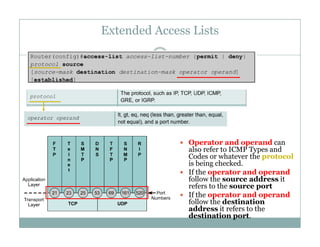
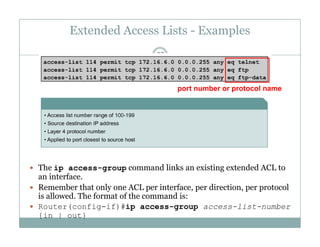
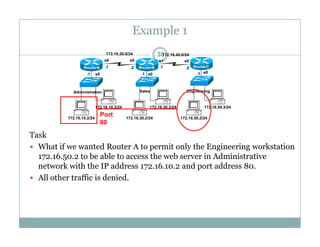
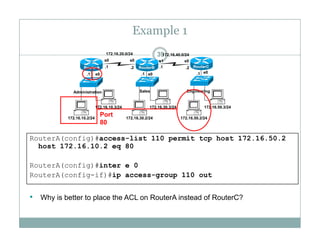
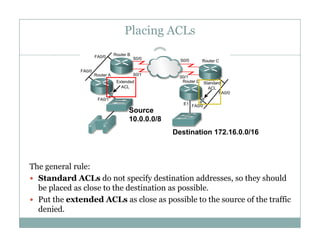
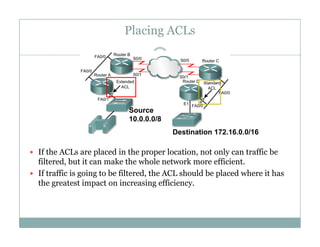
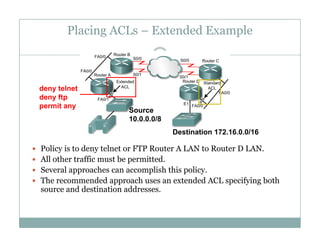
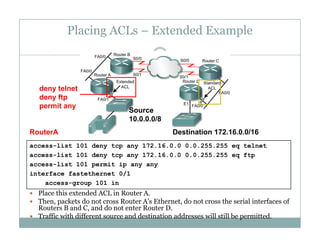
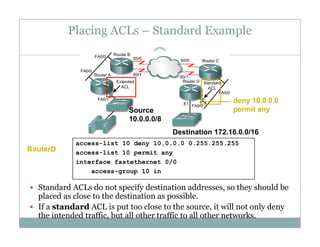
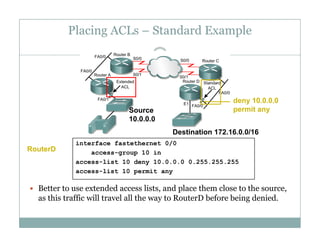
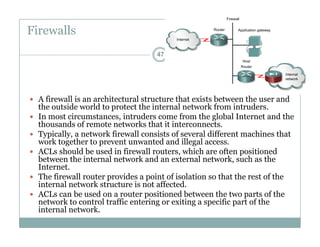
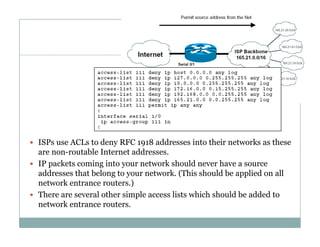
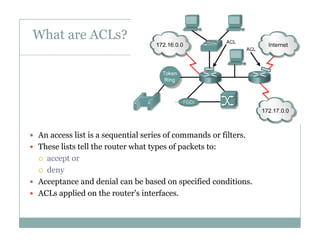
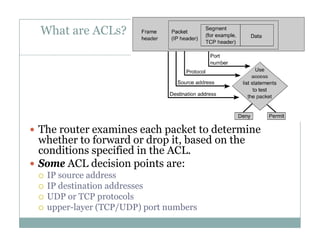
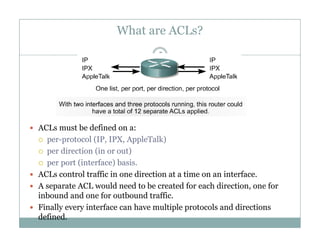
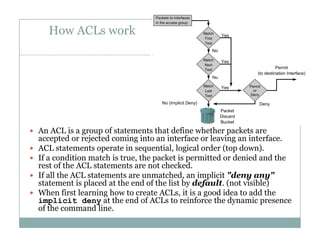
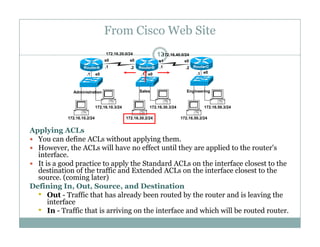
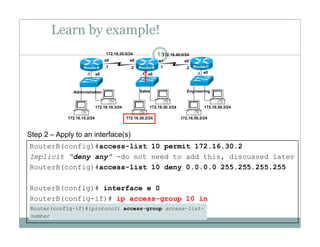
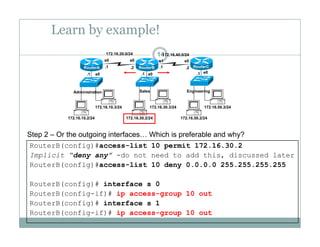
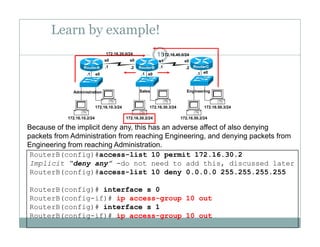
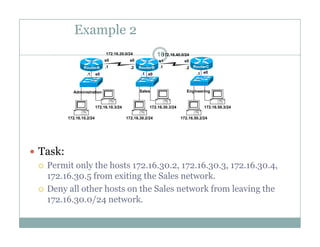
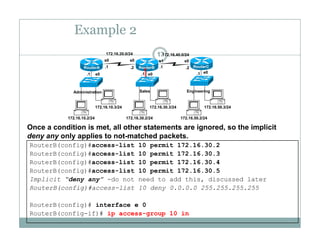
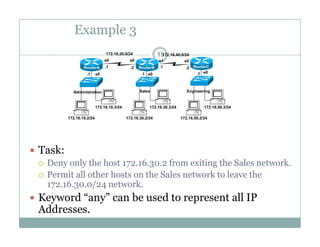
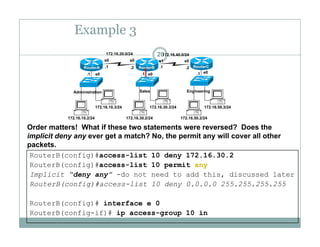
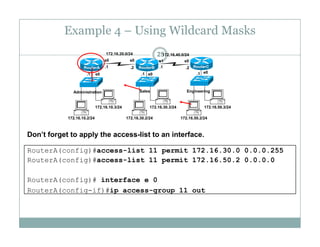
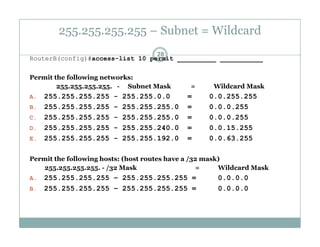
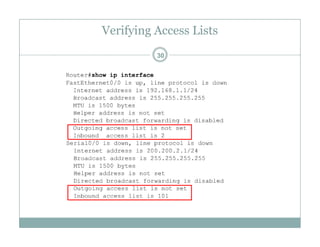
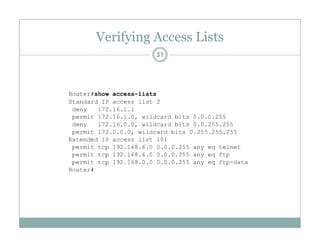
An access control list (ACL) is a sequential list of permit or deny statements that apply to network traffic and are used to control what traffic is allowed or denied on a network interface. ACLs can filter traffic based on source/destination IP addresses, protocols, and port numbers. Standard ACLs filter only on source IP addresses while extended ACLs can filter on additional parameters. ACLs are applied to interfaces using the ip access-group command to implement the access control on inbound or outbound traffic on that interface.








![Standard ACL
33
W ill h i
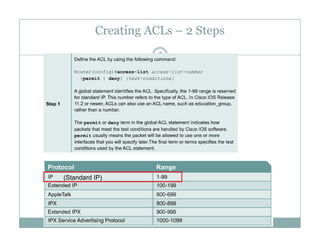
The full syntax of the standard ACL command is:
Router(config)#access-list access-list-number {deny |
We will see why in a moment.
Router(config)#access list access list number {deny |
permit} source [source-wildcard ] [log]
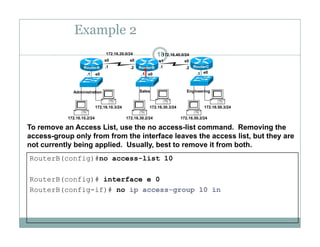
The no form of this command is used to remove a standard ACL. This is
h ( l i AC !)the syntax: (Deletes entire ACL!)
Router(config)#no access-list access-list-number](https://image.slidesharecdn.com/modul5accesscontrollist-190422163531/85/Modul-5-access-control-list-33-320.jpg)