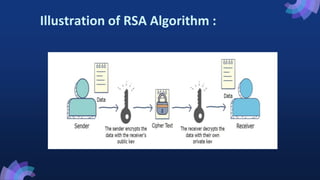
The document summarizes the RSA cryptosystem. It begins with an introduction to cryptography and the two types: symmetric and asymmetric. RSA is an asymmetric algorithm that uses a public and private key pair. The document provides an illustration of how RSA works and describes the key generation process where two prime numbers are multiplied to generate the modulus and keys. It also provides an example of encrypting a plaintext message using a public key and decrypting the ciphertext with a private key. Advantages of RSA include security while disadvantages are slower speed and large key sizes.