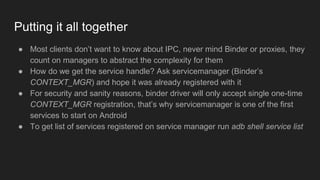
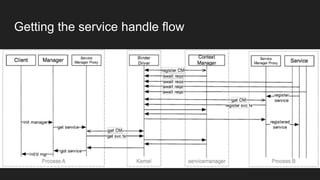
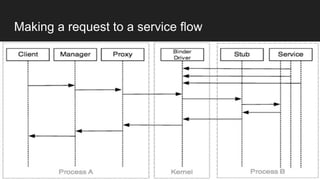
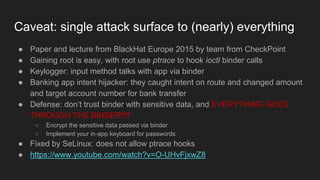
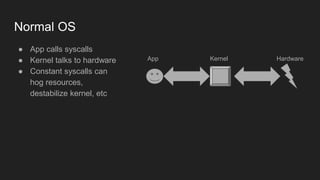
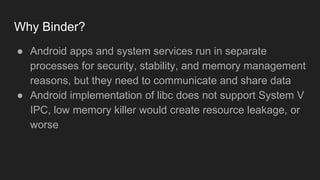
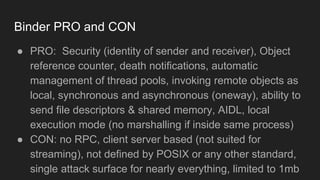
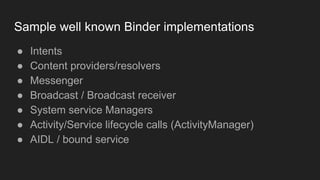
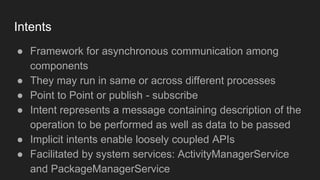
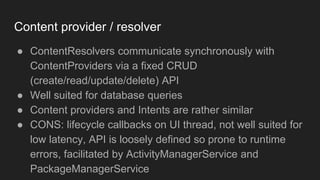
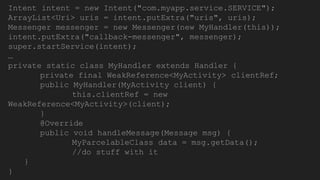
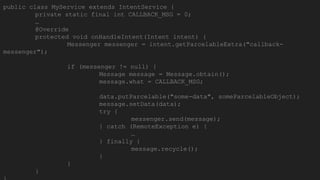
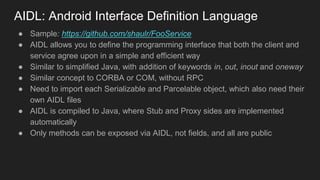
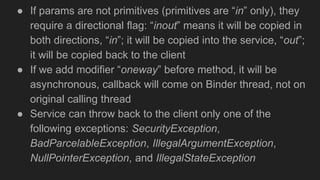
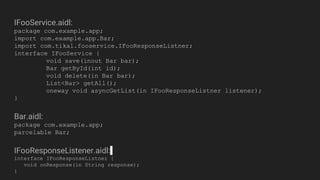
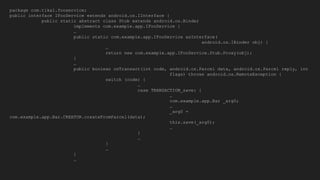
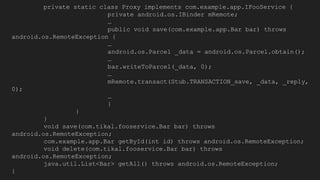
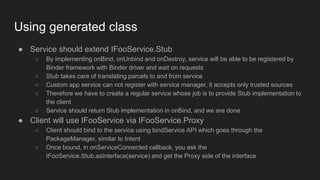
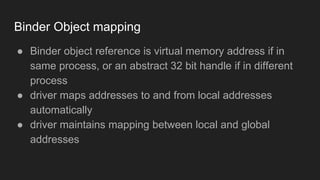
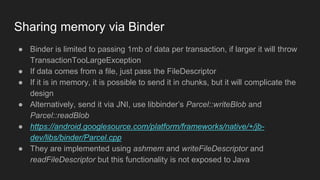
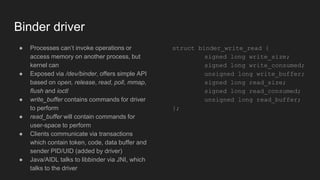
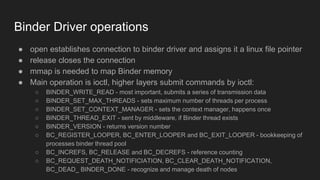
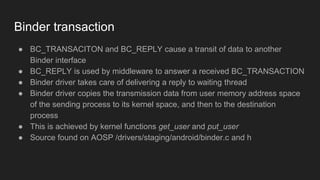
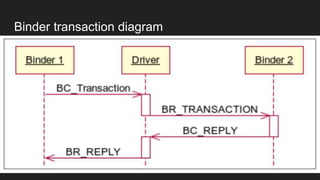
The document discusses the Binder IPC framework in Android, which facilitates communication between apps and system services while ensuring security, stability, and resource management. It elaborates on the components of the Binder system, including its architecture, various communication methods (like AIDL, intents, content providers), and the transaction model, highlighting its importance in the Android environment. Additionally, it touches on security considerations and potential vulnerabilities associated with Binder transactions.






![AIDL types
● null
● Java Primitives and their arrays
● CharSequence and String (as UTF-16)
● FileDescriptor (as dup of original)
● Serializable (not efficient, made for
serialization to storage)
● Map (reconstructed as HashMap)
● Bundle
● List (reconstructed as ArrayList)
● Object[]
● SparseArray and SparseBooleanArray
● IBinder and IInterface (transferred by
globally unique reference, not copied
over, used for callbacks, strong binder)
● Parcelable, for custom types
○ Parcelable can not be serialized to storage,
unlike Serializable
○ You need to implement marshalling and
unmarshalling yourself
○ Mechanism for flattening objects, proxy calls
writeToParcel, stub re-creates the object](https://image.slidesharecdn.com/binder-180501110351/85/Binder-Android-IPC-20-320.jpg)

![struct binder_transaction_data {
union {
size_t handle;
void *ptr;
} target;
void *cookie;
unsigned int code;
unsigned int flags;
pid_t sender_pid;
uid_t sender_euid;
size_t data_size;
size_t offsets_size;
union {
struct {
const void
*buffer;
const void
*offsets;
} ptr;
uint8_t buf[8];
} data;
};](https://image.slidesharecdn.com/binder-180501110351/85/Binder-Android-IPC-31-320.jpg)