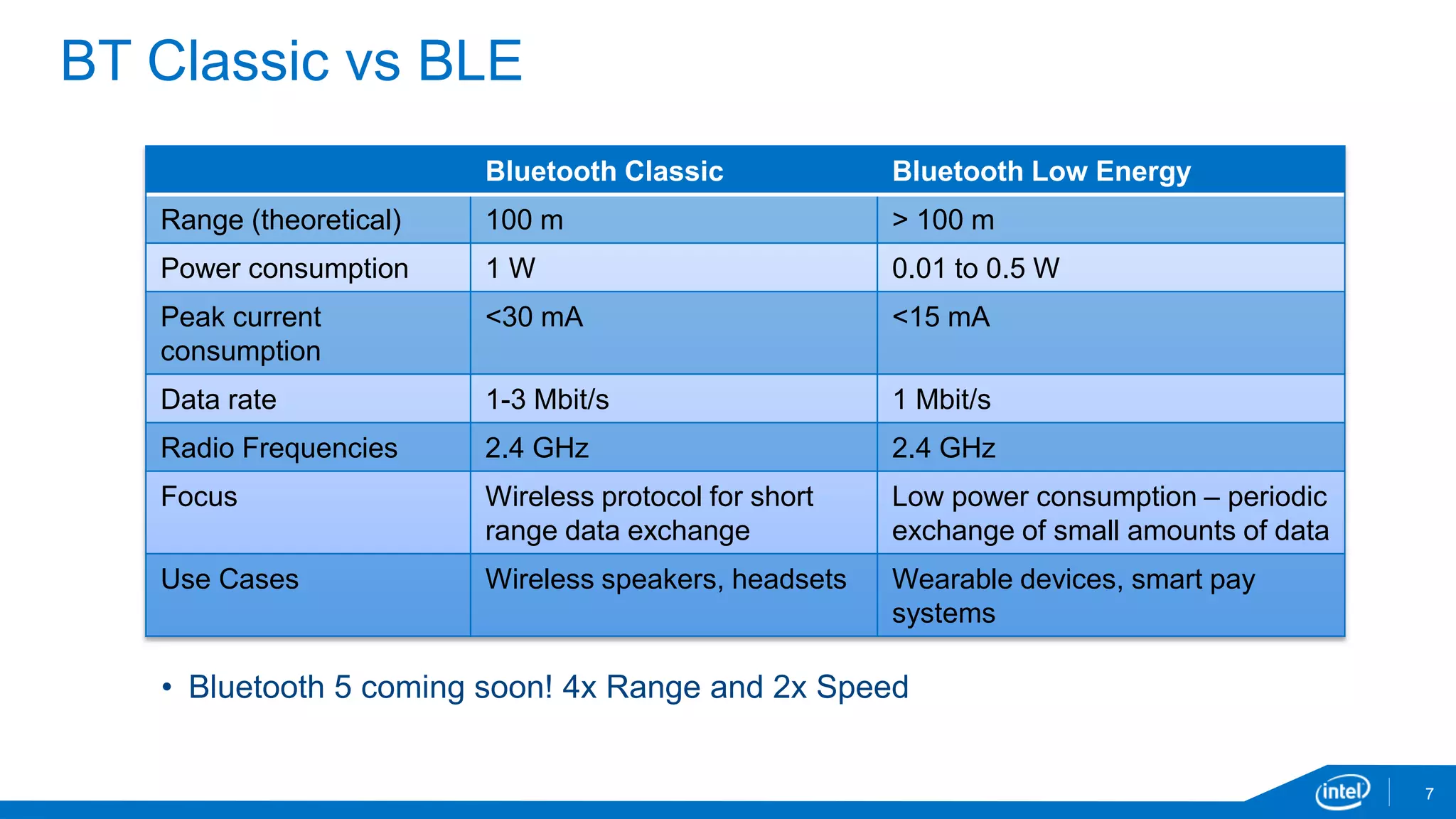
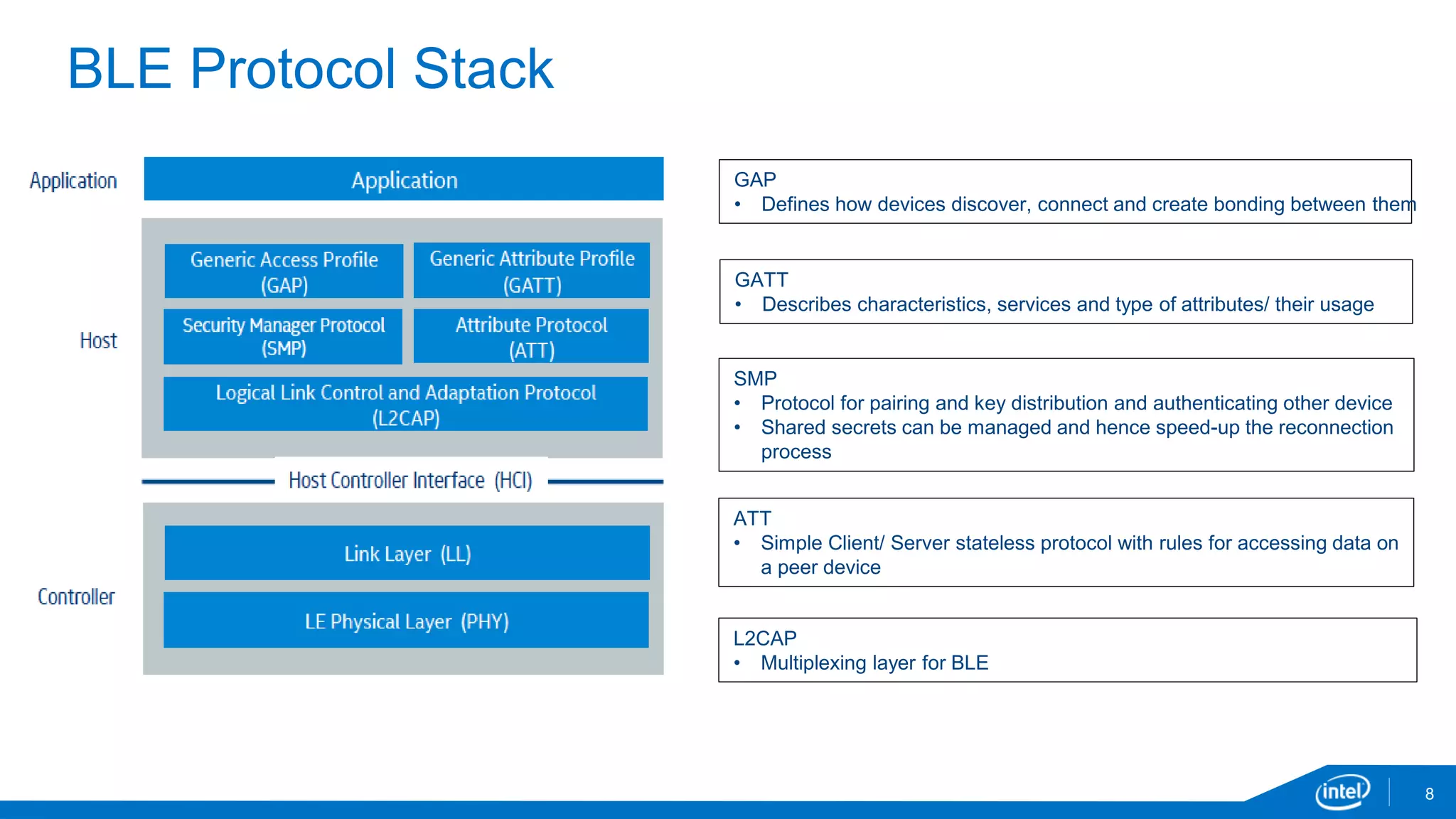
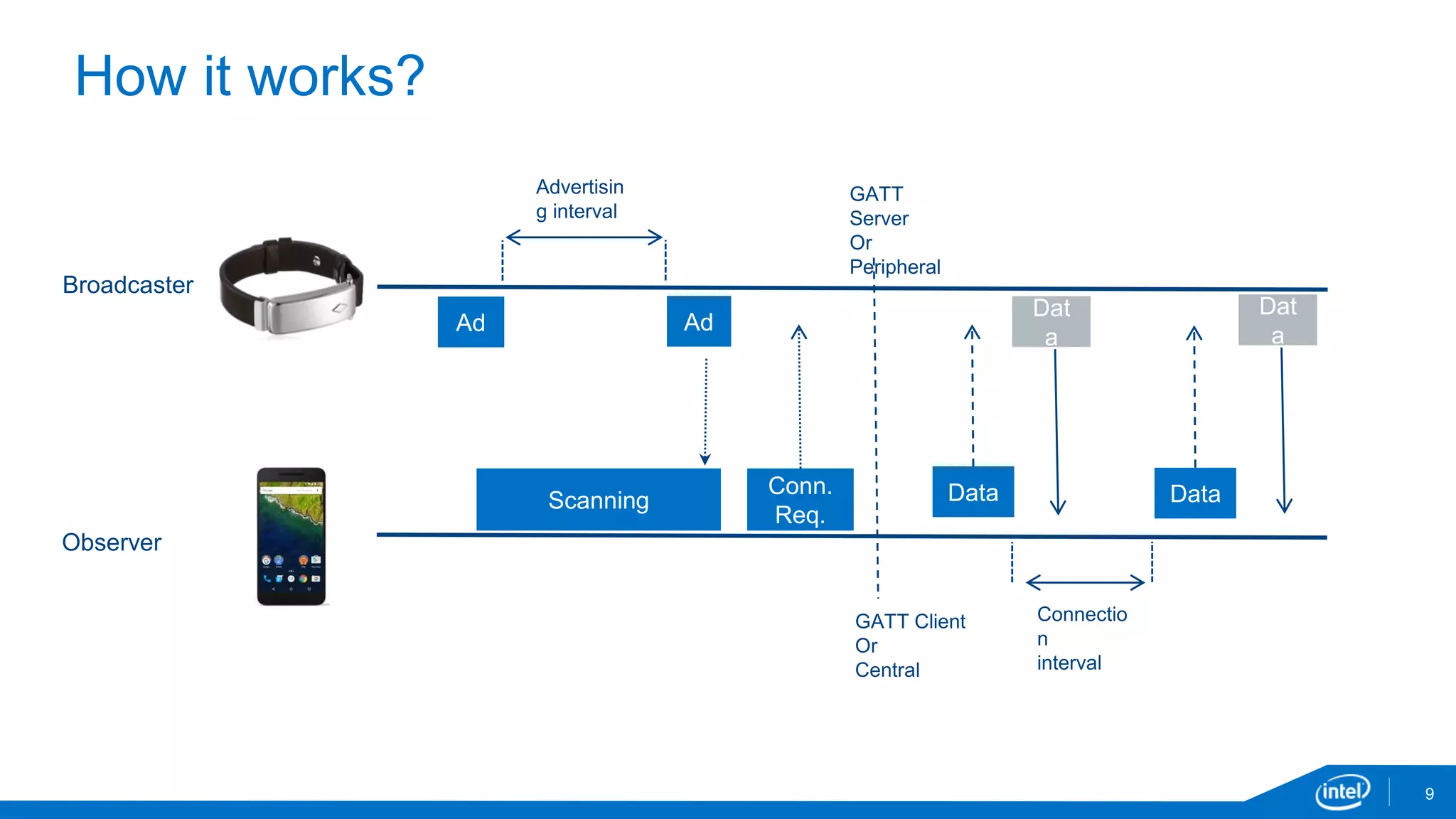
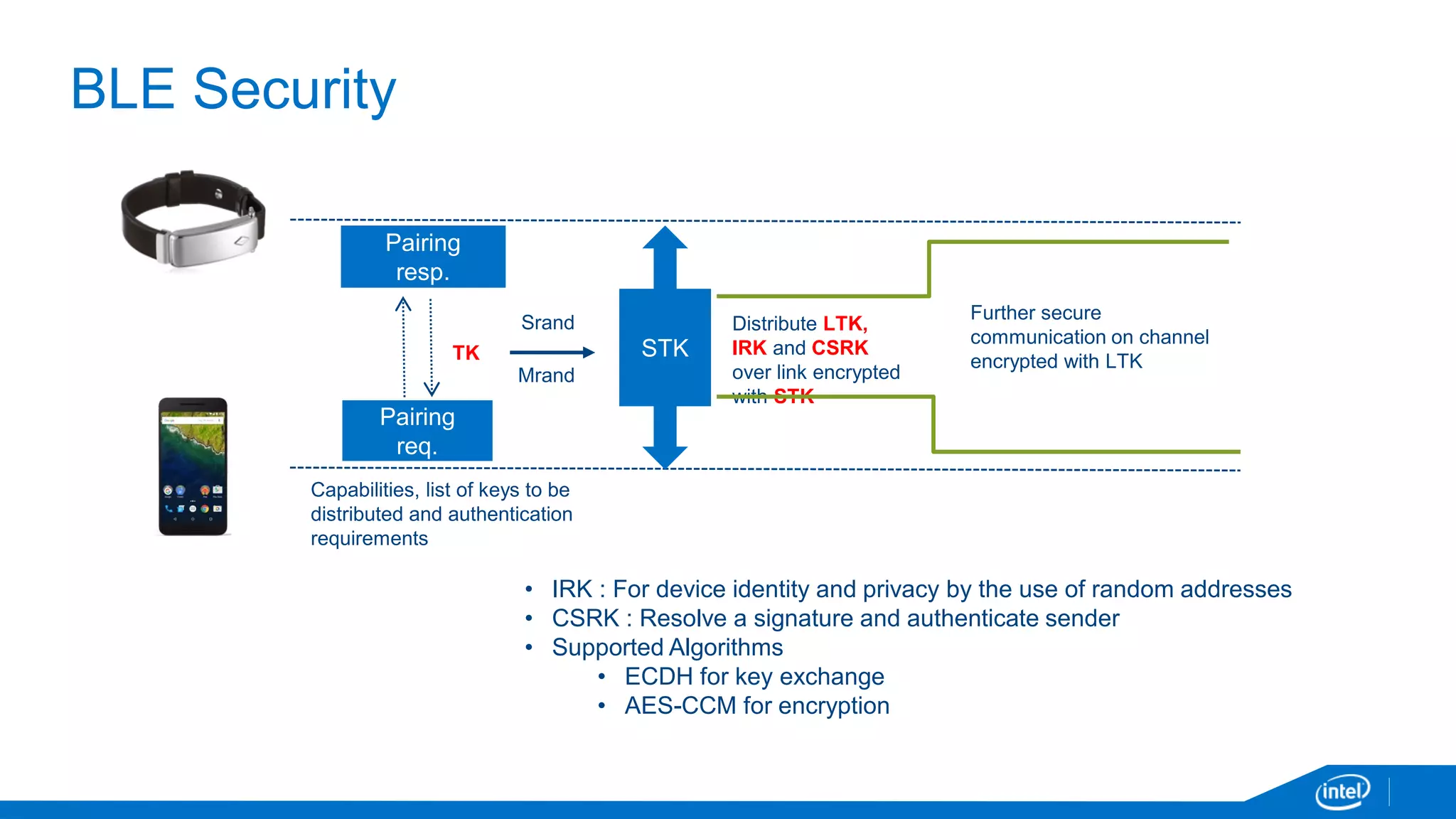
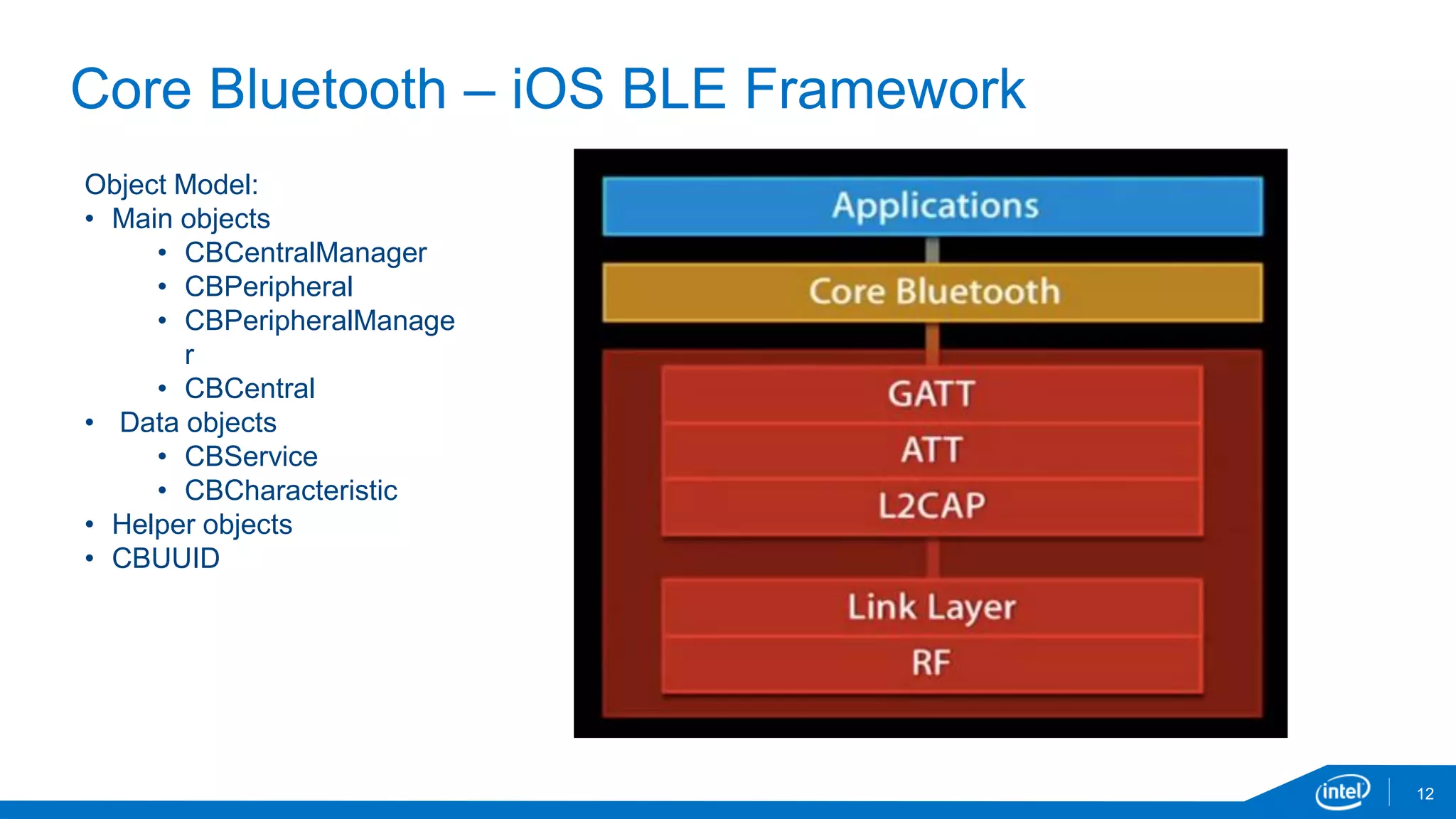
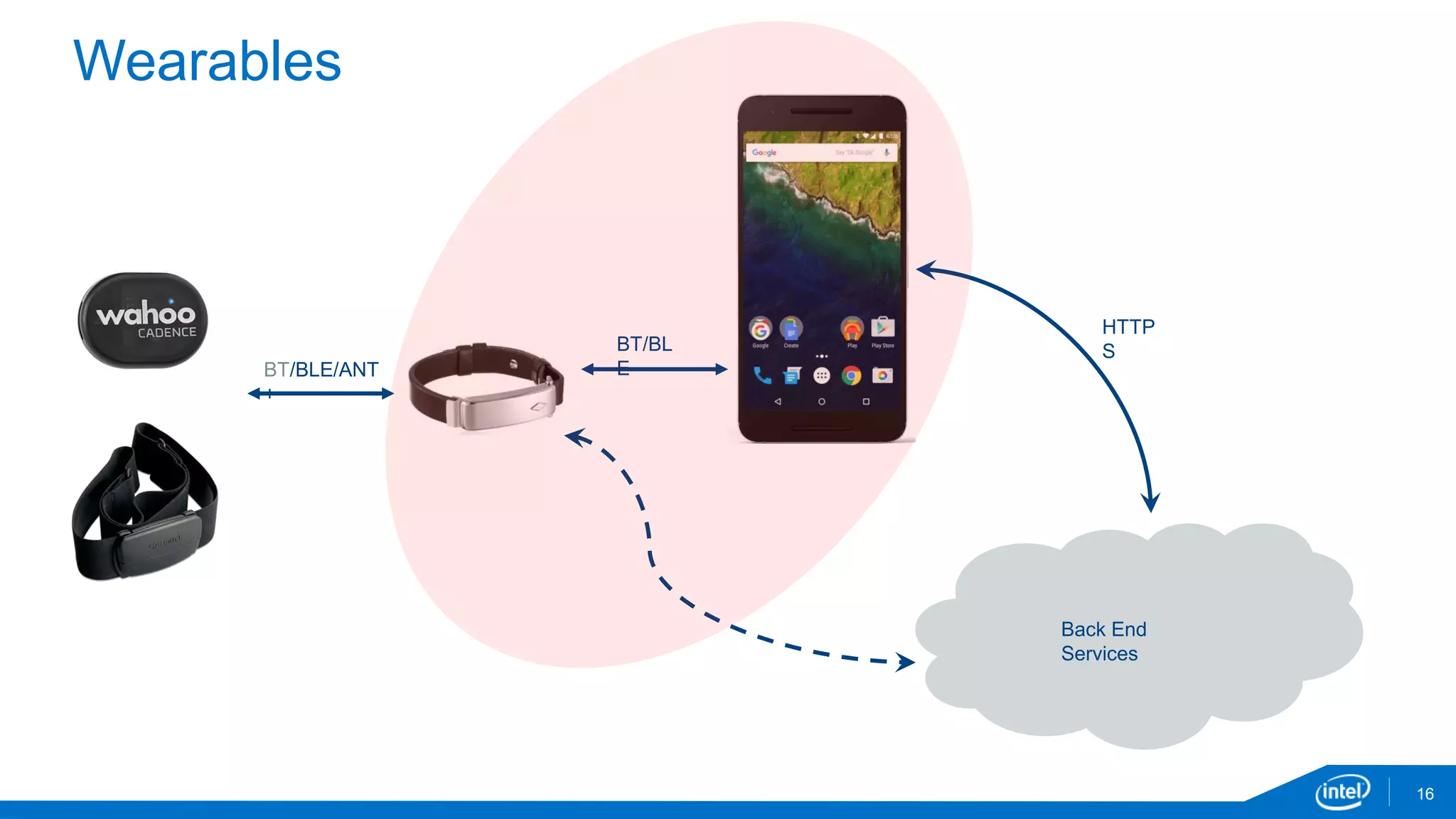
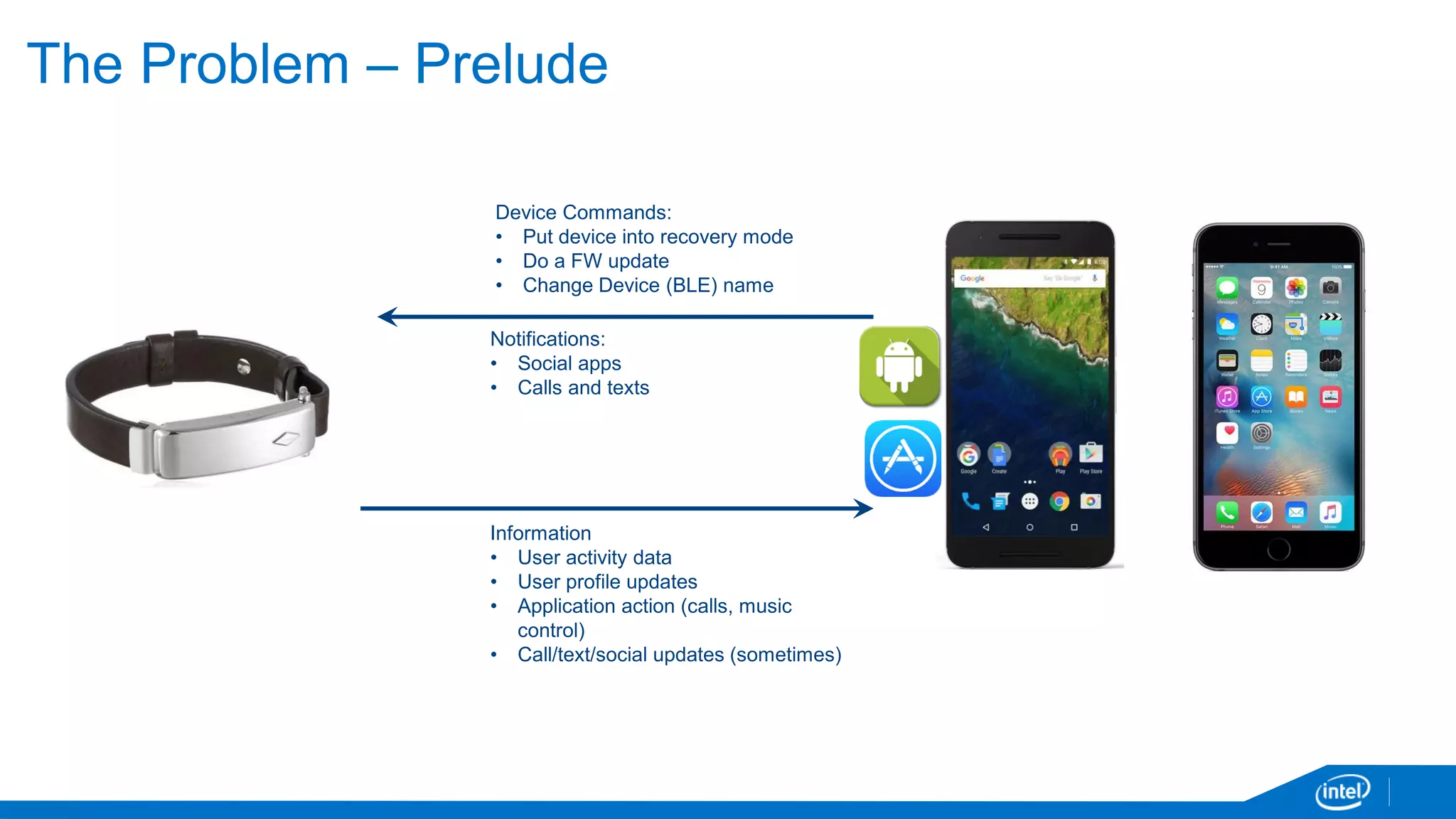
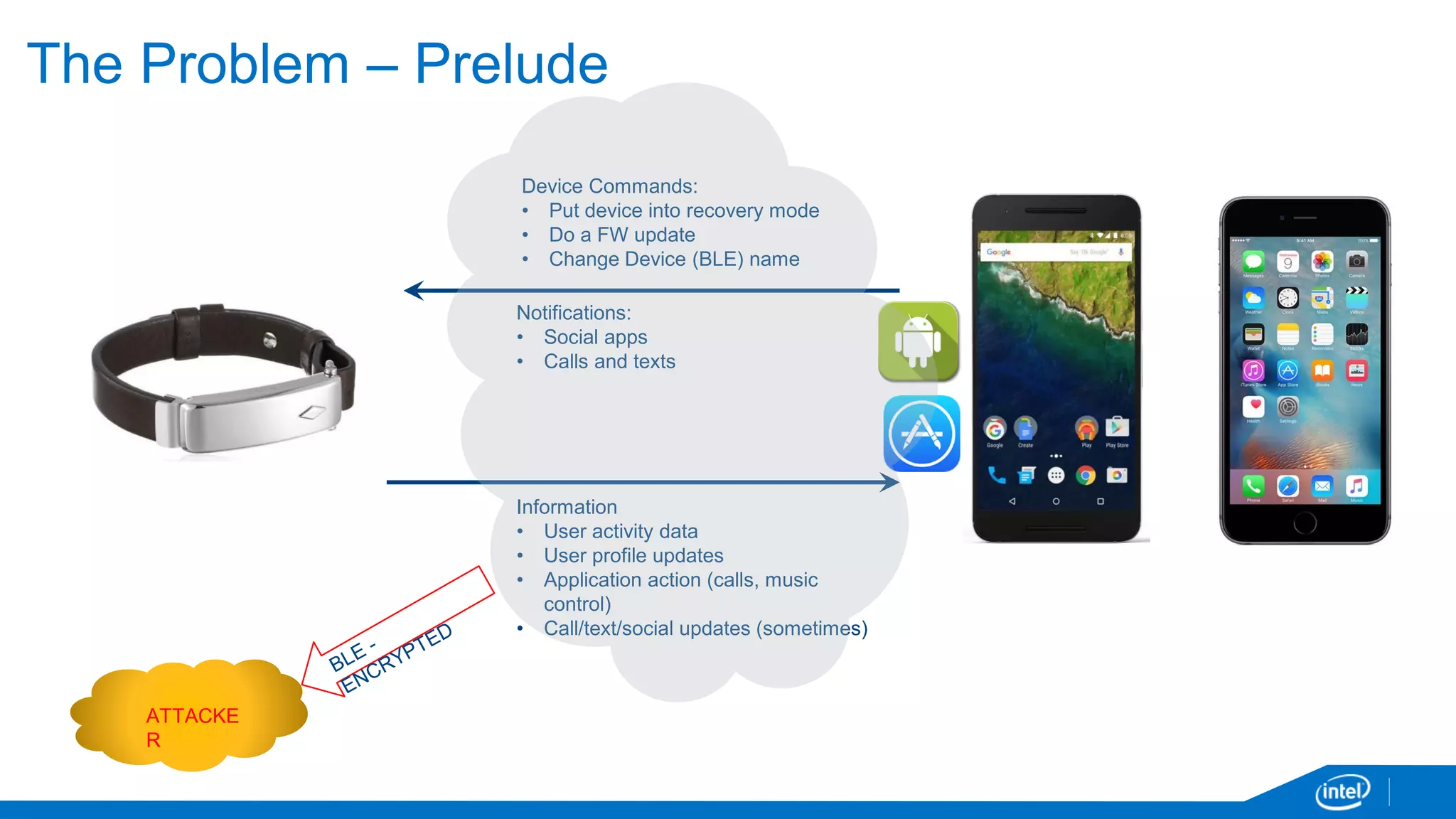
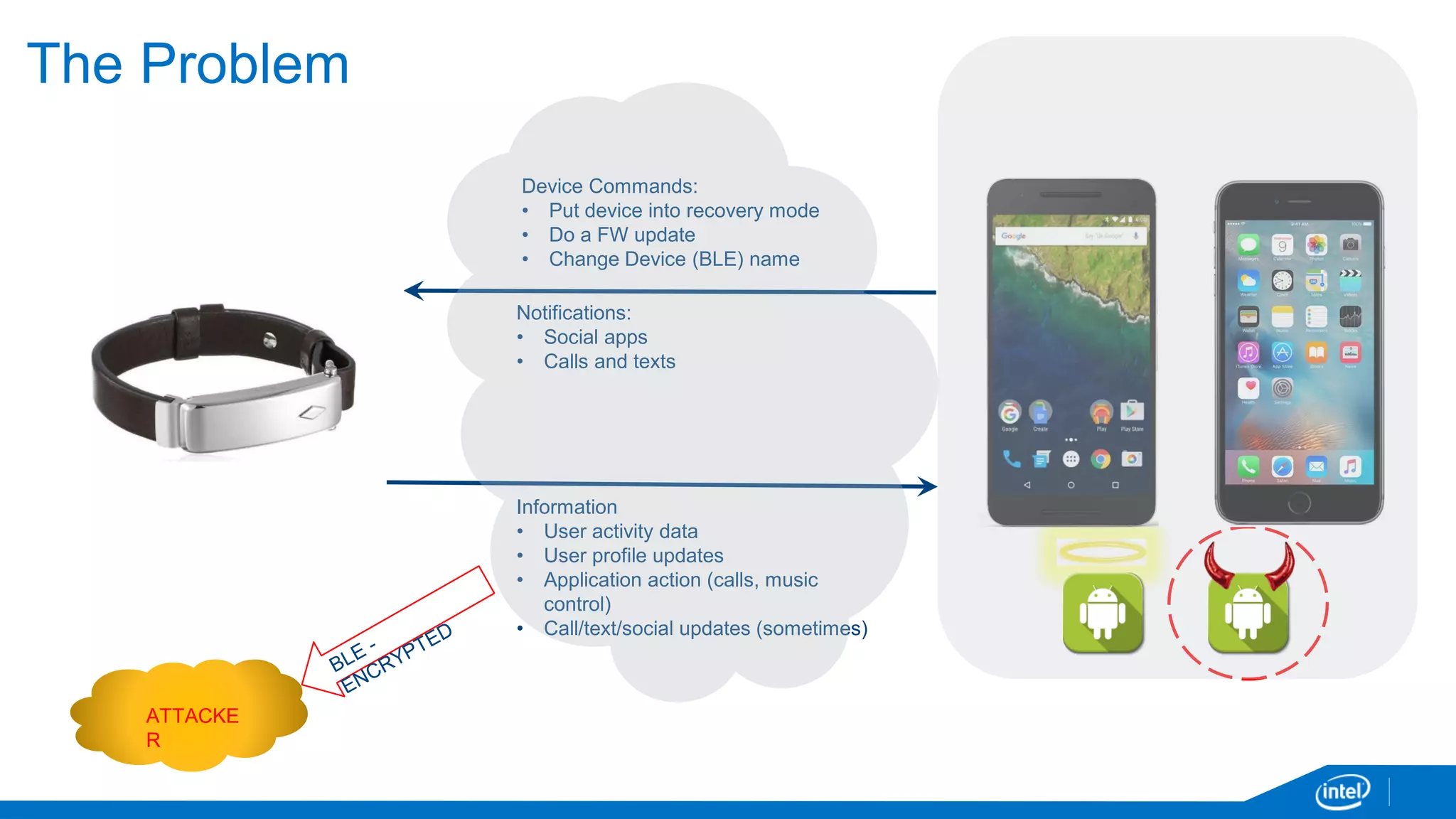
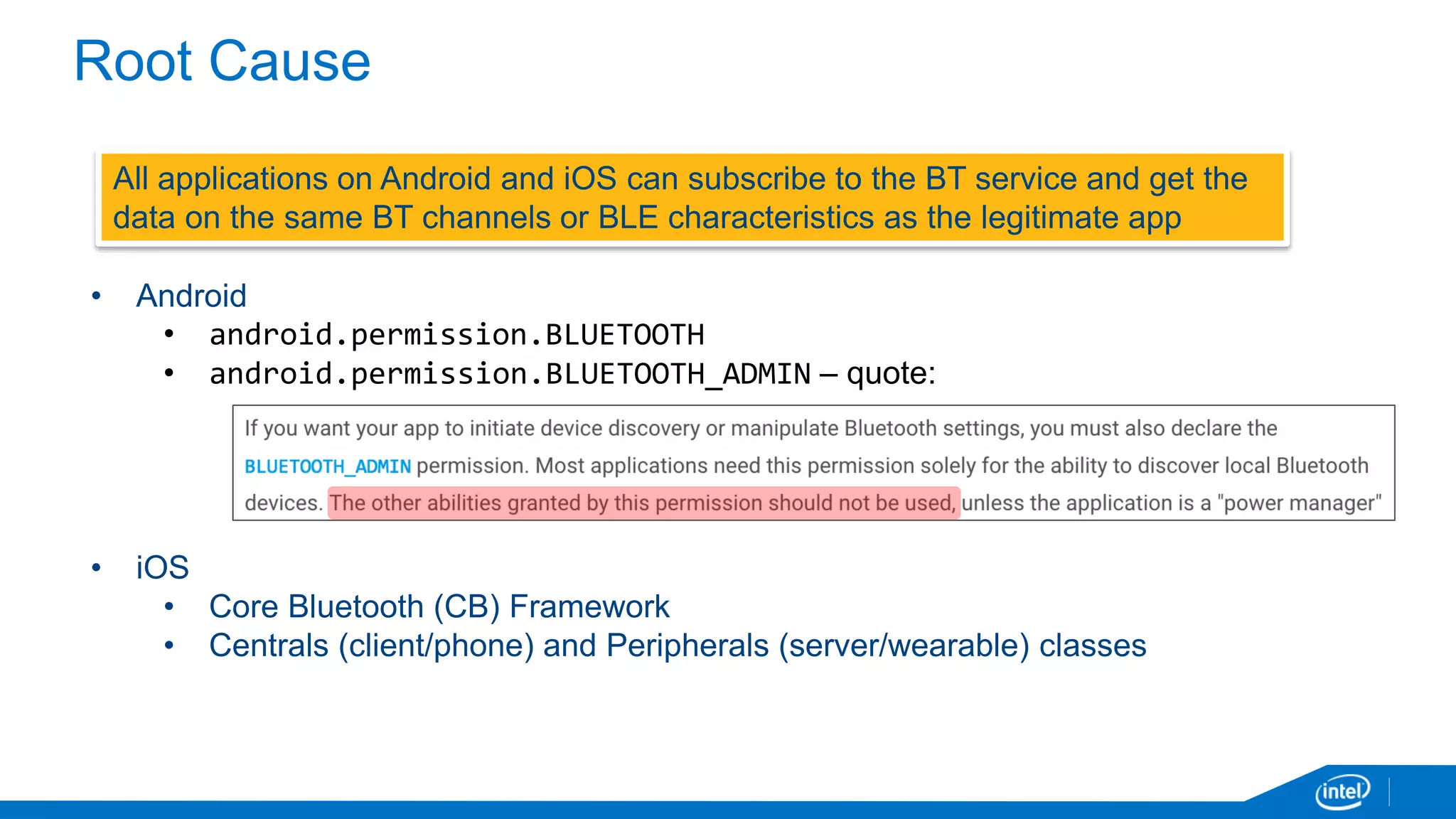
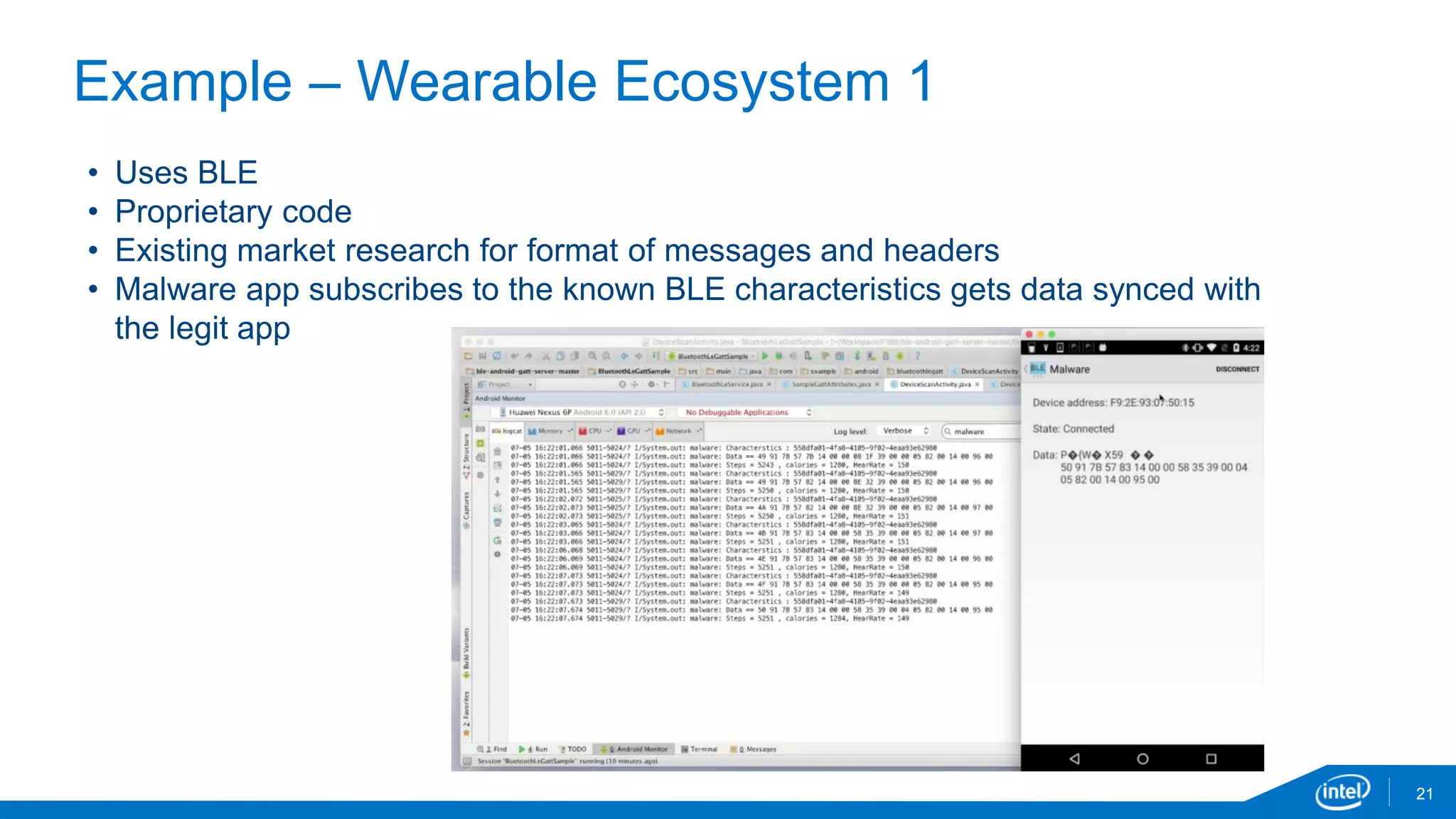
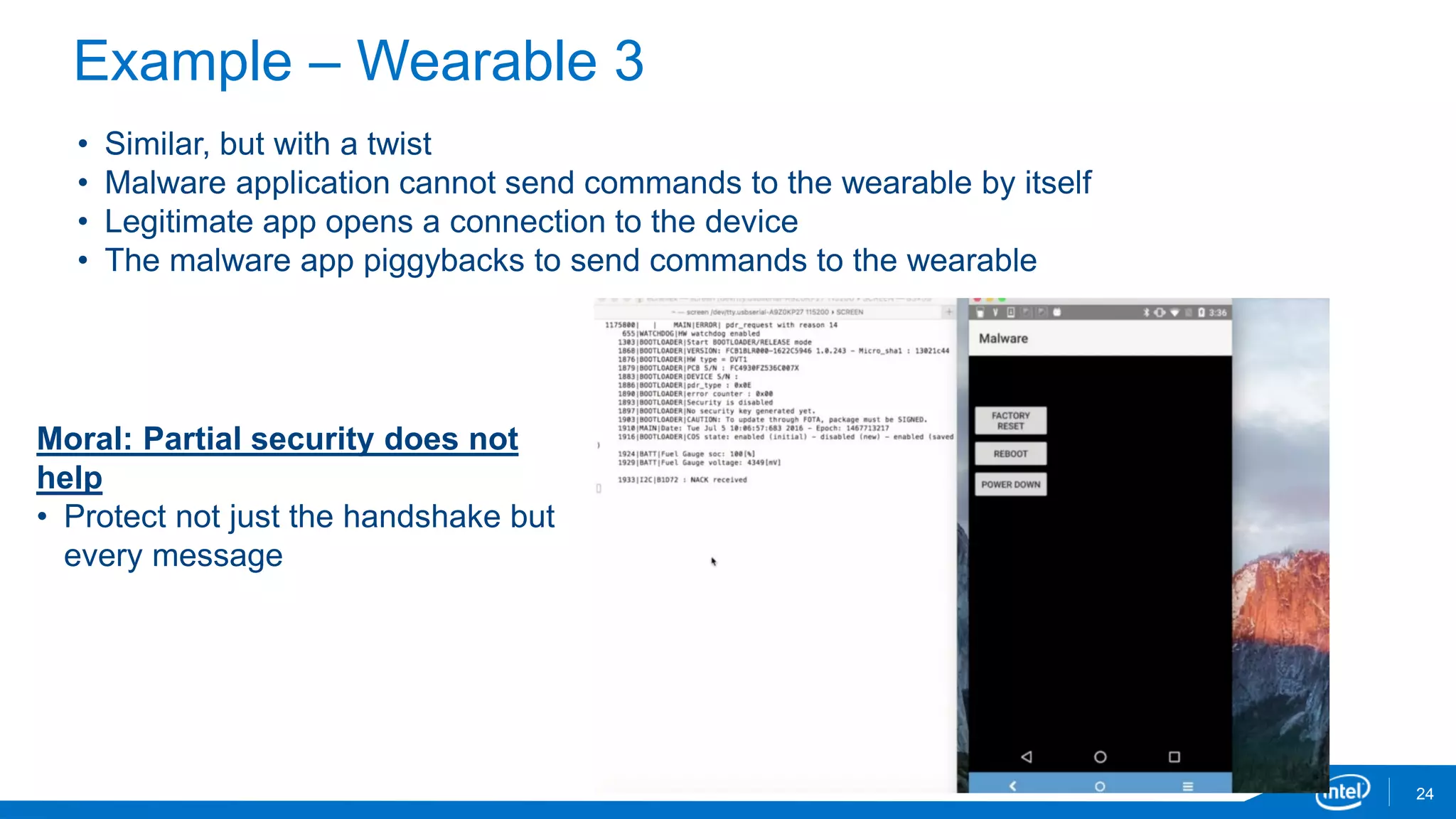
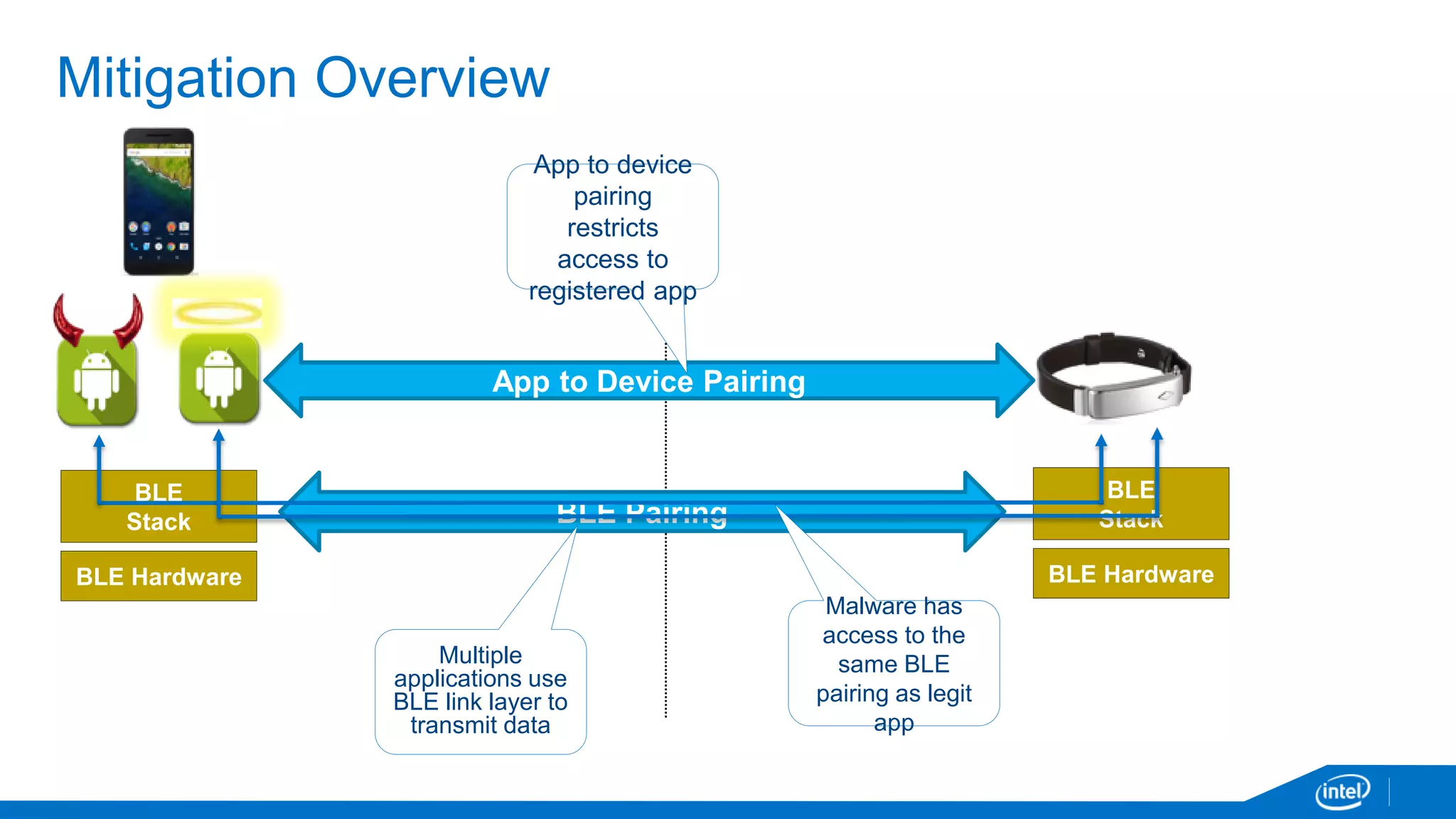
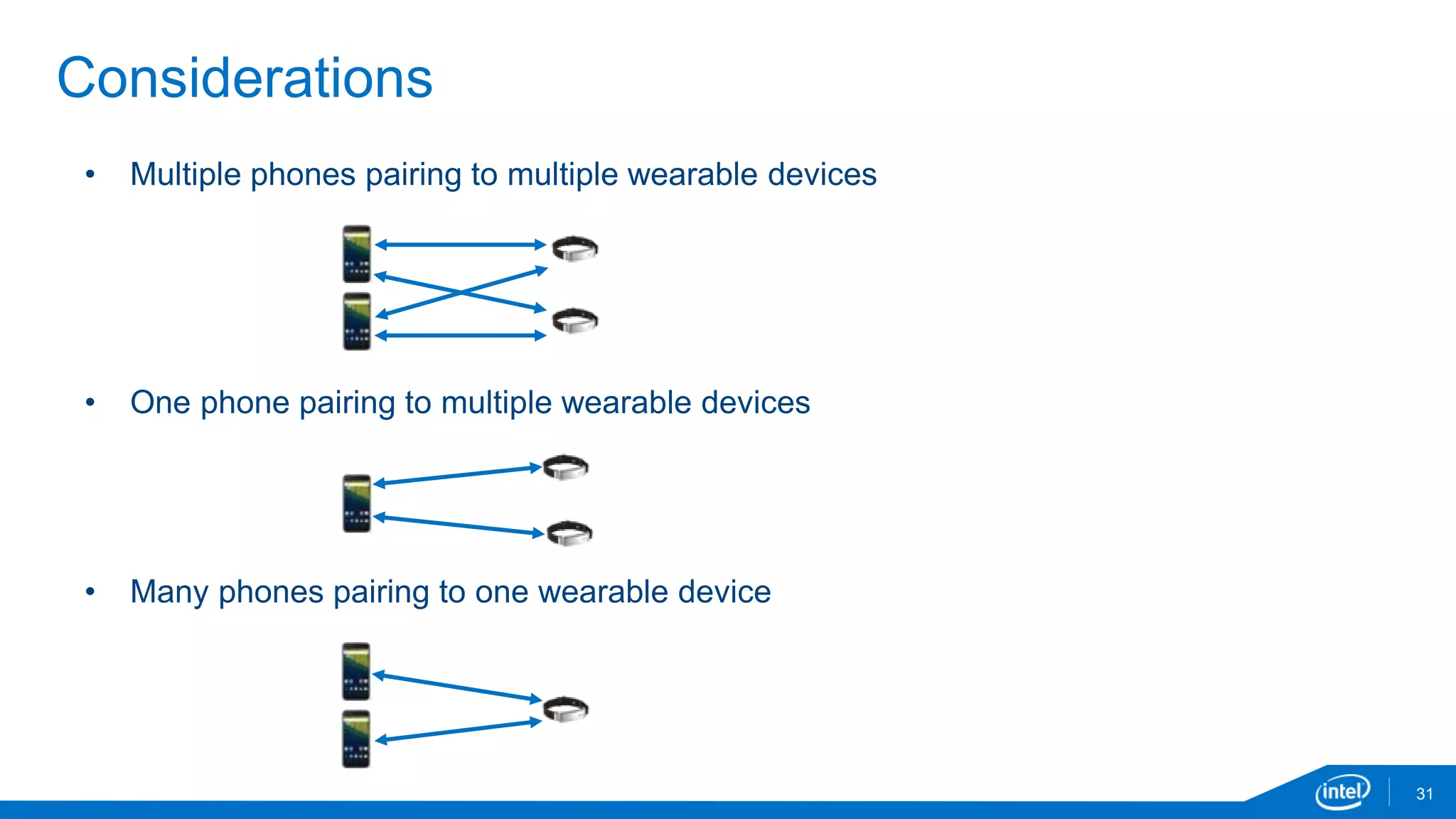
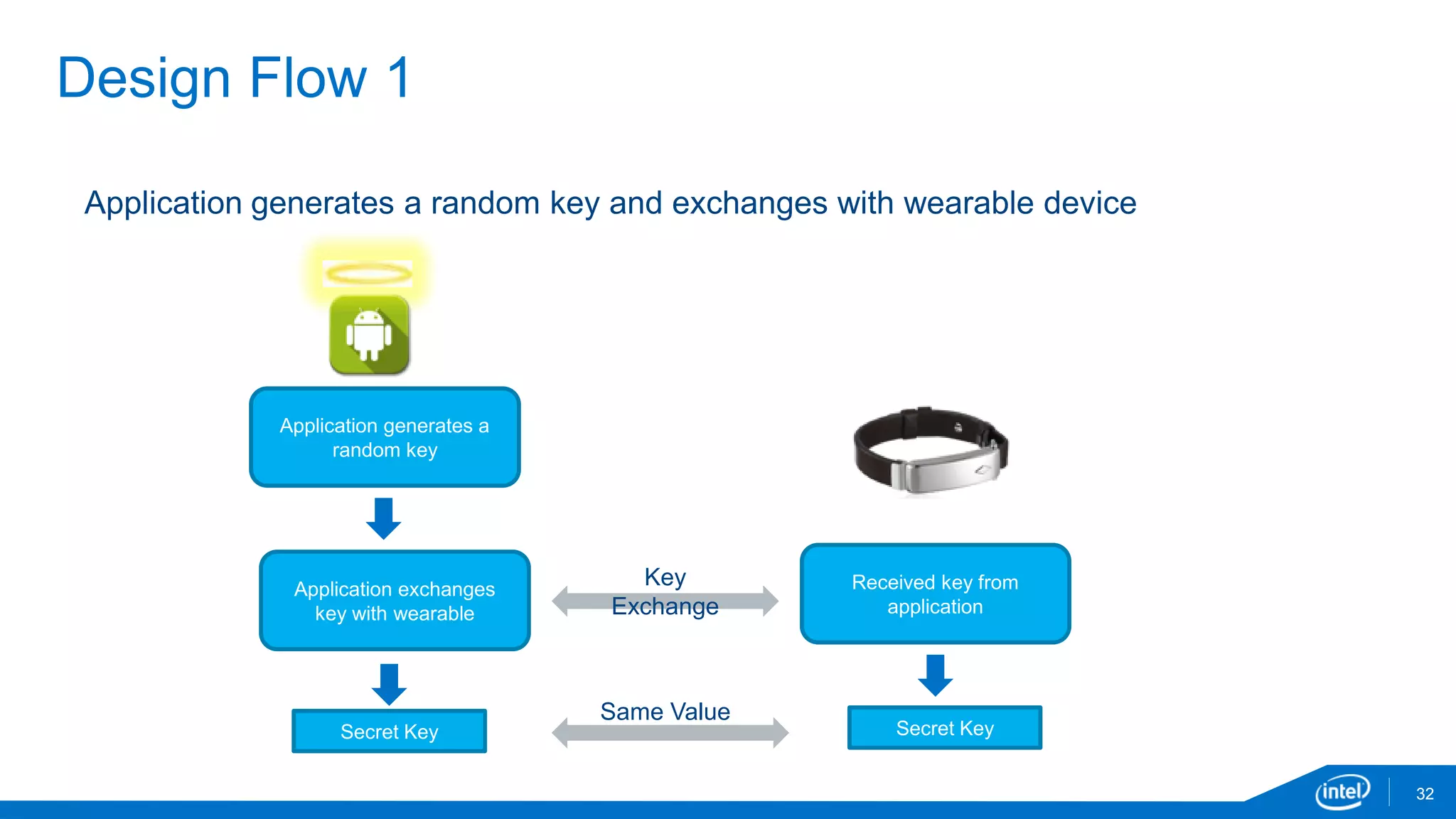
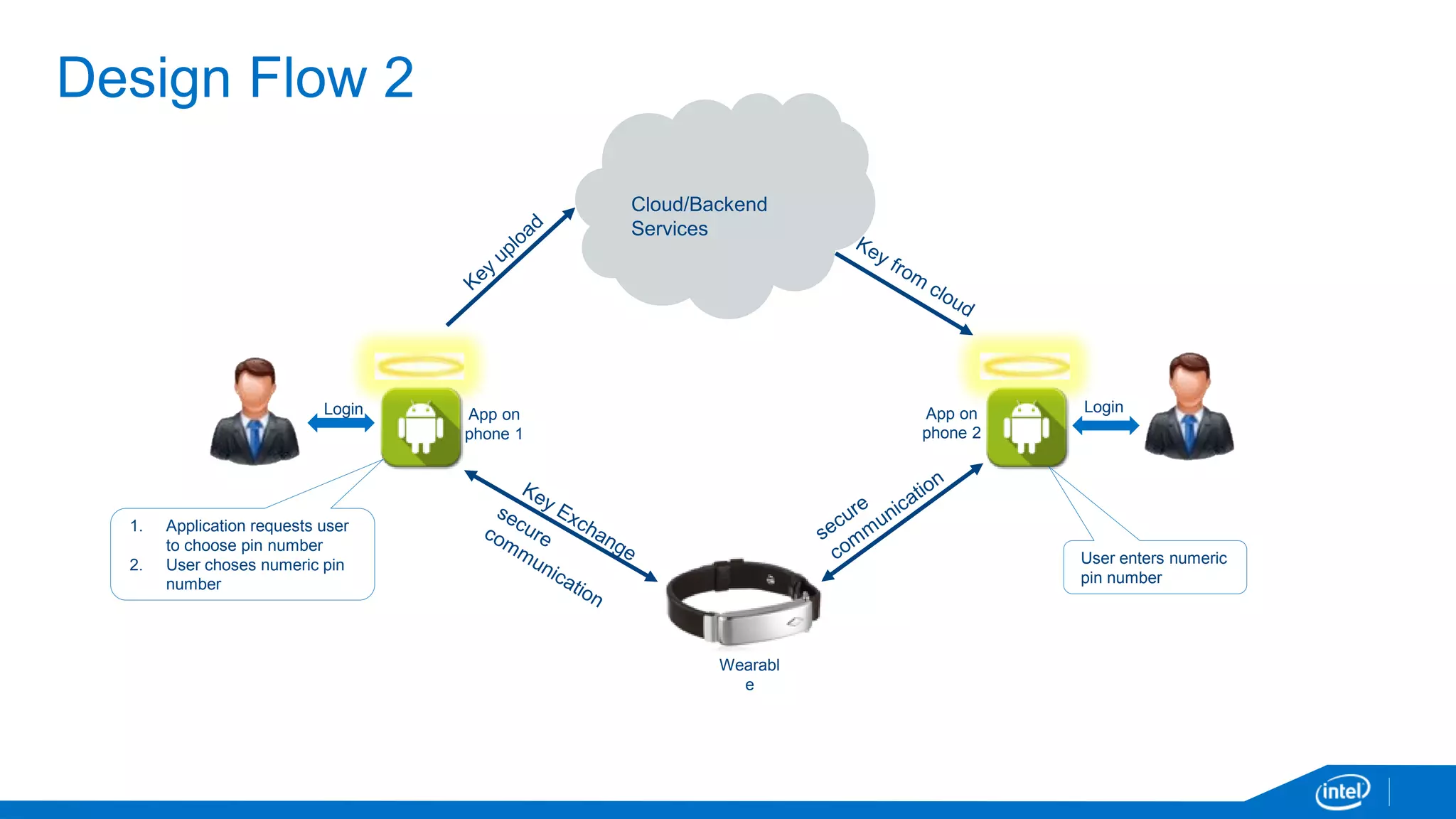
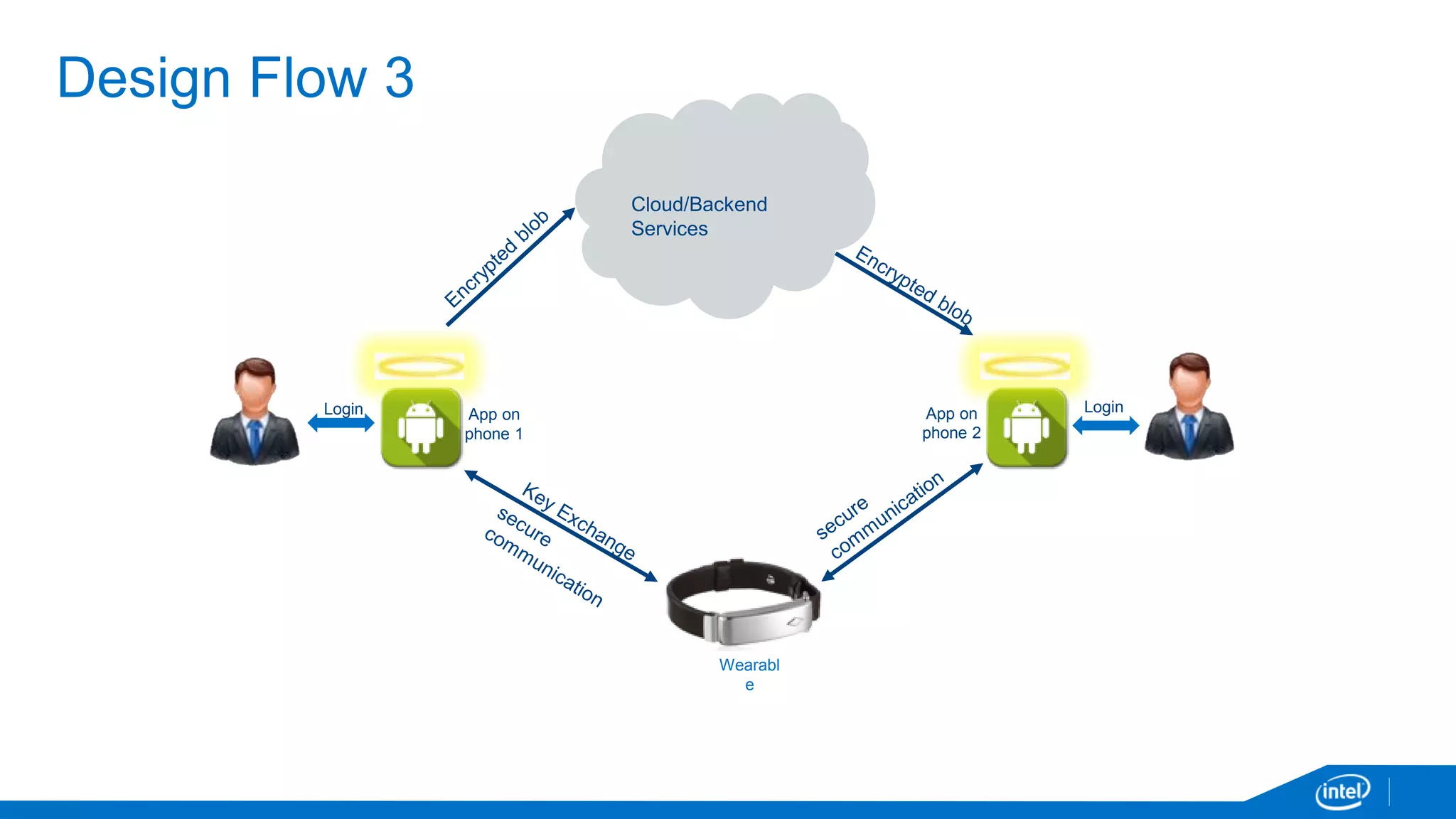
The document discusses the security vulnerabilities associated with mobile communication between wearables and devices using Bluetooth Low Energy (BLE). It highlights how encryption alone is insufficient for security, emphasizing various attack vectors such as man-in-the-middle and eavesdropping during the pairing process. The authors propose design and mitigation strategies to improve security and protect sensitive user data within the wearable and mobile application ecosystem.