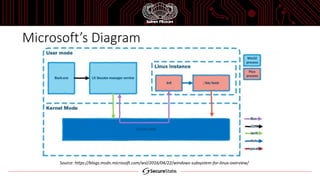
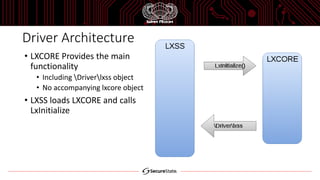
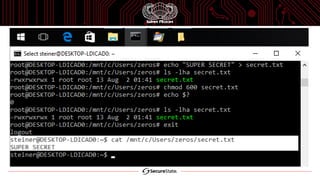
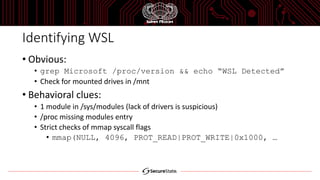
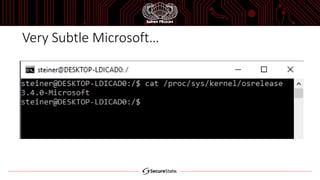
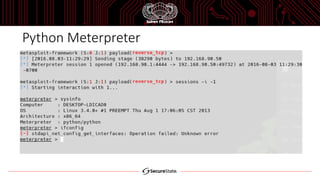
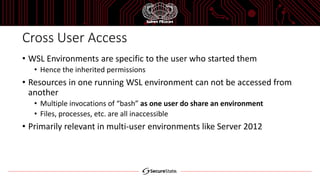
The document discusses the Windows Subsystem for Linux (WSL), which allows Linux binaries to run natively on Windows. WSL implements Linux syscalls via two Windows drivers. It uses "picoprocesses" which are lightweight isolated processes. This allows Linux files to be accessed via special filesystems like DriveFS. The document also notes considerations for attackers using WSL, such as limitations on cross-process access between Linux and Windows.