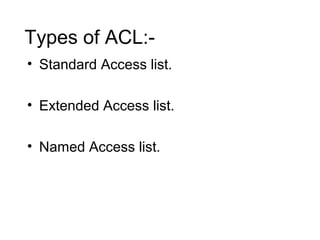
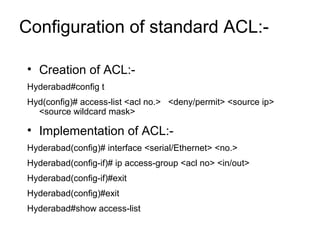
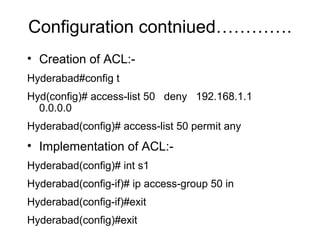
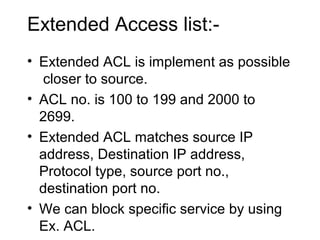
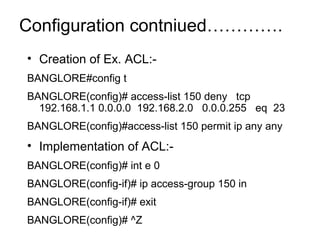
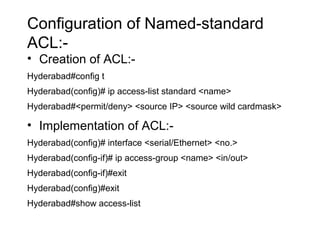
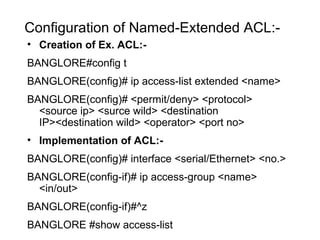
ACL (Access Control List) is a layer 3 security feature that controls traffic flow between routers by matching packets based on various criteria like source/destination IP addresses, protocols, and port numbers. There are standard, extended, and named ACLs that provide different matching capabilities. ACLs are configured on router interfaces using access lists and access groups to filter inbound or outbound traffic.