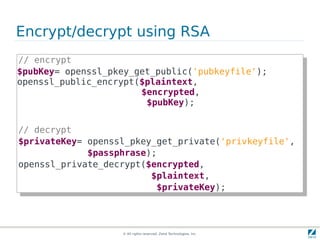
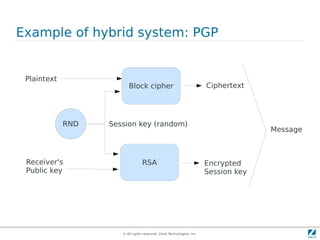
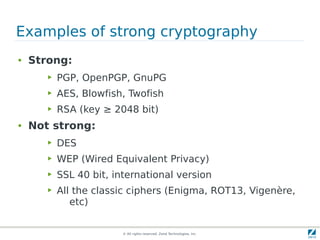
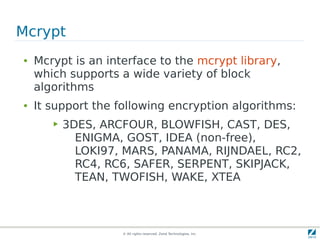
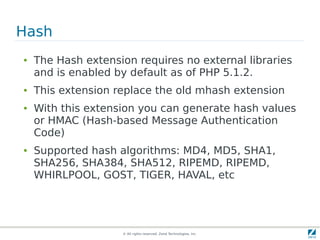
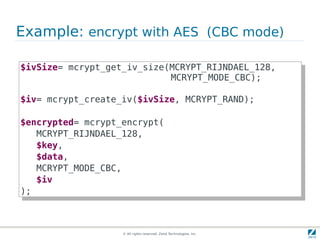
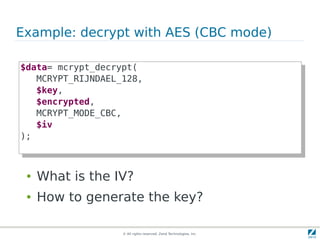
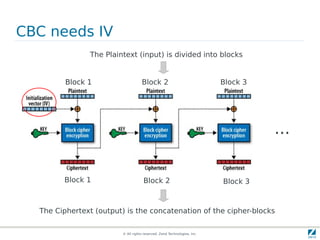
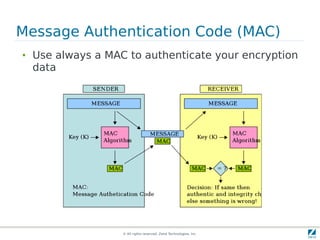
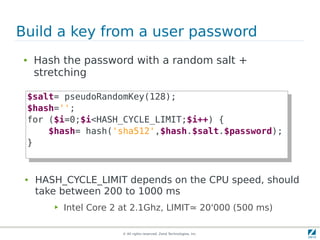
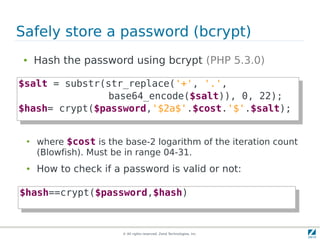
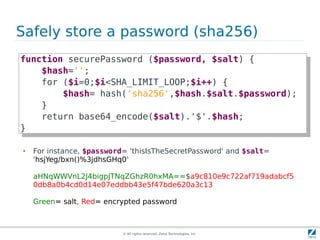
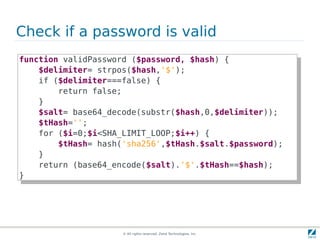
The document discusses strong cryptography in PHP, highlighting its importance in secure data handling and various algorithms such as AES and RSA. It emphasizes that strong cryptography involves more than encryption, including hashing and secure password storage practices. Additionally, it outlines best practices, key generation techniques, and the use of libraries like OpenSSL and mcrypt in PHP applications.


















![Pseudo random key
function pseudoRandomKey($size) {{
function pseudoRandomKey($size)
if(function_exists('openssl_random_pseudo_bytes')) {{
if(function_exists('openssl_random_pseudo_bytes'))
$rnd == openssl_random_pseudo_bytes($size, $strong);
$rnd openssl_random_pseudo_bytes($size, $strong);
if($strong === TRUE)
if($strong === TRUE)
return $rnd;
return $rnd;
}}
$sha=''; $rnd='';
$sha=''; $rnd='';
for ($i=0;$i<$size;$i++) {{
for ($i=0;$i<$size;$i++)
$sha= hash('sha256',$sha.mt_rand());
$sha= hash('sha256',$sha.mt_rand());
$char= mt_rand(0,62);
$char= mt_rand(0,62);
$rnd.= chr(hexdec($sha[$char].$sha[$char+1]));
$rnd.= chr(hexdec($sha[$char].$sha[$char+1]));
}}
return $rnd;
return $rnd;
}}
© All rights reserved. Zend Technologies, Inc.](https://image.slidesharecdn.com/strongcryptography-110521082240-phpapp02/85/Strong-cryptography-in-PHP-26-320.jpg)
![Generate public and private keys
$privateKey = openssl_pkey_new(array(
$privateKey = openssl_pkey_new(array(
'private_key_bits' => 2048,
'private_key_bits' => 2048,
'private_key_type' => OPENSSL_KEYTYPE_RSA
'private_key_type' => OPENSSL_KEYTYPE_RSA
));
));
openssl_pkey_export_to_file($privateKey,,
openssl_pkey_export_to_file($privateKey
'/path/to/privatekey', $passphrase);
'/path/to/privatekey', $passphrase);
$keyDetails = openssl_pkey_get_details($privateKey);
$keyDetails = openssl_pkey_get_details($privateKey);
file_put_contents('/path/to/publickey',
file_put_contents('/path/to/publickey',
$keyDetails['key']);
$keyDetails['key']);
© All rights reserved. Zend Technologies, Inc.](https://image.slidesharecdn.com/strongcryptography-110521082240-phpapp02/85/Strong-cryptography-in-PHP-31-320.jpg)