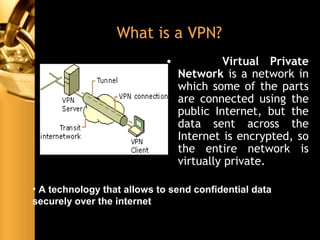
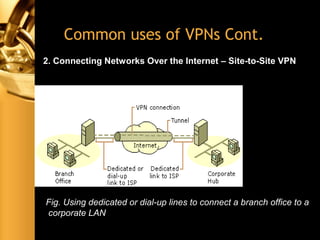
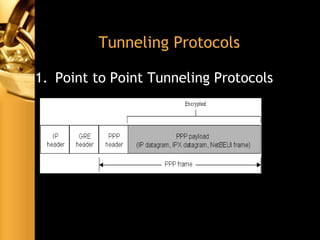
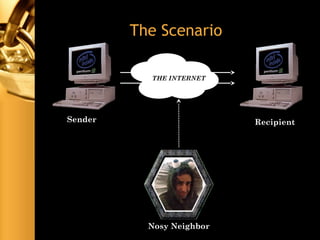
The document discusses various aspects of network security, including threats (passive and active), firewalls (their types, functions, and policies), and virtual private networks (VPNs) with a focus on tunneling protocols like PPTP and L2TP. It highlights the importance of firewalls in protecting networks from unauthorized access and describes the limitations and challenges associated with packet filtering. Additionally, the document explains the function of IPSec in securing data transfer across networks.