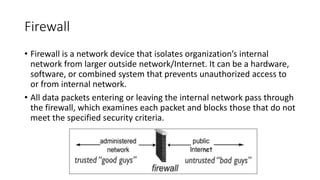
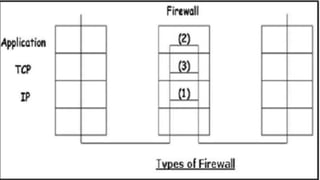
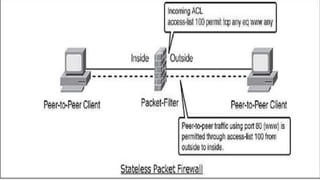
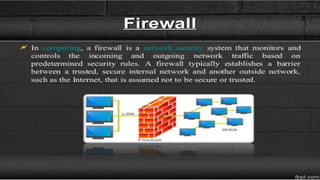
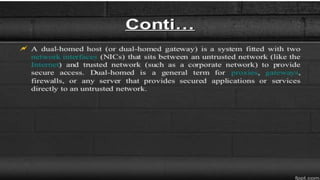
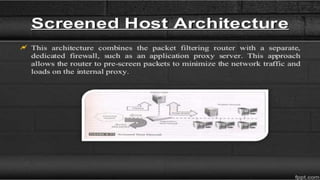
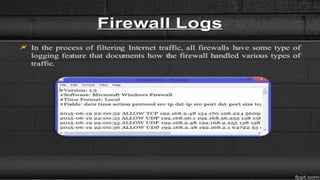
Firewalls are network security devices that control incoming and outgoing network traffic based on a set of security rules. There are three main types of firewalls: packet filtering firewalls, which filter network traffic at the packet level; application-level firewalls, which filter traffic at the application layer; and circuit-level firewalls, which monitor traffic connections and sessions. Firewalls provide security benefits but also have limitations, such as not preventing unauthorized internal access or protecting against social engineering attacks.