharecdn.com/applying-security-algorithms-using-openssl-crypto-library-4634/85/Applying-Security-Algorithms-Using-openSSL-crypto-library-46-320.jpg)