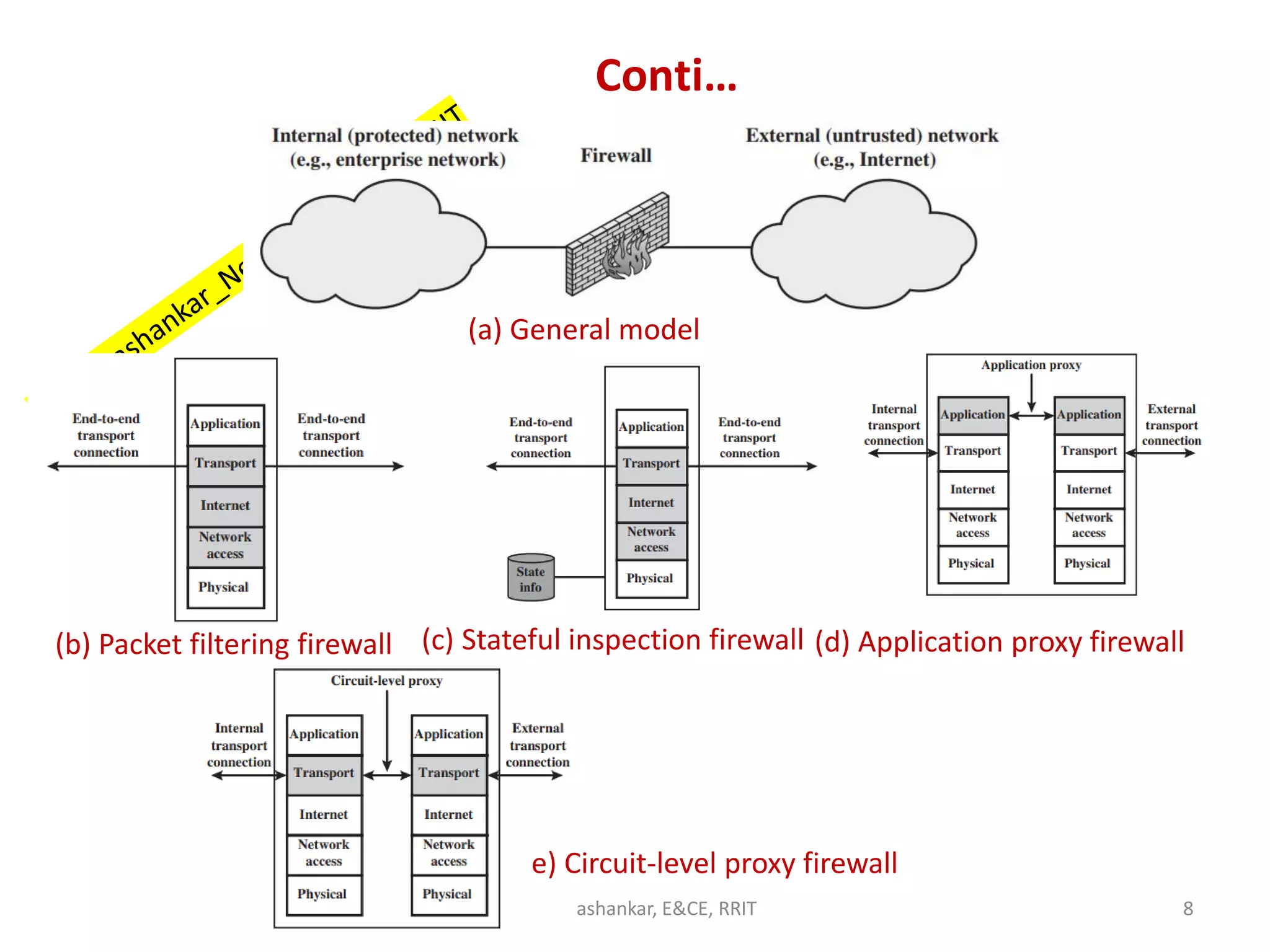
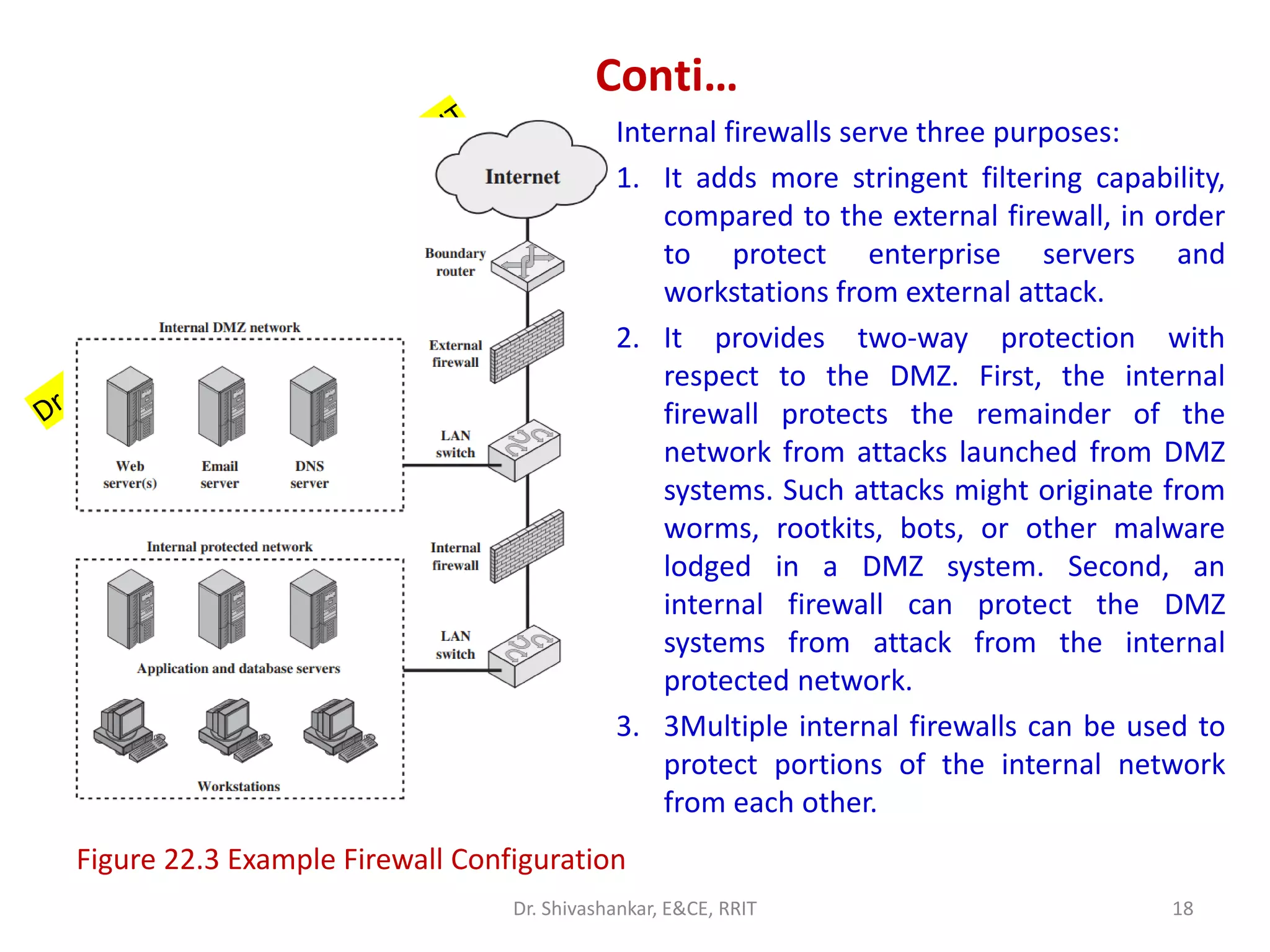
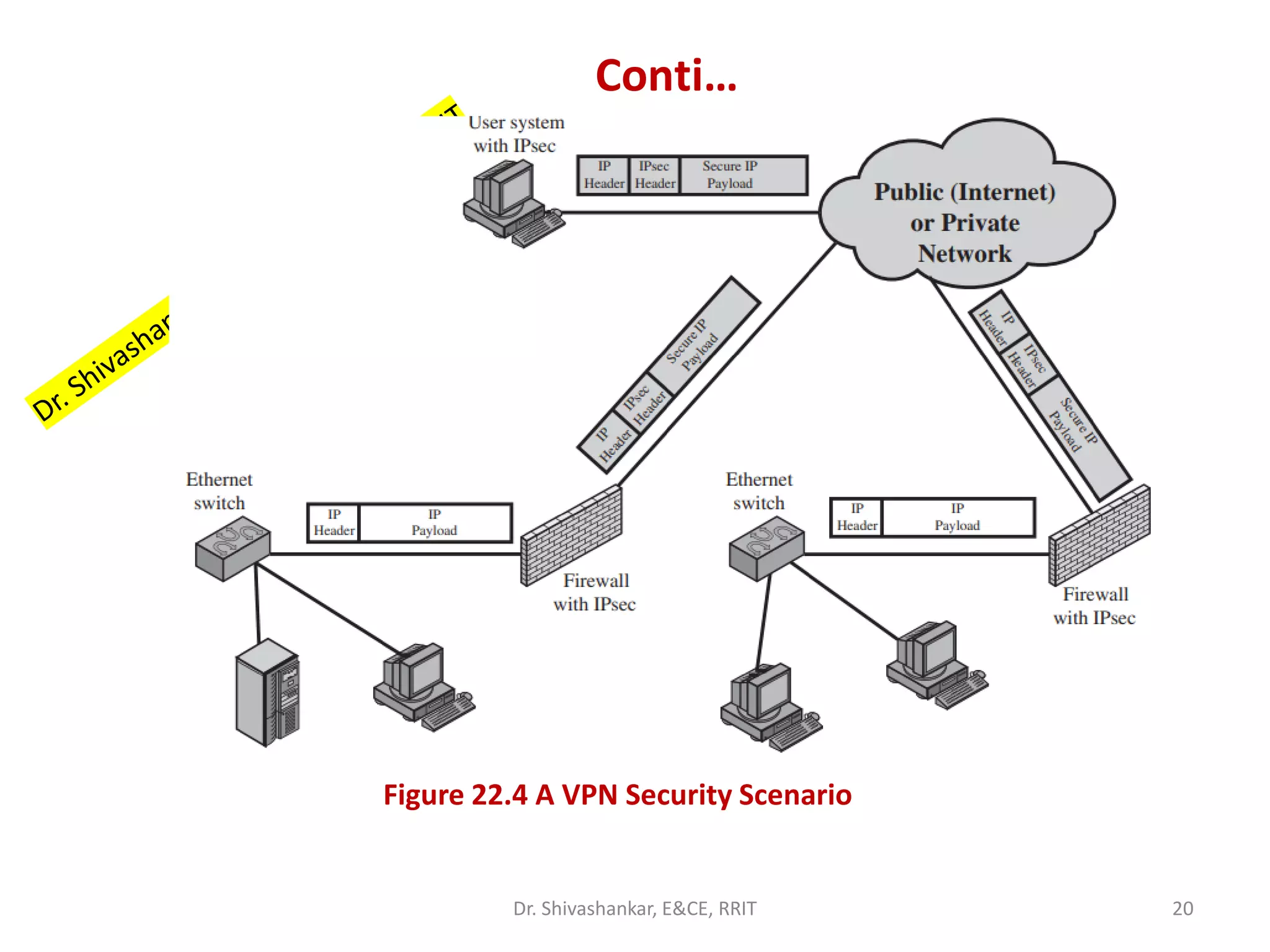
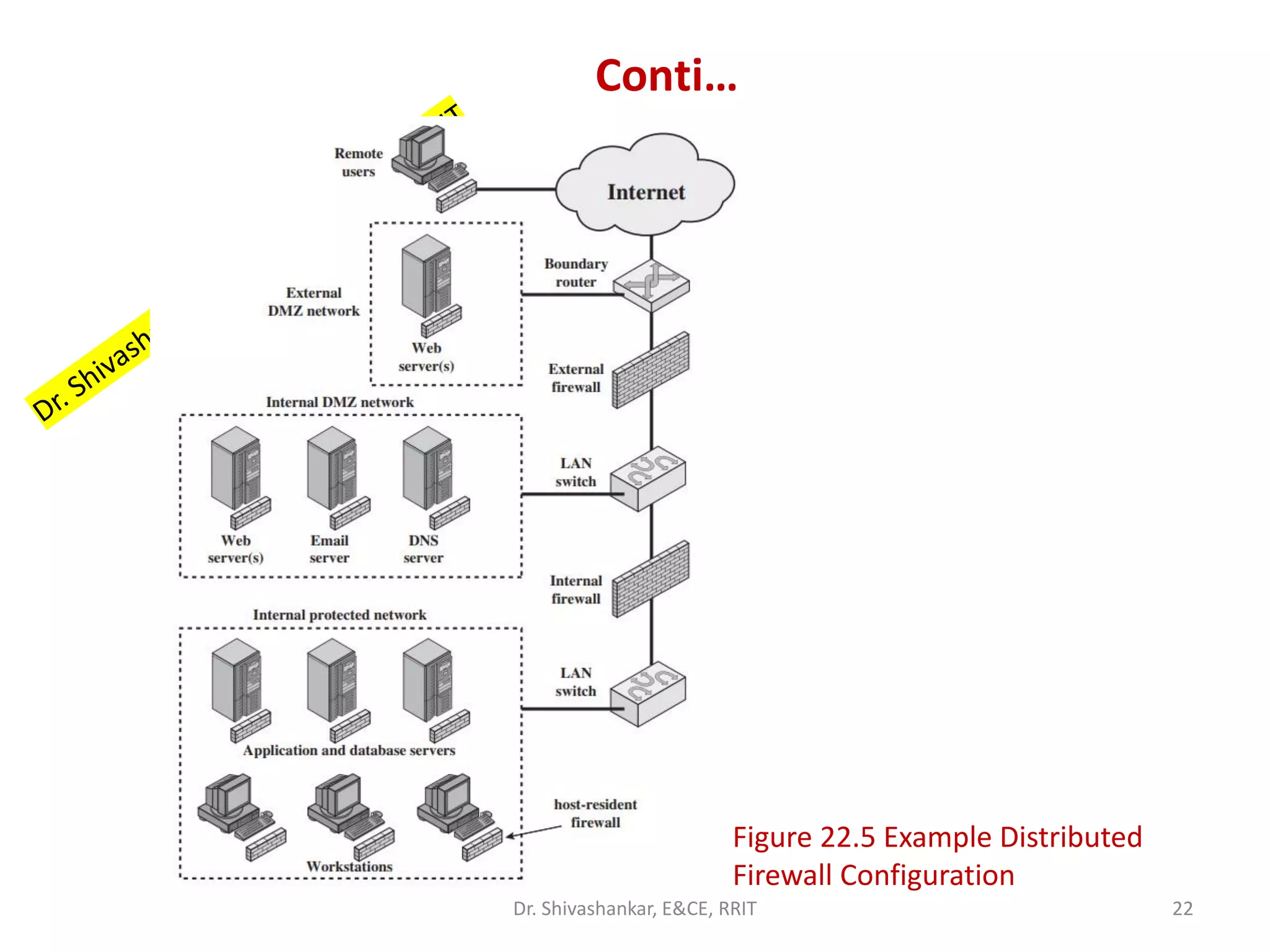
This document discusses network security and firewalls. It provides an overview of different types of firewalls including packet filtering firewalls, stateful inspection firewalls, application-level gateways, and circuit-level gateways. It also discusses firewall configuration options such as bastion hosts, host-based firewalls, personal firewalls, demilitarized zone networks, and distributed firewall setups. The key purpose of firewalls is to control access and enforce a site's security policy by filtering network traffic based on security rules.