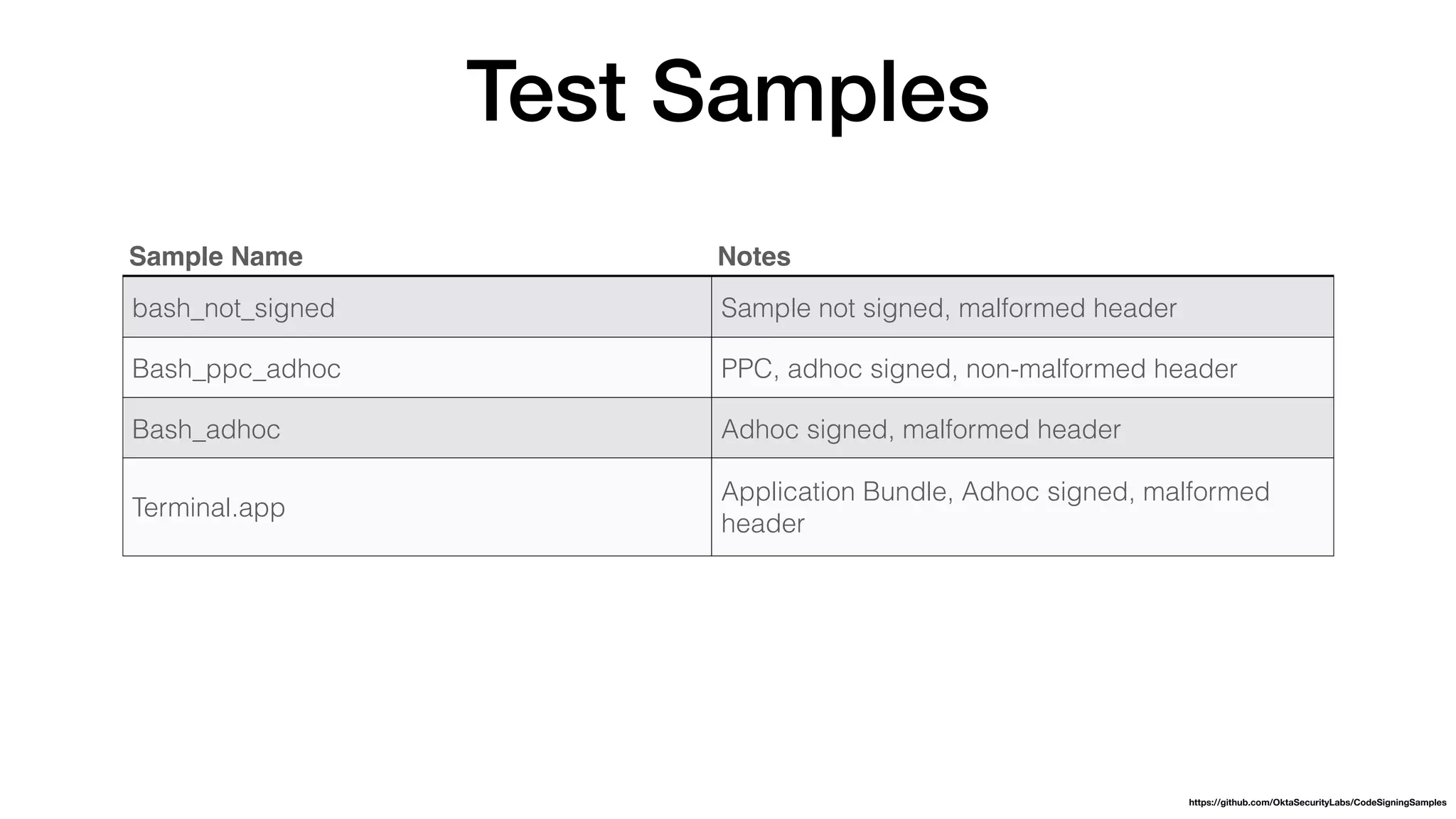
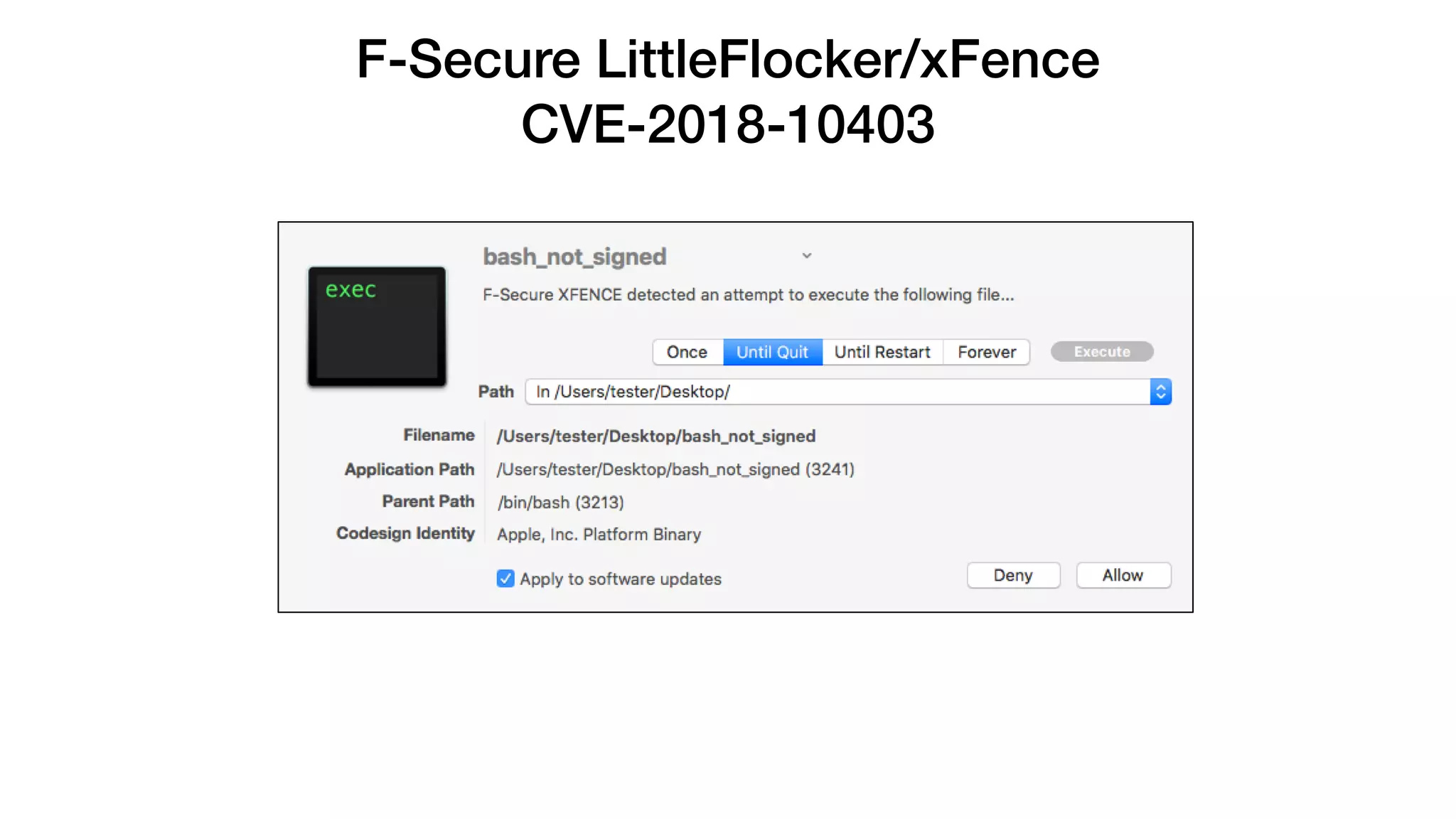
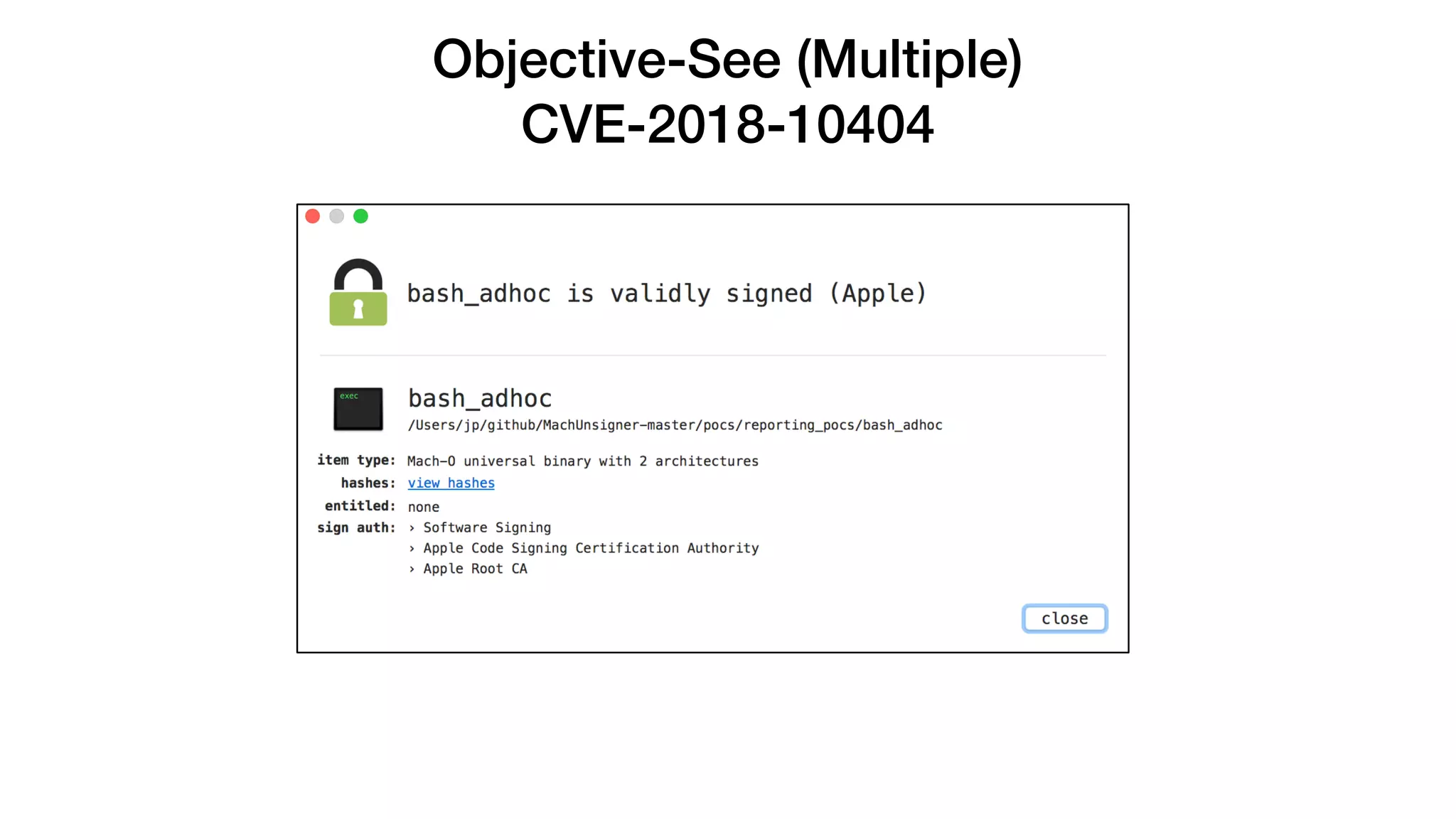
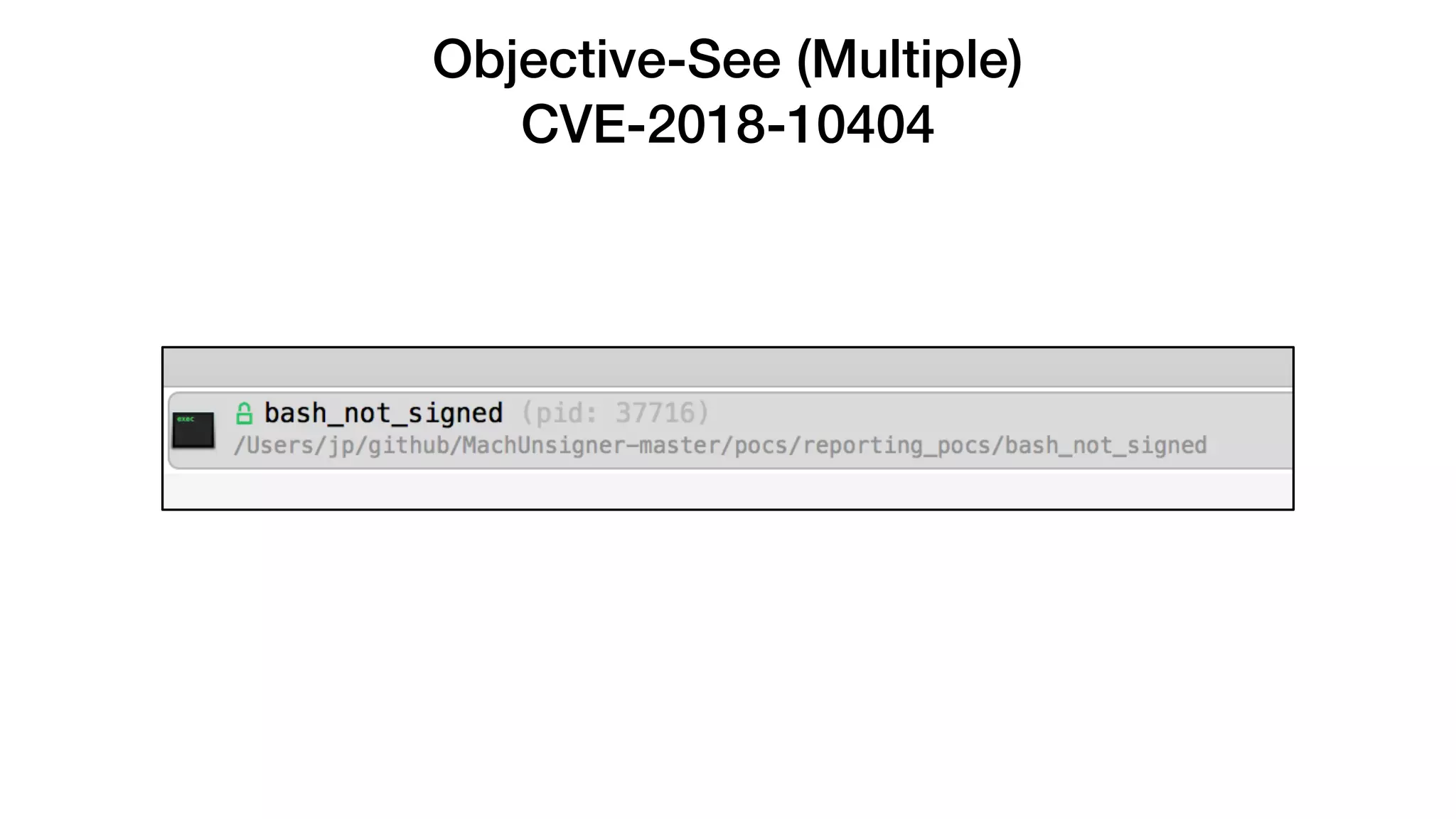
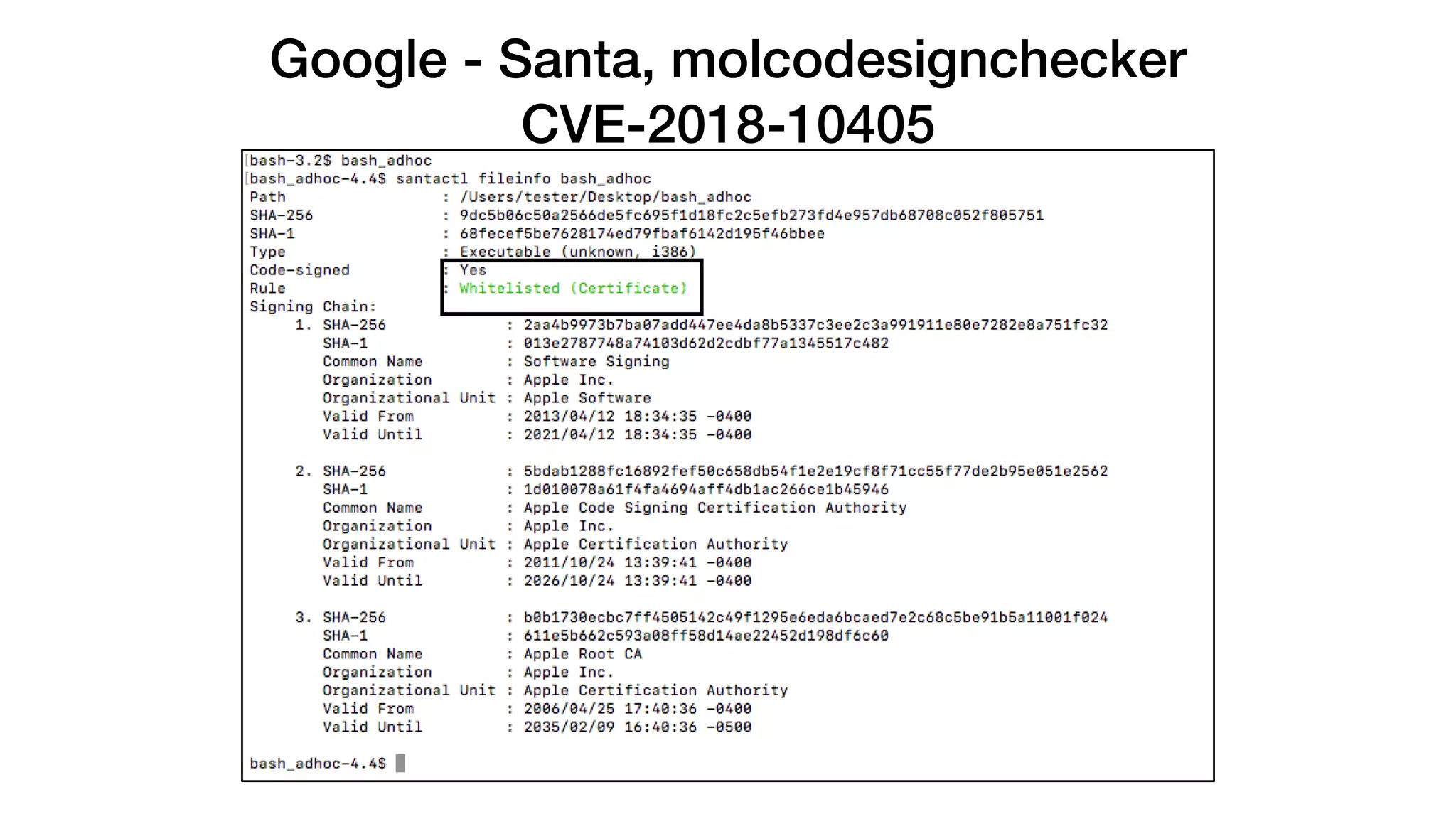
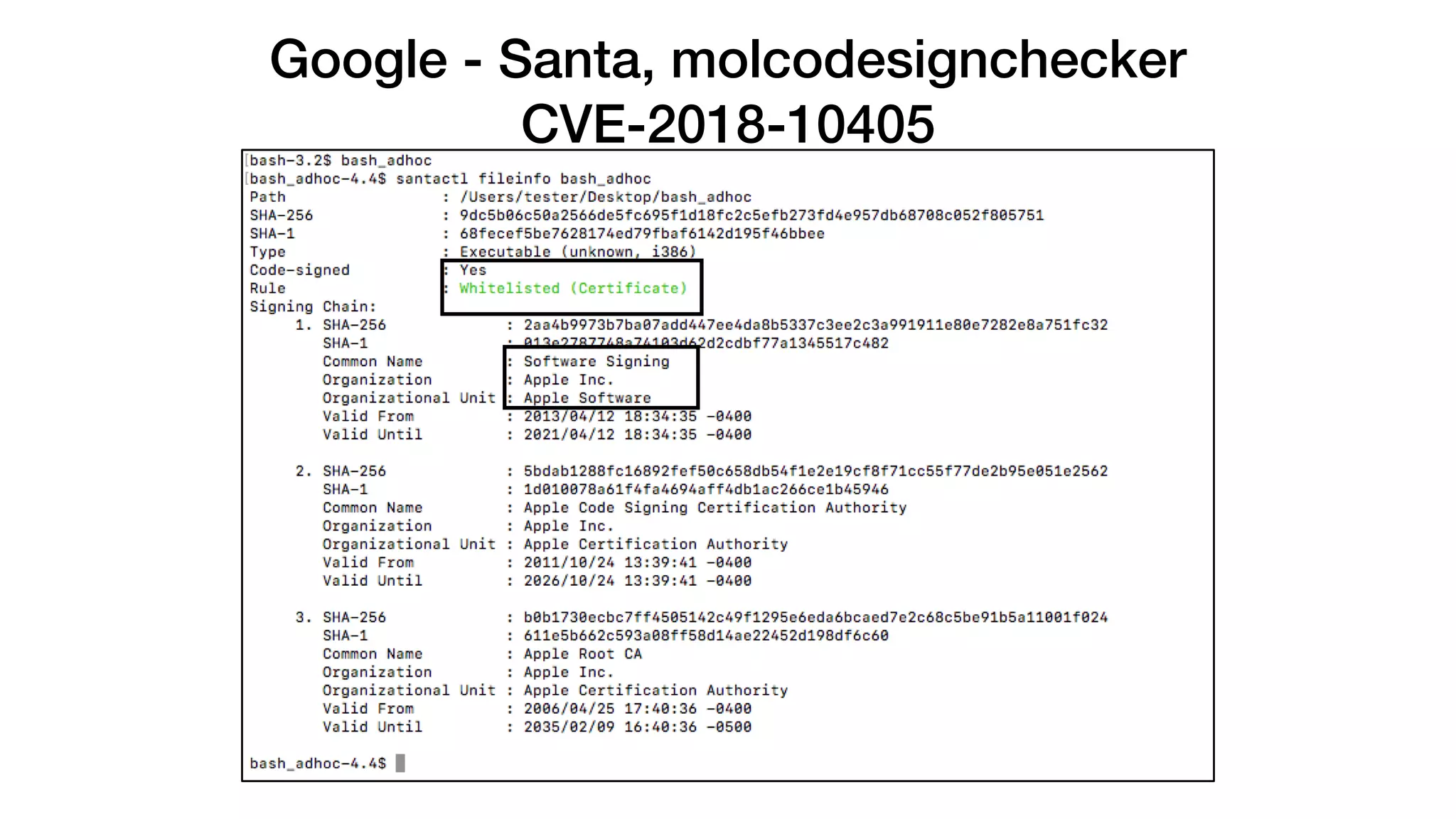
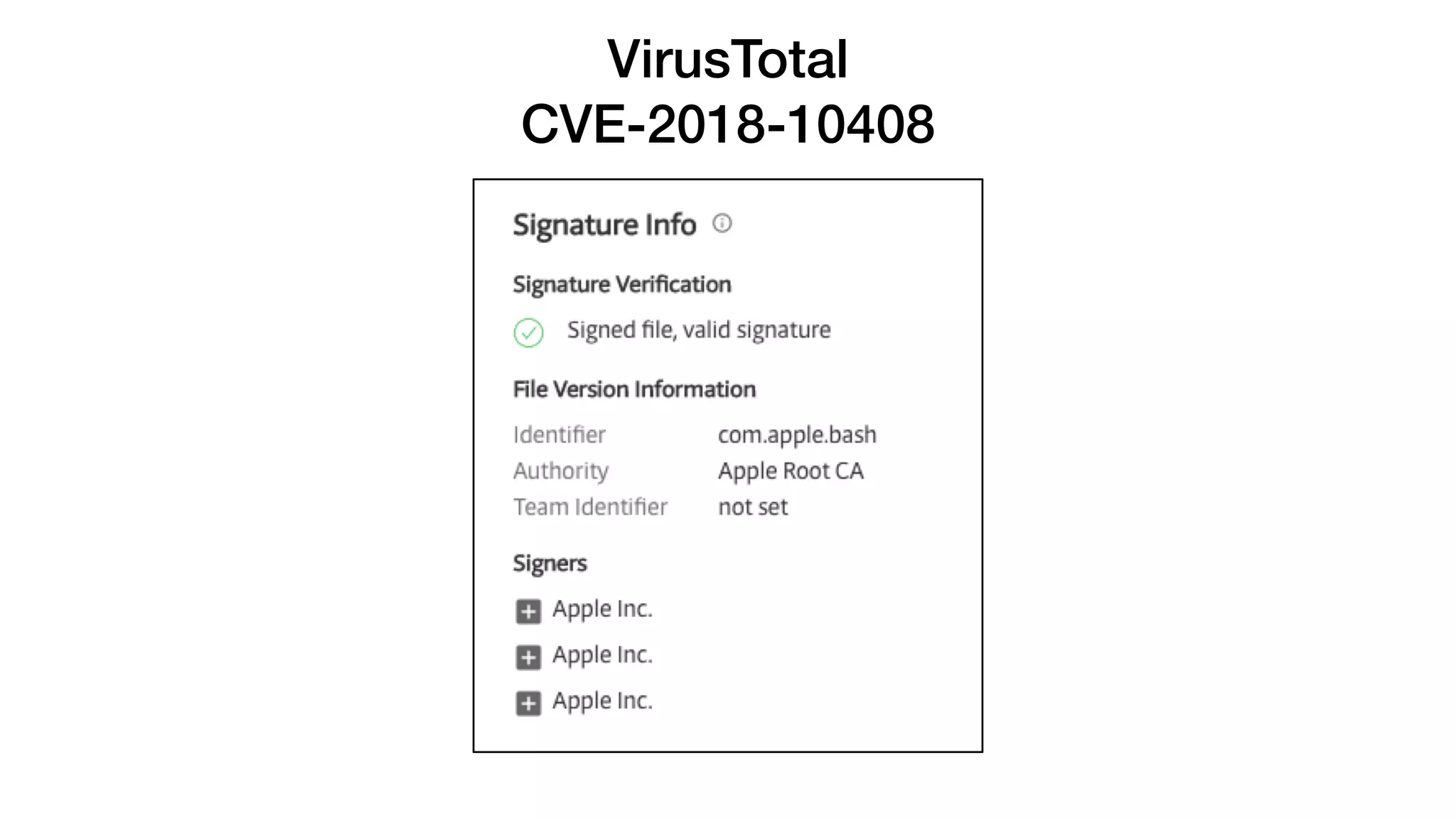
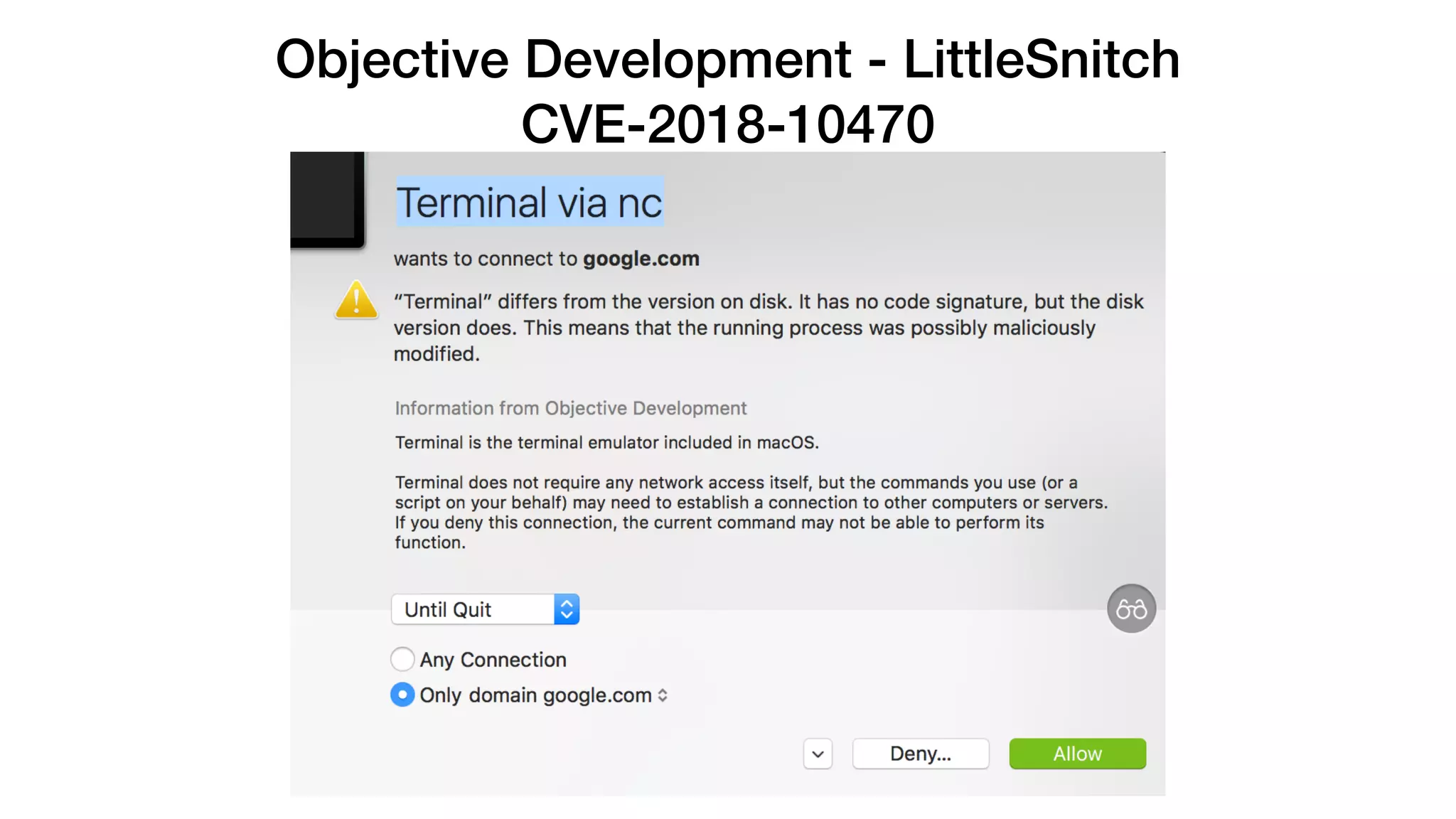
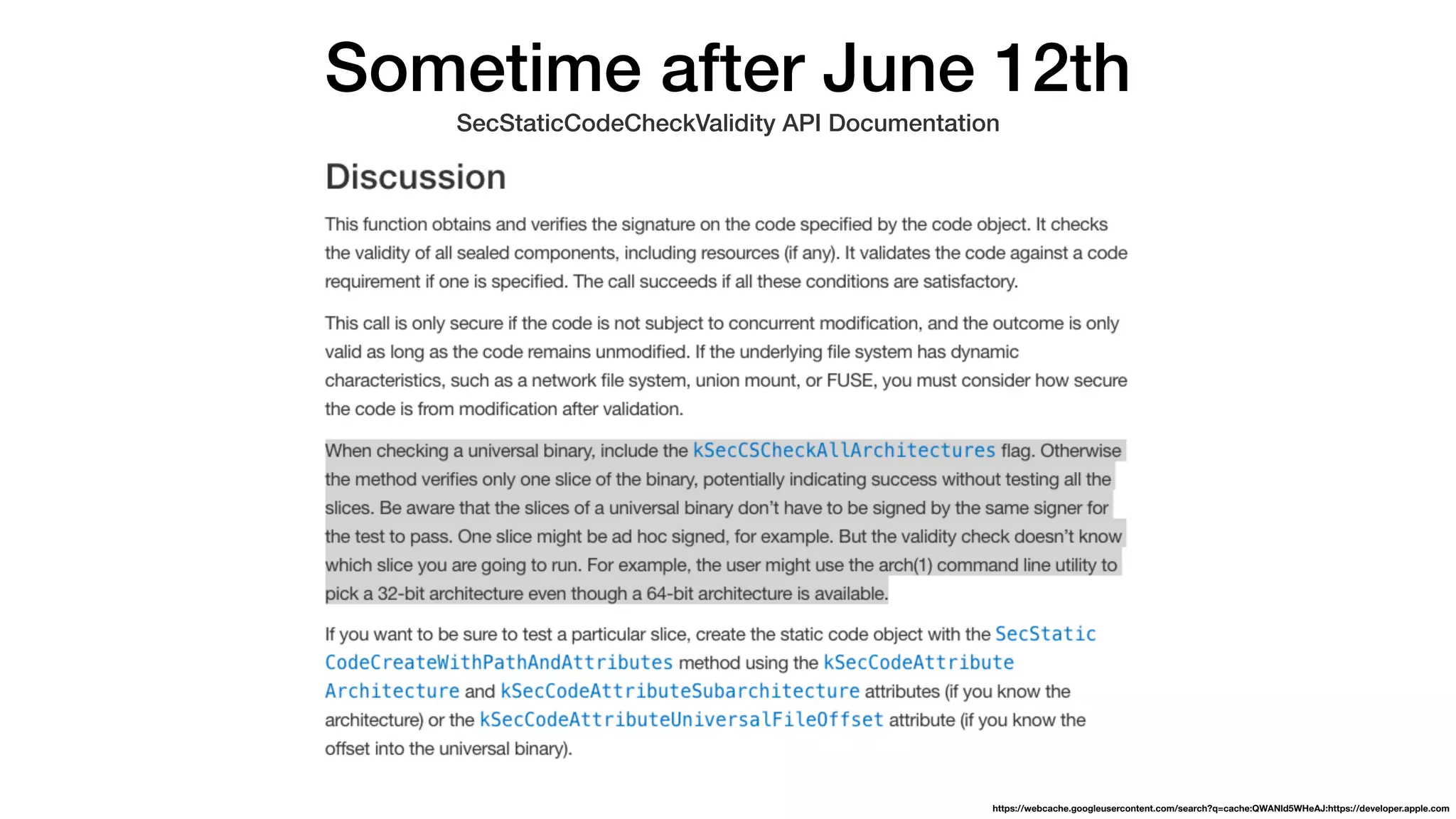
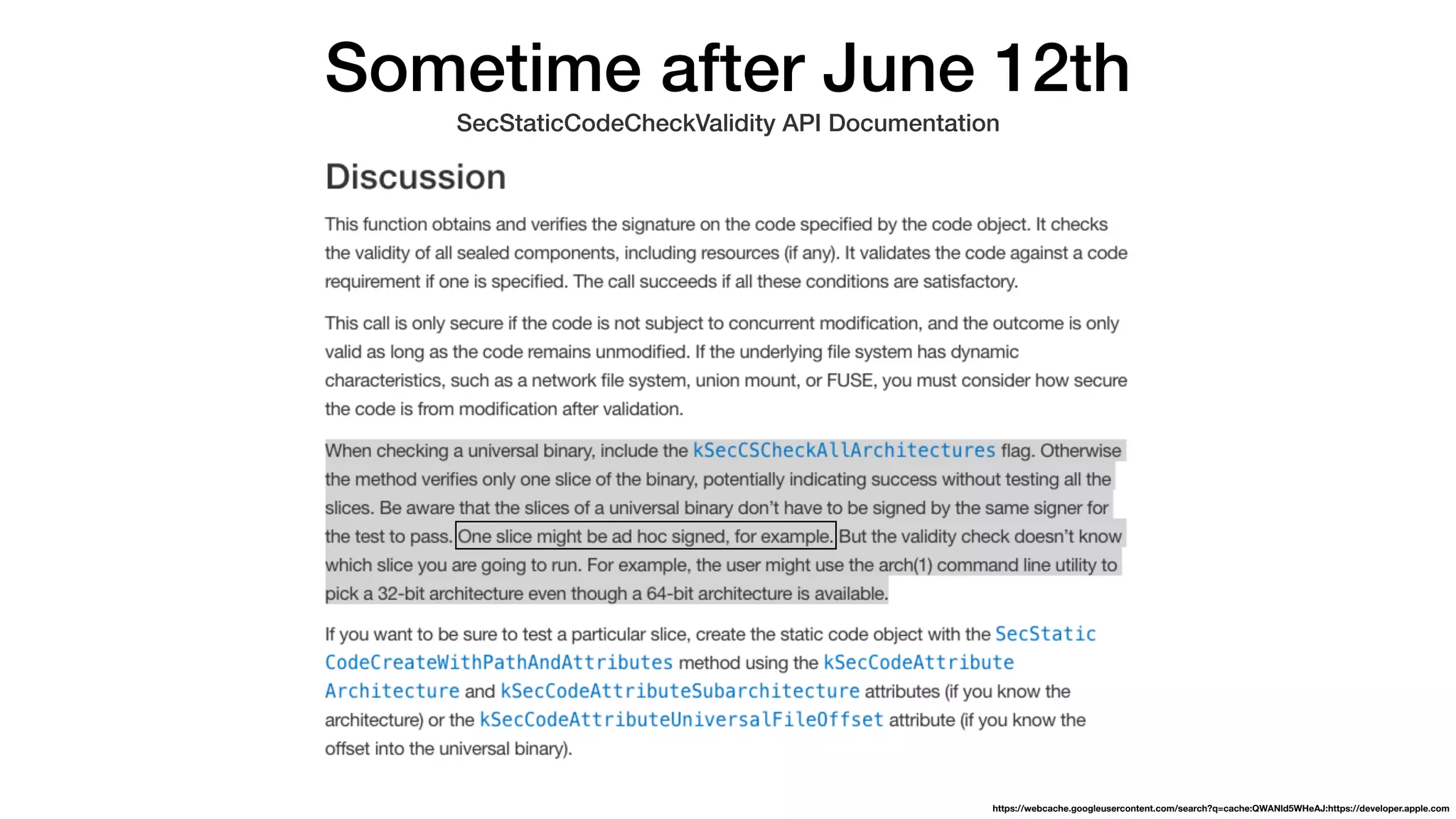
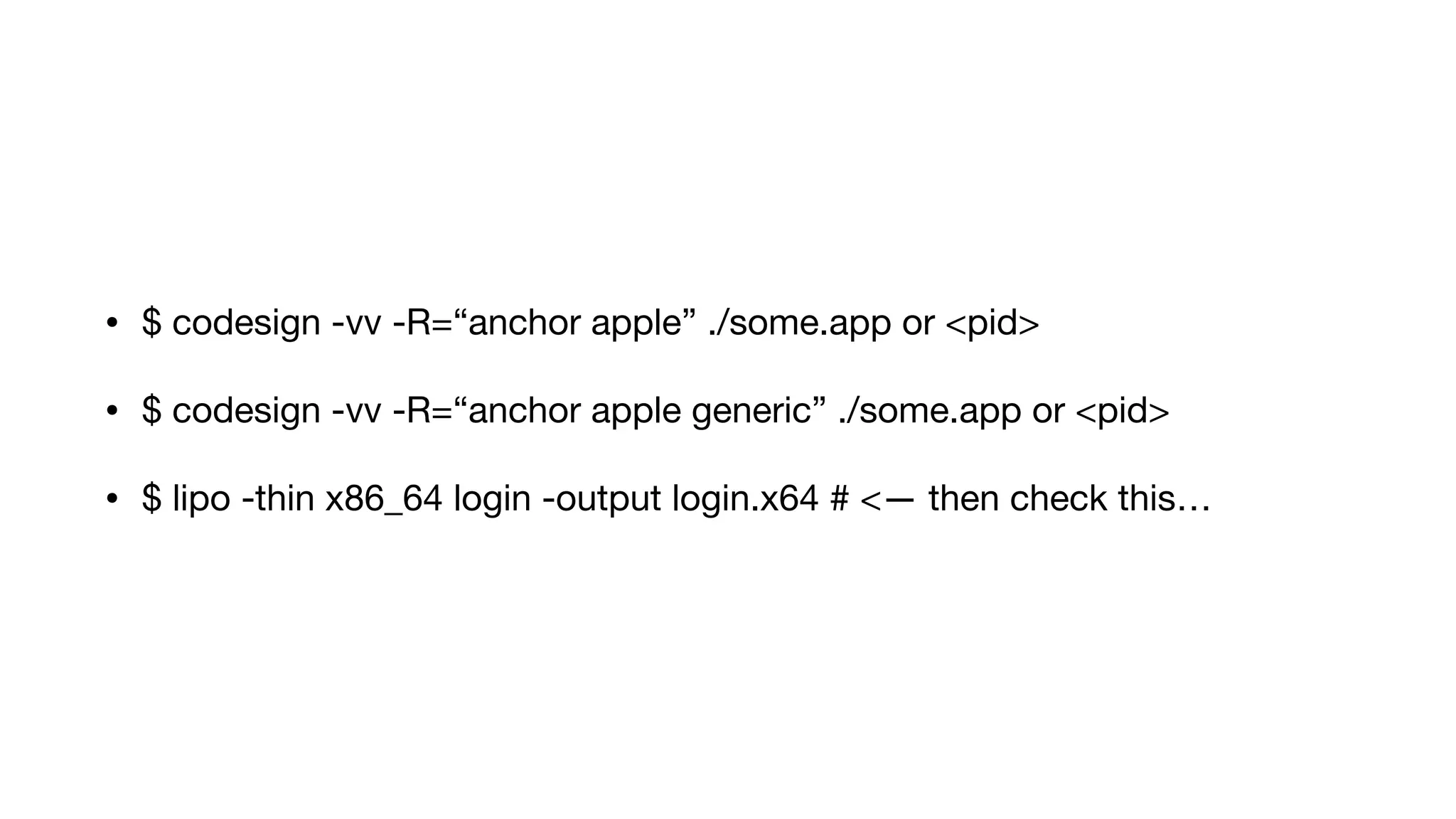
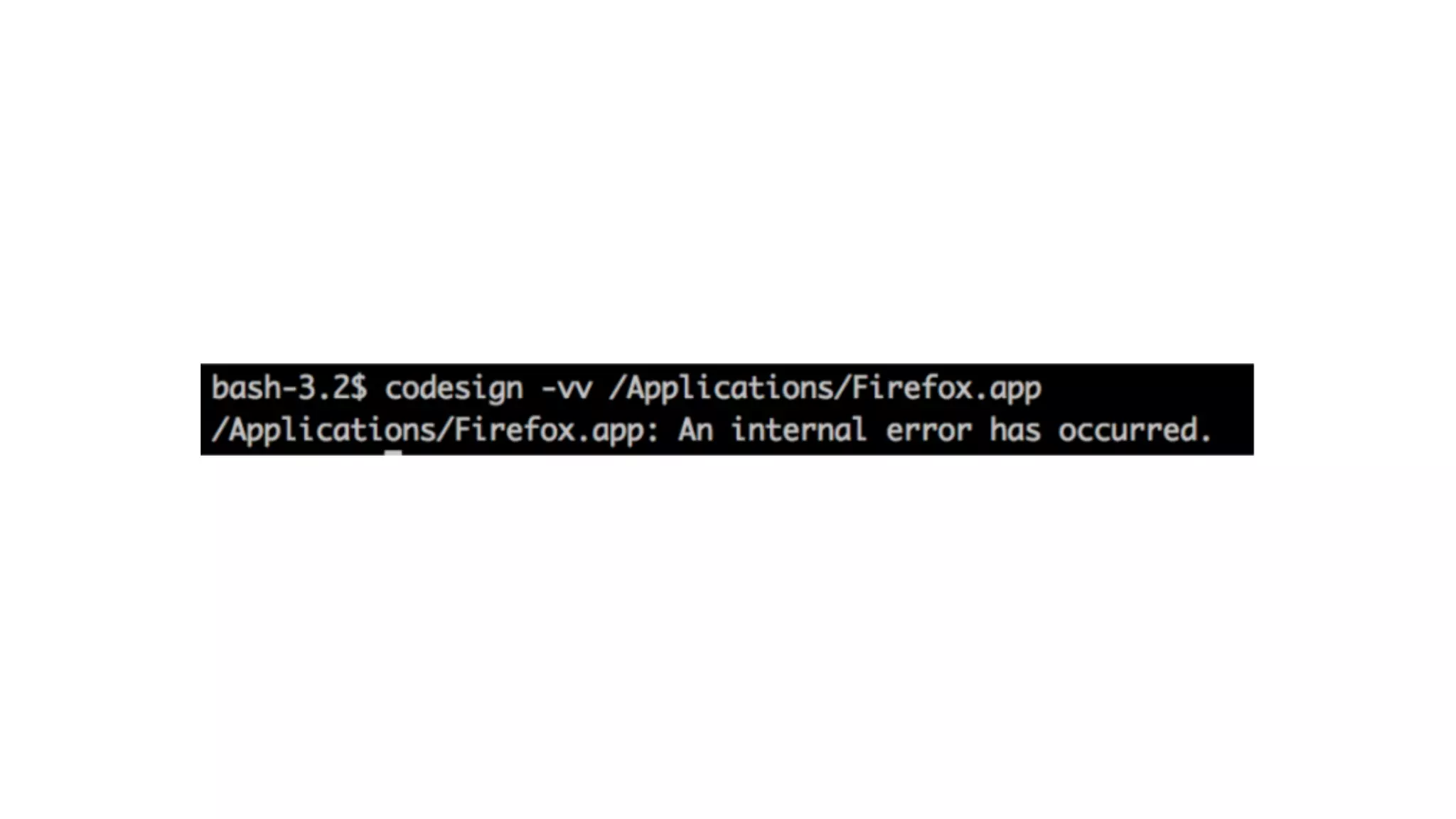
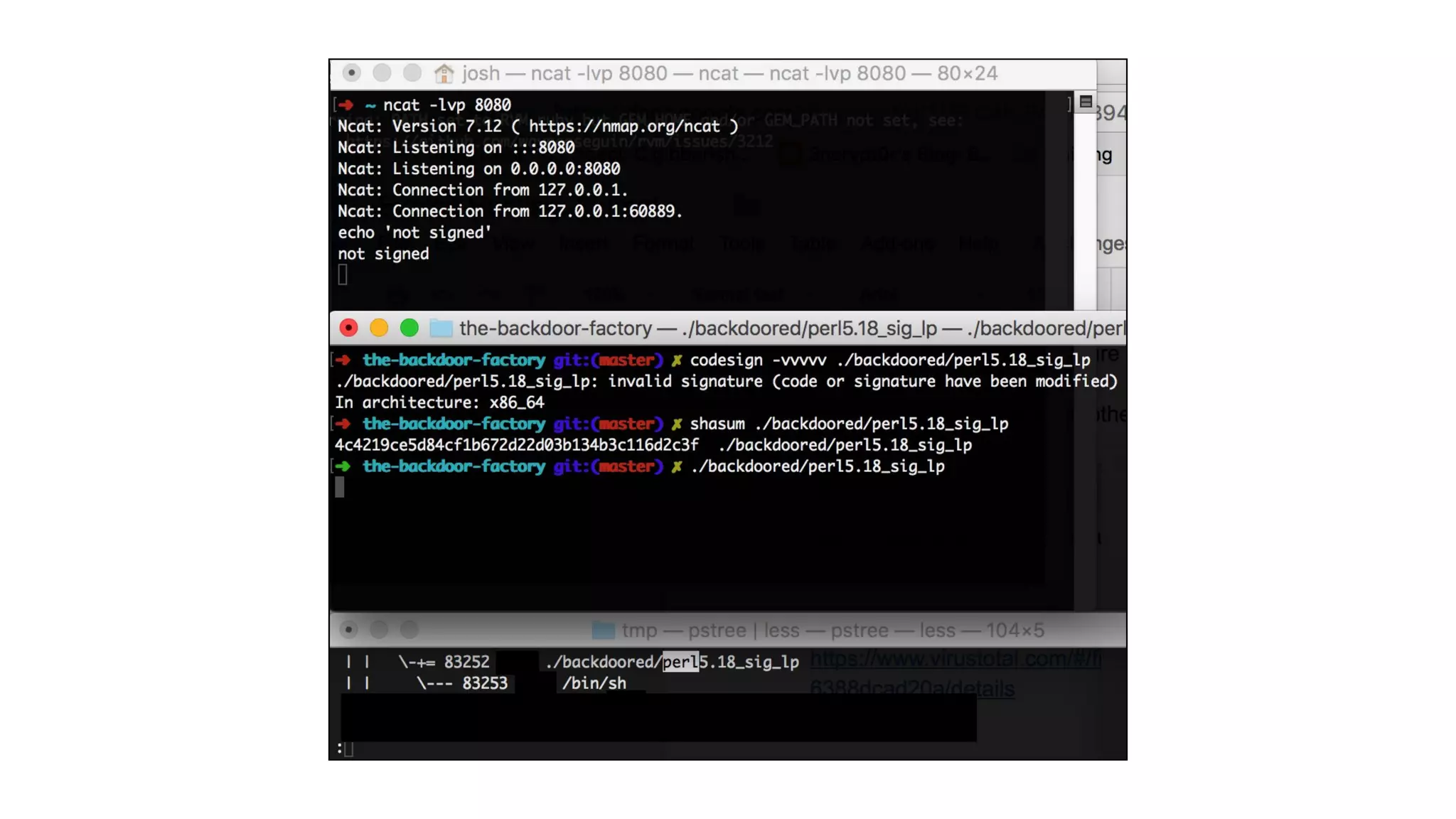
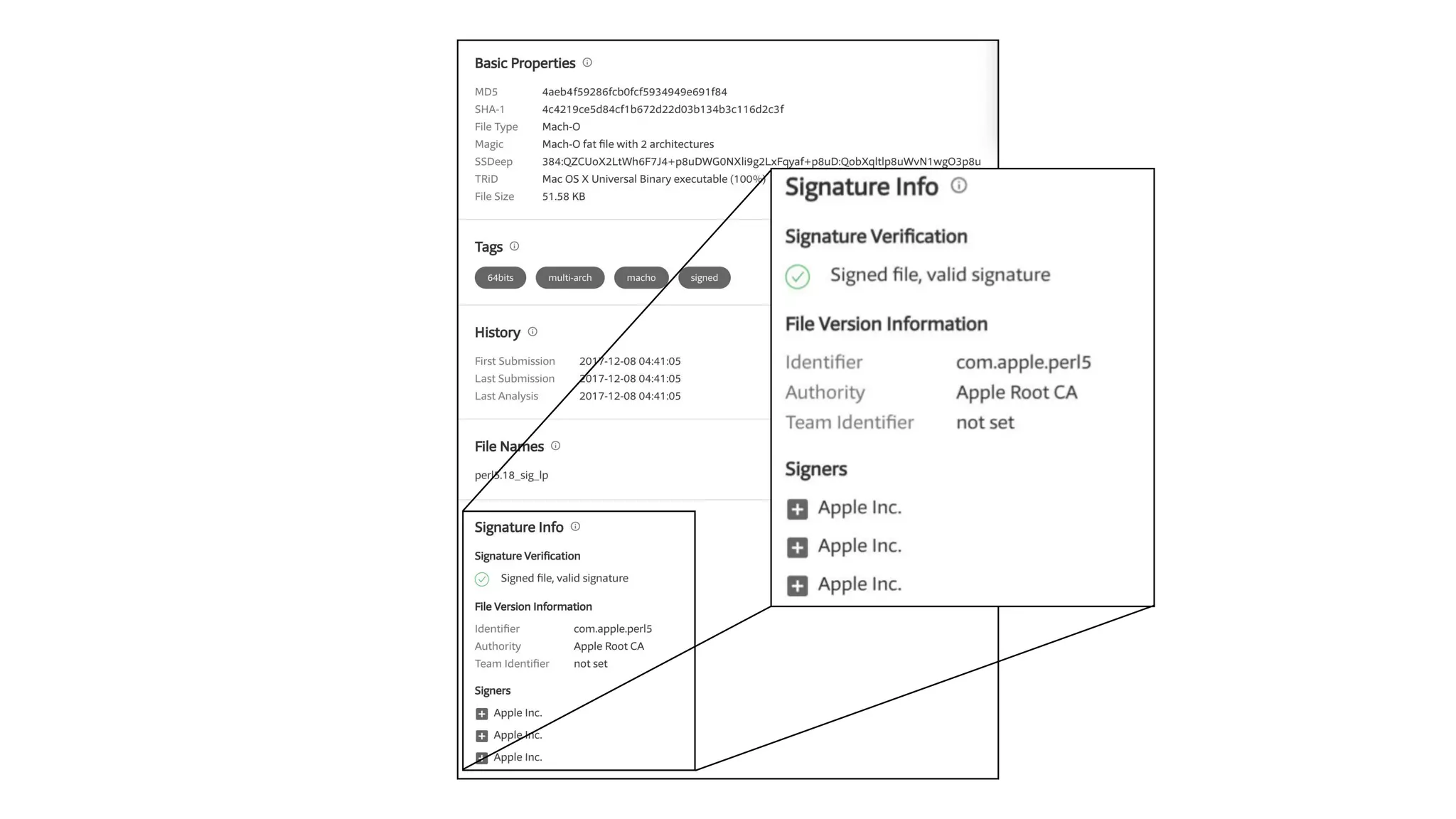
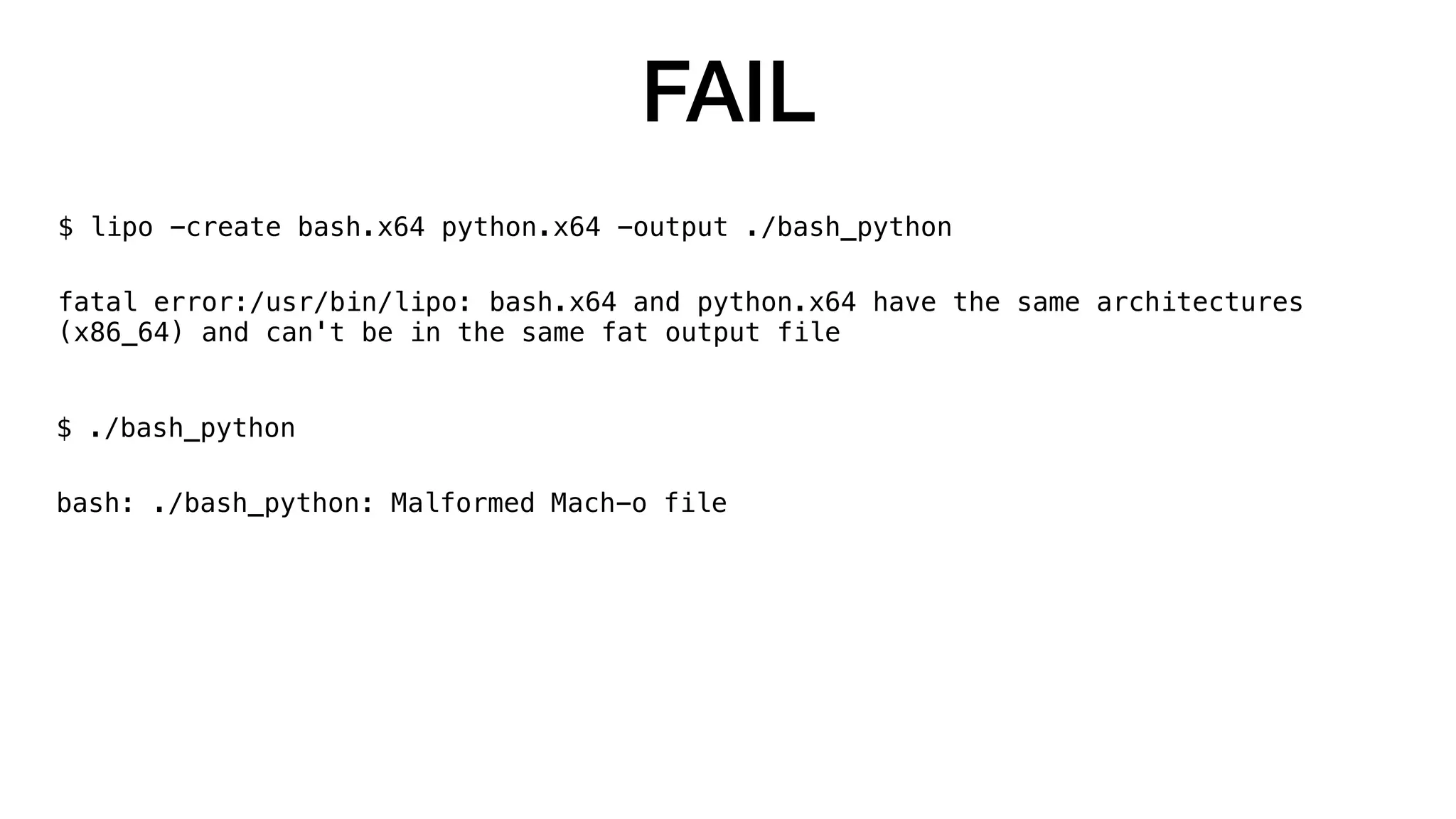
The document summarizes a presentation about exploiting a vulnerability in Apple's code signing process on macOS. The vulnerability allows ad-hoc signed malicious code to bypass Gatekeeper and execute on systems where only Apple-signed code is supposed to run. The presentation covered code signing basics, a demonstration of the vulnerability, technical details, how it impacts third-party software vendors, the disclosure process to Apple, and recommendations for properly validating signed code.



















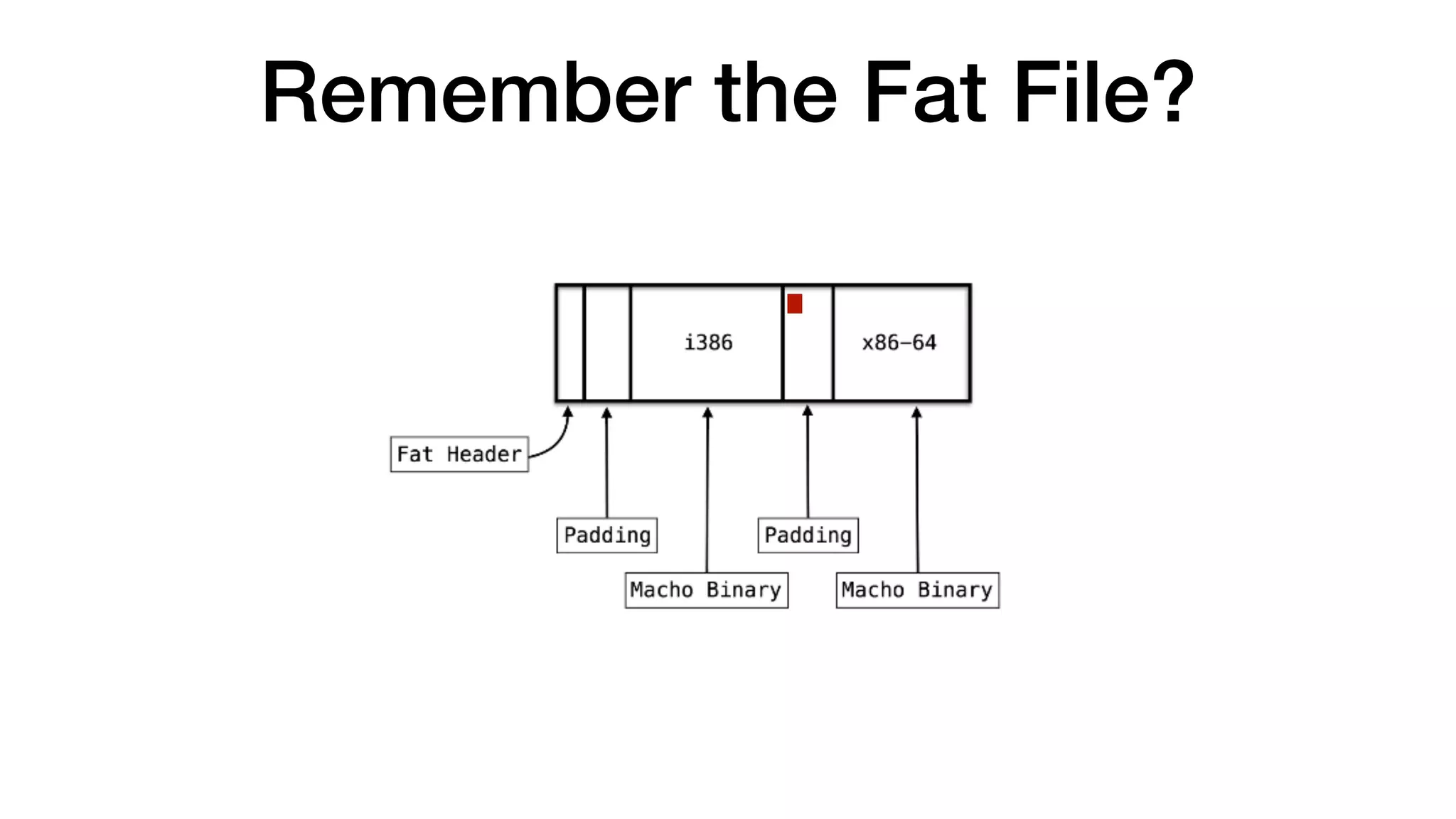
![$ file /bin/sync
/bin/sync: Mach-O universal binary with 2 architectures: [x86_64:Mach-O 64-bit executable x86_64]
[i386:Mach-O executable i386]
/bin/sync (for architecture x86_64): Mach-O 64-bit executable x86_64
/bin/sync (for architecture i386): Mach-O executable i386](https://image.slidesharecdn.com/icanbeappleandsocanyou-180726072951/75/I-can-be-apple-and-so-can-you-20-2048.jpg)
![$ file /bin/sync
/bin/sync: Mach-O universal binary with 2 architectures: [x86_64:Mach-O 64-bit executable x86_64]
[i386:Mach-O executable i386]
/bin/sync (for architecture x86_64): Mach-O 64-bit executable x86_64
/bin/sync (for architecture i386): Mach-O executable i386](https://image.slidesharecdn.com/icanbeappleandsocanyou-180726072951/75/I-can-be-apple-and-so-can-you-21-2048.jpg)
![$ file /bin/sync
/bin/sync: Mach-O universal binary with 2 architectures: [x86_64:Mach-O 64-bit executable x86_64]
[i386:Mach-O executable i386]
/bin/sync (for architecture x86_64): Mach-O 64-bit executable x86_64
/bin/sync (for architecture i386): Mach-O executable i386](https://image.slidesharecdn.com/icanbeappleandsocanyou-180726072951/75/I-can-be-apple-and-so-can-you-22-2048.jpg)