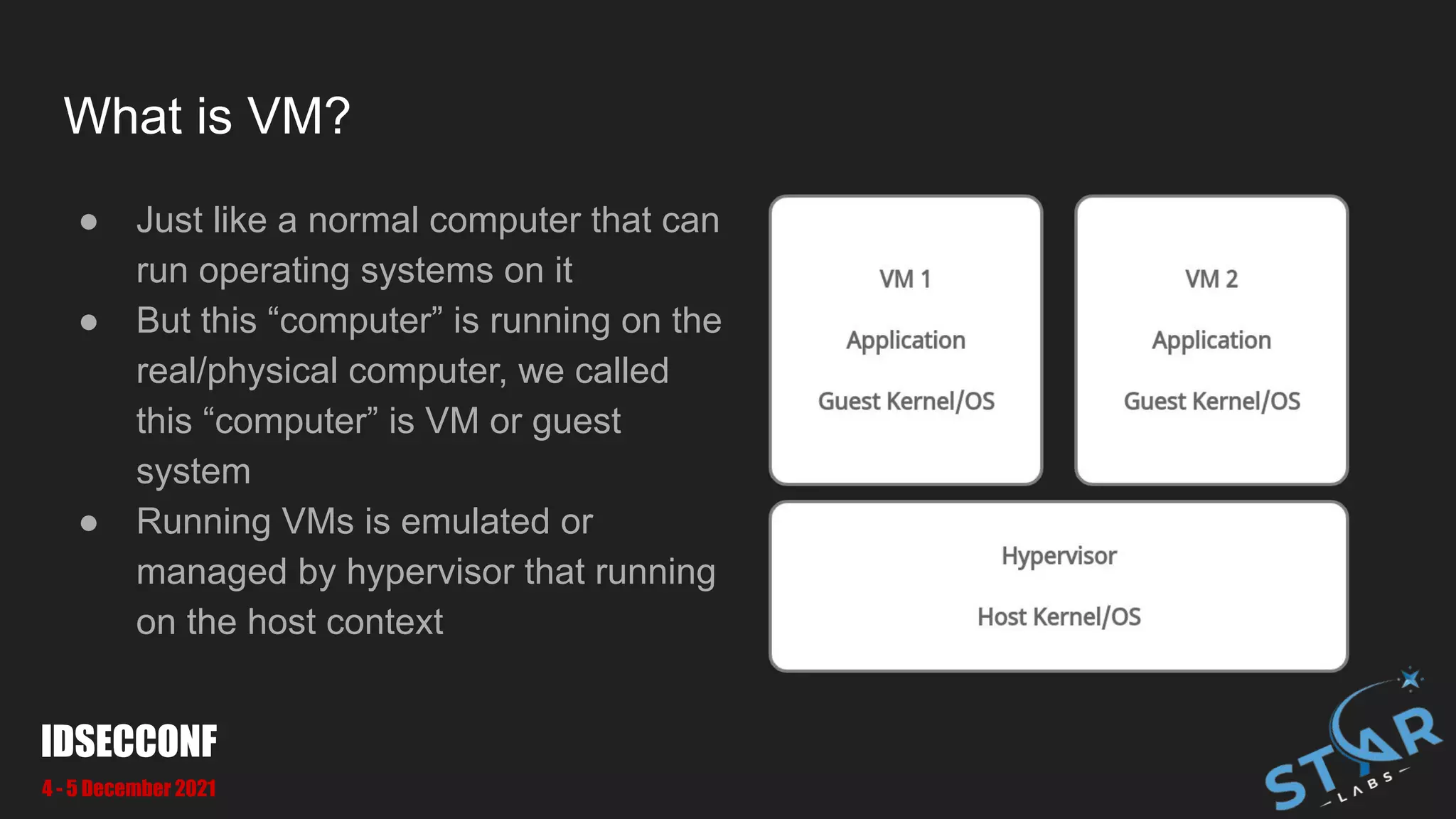
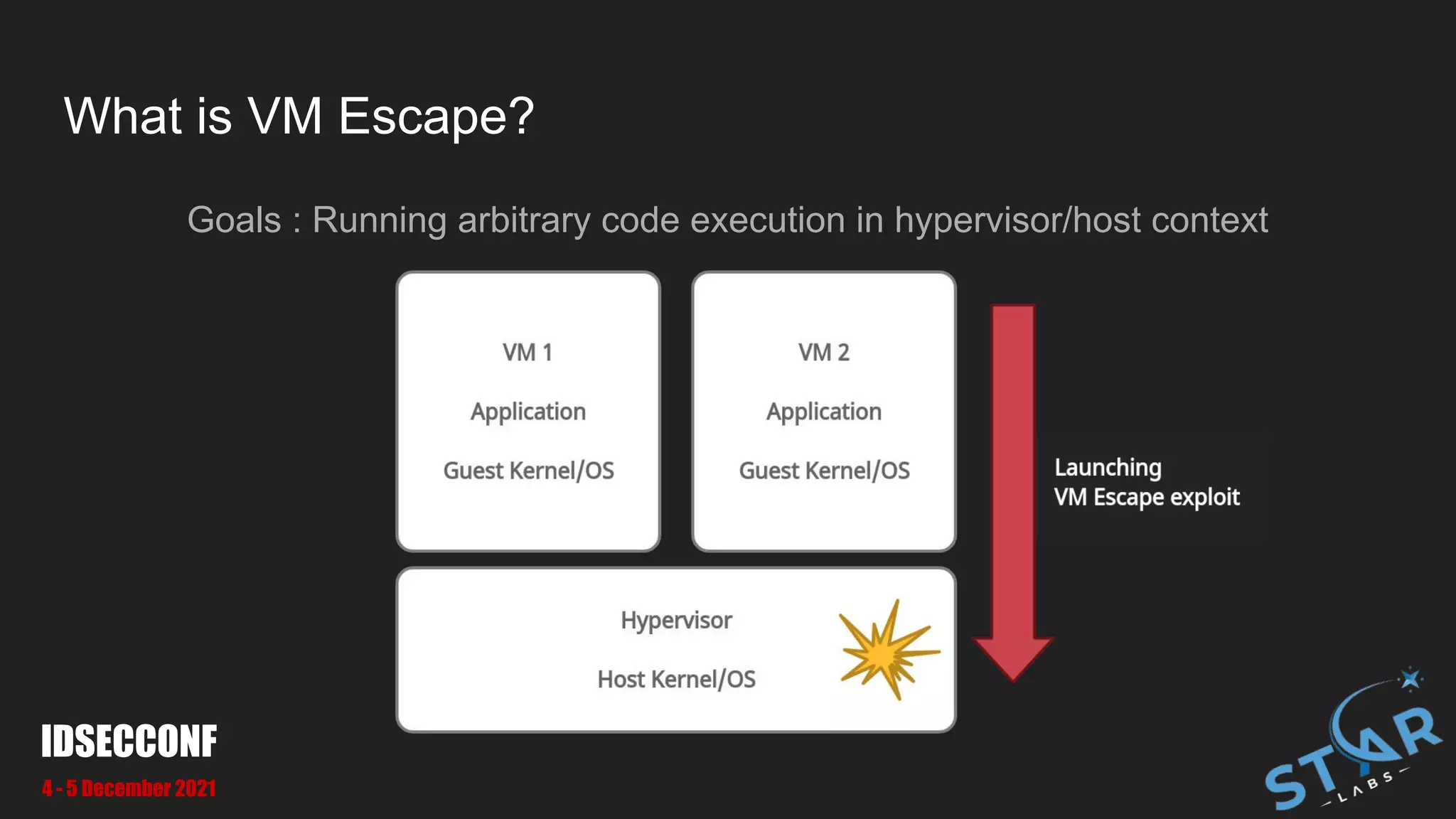
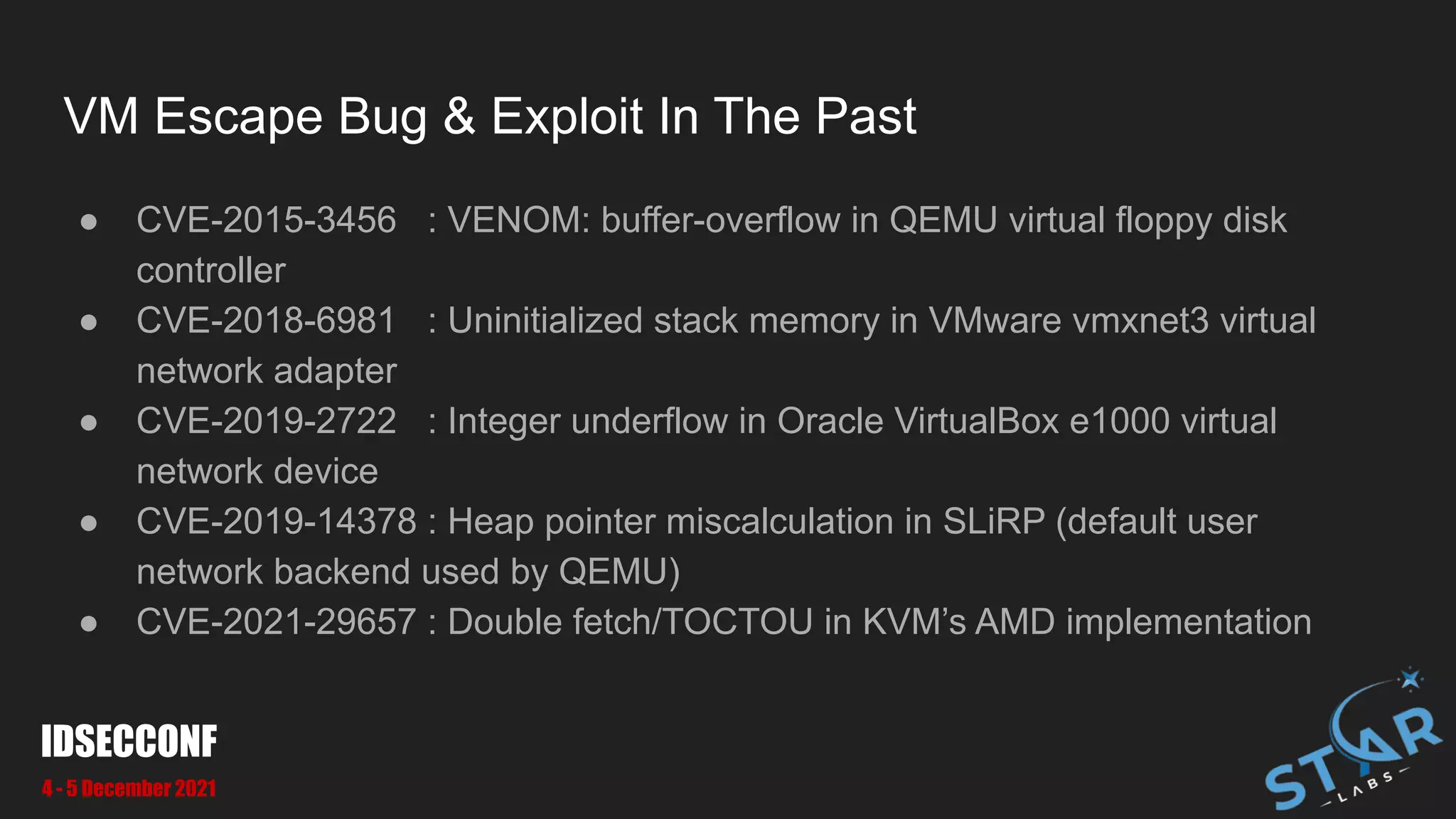
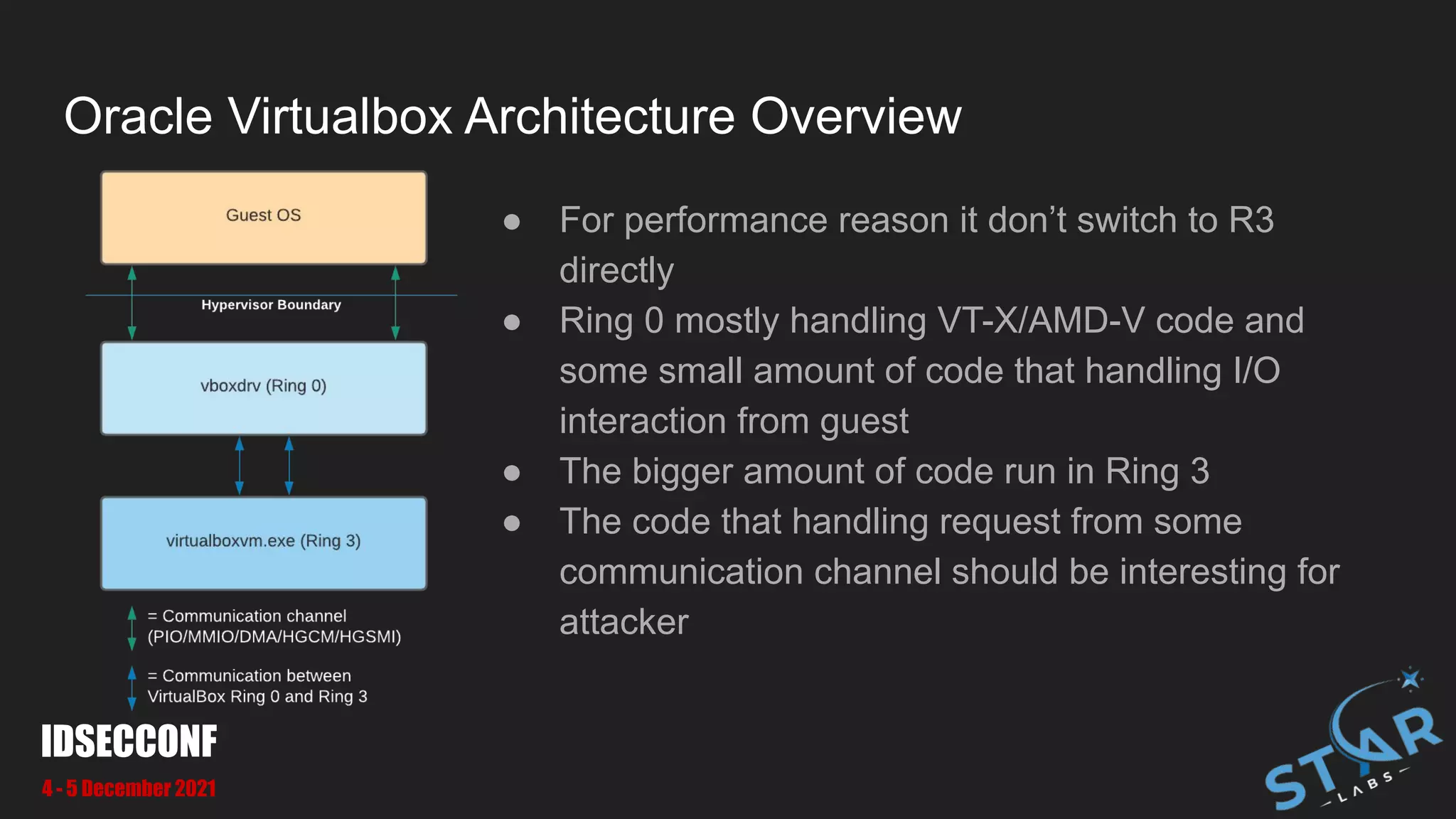
This document details a security research study on vulnerabilities found in Oracle VirtualBox, specifically focusing on VM escape and exploitation techniques. It highlights two critical vulnerabilities, CVE-2021-2321 and CVE-2021-2250, which involve out-of-bounds read and heap-based overflow, respectively. Additionally, it discusses the architecture of VirtualBox, the attack surfaces, and methodologies for bug hunting and exploitation.


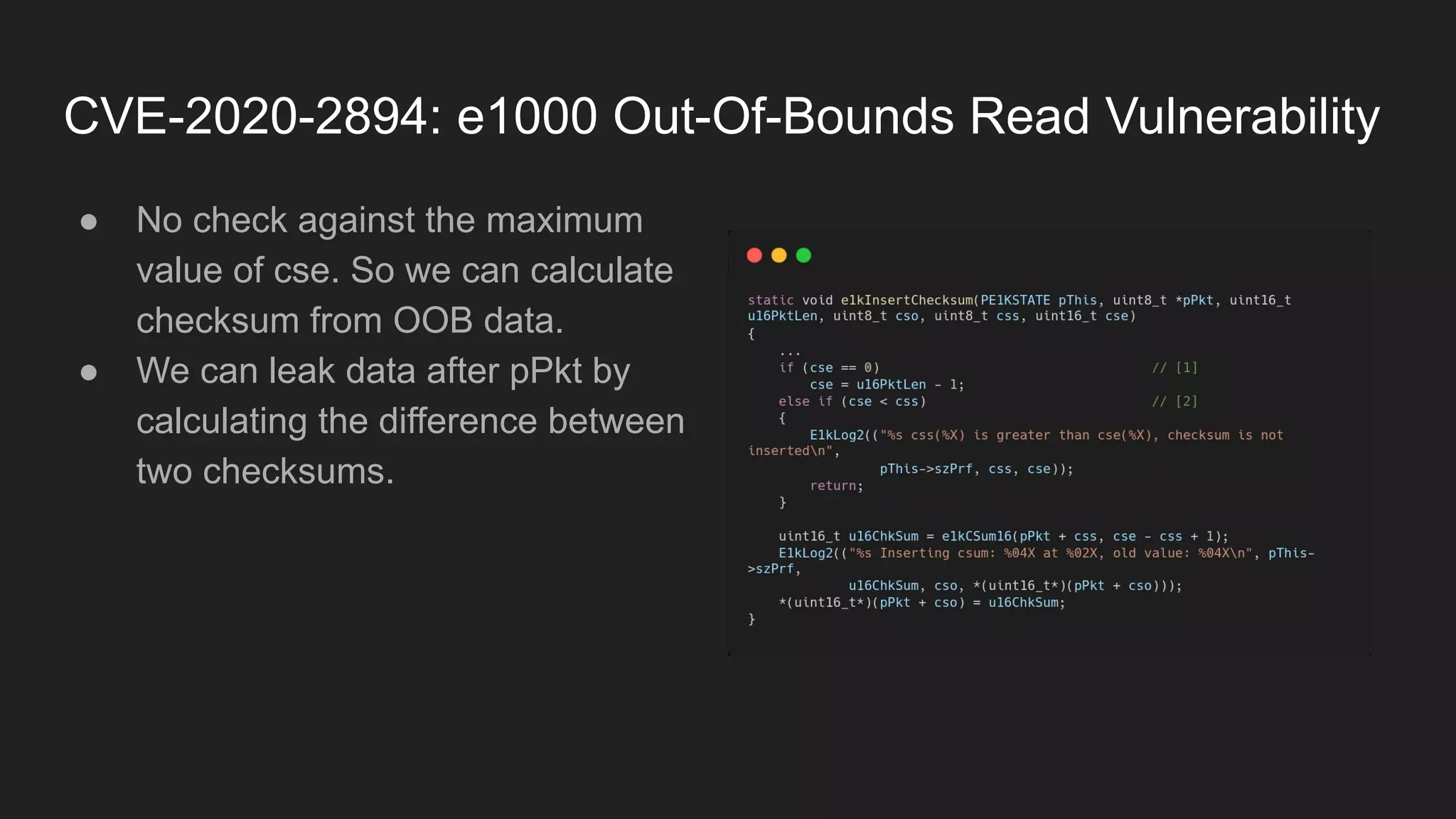
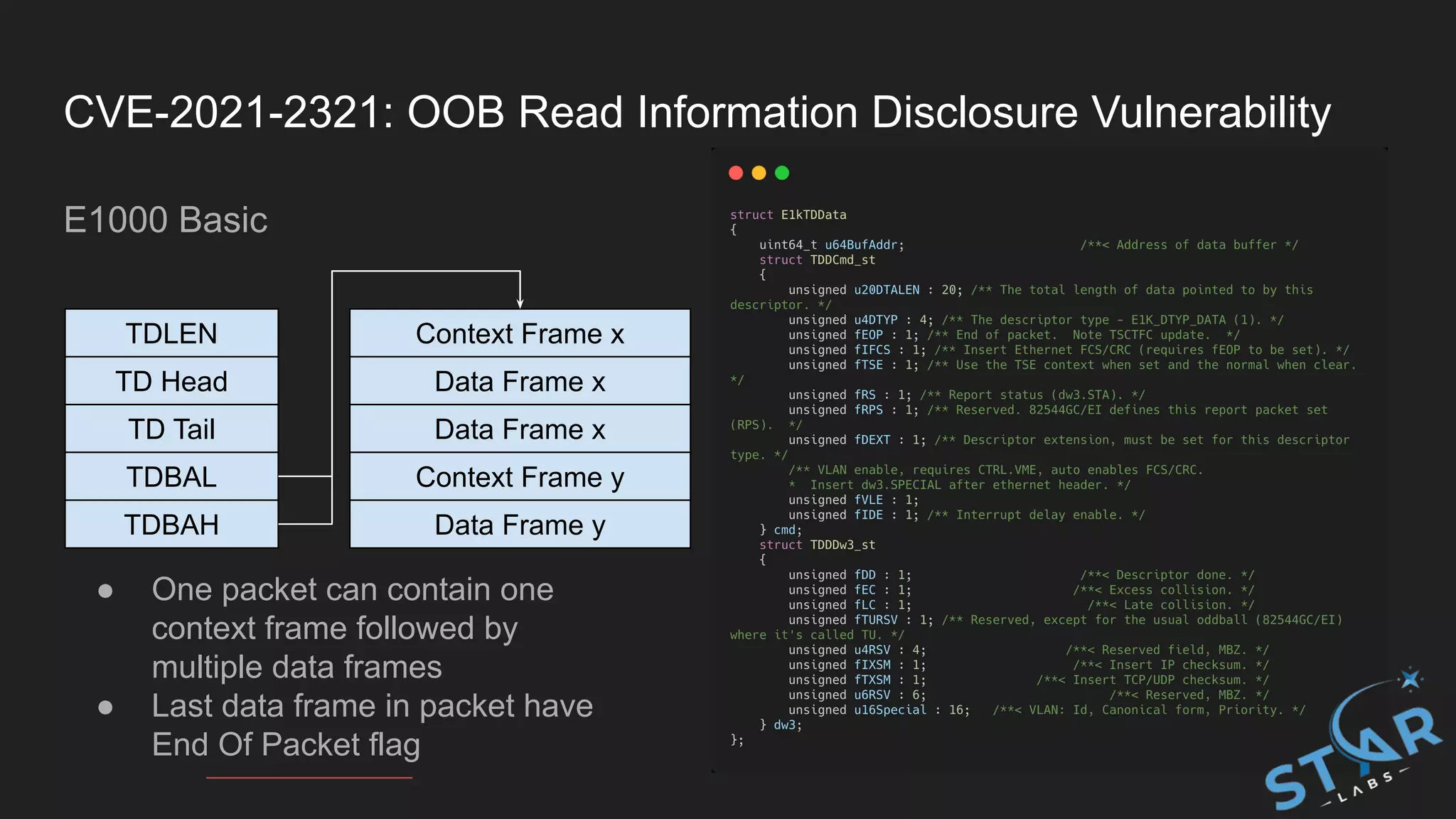
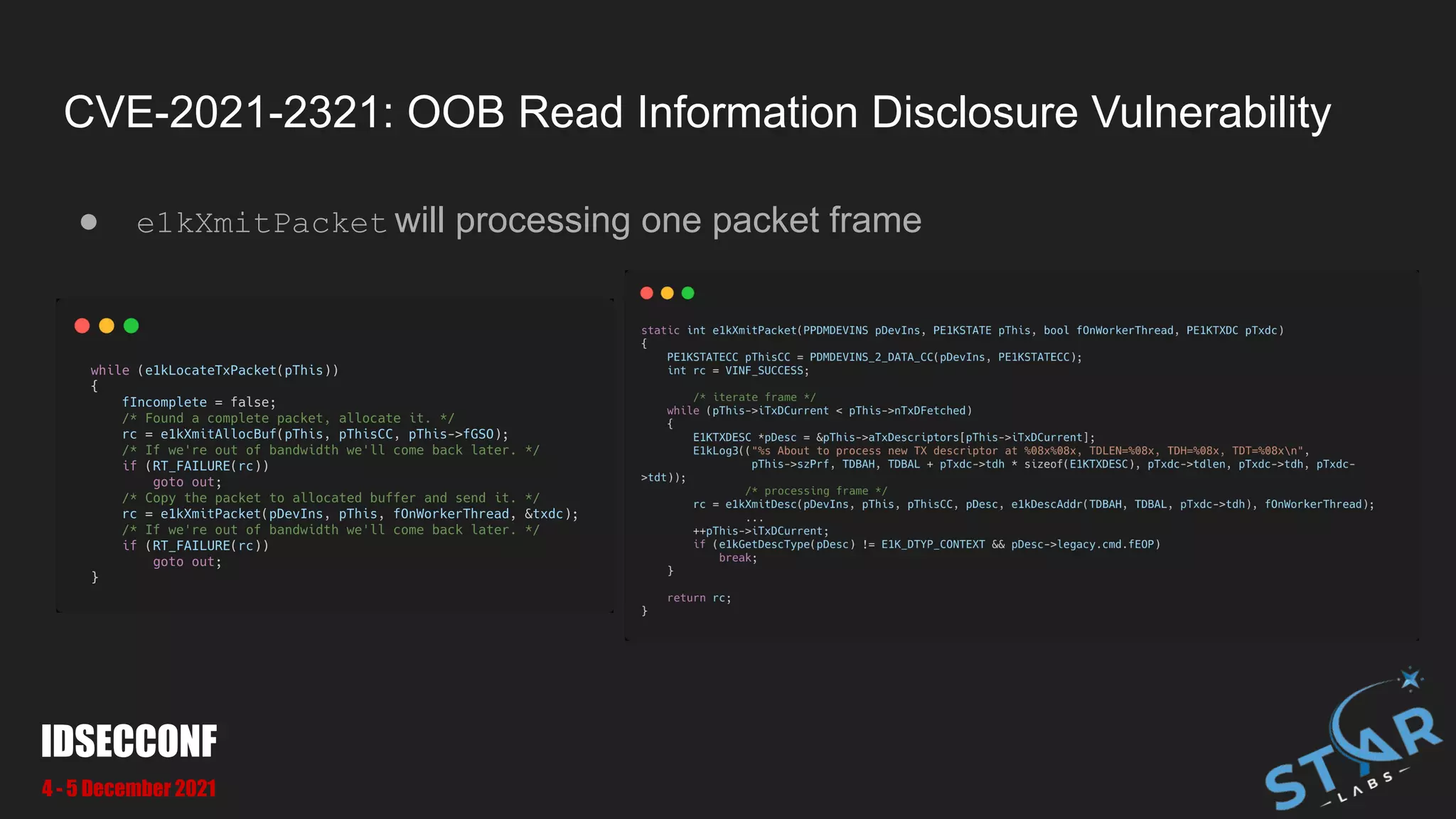
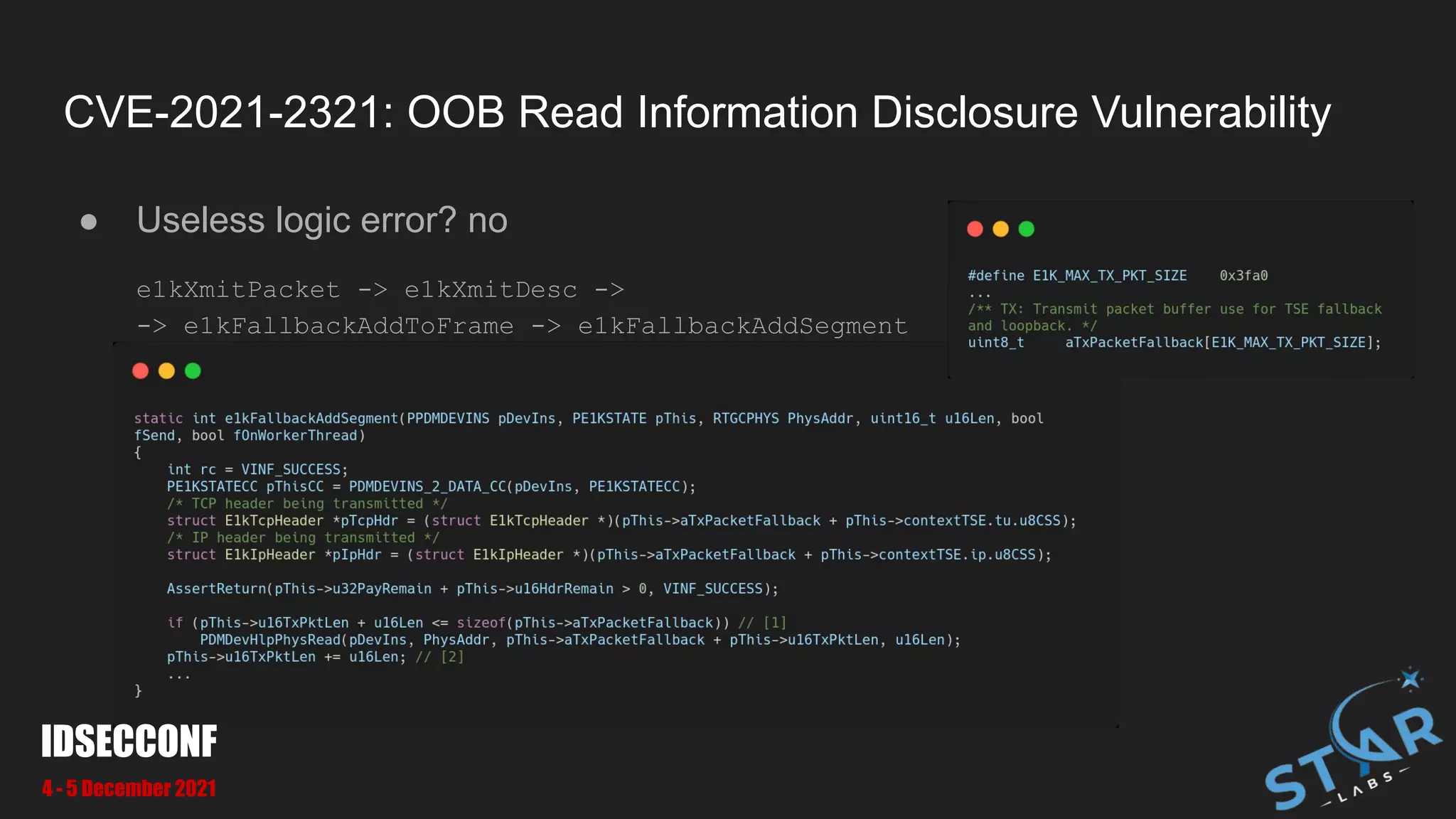
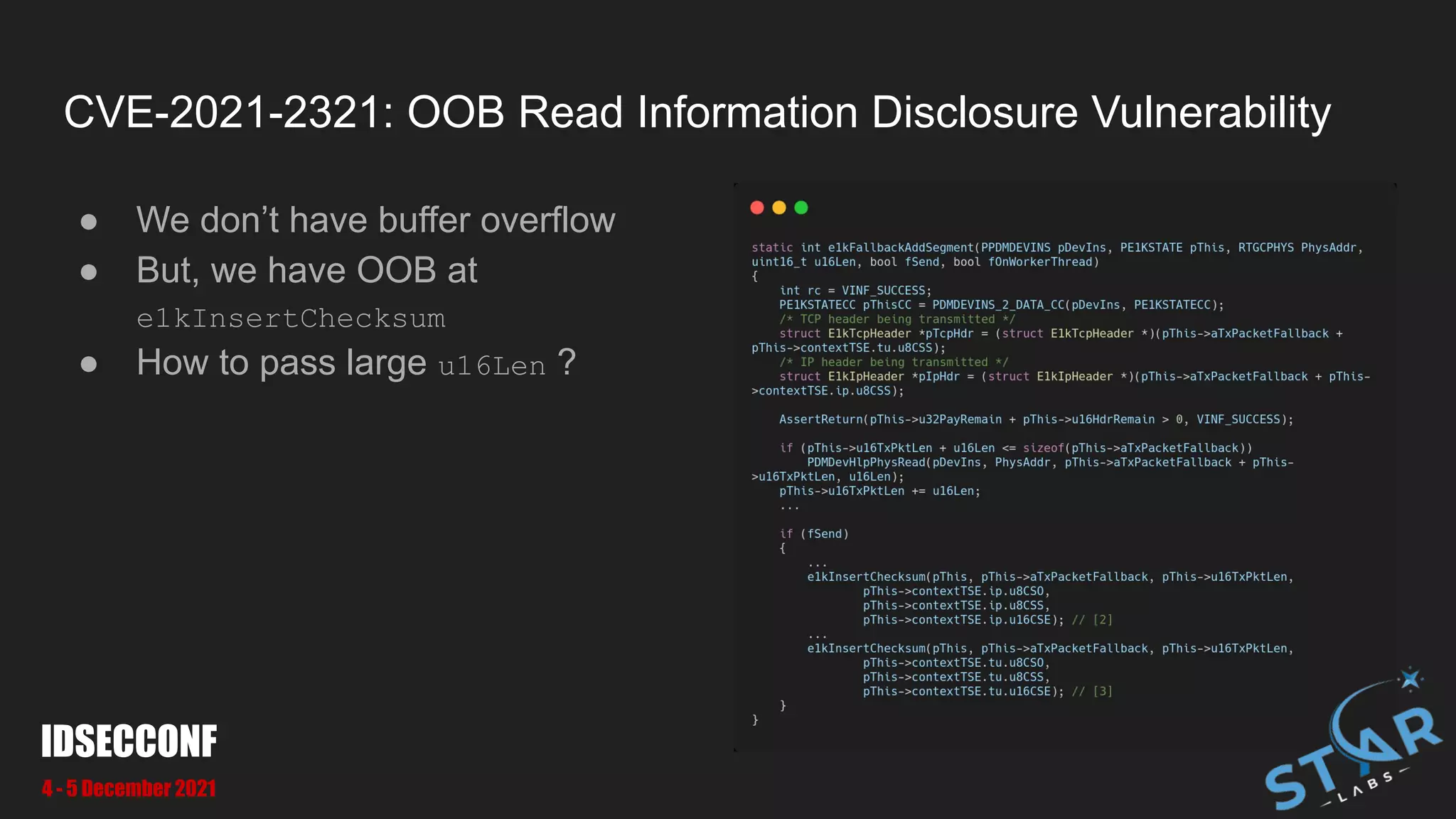
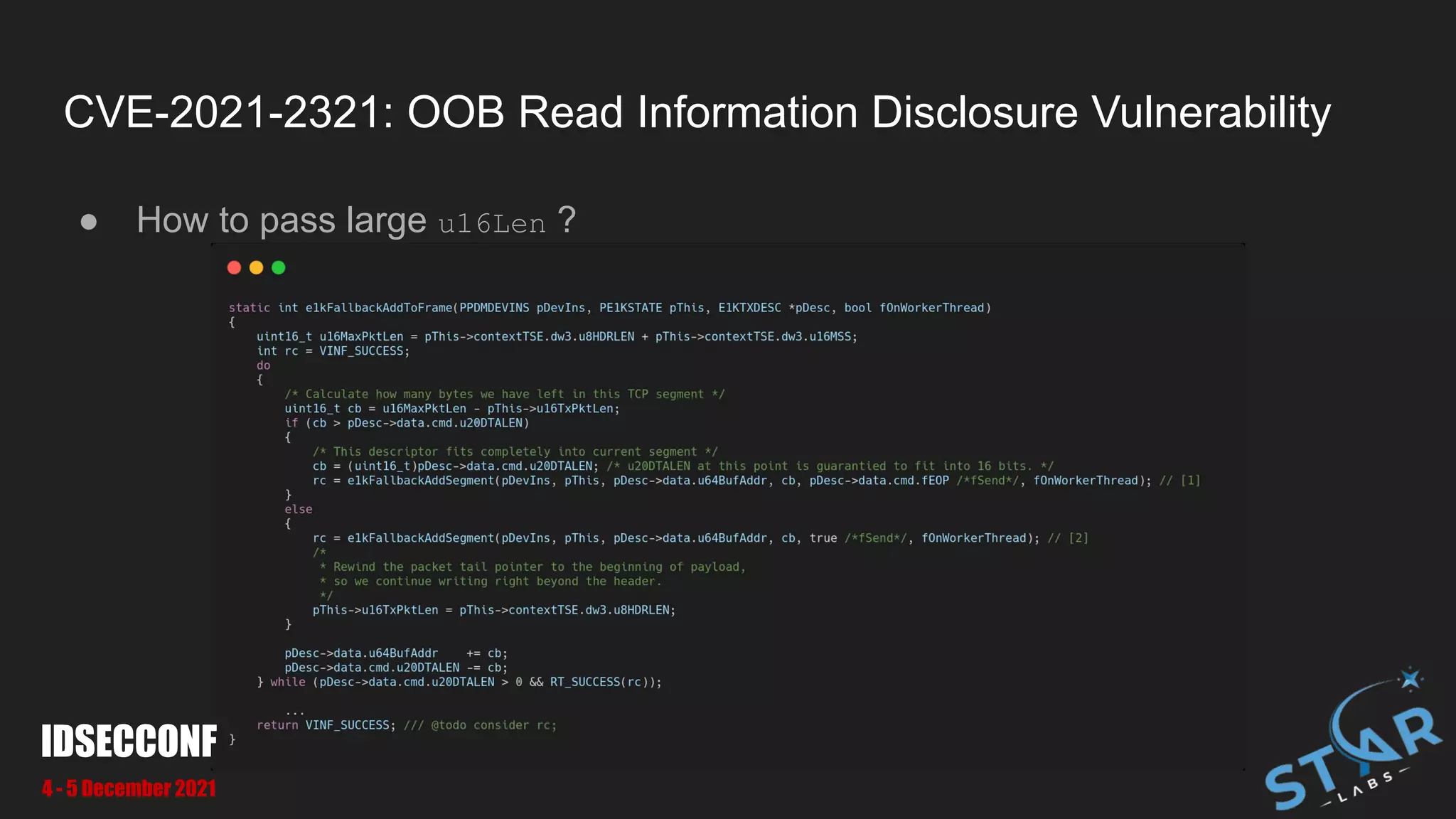
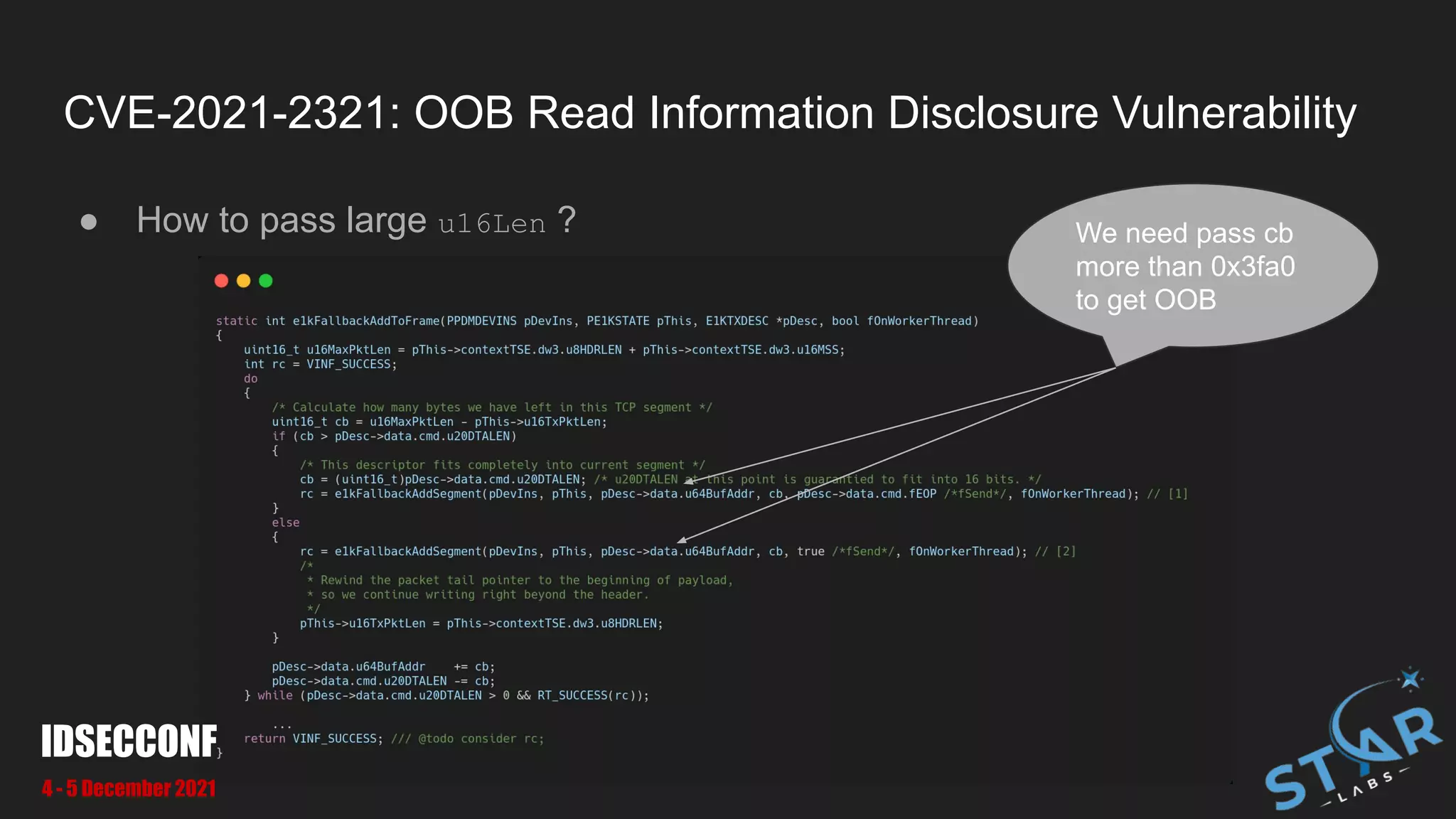
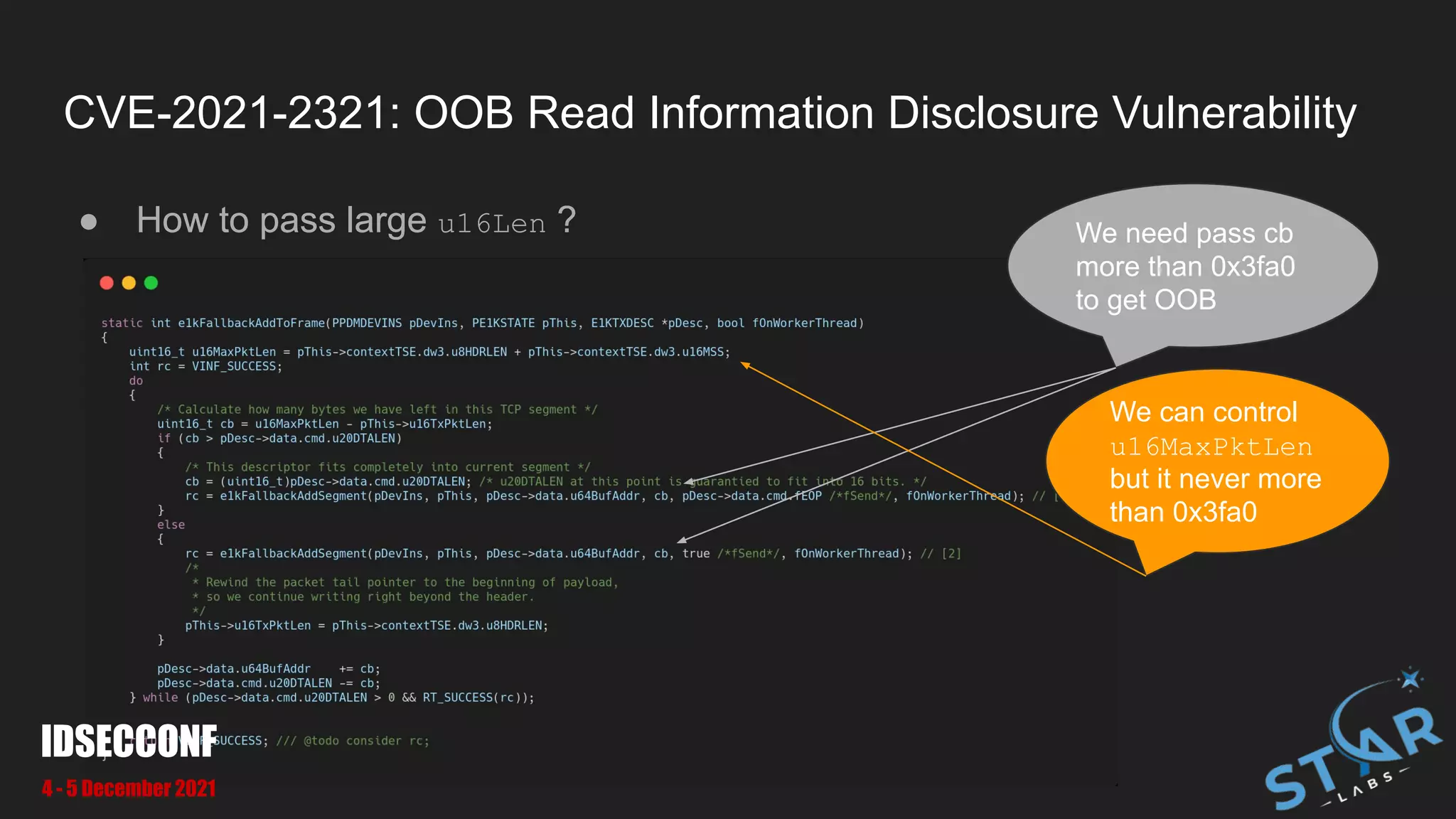
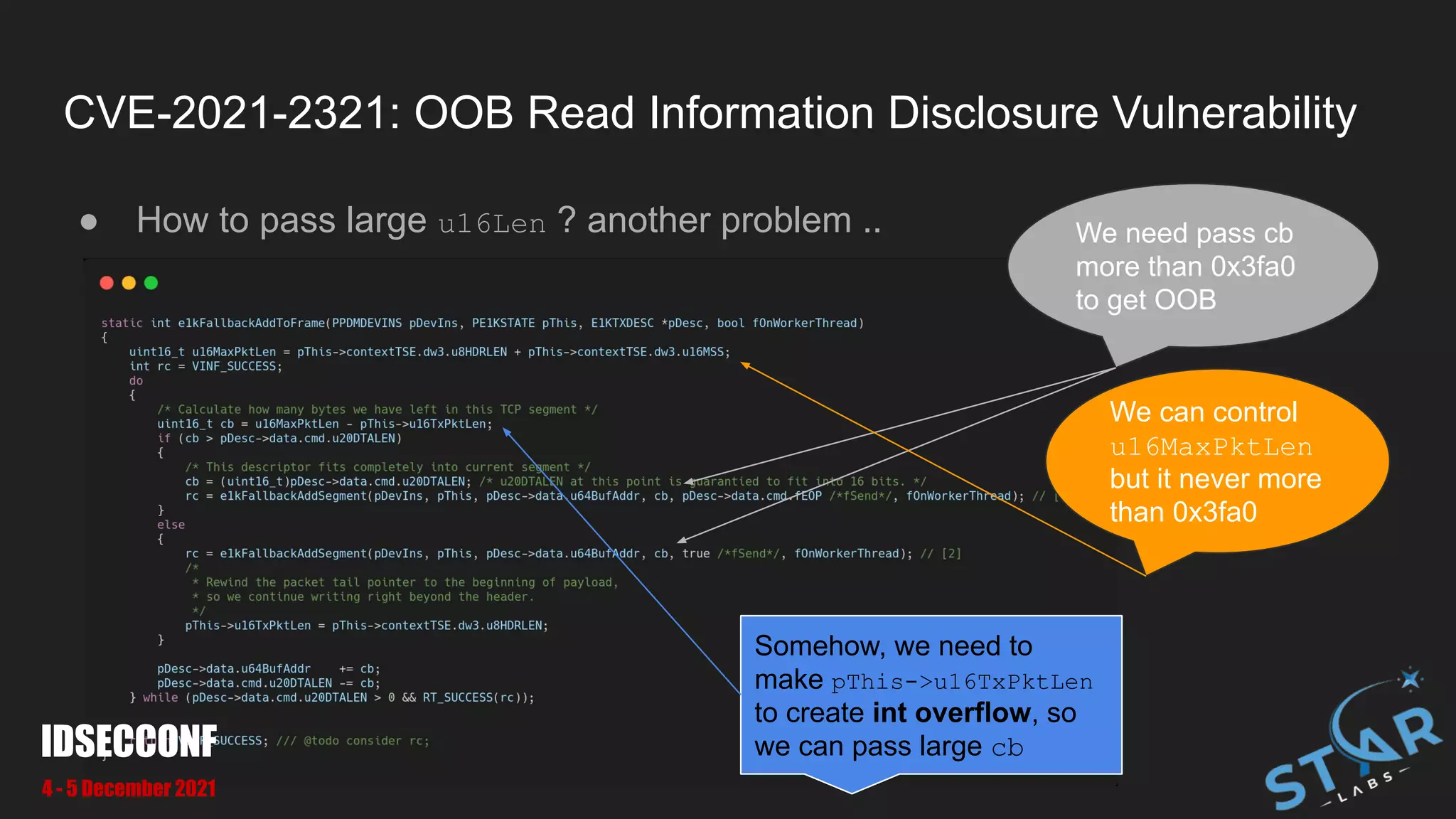
![CVE-2021-2321: OOB Read Information Disclosure Vulnerability
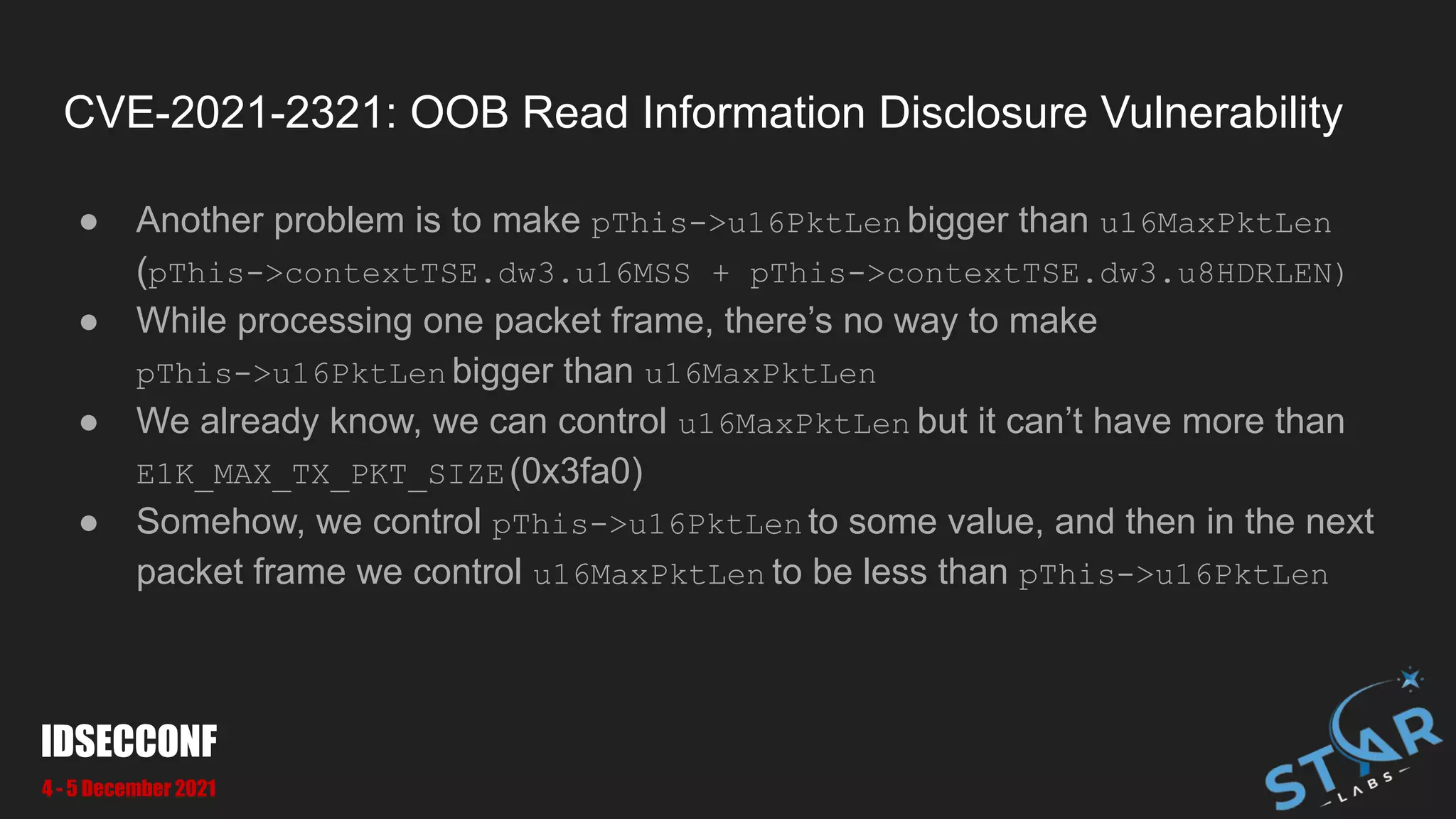
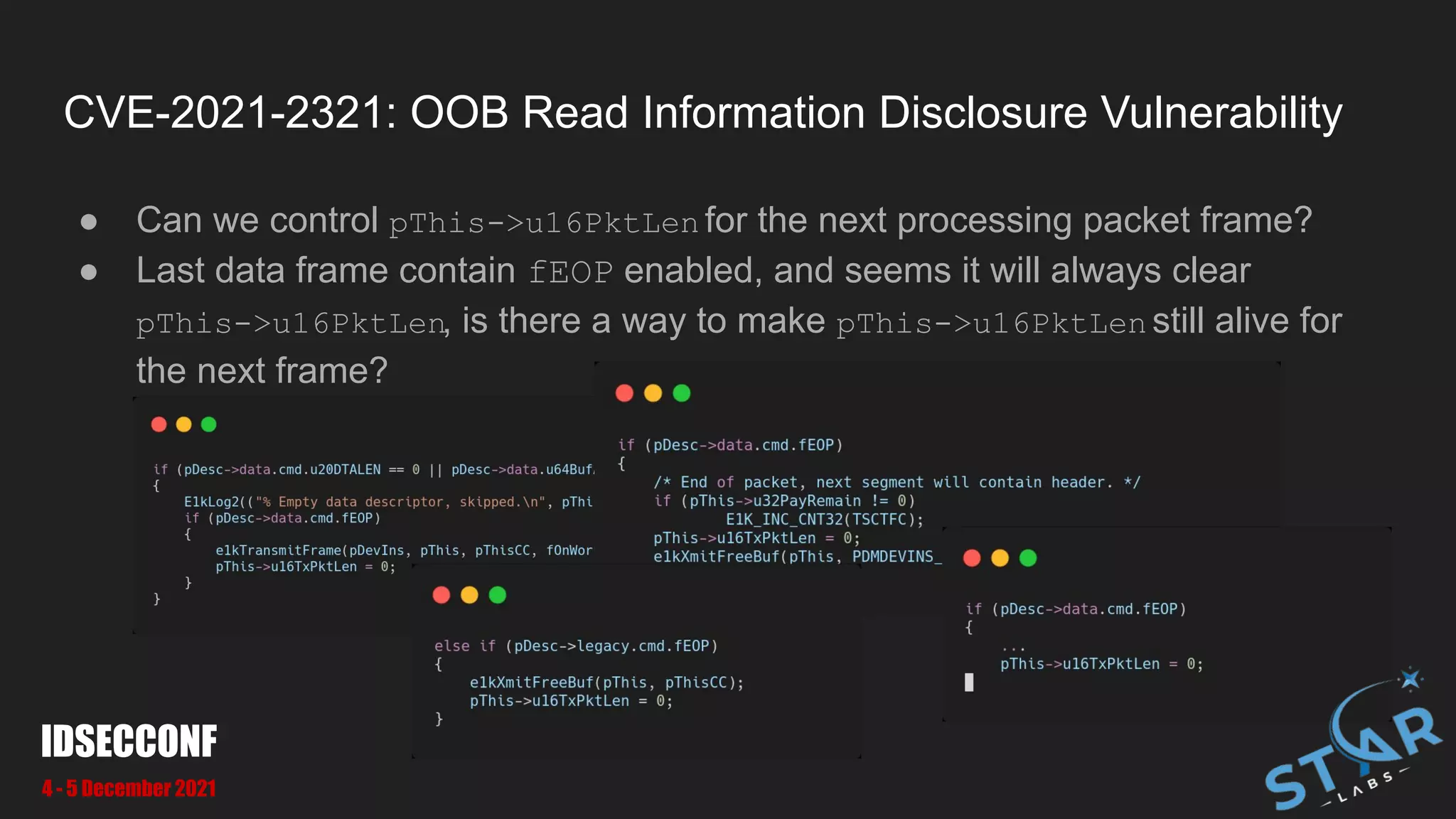
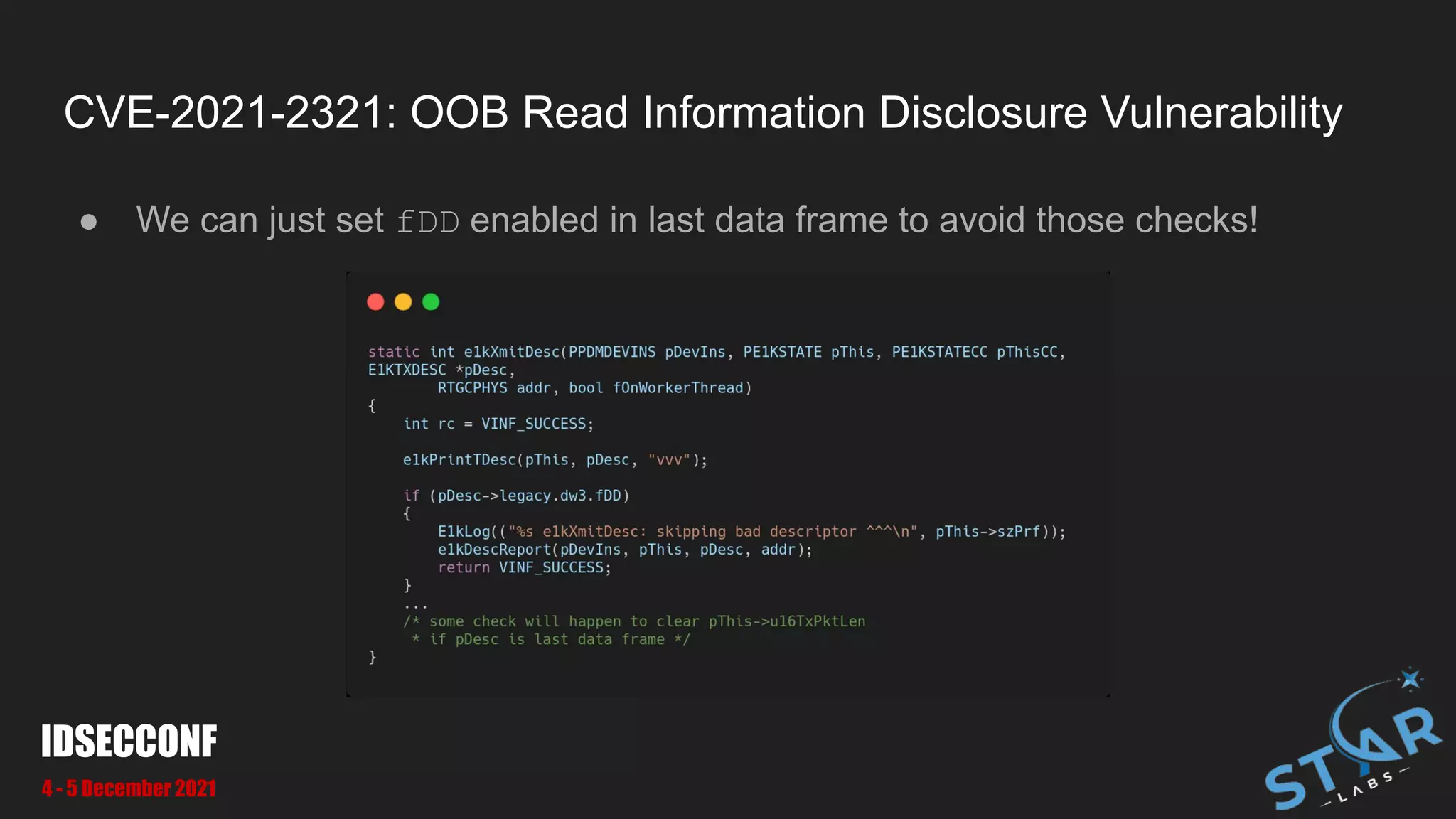
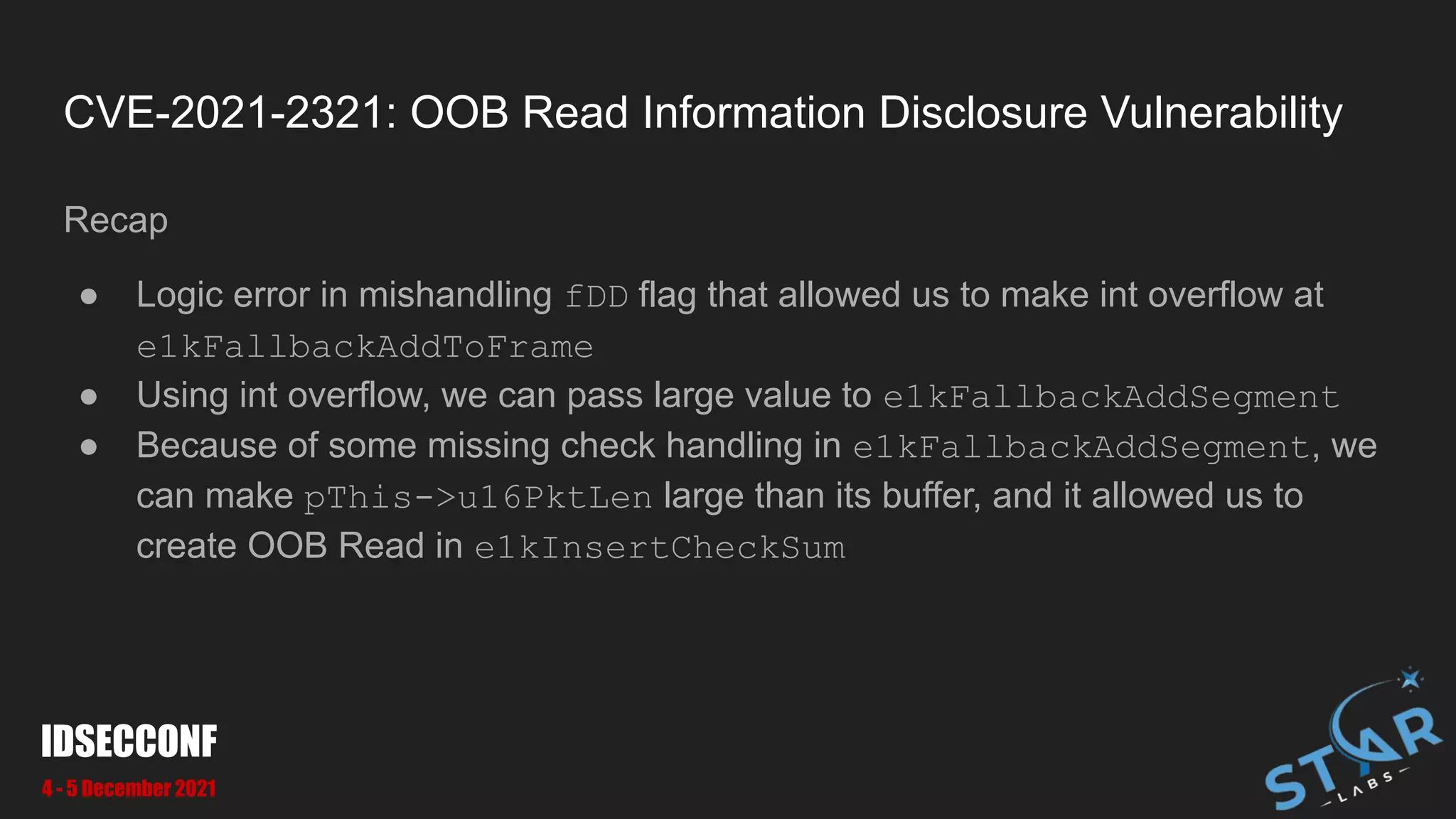
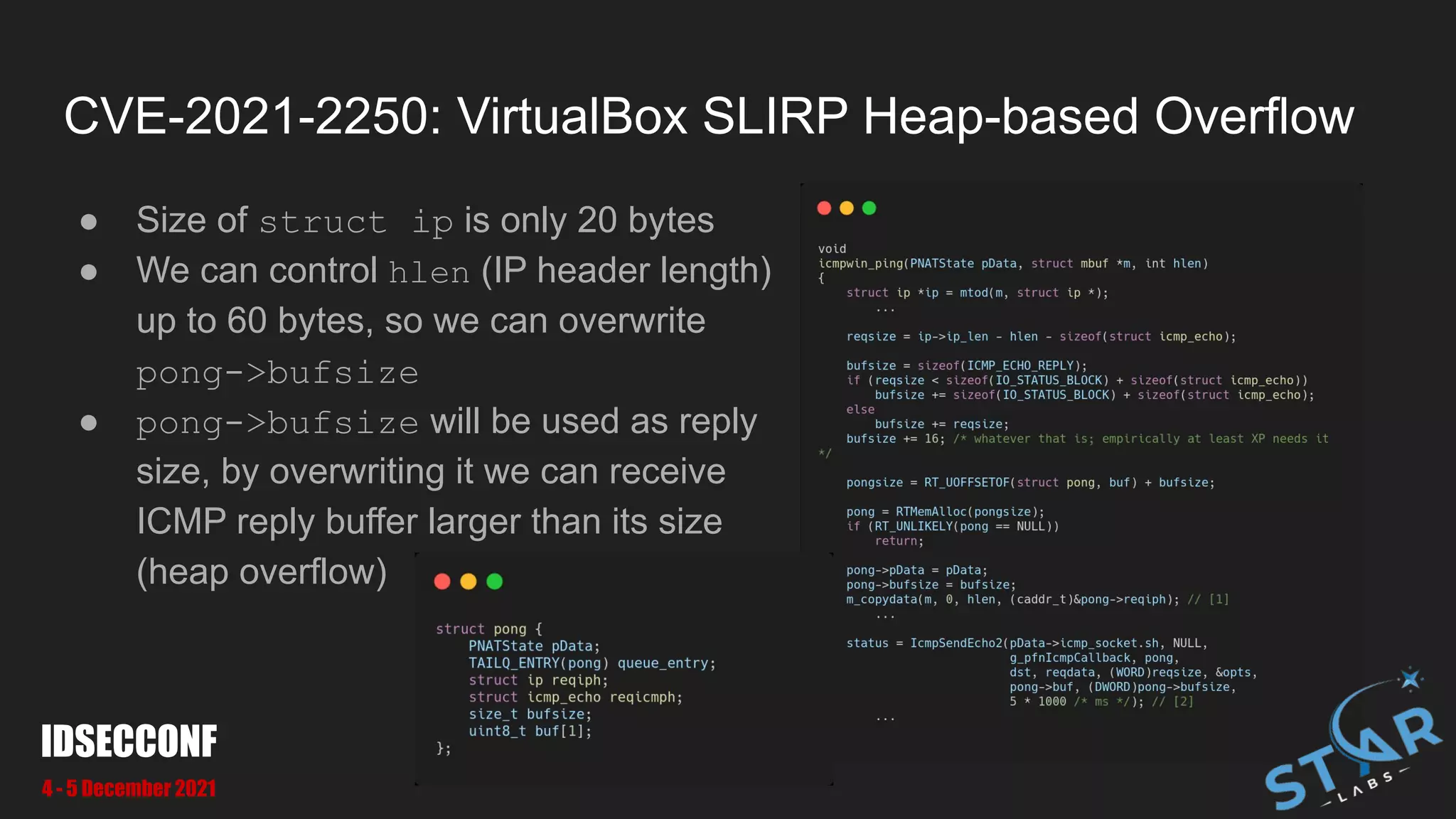
● We can pass pass large u16Len to make OOB at [1] and [2]
IDSECCONF
4 - 5 December 2021](https://image.slidesharecdn.com/vmescapecasestudyvirtualboxbughuntingandexploitationmuhammad-211206235031/75/Vm-escape-case-study-virtualbox-bug-hunting-and-exploitation-Muhammad-Alifa-Ramdhan-24-2048.jpg)
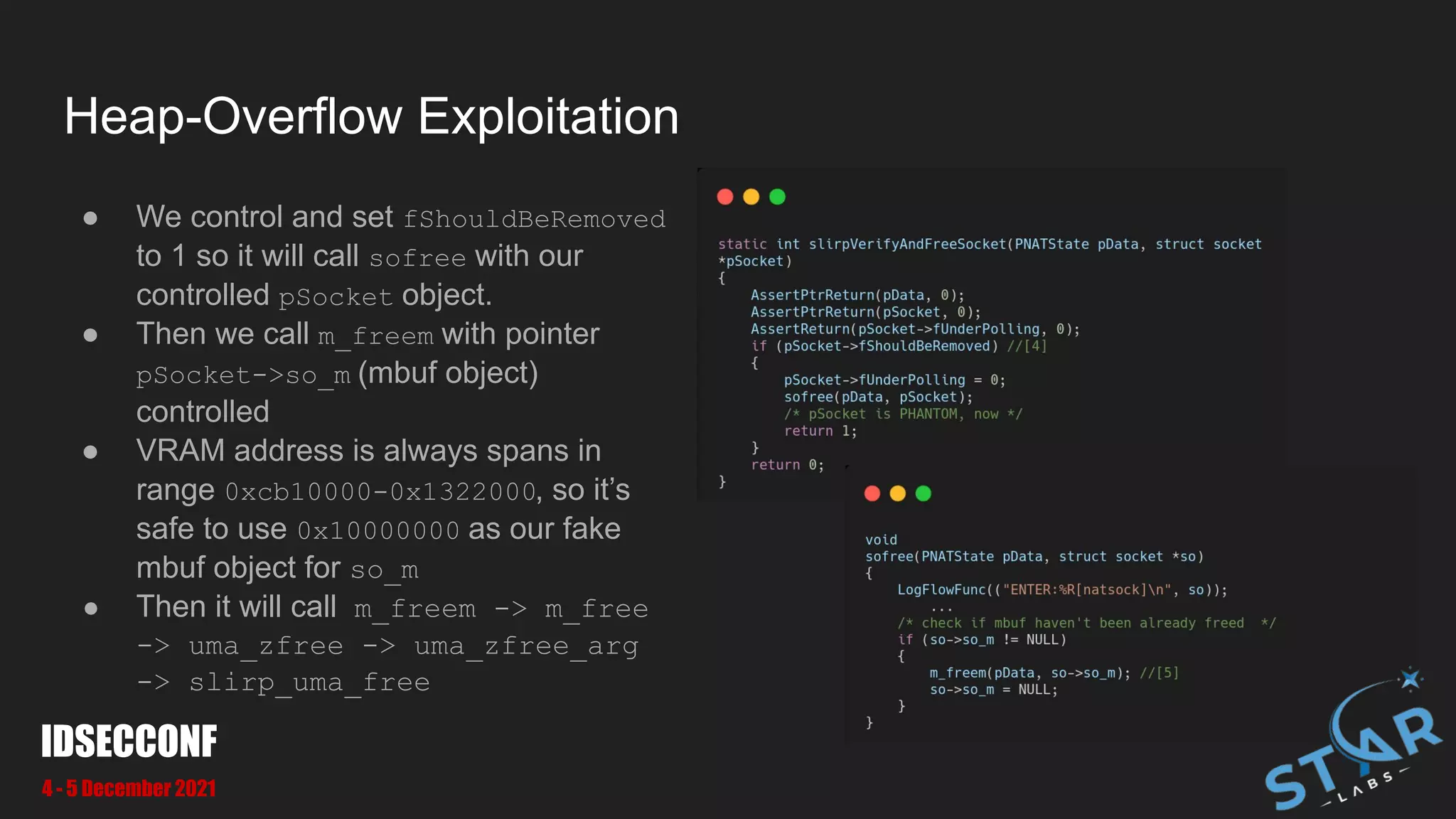
![Heap-Overflow Exploitation
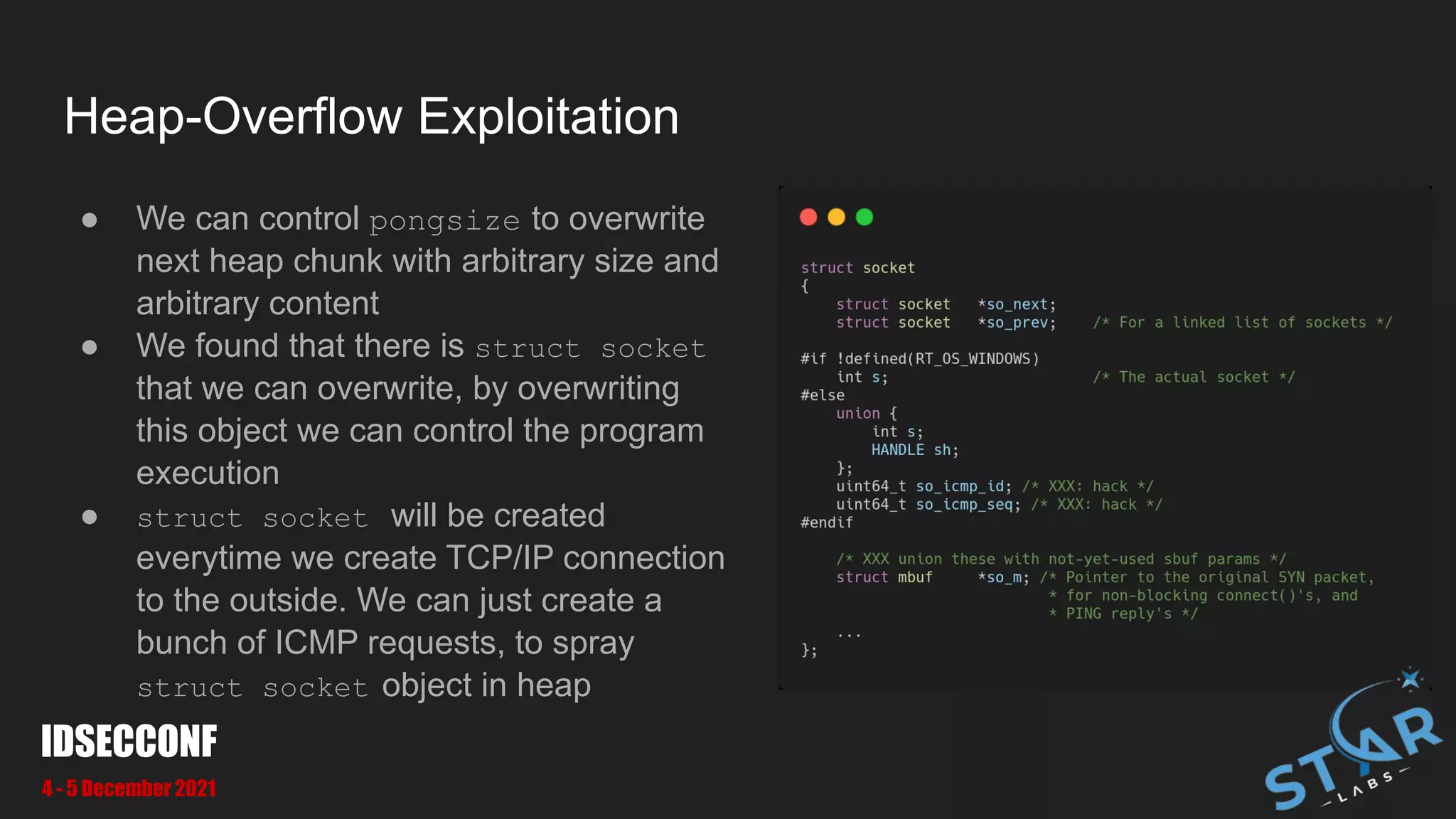
● There is a function which collect
struct socket object for handling
events e.g: there is ICMP reply coming
back
● In [1] it will process ICMP reply and
heap overflow will happened on some
struct object
● In [2] will collecting struct socket
object including the one we overwritten
● An overwritten struct socket will be
processed in [3]
IDSECCONF
4 - 5 December 2021](https://image.slidesharecdn.com/vmescapecasestudyvirtualboxbughuntingandexploitationmuhammad-211206235031/75/Vm-escape-case-study-virtualbox-bug-hunting-and-exploitation-Muhammad-Alifa-Ramdhan-29-2048.jpg)
![Heap-Overflow Exploitation
● We can control item, and redirect
program execution in [6]
● From the VBoxDD address we
retrieve with CVE-2021-2321. We
redirect address to stack pivot
gadget, and execute our
RopChain we already put at
VRAM address
● Then the RopChain will prepare
the shellcode and will execute
calc.exe!
IDSECCONF
4 - 5 December 2021](https://image.slidesharecdn.com/vmescapecasestudyvirtualboxbughuntingandexploitationmuhammad-211206235031/75/Vm-escape-case-study-virtualbox-bug-hunting-and-exploitation-Muhammad-Alifa-Ramdhan-31-2048.jpg)