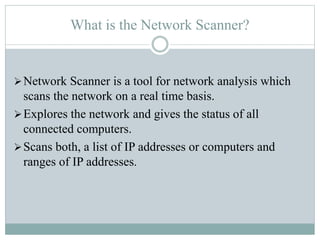
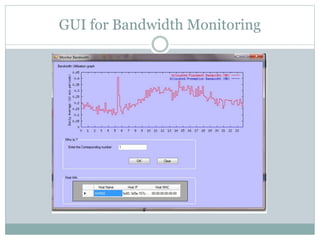
This document describes a network scanner project. The network scanner scans a network in real-time to explore connected computers and provide their status. It allows network administrators to efficiently analyze and monitor the network. Key features include classifying network components, bandwidth monitoring and control, and remote access capabilities. The project will be implemented in phases, beginning with a graphical user interface module and also including address calculation, bandwidth capturing, and remote access modules.