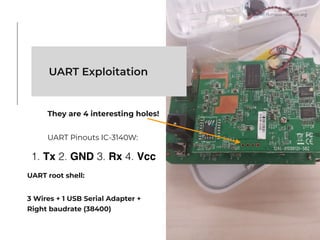
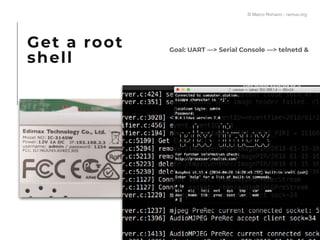
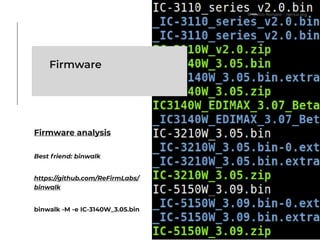
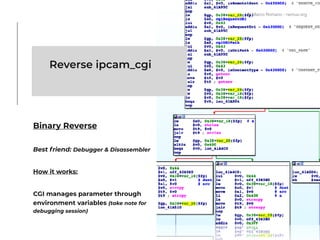
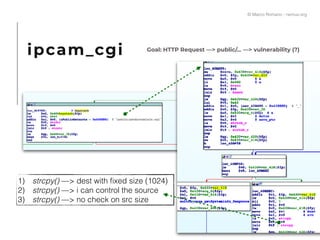
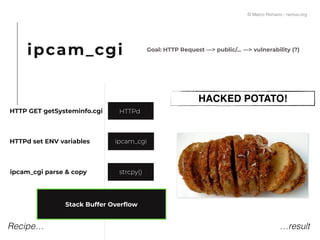
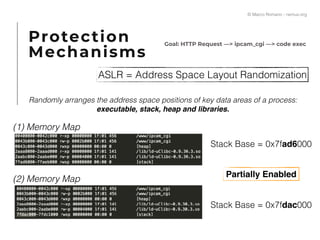
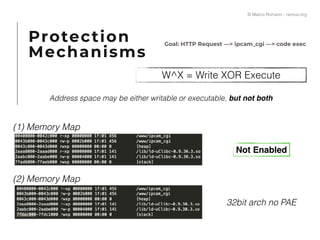
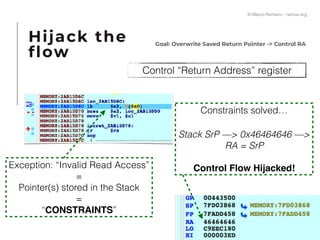
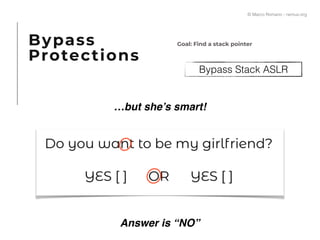
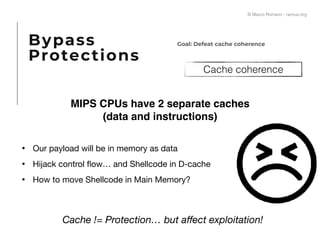
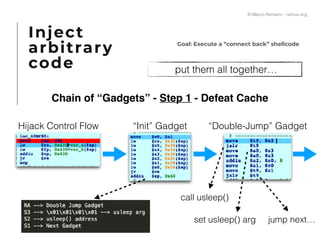
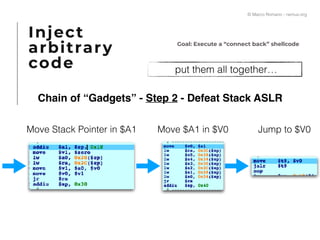
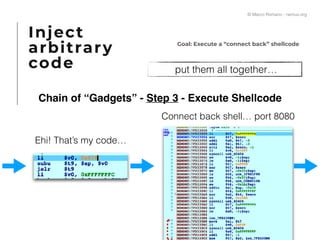
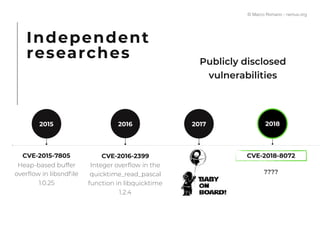
The document presents a technical exploration of IoT exploitation, specifically focusing on vulnerabilities in Edimax network cameras, including a stack buffer overflow issue (CVE-2018-8072). It details the methodology for vulnerability assessment and exploitation, including firmware analysis, bypassing protection mechanisms like ASLR, and executing arbitrary code. The findings culminate in a proof of concept that illustrates how to exploit these vulnerabilities for unauthorized access.



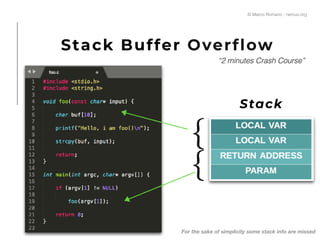
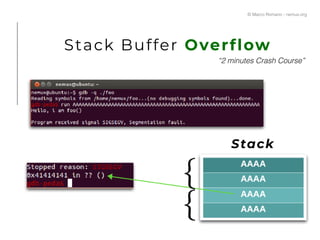
![Stack Buffer Overflow
© Marco Romano - nemux.org
1) main() calls foo()
2) foo() copies “AA…” in buf[]
3) foo() “return;” —> go back in main()
“2 minutes Crash Course”
Stack](https://image.slidesharecdn.com/romano-nemuxcodemotionrome18cover-180706083851/85/IoT-exploitation-from-memory-corruption-to-code-execution-Marco-Romano-Codemotion-Rome-2018-6-320.jpg)