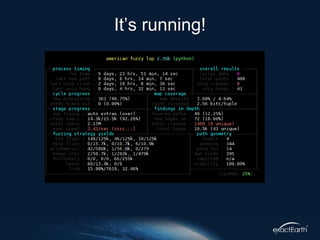
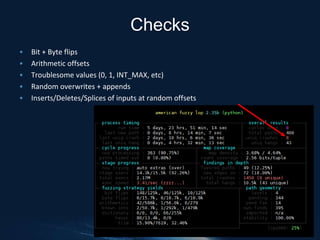
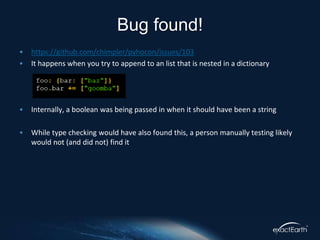
American Fuzzy Lop (AFL) is a black box fuzzing tool used to find crashes in software by generating random inputs. It operates on instrumented binaries without needing knowledge of the problem domain, proving effective in discovering elusive bugs across numerous applications. The document specifically discusses using AFL to test the encode/decode functions of the Python library PyHocon, highlighting its ease of use and potential in identifying complex issues.