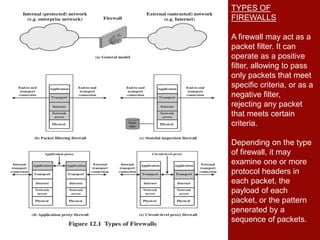
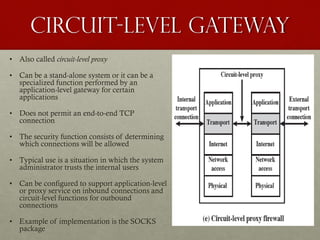
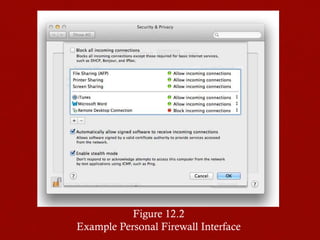
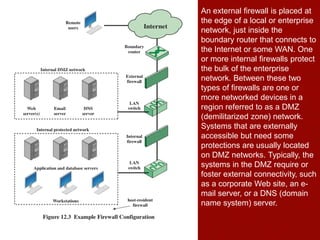
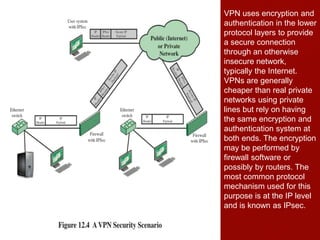
This document discusses firewalls, including their role and characteristics. Firewalls establish a controlled link between an internal network and the internet to protect the internal network. There are various types of firewalls such as packet filtering, stateful inspection, application-level gateways, and circuit-level gateways. Firewalls can be located individually on hosts, or in distributed configurations with internal and external firewalls and demilitarized zones (DMZs) to host public-facing servers. Virtual private networks (VPNs) and distributed firewalls provide additional security. The document provides examples of common firewall locations and topologies used in small to large organizations.