The document discusses access control lists (ACLs) including:
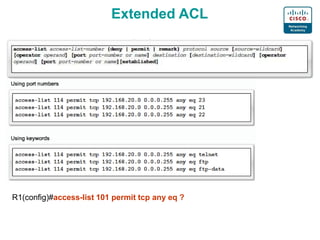
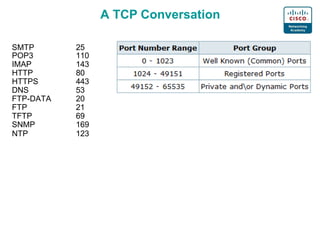
1. Common port numbers for protocols like SMTP, POP3, IMAP, HTTP, HTTPS, DNS, FTP, TFTP, SNMP, and NTP.
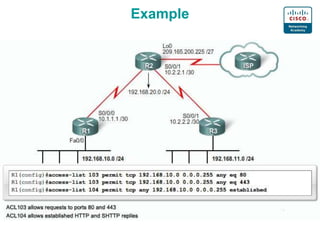
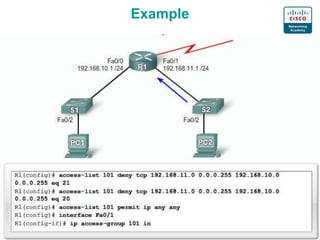
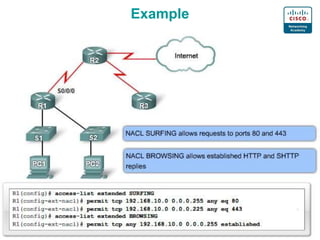
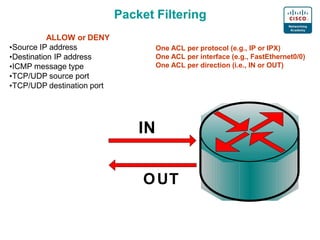
2. The basics of packet filtering using ACLs including allowing or denying based on source/destination IP addresses and ports.
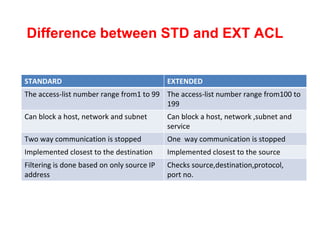
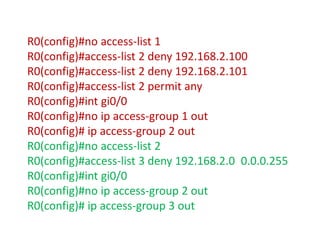
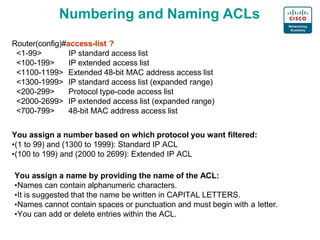
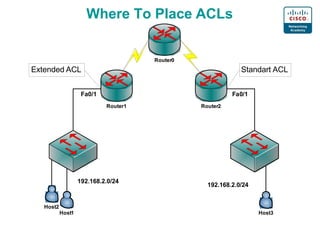
3. Numbering, naming, and applying standard and extended ACLs to interfaces for inbound and outbound traffic.

![Standard ACL
[no] access-list acl-num {deny|permit|remark} [source [source-wildcard]] [log]
Router#show access-lists
Standard IP access list 99
10 permit host 192.168.99.0
20 permit host 192.168.98.0
Router#conf t
Router(config)#no access-list 99
Router(config)#end
Router#show access-lists
Router#
Router(config)#access-list 10 remark Acces_to_LAN
Router(config)#access-list 10 permit 192.168.10.0
access-list 2 deny 192.168.10.1
access-list 2 permit 192.168.10.0 0.0.0.255
access-list 2 deny 192.168.0.0 0.0.255.255
access-list 2 permit 192.0.0.0 0.255.255.255
Router(config-if)#ip access-group {access-list-number | access-list-name} {in | out}
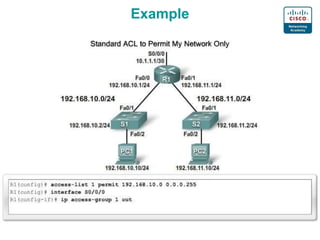
Router(config)#access-list 1 permit ip 192.168.10.0 0.0.0.255
Router(config)#interface FastEthernet0/0
Router(config-if)#ip access-group 1 out](https://image.slidesharecdn.com/aclcisco-200426085614/85/Acl-cisco-6-320.jpg)

![Naming ACL
Router(config)#ip access-list [standart | extended] name
Router(config-std-nacl)#[no] [num] {deny|permit|remark} …
Router(config)#ip access-list standard Bumburum
Router(config-std-nacl)#deny host 192.168.0.1
Router(config-std-nacl)#permit 192.168.0.0 0.0.0.255
Router#sh access-lists
Standard IP access list Bumburum
10 deny host 192.168.0.1
20 permit 192.168.0.0 0.0.0.255
Router(config-if)#ip access-group {access-list-number | access-list-name} {in | out}
Router(config-if)#ip access-group Bumburum out](https://image.slidesharecdn.com/aclcisco-200426085614/85/Acl-cisco-12-320.jpg)
![Edit ACL
Router#show access-lists {acl-num|name}
Router#sh access-lists 99
Standard IP access list 99
10 permit host 192.168.9.9
20 permit host 192.168.9.11
Router(config)#ip access-list {standart | extended} {acl-num|name}
Router(config-std-nacl)#[no] [num] {deny|permit|remark} …
Router#sh access-lists standard 99
Router(config-std-nacl)#15 permit host 192.168.9.10
Router#sh access-lists 99
Standard IP access list 99
10 permit host 192.168.9.9
15 permit host 192.168.9.10
20 permit host 192.168.9.11](https://image.slidesharecdn.com/aclcisco-200426085614/85/Acl-cisco-13-320.jpg)