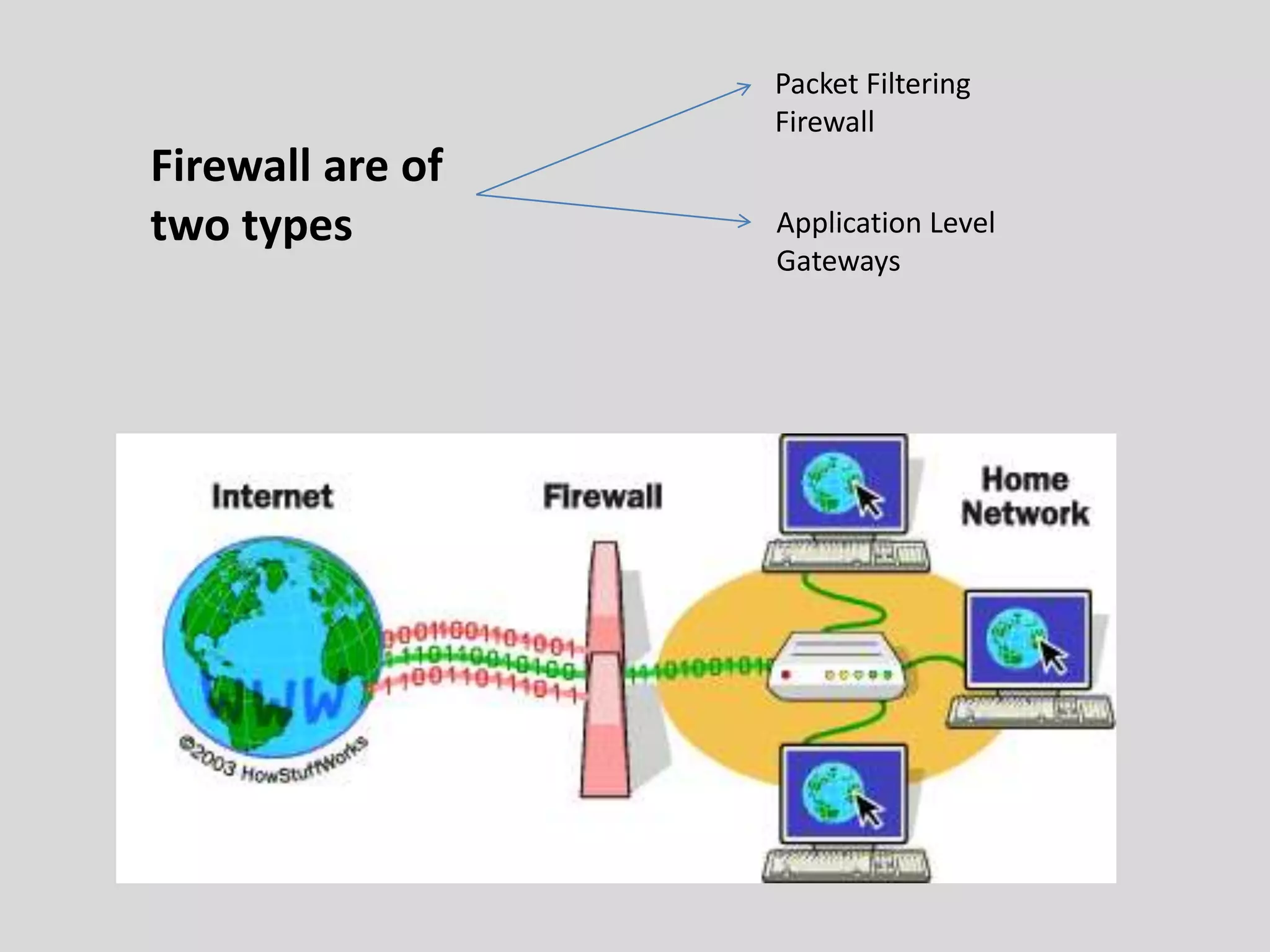
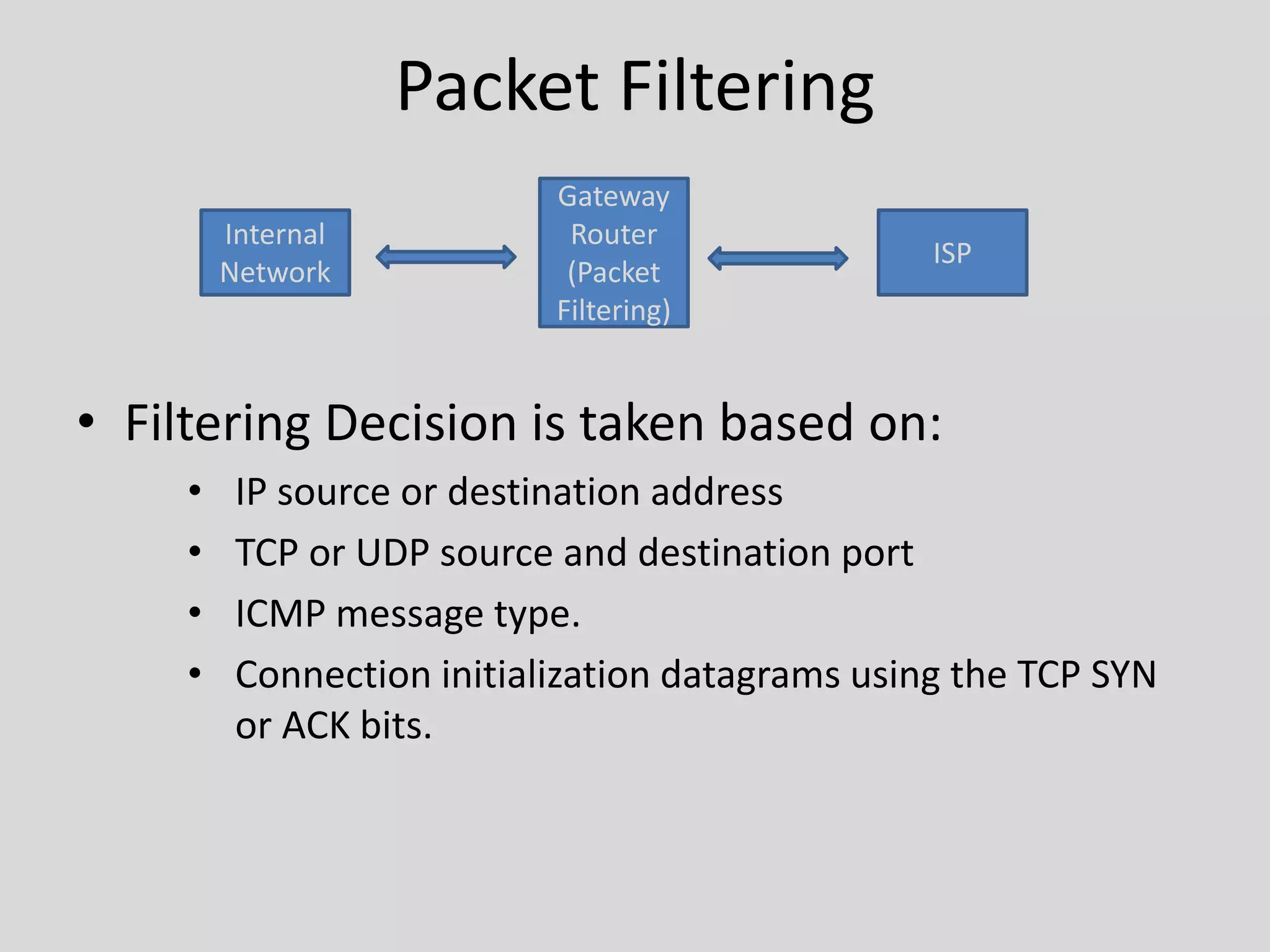
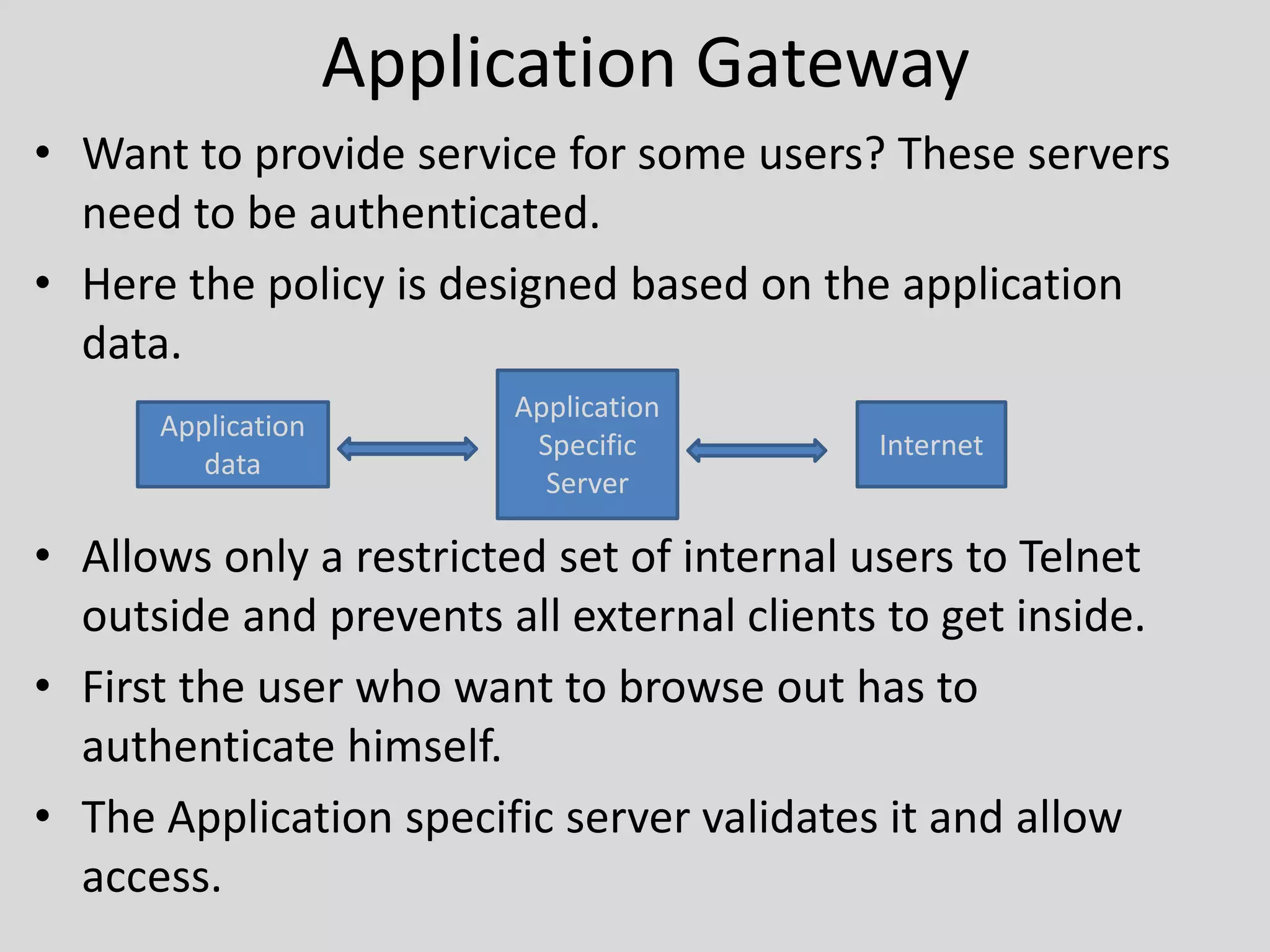
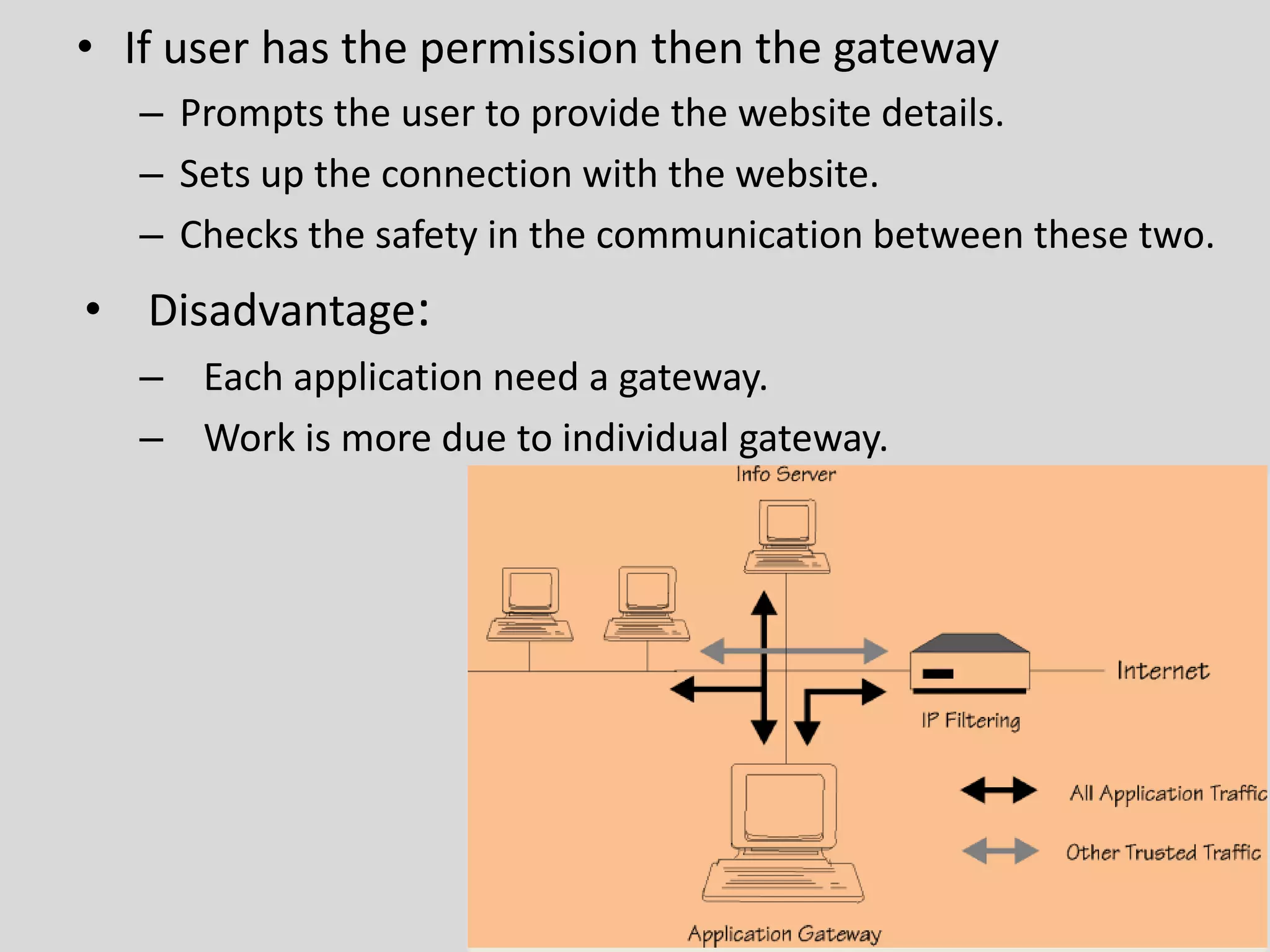
Firewalls provide protection for the entry and exit points of computer networks. There are two types of firewalls: packet filtering firewalls and application-level gateways. Packet filtering firewalls make filtering decisions based on IP addresses and port numbers, blocking or allowing network traffic based on these attributes. Application-level gateways provide additional security by only allowing authenticated internal users to access specific external applications and preventing external clients from entering the internal network. Firewalls help secure computer networks by controlling inbound and outbound network traffic.