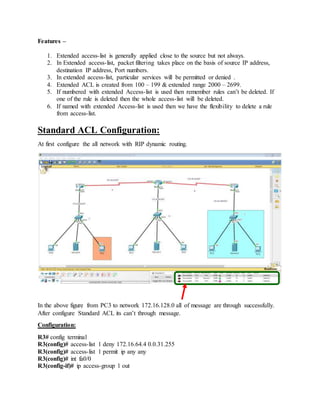
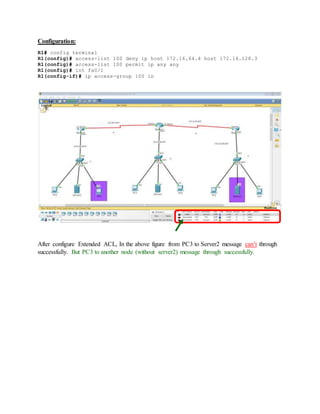
The document is a lab report that describes configuring standard and extended access control lists (ACLs) in a computer network. It defines standard ACLs as using only source IP addresses to permit or deny all protocol traffic between an entire network or sub-network. Extended ACLs can distinguish different protocol traffic like TCP, UDP, and HTTPS using source/destination IP addresses and port numbers to permit or deny specific services. The report provides examples of configuring a standard ACL to deny all traffic from one subnet and an extended ACL to deny traffic between a specific host and server.