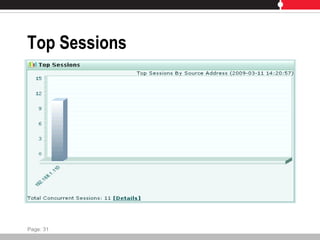
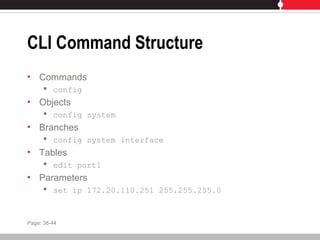
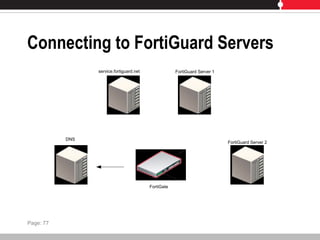
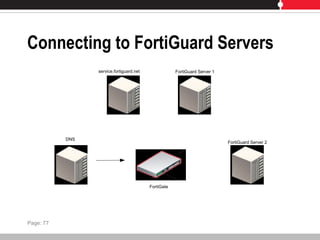
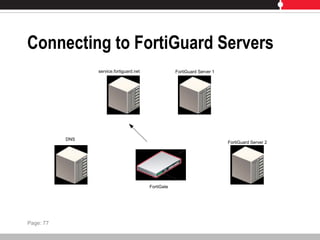
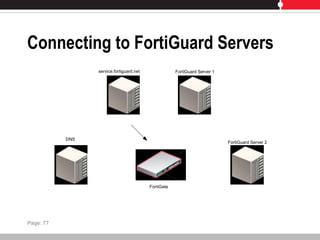
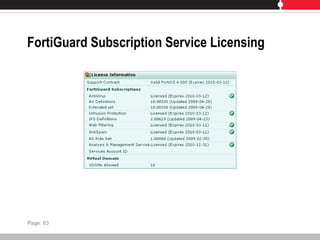
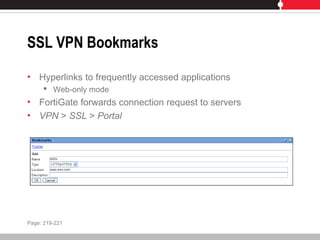
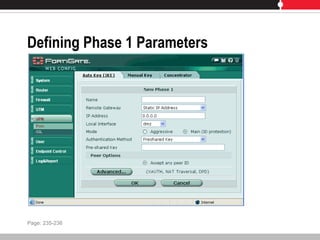
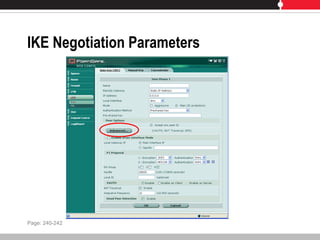
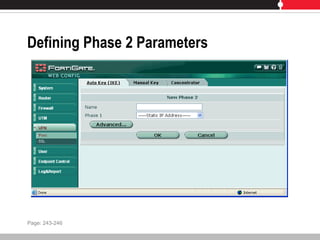
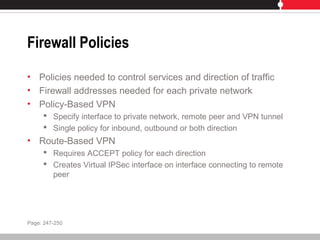
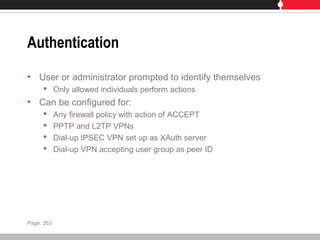
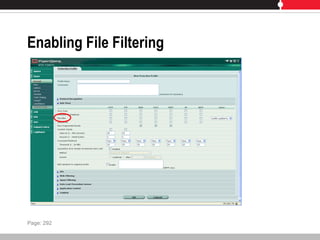
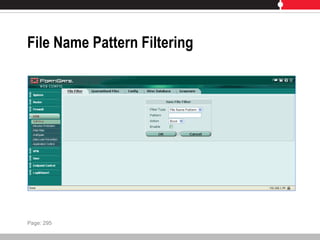
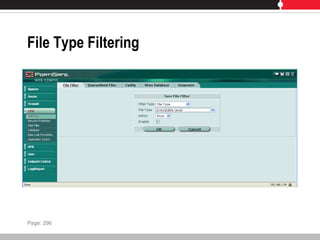
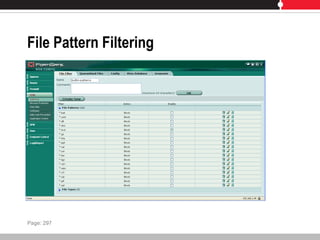
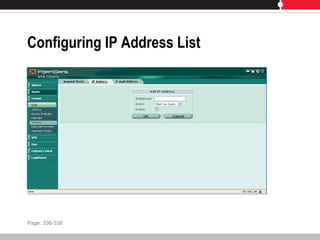
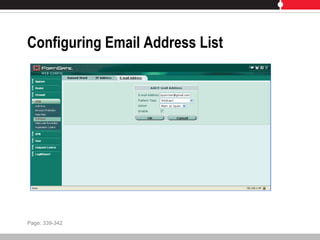
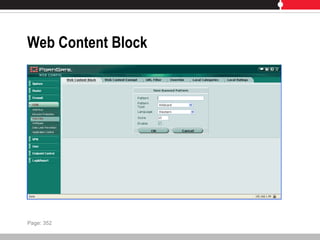
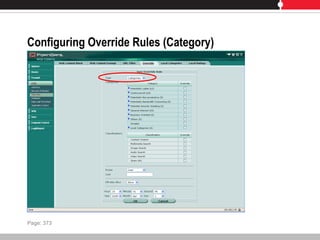
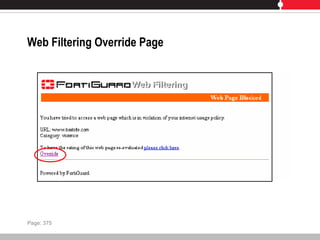
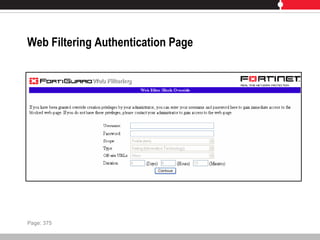
This document provides an overview of FortiGate multi-threat security systems and their administration, content inspection, and basic VPN capabilities. It discusses FortiGate devices, FortiGuard subscription services, logging and alerts capabilities, firewall policies, basic VPN configurations, authentication, antivirus, spam filtering, and web filtering. The document includes descriptions of FortiGate portfolio models, FortiGuard dynamic updates, FortiManager and FortiAnalyzer management products, logging levels, and log storage locations.