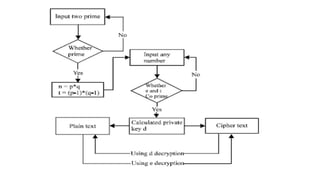
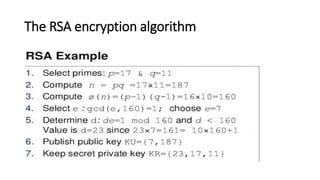
The RSA encryption algorithm is one of the most widely used public key encryption algorithms invented in 1977. It uses two large prime numbers to generate a public key and a private key. The public key is used to encrypt messages while the private key is used to decrypt them. RSA works by: 1) Generating two large prime numbers and computing n as their product, 2) Finding a number e that is coprime to another number m, 3) Finding d such that d*e is congruent to 1 modulo m, 4) Publishing e and n as the public key and keeping d and n as the private key.